ninja10
Humor Tactician
LEVEL 1
400 XP

Hey Folks, in this tutorial we will install kodachi linux operating system on VMware in windows machine. Linux Kodachi operating system is based on Xubuntu 18.04 LTS it will provide you with a secure, anti forensic, and anonymous operating system considering all features that a person who is concerned about privacy would need to have in order to be secure. If you want to read more about it you can go here.
Let’s take a look
Installation of VMware
Installing VMware software in a Windows machine is quite easy which you can do by downloading it from here.

Fire
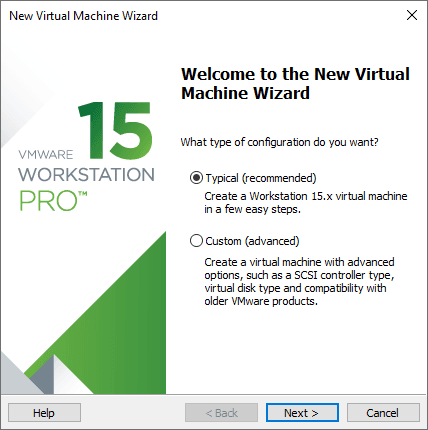
Just go with the software recommended option and click on Next.
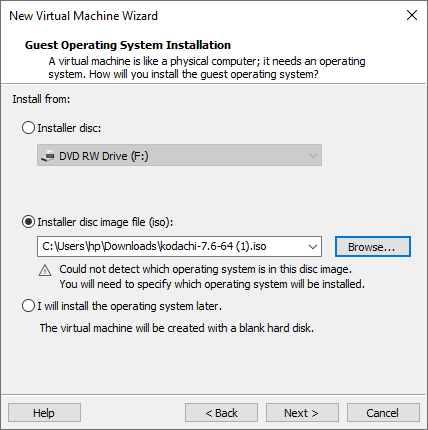
Now click on the browse button to select the Kodachi downloaded ISO image. You can download ISO image from here.
Select the operating system type “Linux” and version as well.
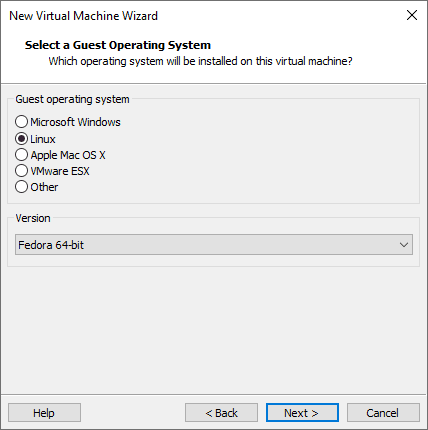
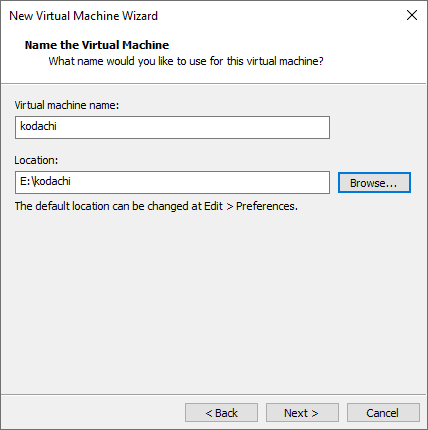
Give the machine name and the location where you want to save the logs and data.
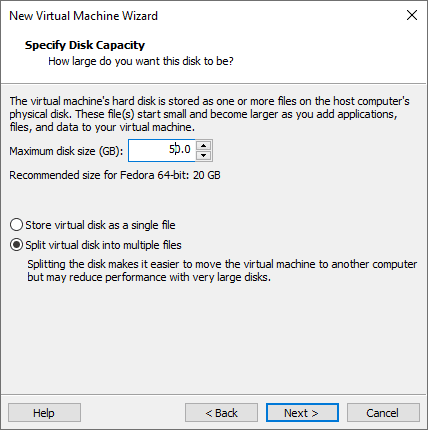
Storage Management
Here you can give storage to your operating system but make sure it should be more than 30 GB.
