TheCacatJoaca
Deployment Wizard
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP

Hey Folks, in this tutorial we are going to introduce an official tool that allows us to perform a complete penetration testing called “Metasploit“. Metasploit Pro recommended for penetration testers and IT security teams, offers a compressive set of advanced features. If you’re simply looking for a basic command-line interface and manual exploitation, check out more about Metasploit Framework from here.
Let’s take a look
Metasploit Registration
We have given a short introduction about this tool which you can read from above. It is free and comes with pro version also but in the pro version you have to pay money to use this tool for lifetime. Don’t worry if you don’t have money, you can still use the pro version free for 14 days which is available to everyone. Now we will register for the Pro version from here.
Done
Metasploit Installation
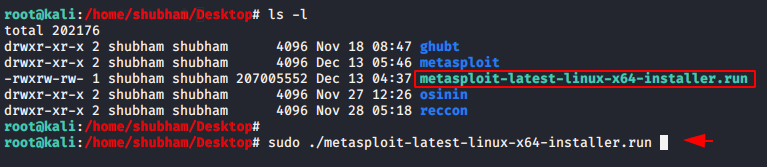
After that we can download it for the window or linux machine that you choose according to you. After downloading we can boot it directly using the following command.
sudo ./metasploit-latest-linux-x64-installer.run1sudo./metasploit-latest-linux-x64-installer.run
Metasploit Installation Location
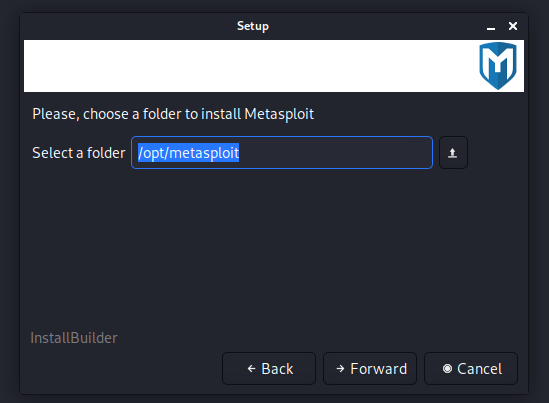
Now we need to give place where we want to save the entire file and install this tool.
Metasploit Persistence Service
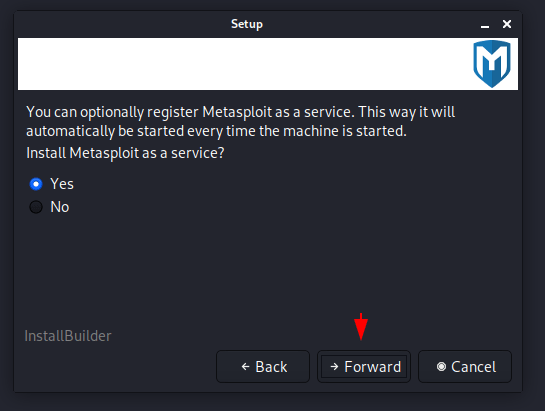
By selecting the “Yes” option we can create the persistence service of this tool after which Metasploit will be activated automatically whenever we start this machine.
Metasploit Hosted
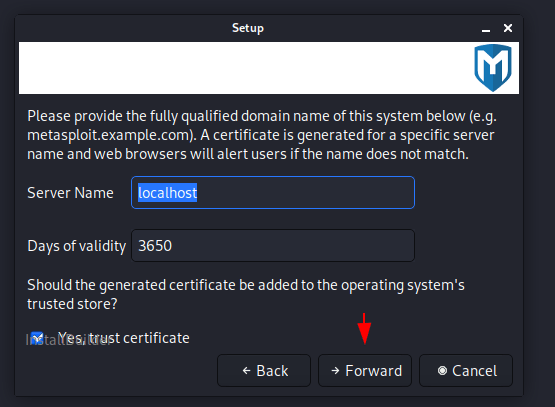
It will automatically fetch all the appropriate web server details, but if it does not display then you can enter the web server details itself and give a port number according to you.
