vinafamily
DeFi Protocol Auditor
LEVEL 1
400 XP

Hey Folks, In our previous articles we discussed about the installation and some features of the Metasploit tool, but in this article we will discuss the leftover features of this tool. You can check both article from here.
Let’s take a look
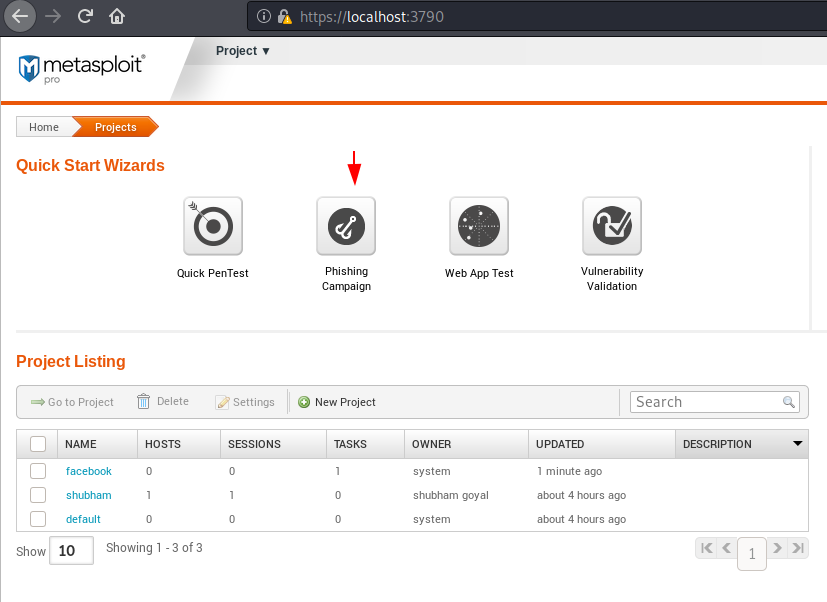
Boot Metasploit Pro
Let’s boot up your Metasploit framework and select the “Phishing Campaign” option. Through this feature of this tool we can easily host phishing pages on our localhost web server and get the victim’s credentials easily.
Hmm
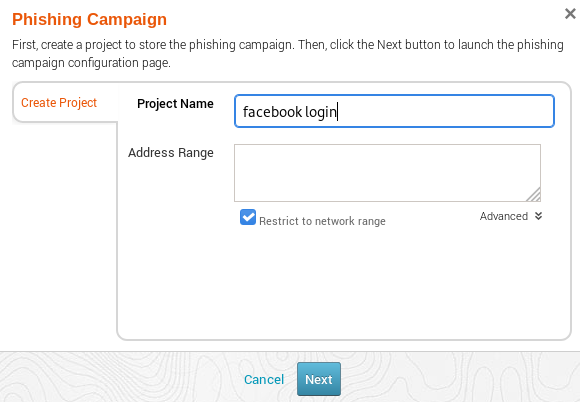
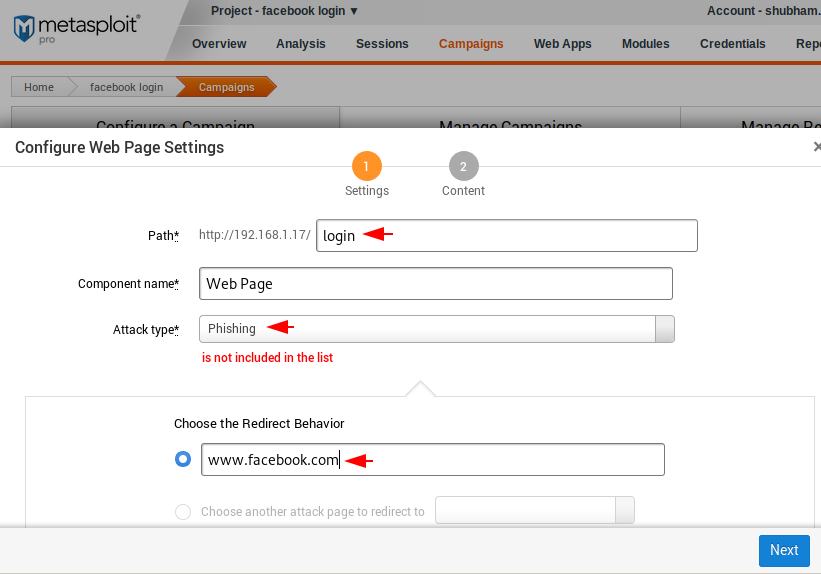
After that we have to name the phishing page which will appear in the link and also on the browser. In our case we give the name of the phishing page as “login“. After that select “Custom Campaign” option and click on “Web page“, a sub-feature of “Custom Campaign” option.
