freelo
Audience Engagement Tactician
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

Hey Folks, in this article we will discuss on an very lightweight information gathering tool as it can easily install and run called “InfoSploit”. The InfoSploit tool is also available for linux, window and android phones ( termux ) that is coded in both bash and python languages.
Let’s take a look
Installation
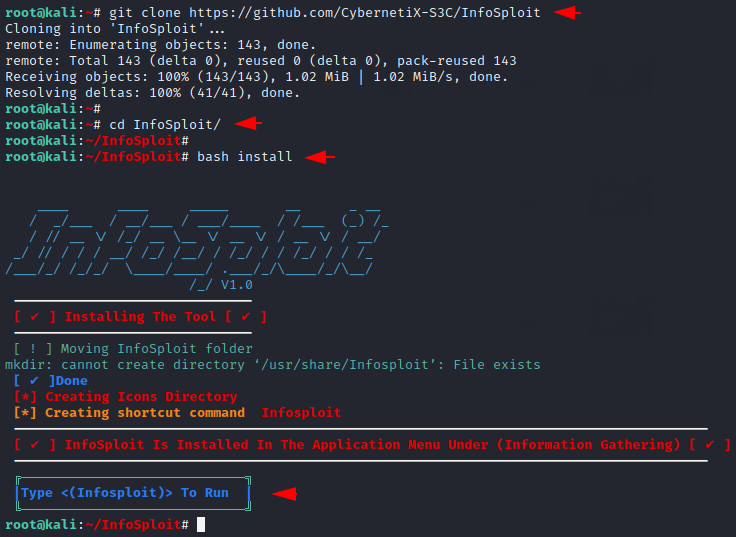
First of all we will download this tool from github by using the git command. After downloading is done then we will go to directory of this tool and execute the bash command in order to install this tool completely. If you have installed all the requirements then this tool will be installed soon, otherwise it will take some time. But after installing it will give us the command to boot this tool directly from anywhere.
git clone https://github.com/CybernetiX-S3C/InfoSploit
cd InfoSploit/
bash install
Infosploit1234git clone
https://github.com/CybernetiX-S3C/InfoSploitcd InfoSploit/bash installInfosploit
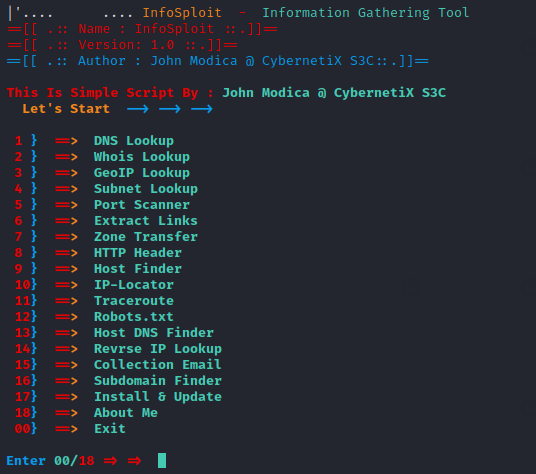
Features
Now you can see all the available special features in the tool, through which we can have good footprint against any target.
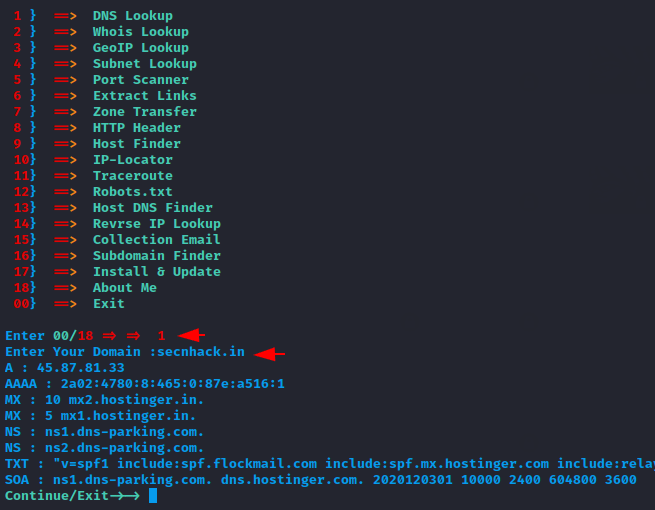
DNS lookup
We can control this tool numerically as you can see in the image below. After selecting the first option, it dumps all DNS records of the target web application.
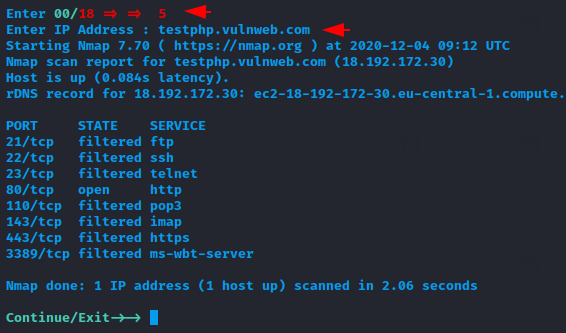
Open Services
Similarly, by selecting the fifth option we can get all the details of open and running services on the target web server.
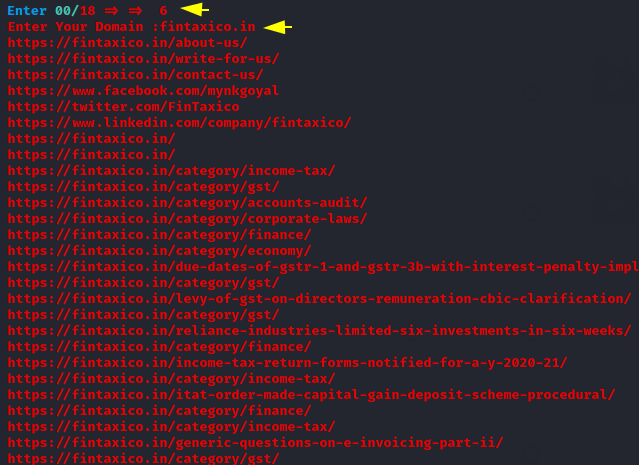
Crawling
Crawling is the best way to find sensitive locations available on the target web application.
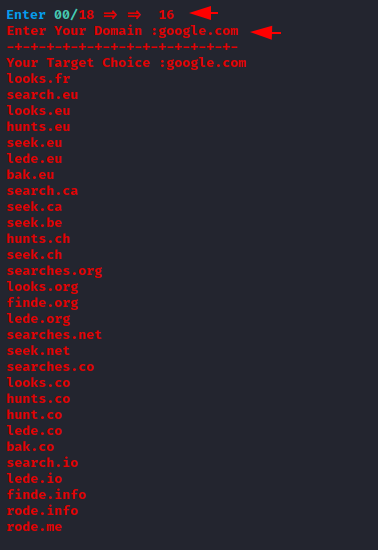
Subdomain Finding
As you can see in the image below how easily all subdomains have been identified.
Nice