provv123
Chuckles Officer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we’re going to solve another boot2root challenge called “Iron Corp“. It’s available at TryHackMe for penetration testing practice. This lab is not difficult if we have the right basic knowledge to break the labs and are attentive to all the details we find during the reconnaissance. The credit for making this lab goes to MrSeth6797. Let’s get started and learn how to break it down successfully.
Level: Hard
Since these labs are available on the TryHackMe website.
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
We put the IP address in “etc/hosts” file and execute nmap.

Enumeration
We access the web service of port 8080 and have a control panel, we examine but there is no functionality that can serve us.

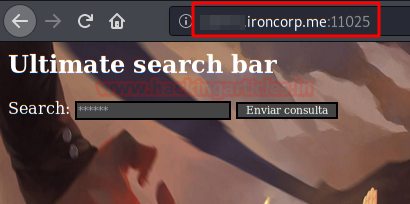
We access the web service of port 11025 and we have the same problem, another website that also does not contain information or functionalities that help us to climb in the system.

Let’s remember that nmap took out the open port 53, let’s see if with dig we can list any sub-domain or information that is relevant to us.
That’s right, we found two subdomains that are running internally.

We cannot access one of them, so we understand that this resource is only exposed internally, we try the other subdomain and see that it loads a protected area with basic authentication.

We help ourselves with Hydra, we “guess” with the user and we use a dictionary with the 10000 most used passwords.

We have listed a new area where you can make inquiries through a form.
Exploiting
After several tests of what kind of vulnerability we are facing, we found that the site is vulnerable to SSRF attacks.
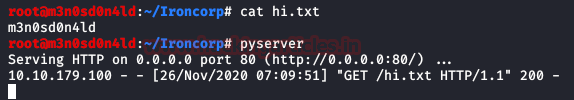
Let’s do the following proof of concept:
We see as a result that it prints us the text of our txt file.

This being the case, we can use it to perform an internal port scan and discover new services that are only available internally. This would help an attacker discover internally exposed services, evading their firewall (in the case of having one, of course).
We took advantage of the vulnerability and loaded the subdomain that we could not access from the perimeter, now we can!

We examine the code and see a variable that prints out a user’s name.
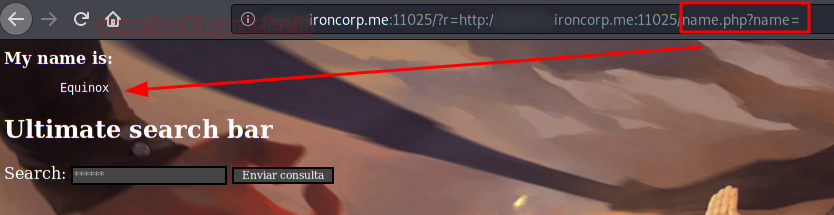
After several code injection tests, you can see that in encode url you can execute commands in the system.

We use “certutil” to download our “Nishan” reverse shell.

Now we run a powershell that runs our shell “m3.ps1“. (

If everything has gone correctly, we will have a connection from the machine to our kali with “nt authority\system” permissions.

And now we can read the “user.txt” flag.

Privilege Escalation (SuperAdmin)
Even being “nt authority\system“, we find that we cannot access the user’s directory “SuperAdmin“, in it the root flag is hidden.
We execute the command “get-acl” to check the permissions we have on that directory, we see that we have a nice “Deny FullControl” to the group of “Administrators“…. But? And if we try to read the flag directly?

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.
Level: Hard
Since these labs are available on the TryHackMe website.
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumeration
- Hydra
- Dig
Exploiting
- SSRF vulnerability attack
Privilege Escalation
- Abuse of privileges on the system
- Capture the flag
Walkthrough
Reconnaissance
We put the IP address in “etc/hosts” file and execute nmap.
Code:
nmap -n -Pn -sV -sC -p53,135,3389,8080,11025,49667,49670 ironcorp.me -o ironcorp.me
Enumeration
We access the web service of port 8080 and have a control panel, we examine but there is no functionality that can serve us.

We access the web service of port 11025 and we have the same problem, another website that also does not contain information or functionalities that help us to climb in the system.

Let’s remember that nmap took out the open port 53, let’s see if with dig we can list any sub-domain or information that is relevant to us.
That’s right, we found two subdomains that are running internally.

We cannot access one of them, so we understand that this resource is only exposed internally, we try the other subdomain and see that it loads a protected area with basic authentication.

We help ourselves with Hydra, we “guess” with the user and we use a dictionary with the 10000 most used passwords.

We have listed a new area where you can make inquiries through a form.

Exploiting
After several tests of what kind of vulnerability we are facing, we found that the site is vulnerable to SSRF attacks.

Let’s do the following proof of concept:
We see as a result that it prints us the text of our txt file.

This being the case, we can use it to perform an internal port scan and discover new services that are only available internally. This would help an attacker discover internally exposed services, evading their firewall (in the case of having one, of course).
We took advantage of the vulnerability and loaded the subdomain that we could not access from the perimeter, now we can!

We examine the code and see a variable that prints out a user’s name.

After several code injection tests, you can see that in encode url you can execute commands in the system.

We use “certutil” to download our “Nishan” reverse shell.

Now we run a powershell that runs our shell “m3.ps1“. (
Yes, you could have run everything in one command, but you can’t always do that ;))

If everything has gone correctly, we will have a connection from the machine to our kali with “nt authority\system” permissions.

And now we can read the “user.txt” flag.

Privilege Escalation (SuperAdmin)
Even being “nt authority\system“, we find that we cannot access the user’s directory “SuperAdmin“, in it the root flag is hidden.
We execute the command “get-acl” to check the permissions we have on that directory, we see that we have a nice “Deny FullControl” to the group of “Administrators“…. But? And if we try to read the flag directly?

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.