Complete
Alright
Loading…
localhost
Loading…
localhost
Again
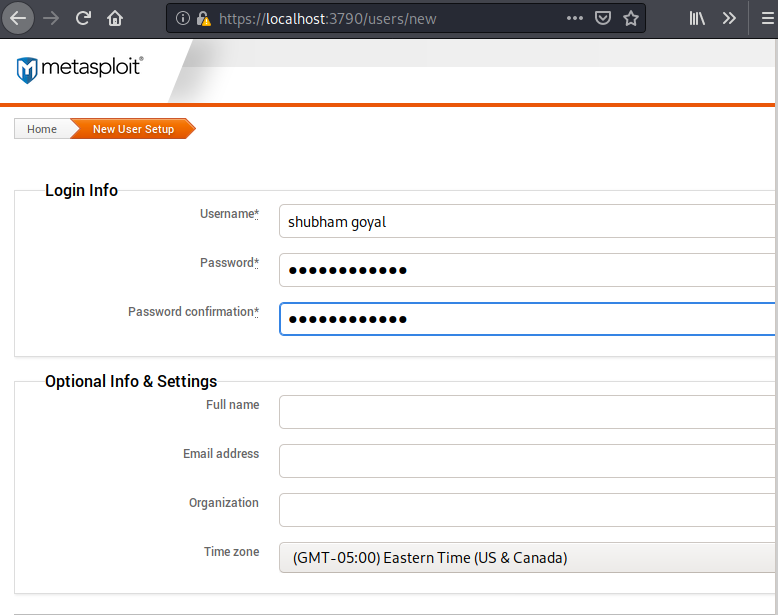
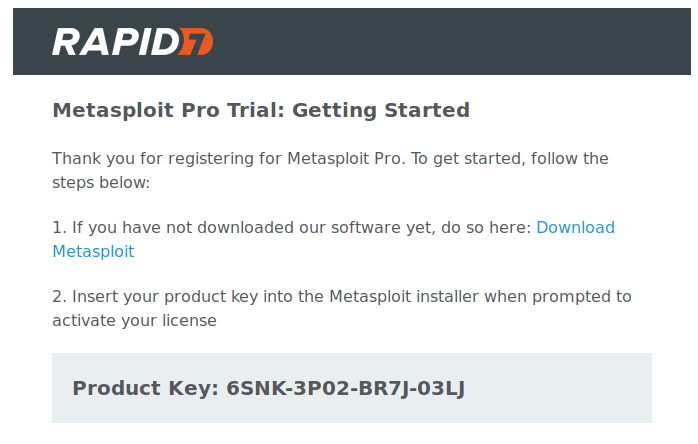
We already have the product key that we had acquired via email by Metasploit Framework after registration.
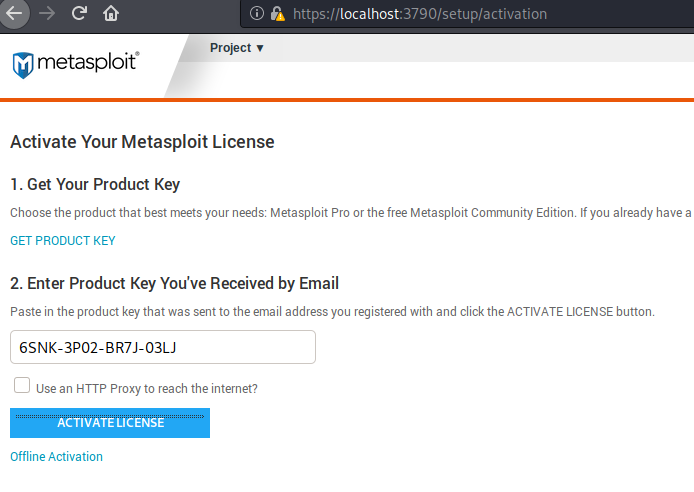
Done
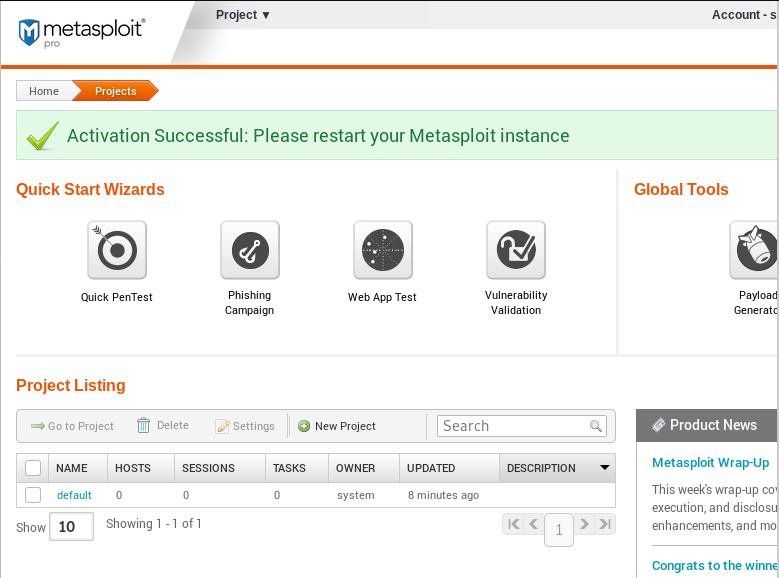
Wait
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.