Hardware Customization
After that just click on “customize hardware” option and proceed. You can provide memory as per availability but minimum should be 3 GB to run perfectly.
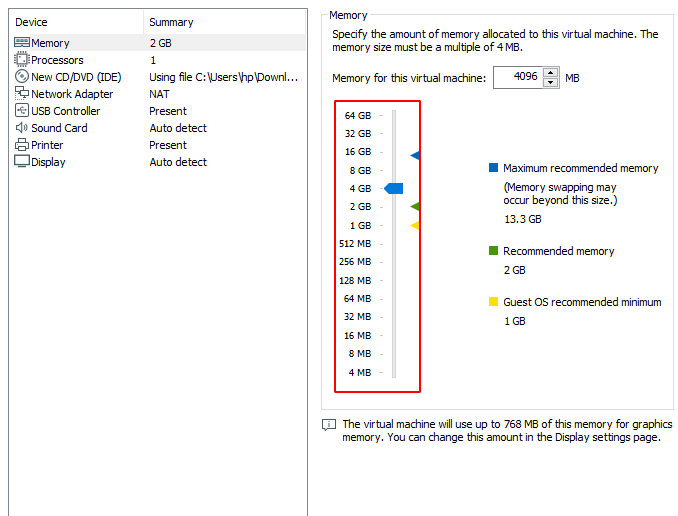
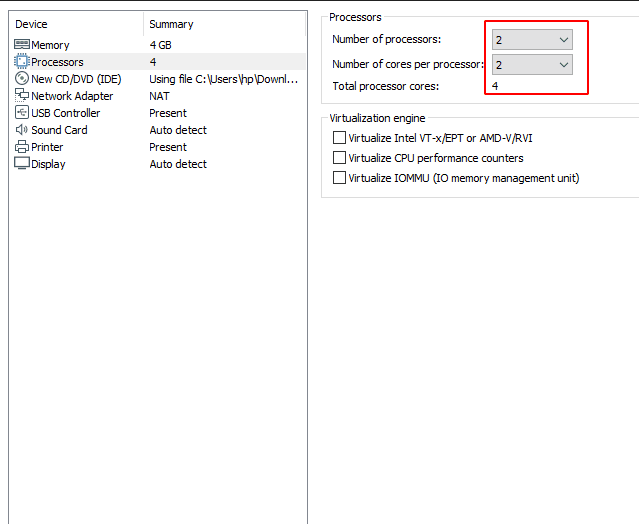
You need to give the same number of processors in both.
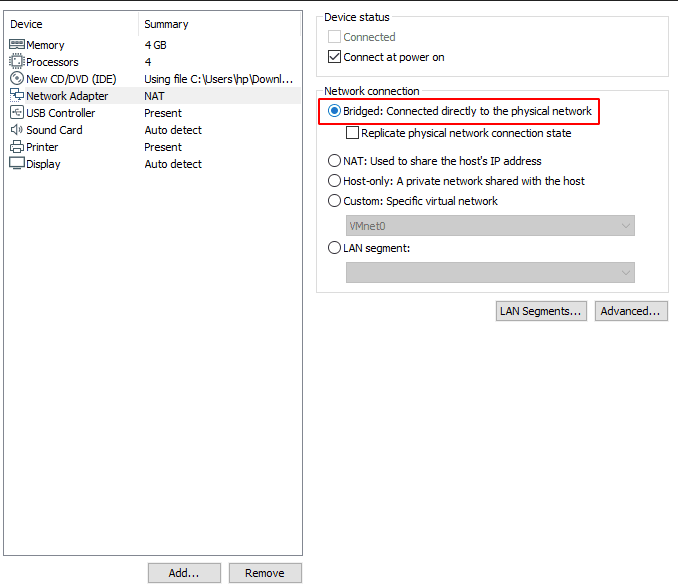
Just change the network connection from “NAT” to “Bridge” and exit from the hardware customization.