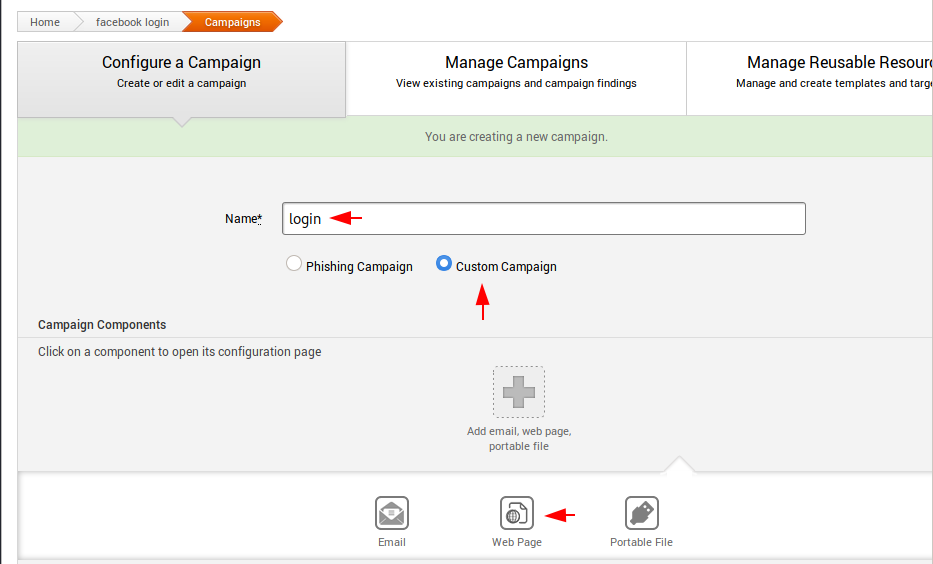
Again, you have to give the same name that we gave in the beginning. Then select the type of attack as phishing and enter the address where you want to redirect the victim.
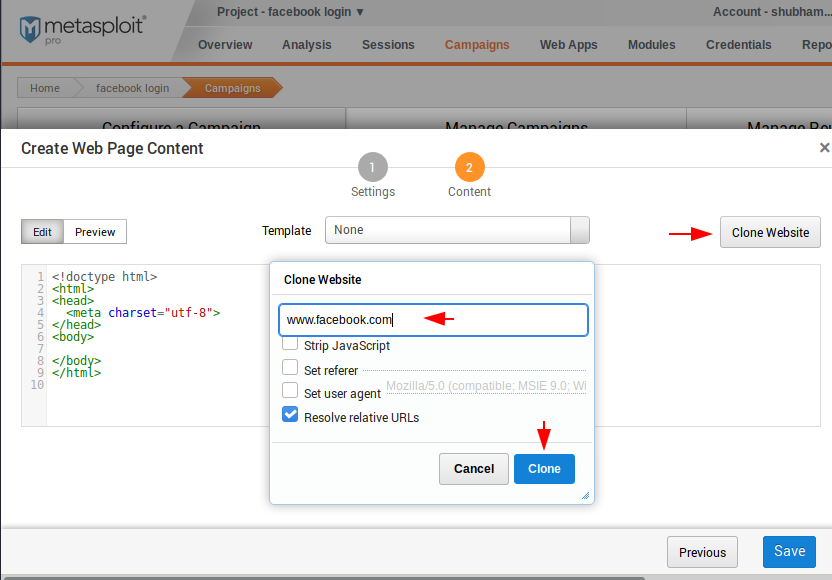
Move to the content section and click on the “Clone Website” option to clone the entire website in just a second. After that give the name of the website you want to clone and then click on “clone” button.
