Vyris47
Backend Admin
LEVEL 1
300 XP

Hey Folks, in this tutorial we are going to configure another subdomain fuzzer in our Kali Linux operating system to make our penetration testing more vigorous. Knockpy is a python3 tool designed to enumerate subdomains on a target domain through dictionary attack. We are constantly writing articles on subdomain takeover tool, so if you don’t like this tool then you can read our previous article once.
Let’s take a look at this tool
Installation
Have you ever installed python dependencies and if not then please check our previous article before going directly to the installation of this tool because we will need python dependencies for this tool to run. So first we will download this tool from github and enter the directory.
git clone https://github.com/guelfoweb/knock.git
cd knock12git clone
https://github.com/guelfoweb/knock.gitcd knock

GOOD
python3 setup.py install1python3 setup.py install

Done
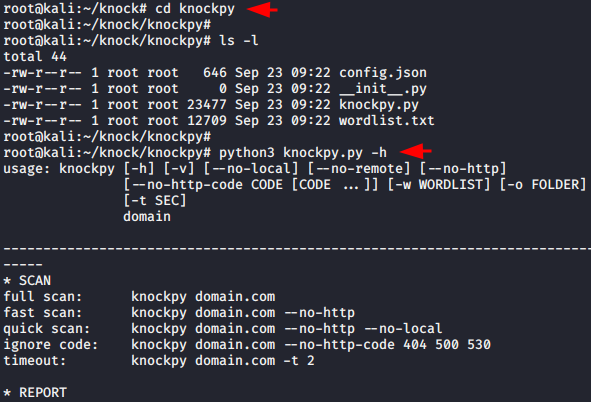
cd knockpy
python3 knockpy.py -h12cd knockpypython3 knockpy.py-h
Full Scan
We take an random domain and perform full scan over it. But actually it takes longer time than the other but gives us good results.
python3 knockpy.py logpac.com1python3 knockpy.py logpac.com

Fast Scan
This functionality of this tool does not follow http request so we got faster results than in normal mode.
python3 knockpy.py logpac.com --no-http1python3 knockpy.py logpac.com--no-http

Ignore Response Code
The most common features which comes in each tool is that we can exclude response from output accordingly by giving specific http code.
python3 knockpy.py logpac.com -w /usr/share/wordlists/dirb/common.txt --no-http-code 404 500 5301python3 knockpy.py logpac.com-w/usr/share/wordlists/dirb/common.txt--no-http-code404500530

Hmm