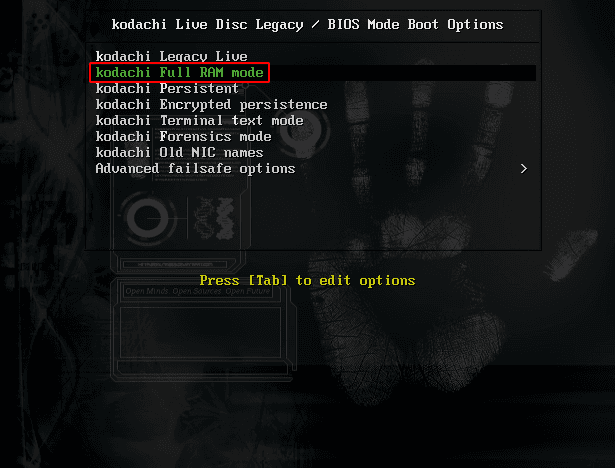
Boot
Great
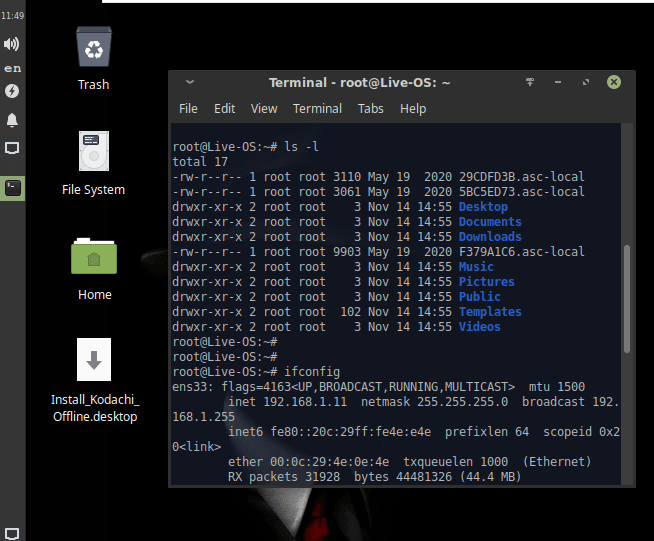
The interface of this operating system is such that hackers in movies.
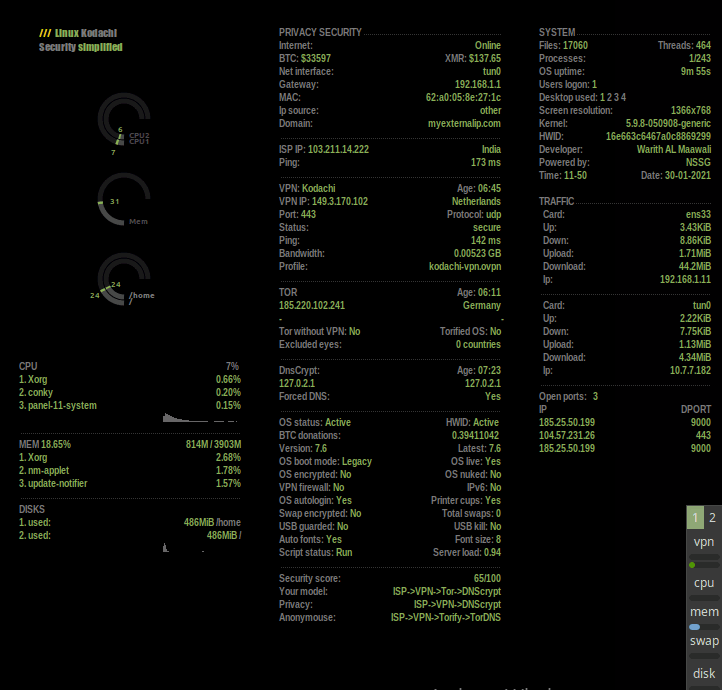
Completely Anonymous