Great

Done
Link
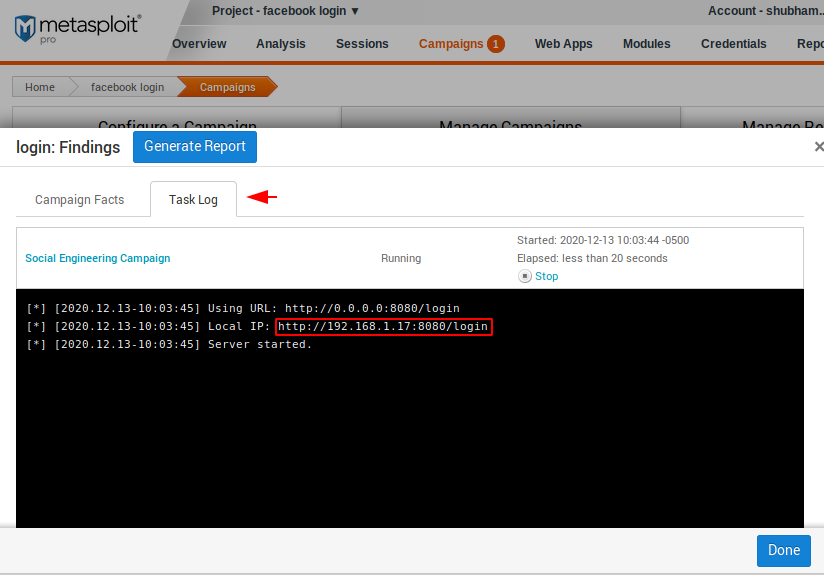
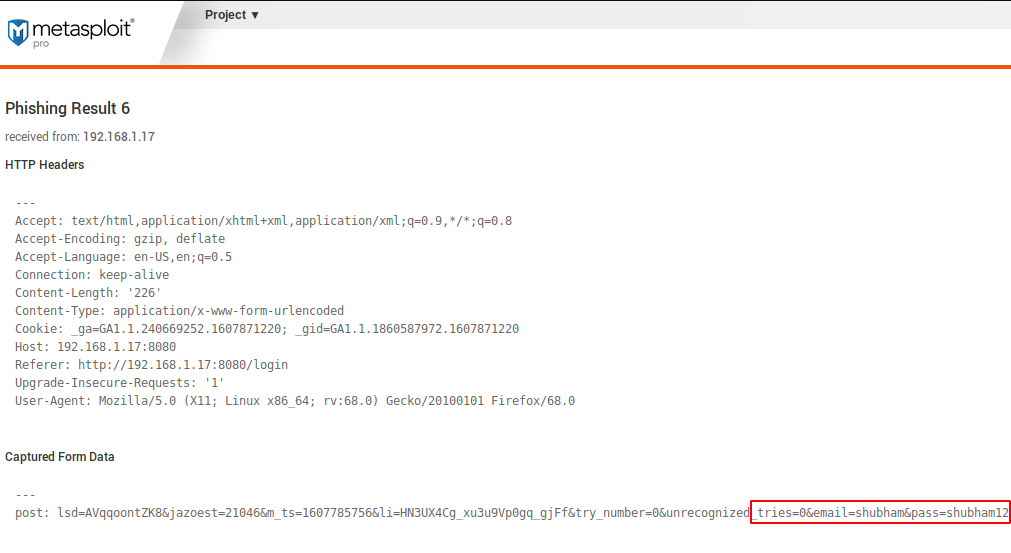
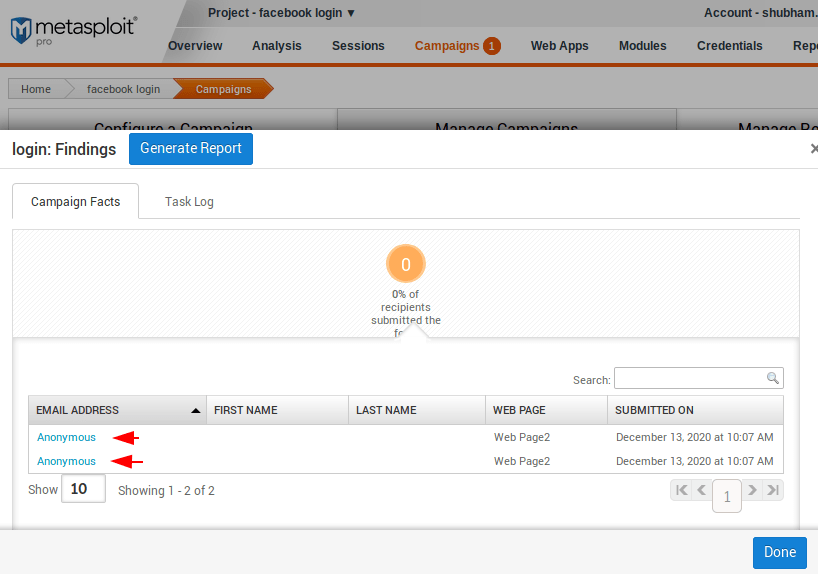
As you can see in the image below what the phishing page looks like after the victim opens the link.

You can see that the credentials has been submit by the victim twice.
Nice